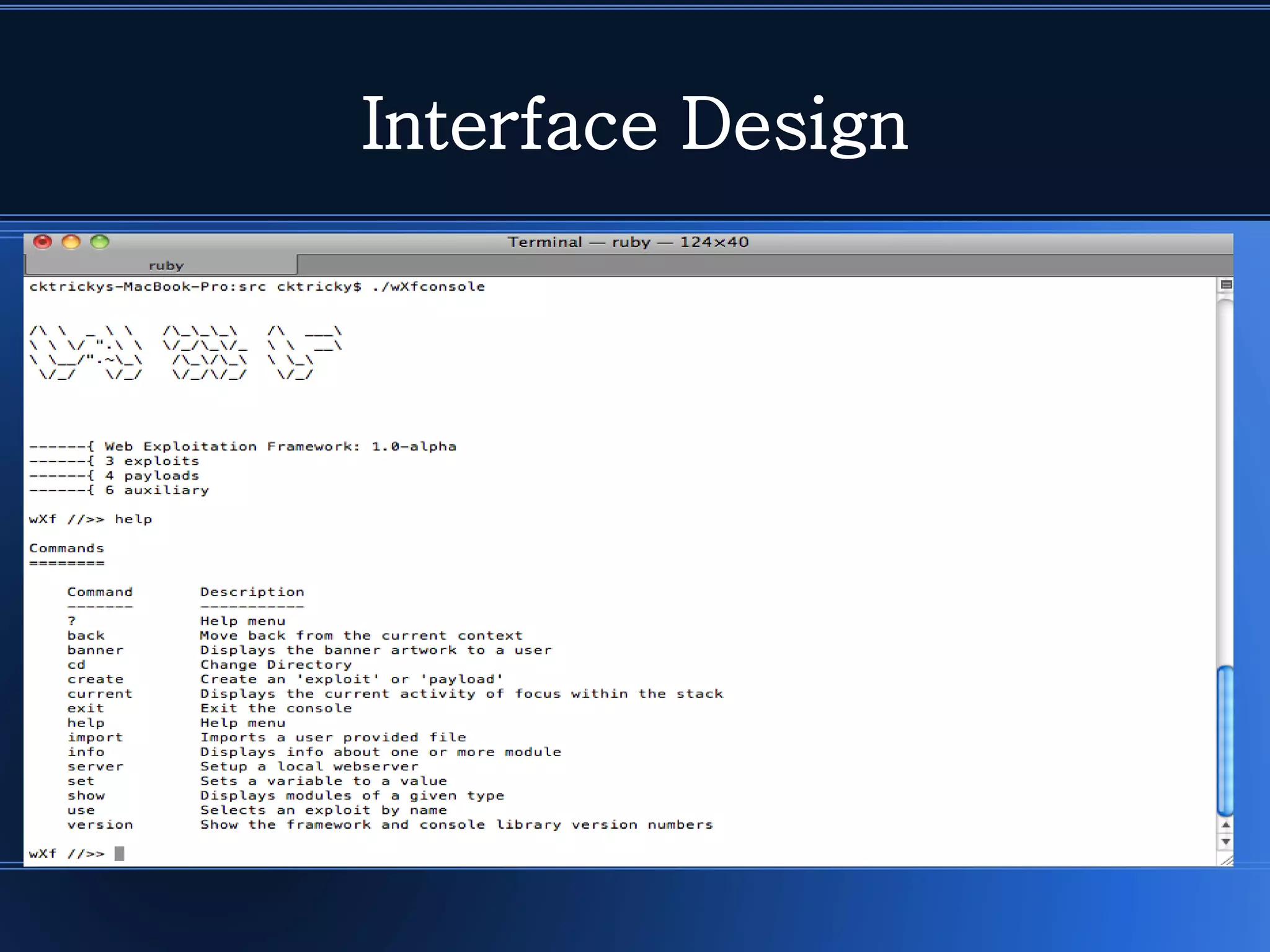
The Web Exploitation Framework (WXF) is a collaborative project developed by experts Seth Law, Chris Gates, and Ken Johnson, focusing on application security and exploitation techniques. WXF aims to enhance web security testing through its core console, customizable modules, and auxiliary functionalities, alongside community involvement for updates and improvements. Future expansions are planned, including additional exploit modules, reporting methods, and compatibility enhancements.