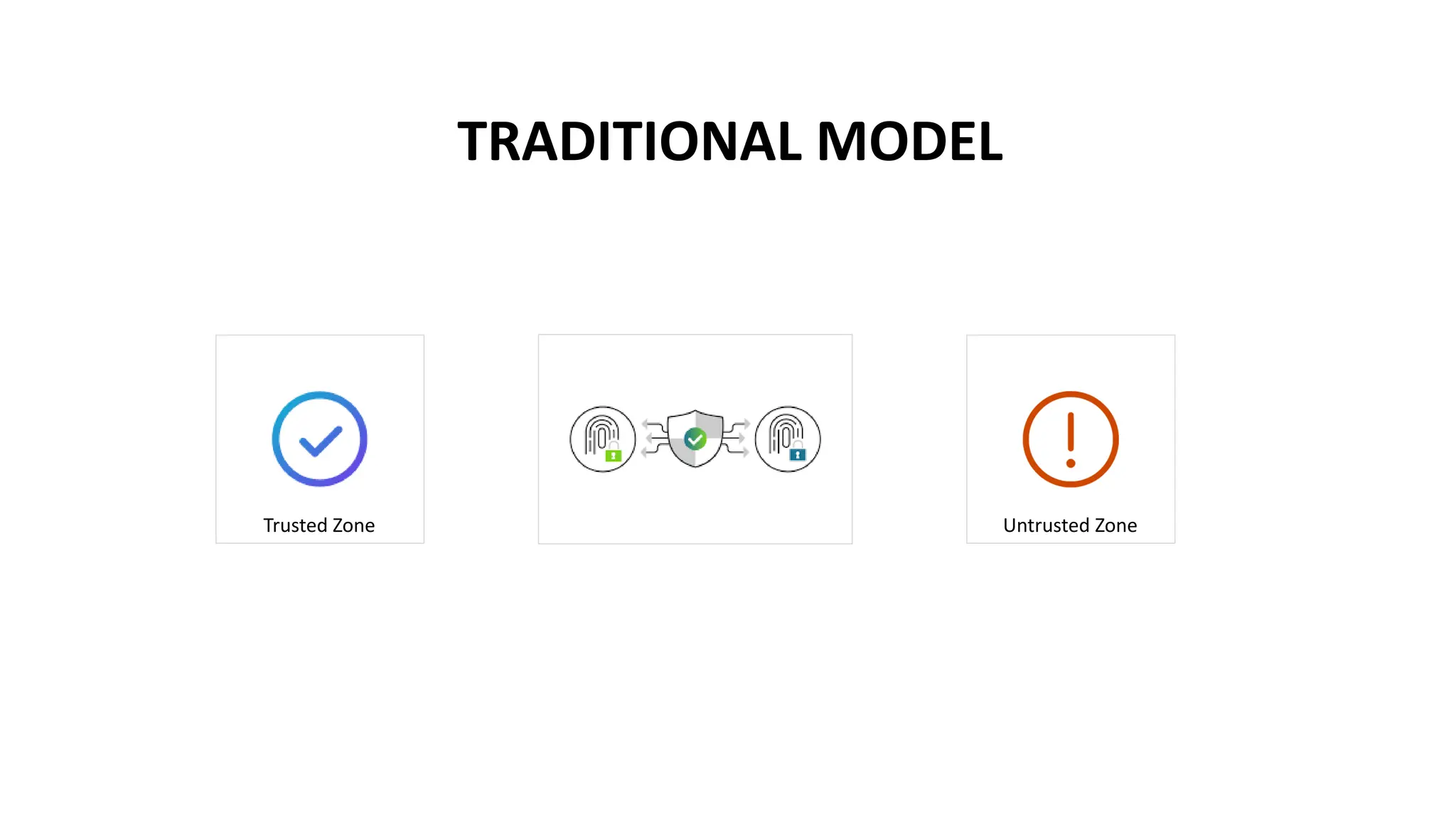
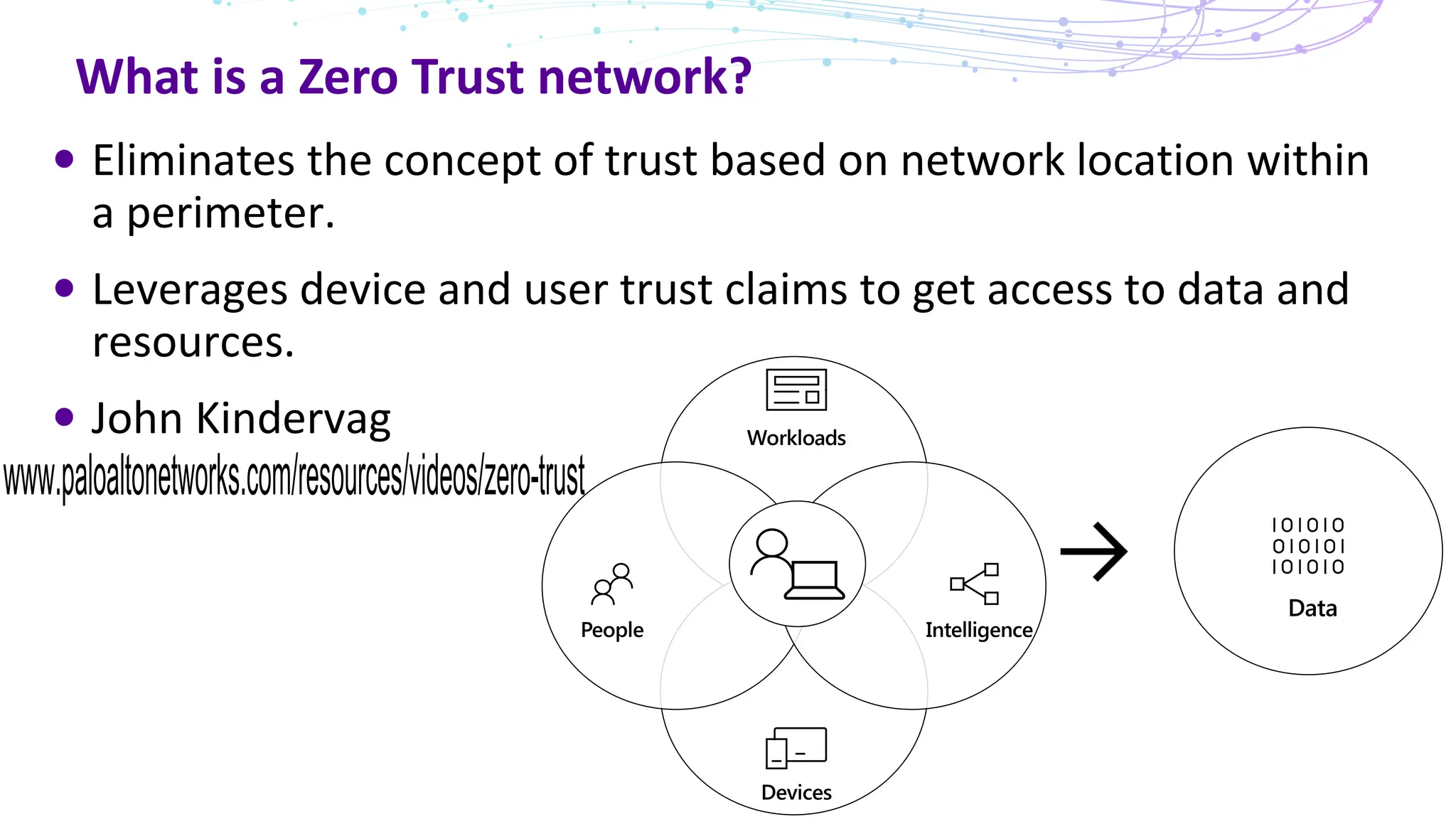
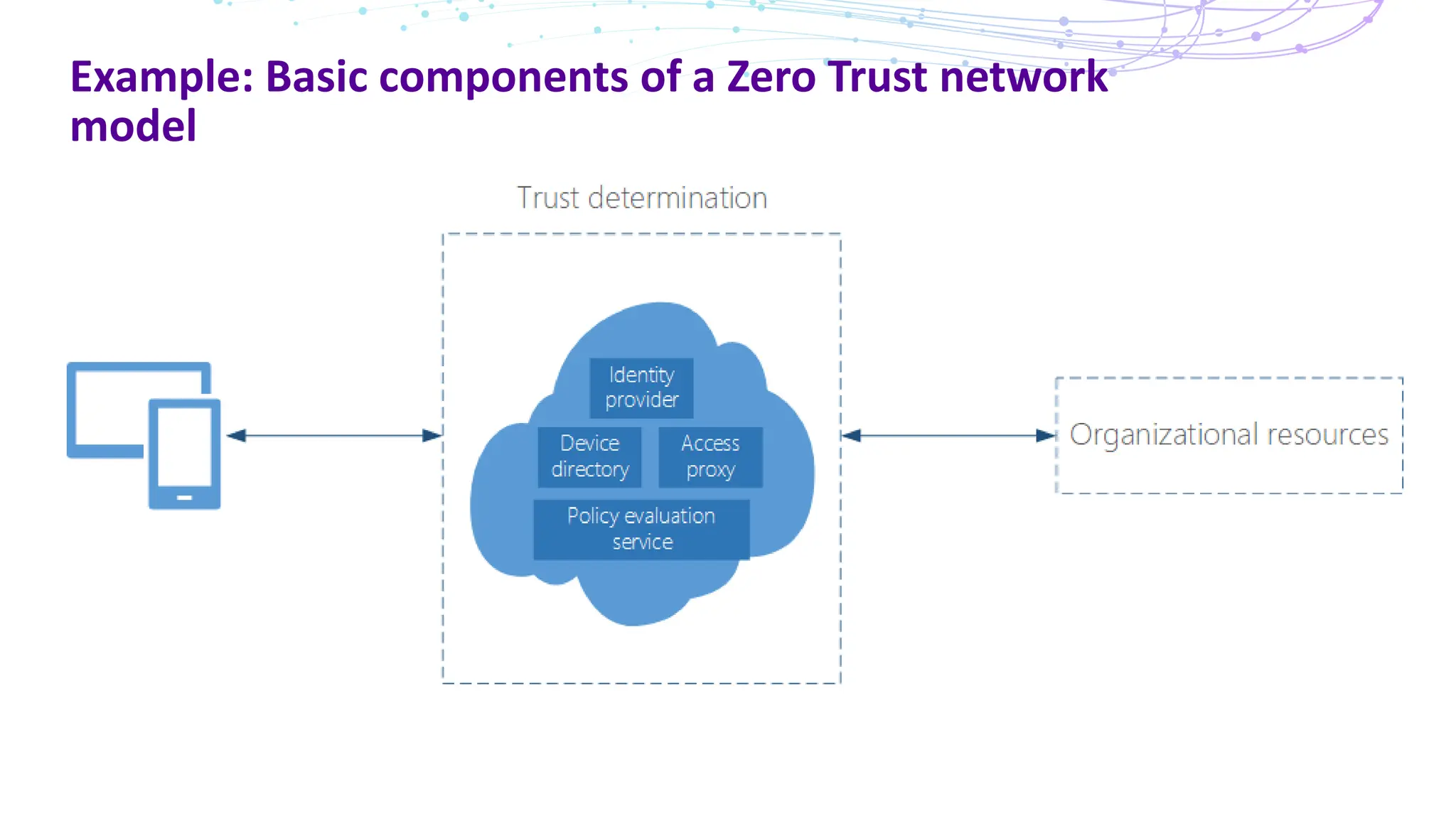
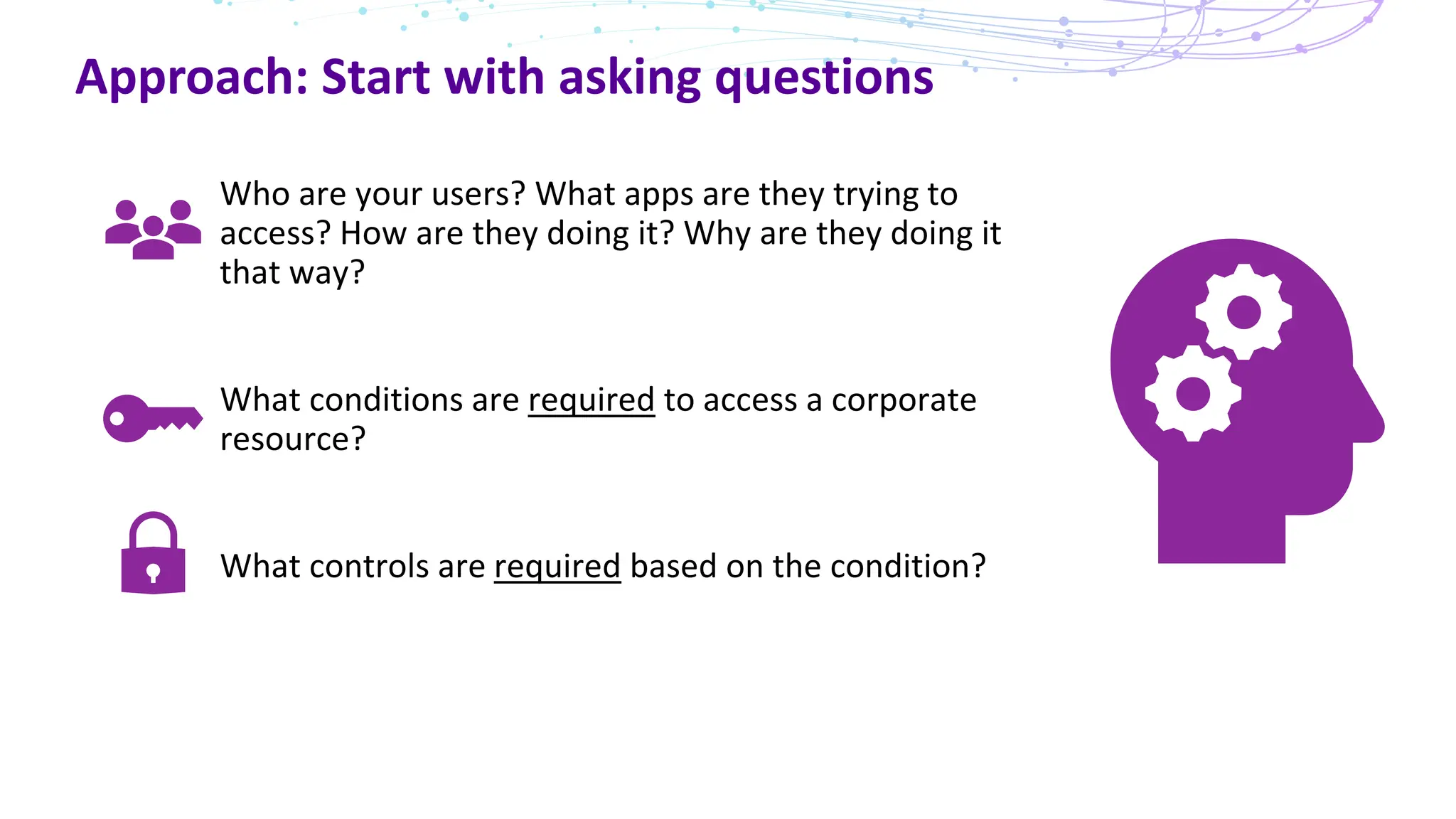
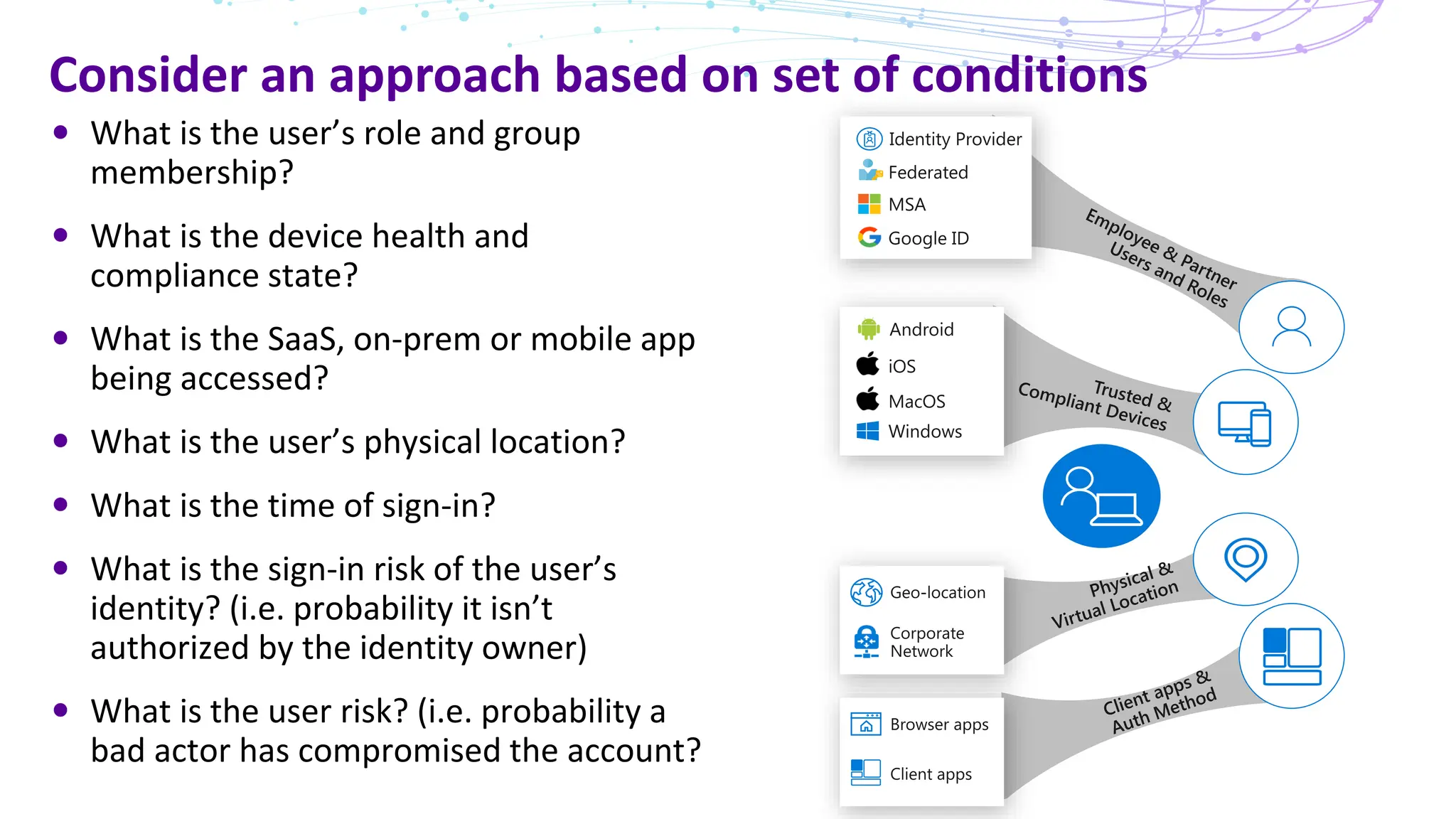
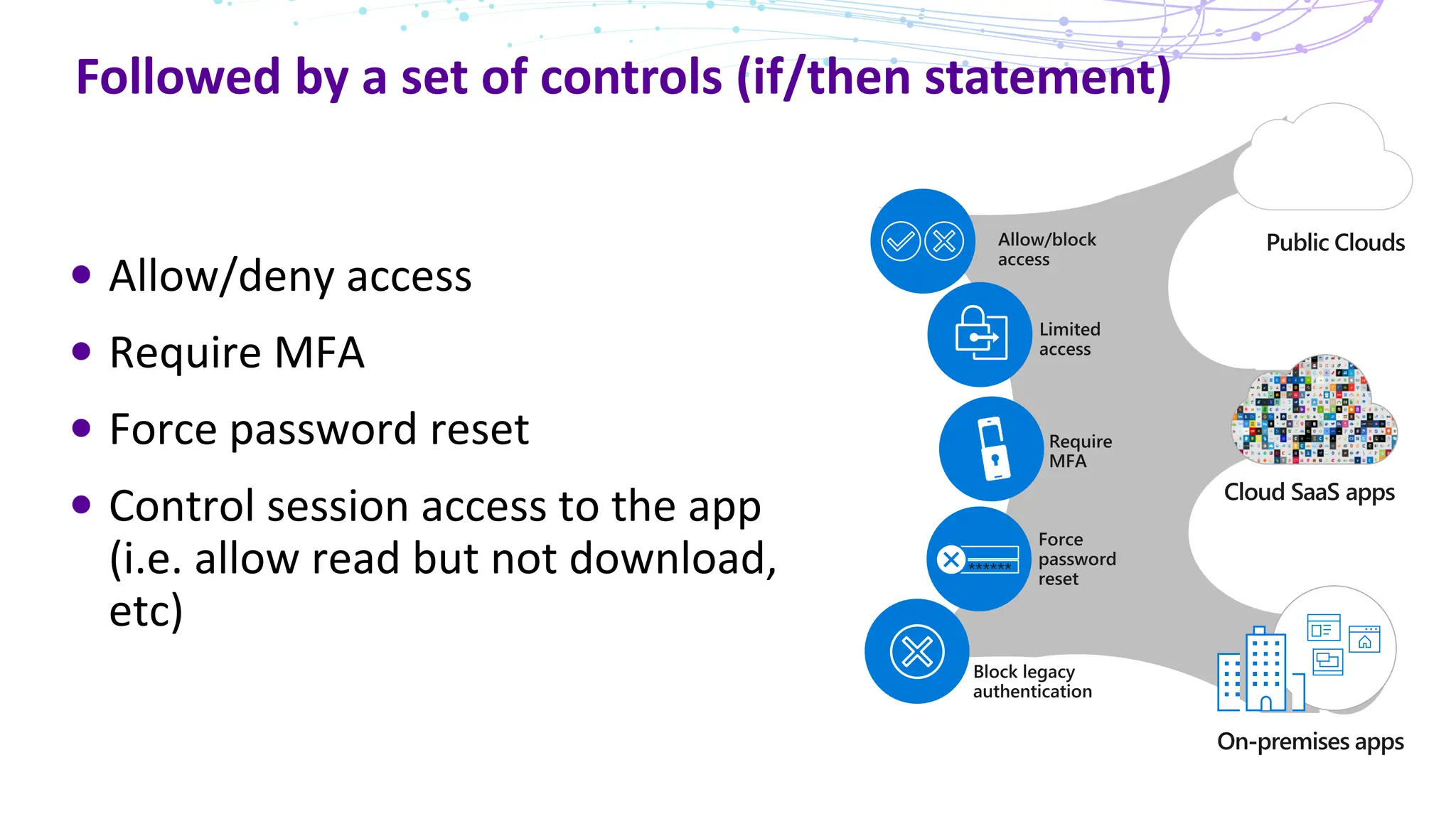
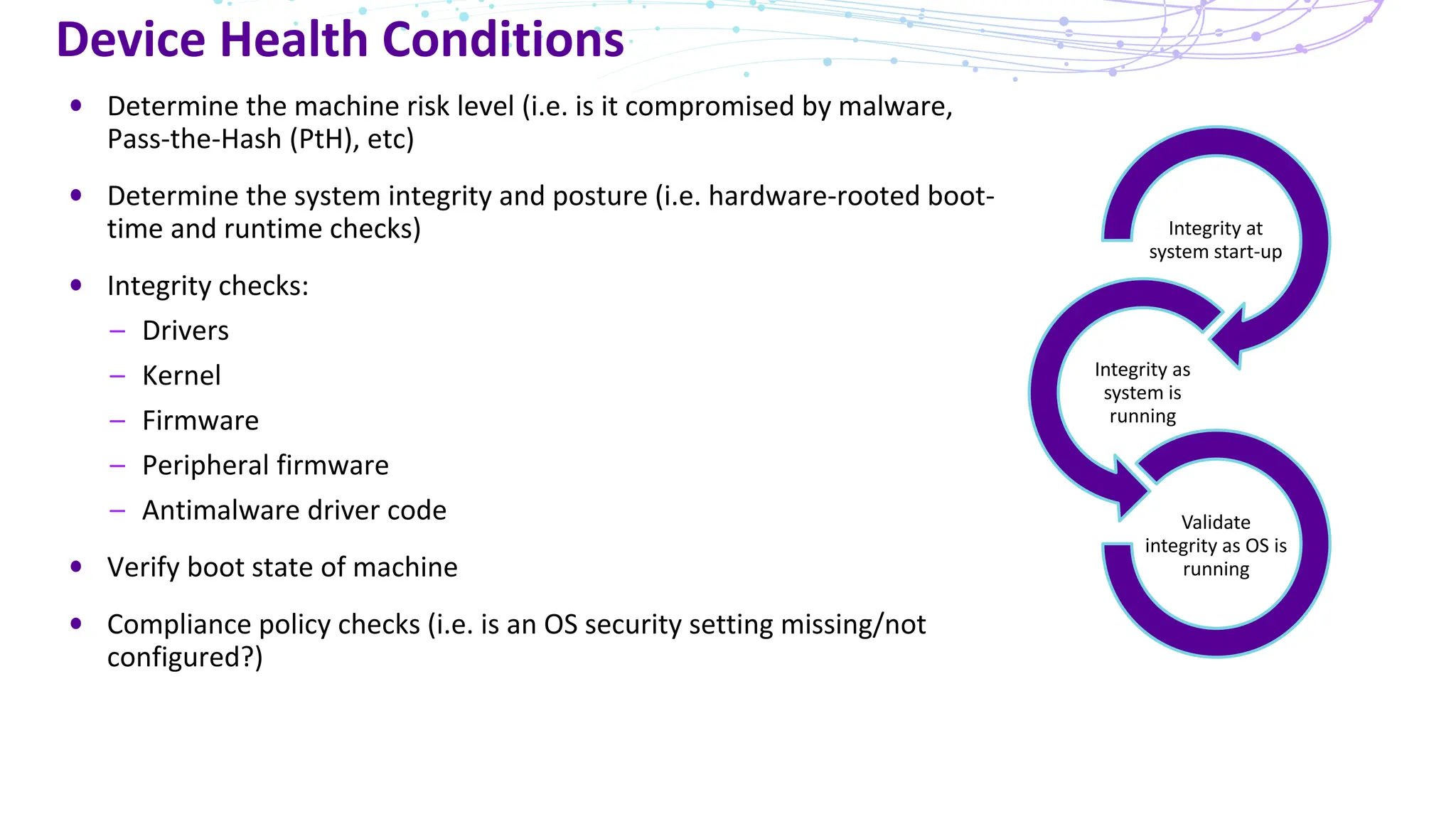
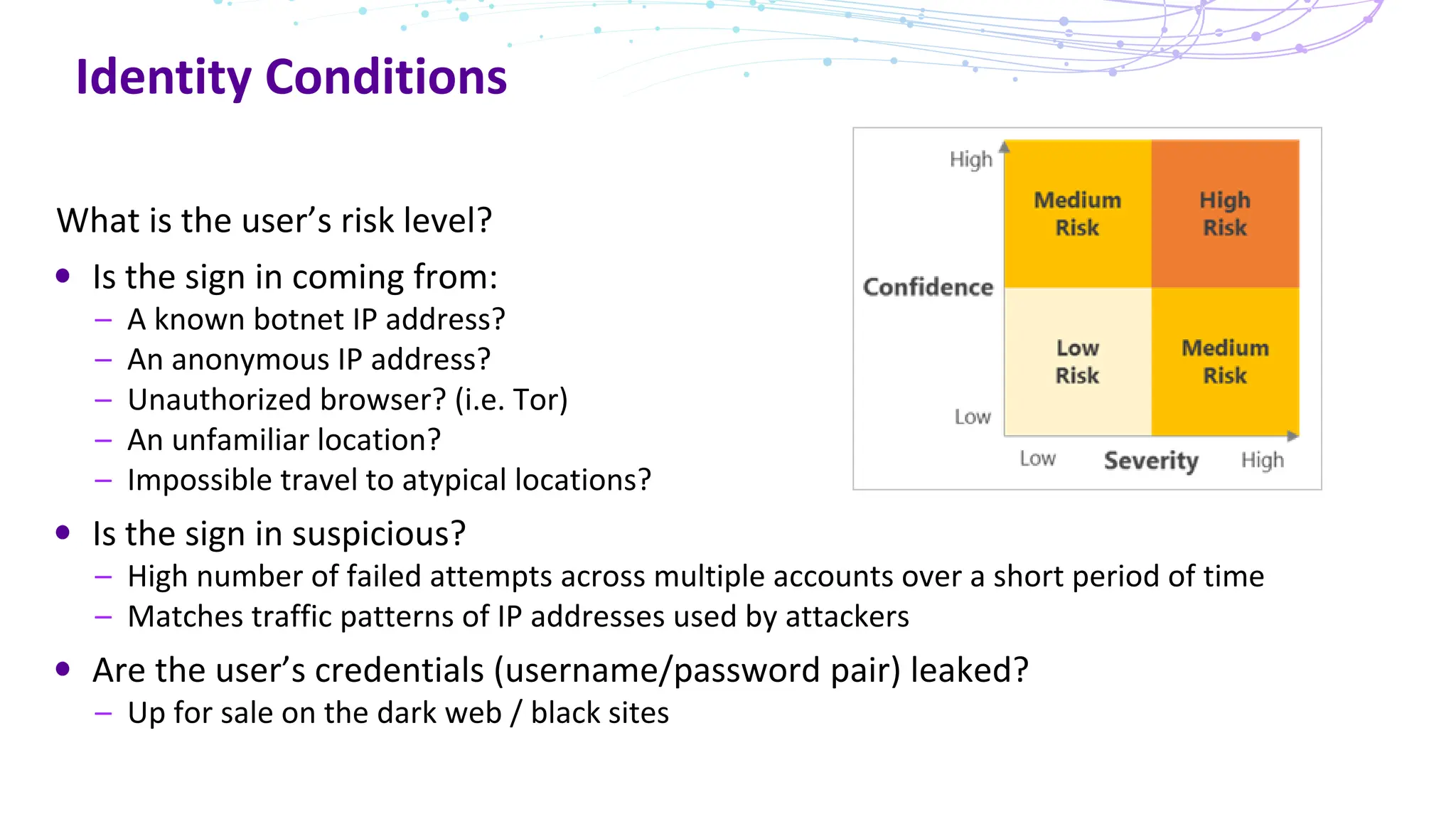
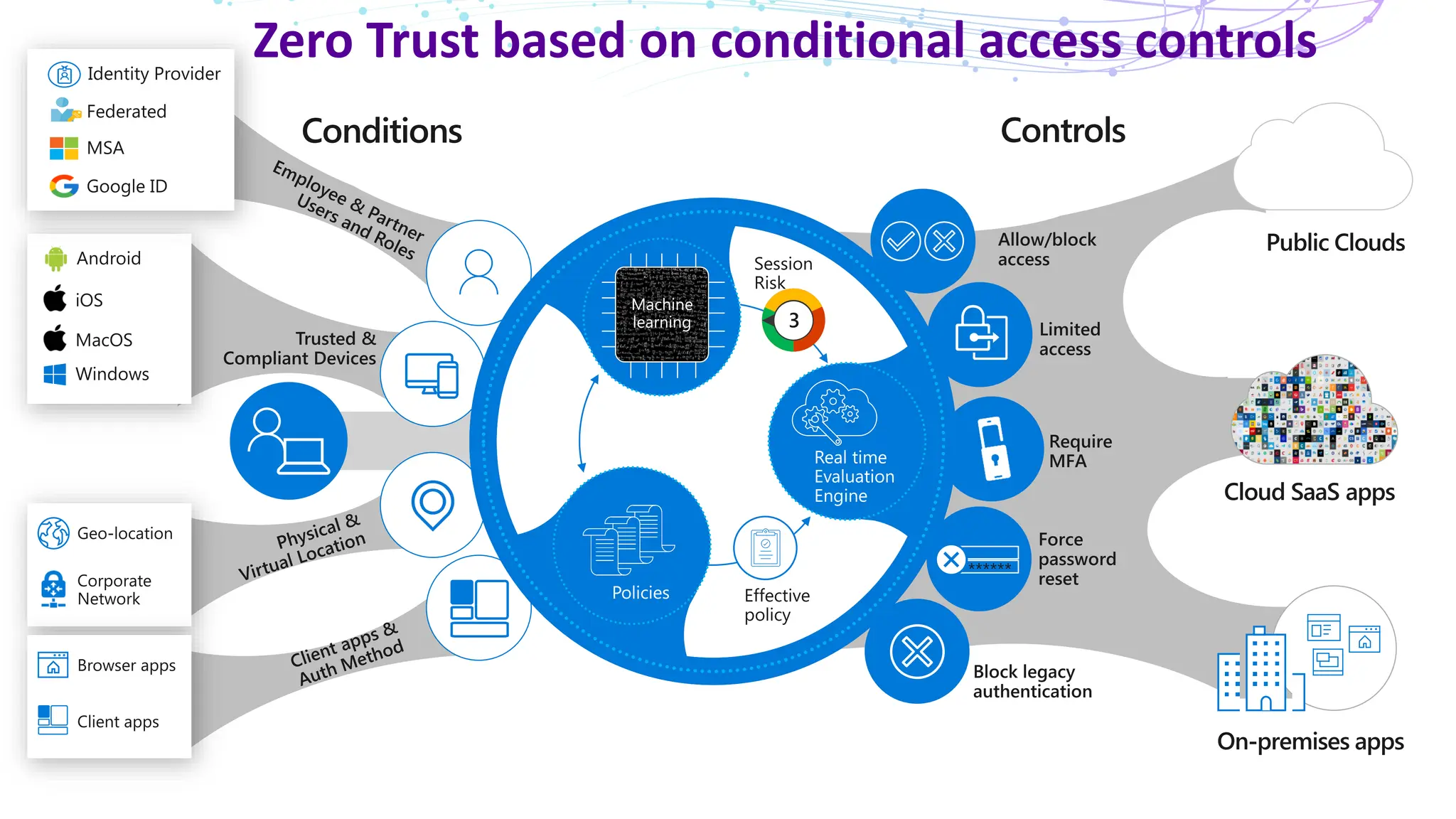
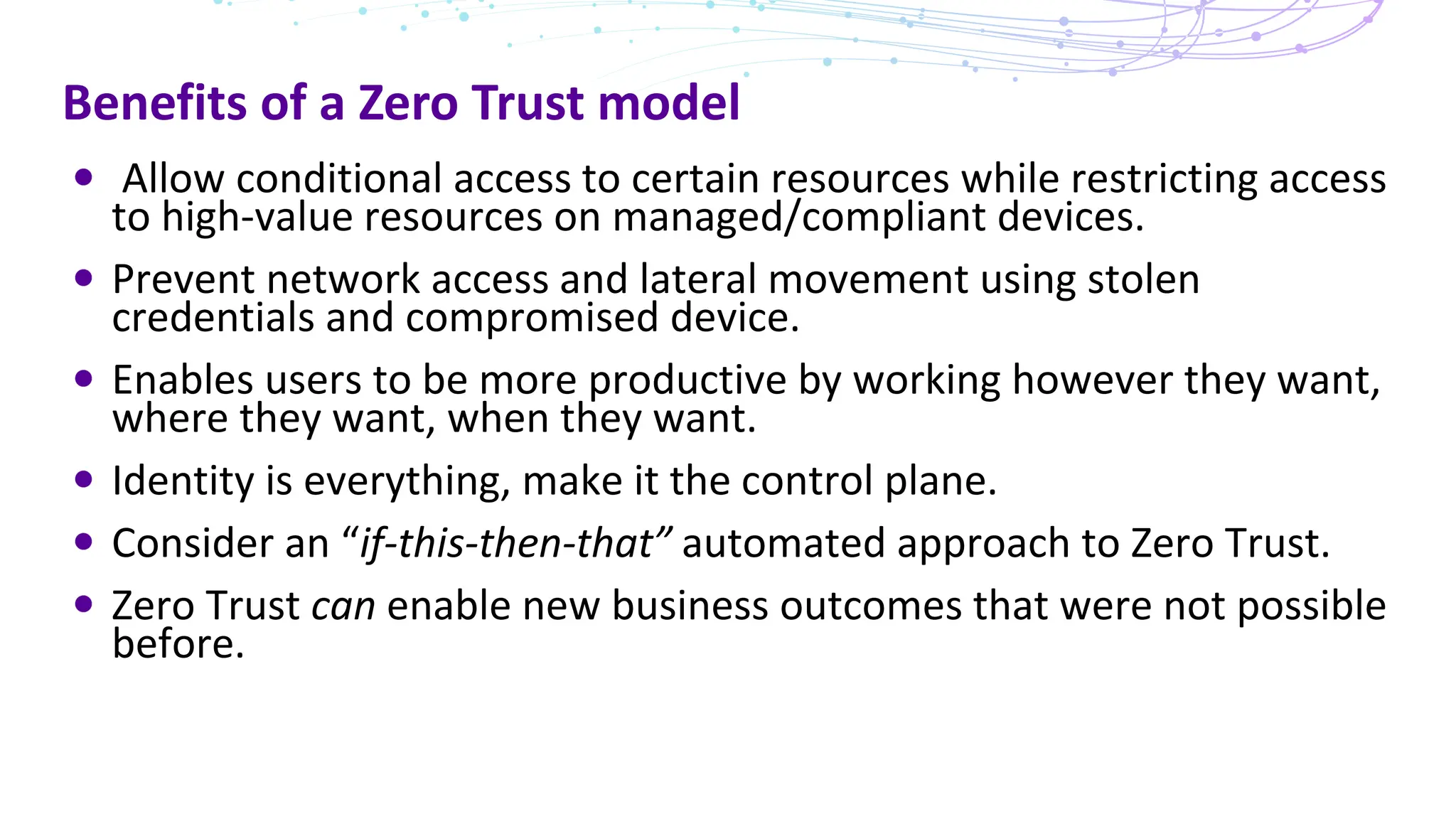
The document discusses the concept of Zero Trust security, emphasizing its importance in modern network architecture to eliminate inherent trust based on network location. It outlines the components needed for a Zero Trust network, including user identity, device health, and conditional access controls, as well as the necessity to adapt to contemporary work styles such as BYOD and BYOC. The document highlights the benefits of implementing a Zero Trust model, including enhanced security, productivity, and improved control over resource access.