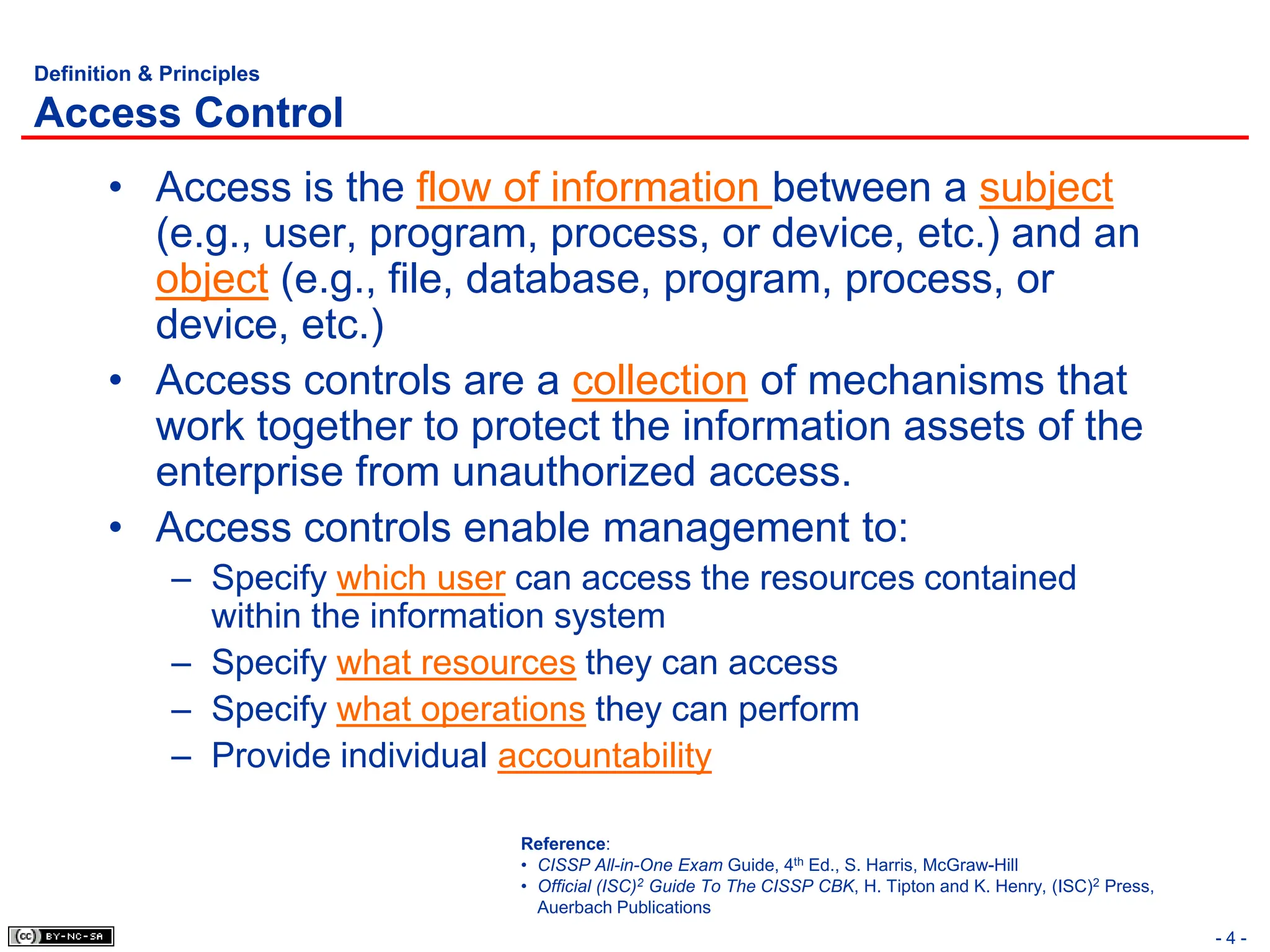
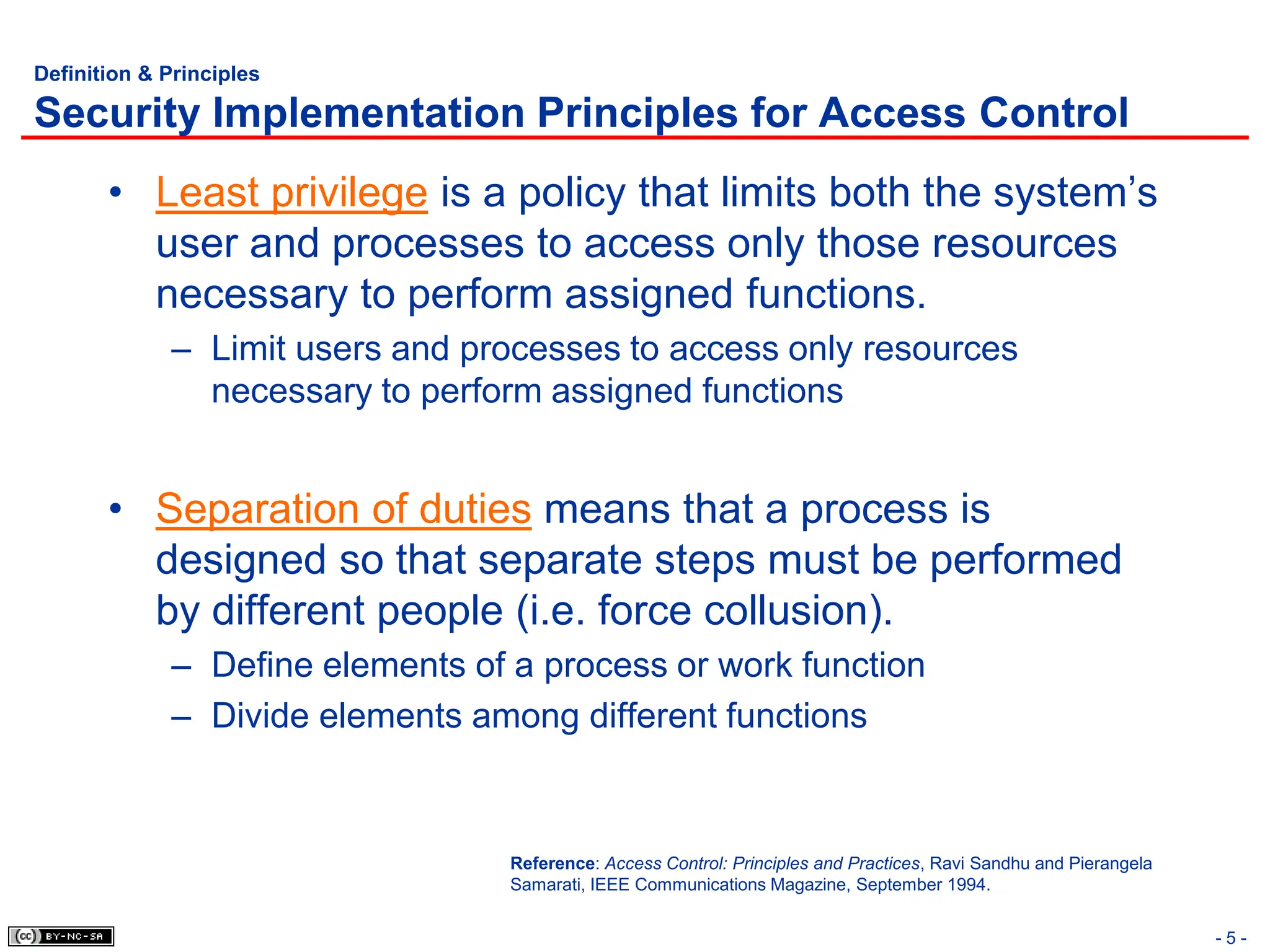
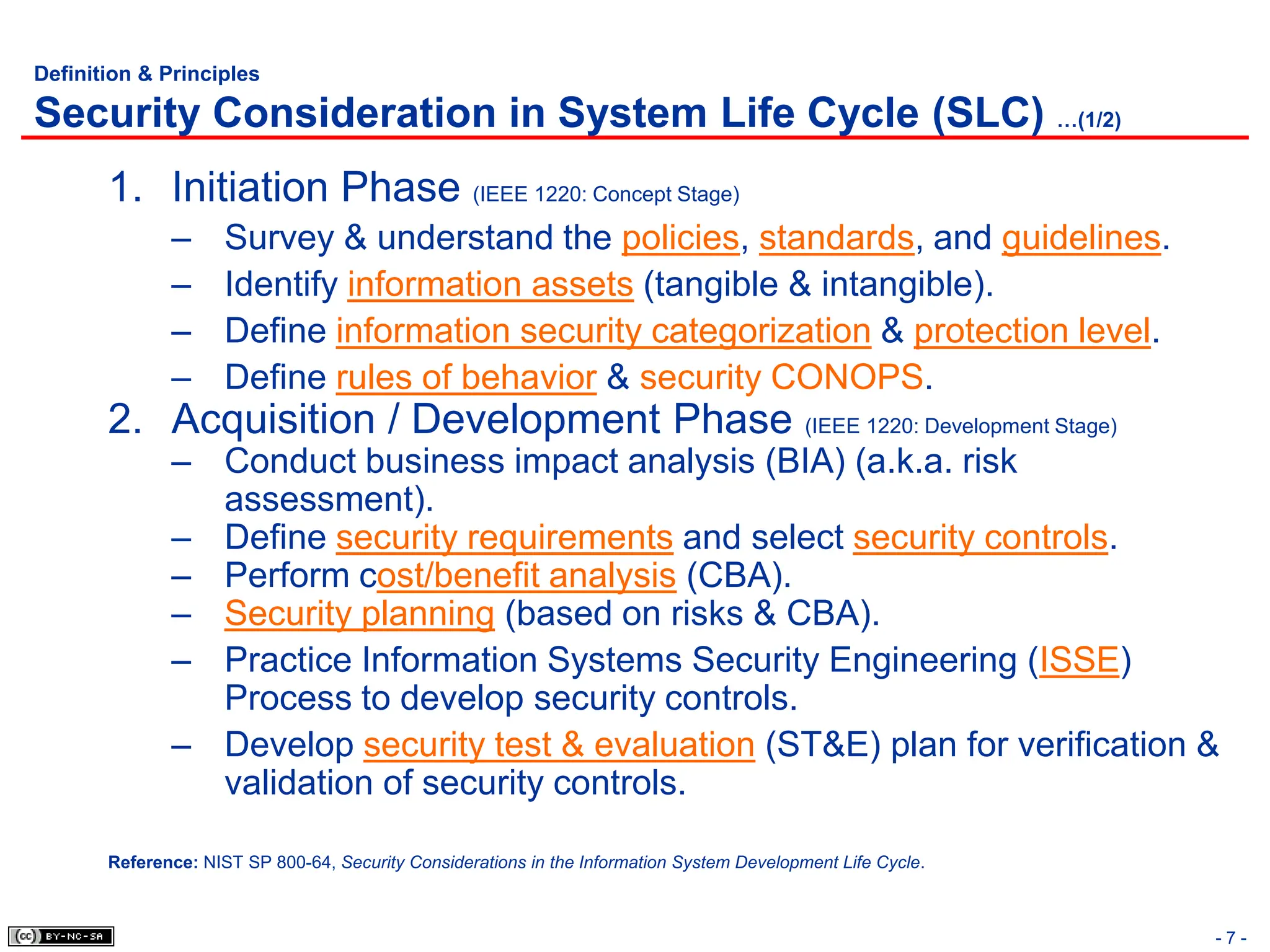
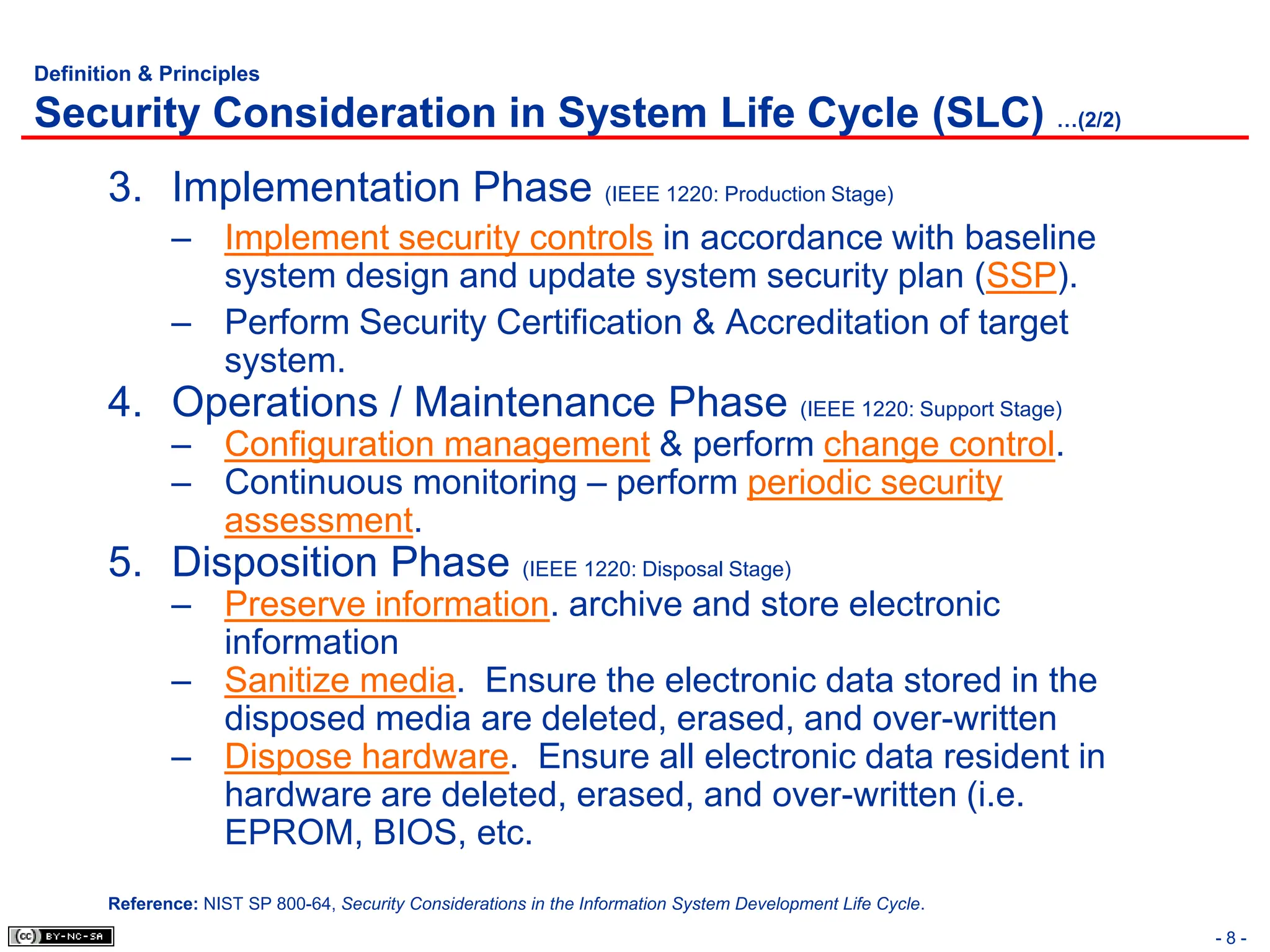
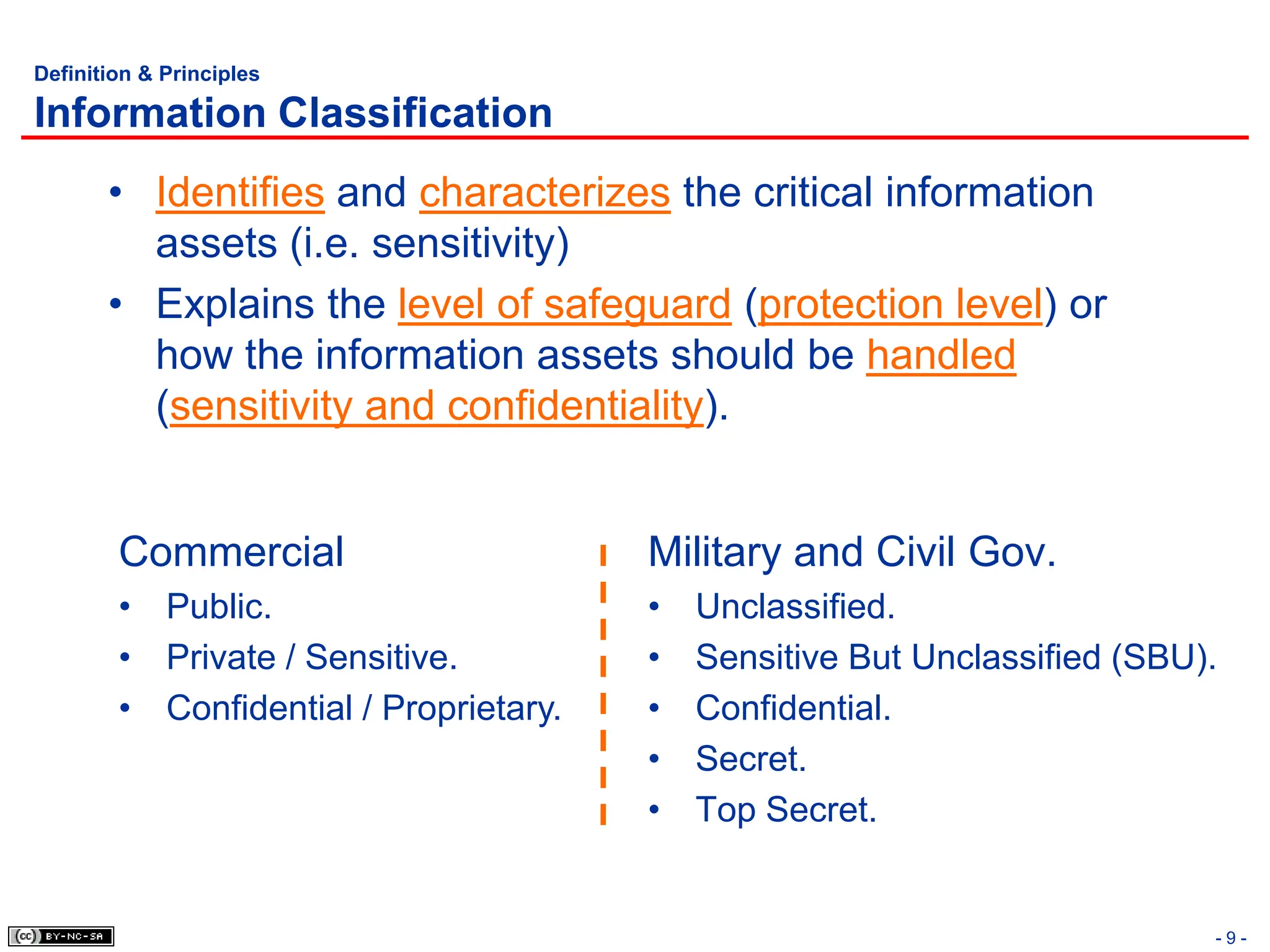
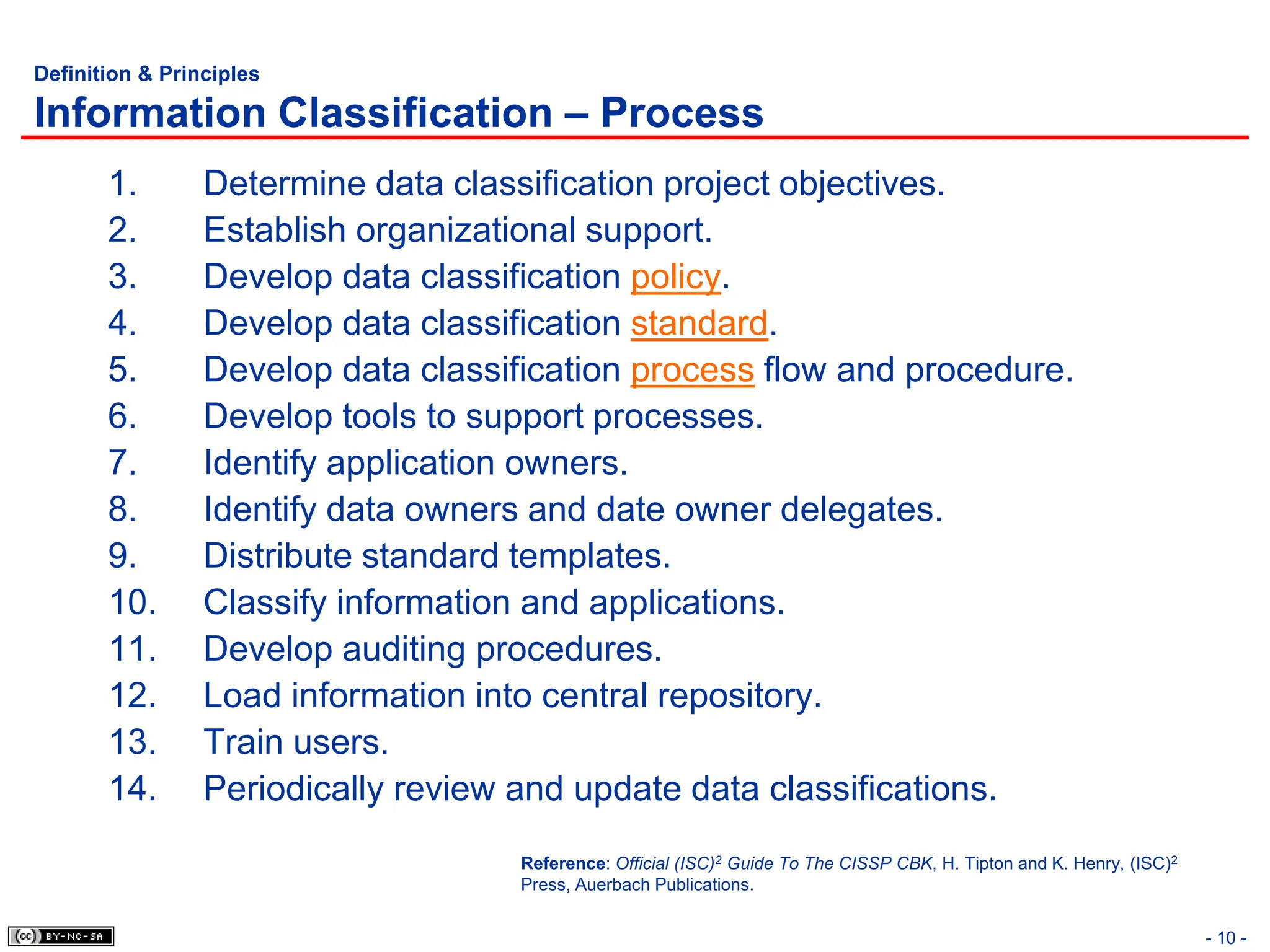
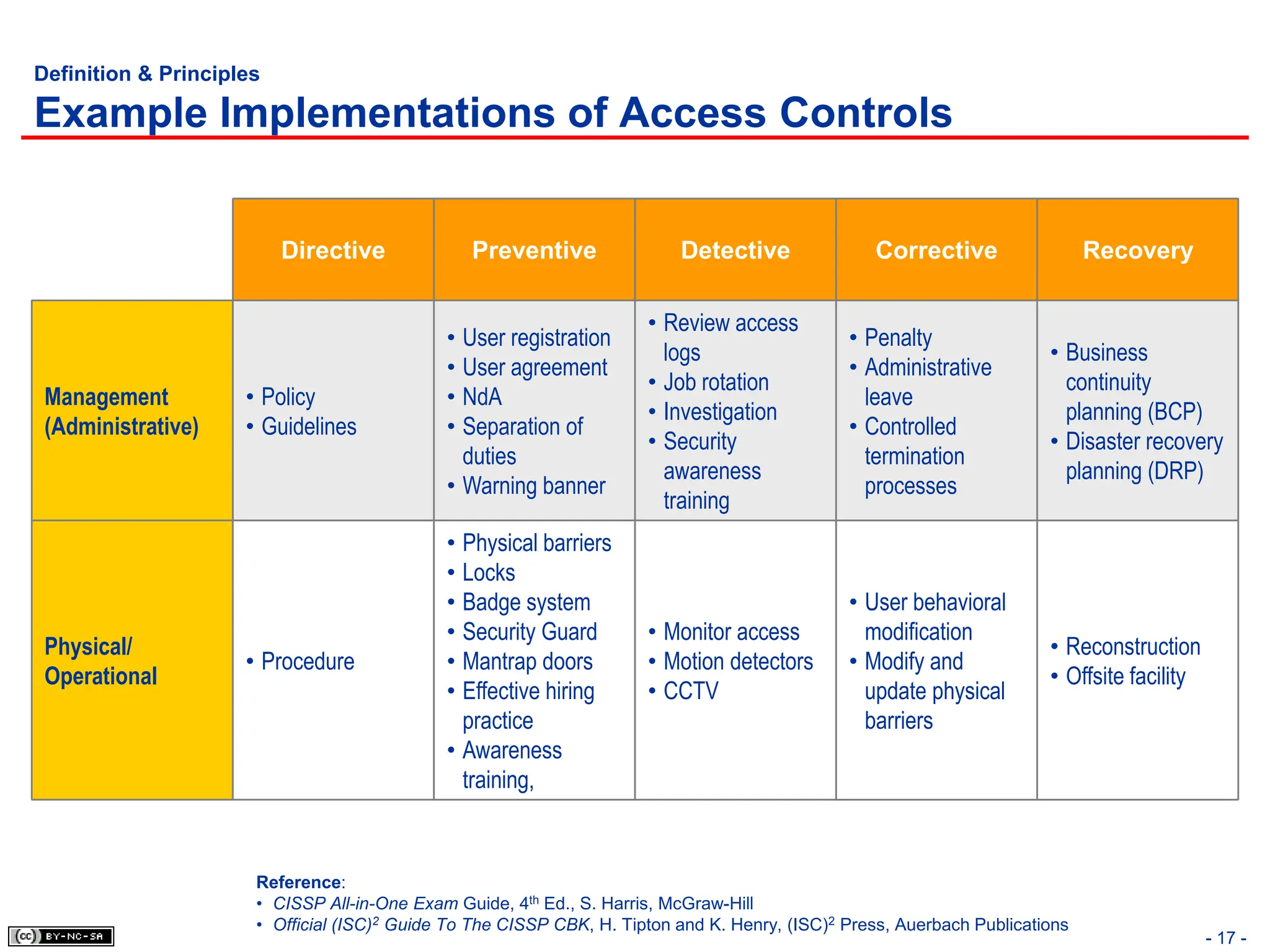
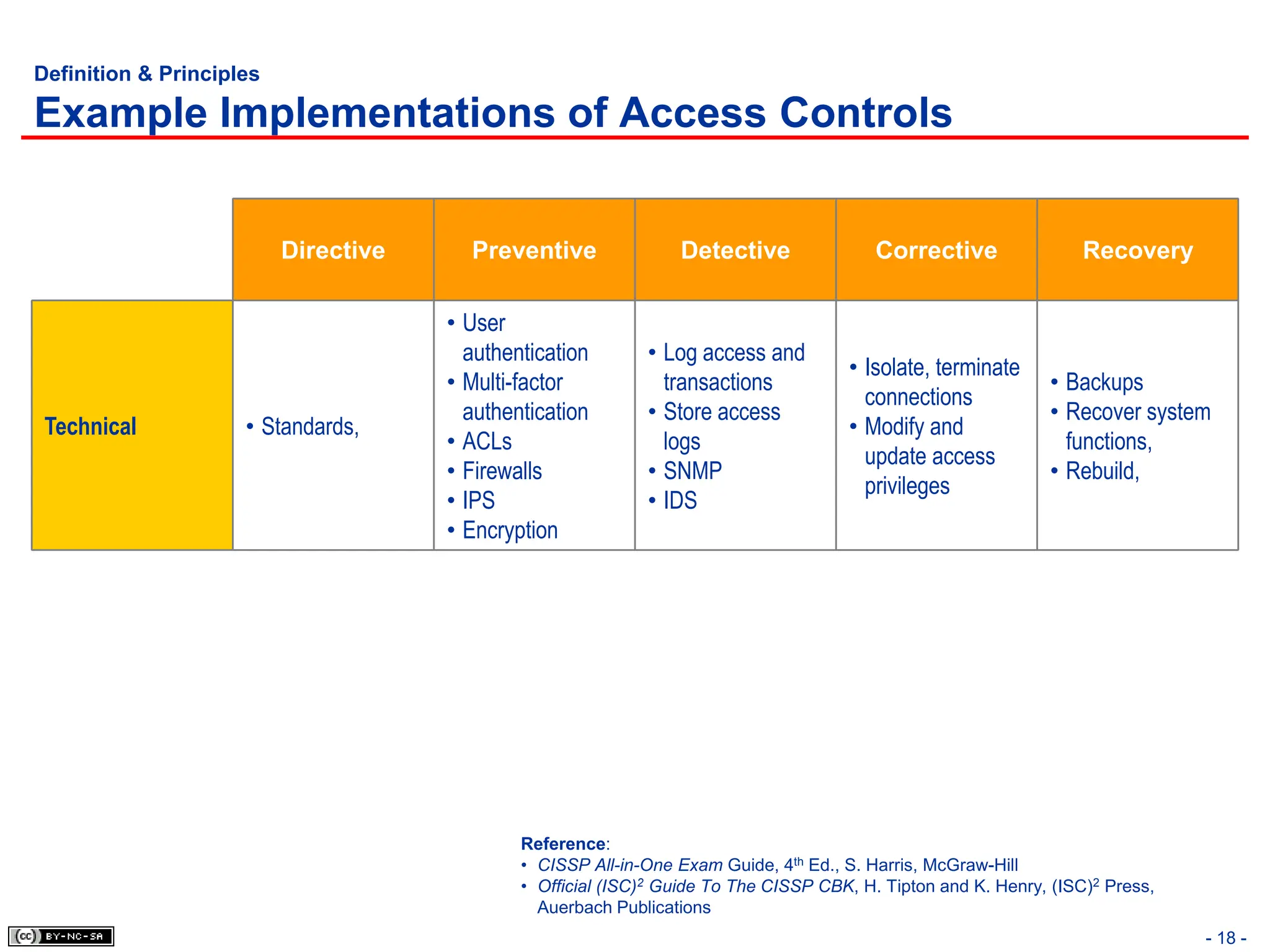
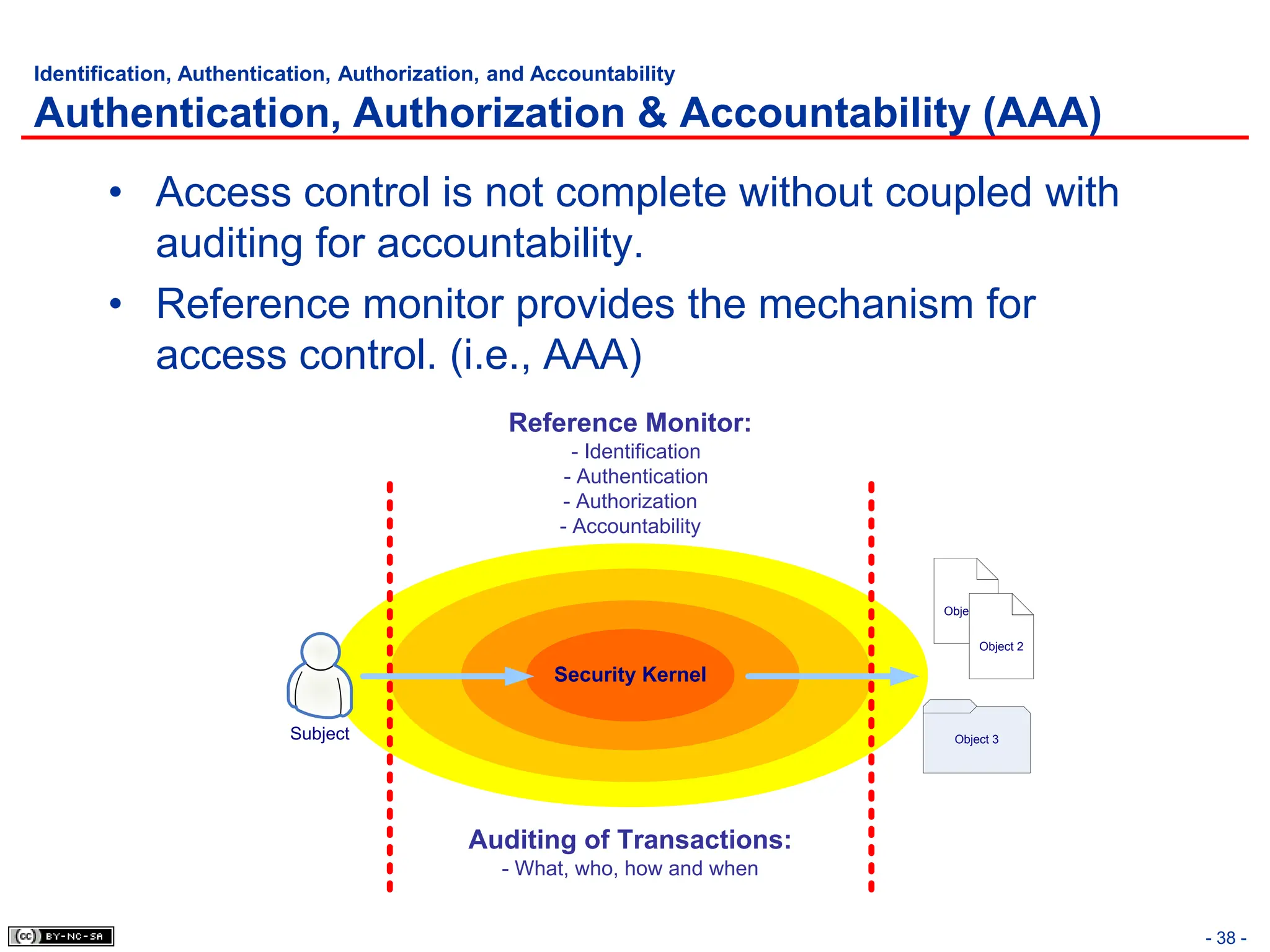
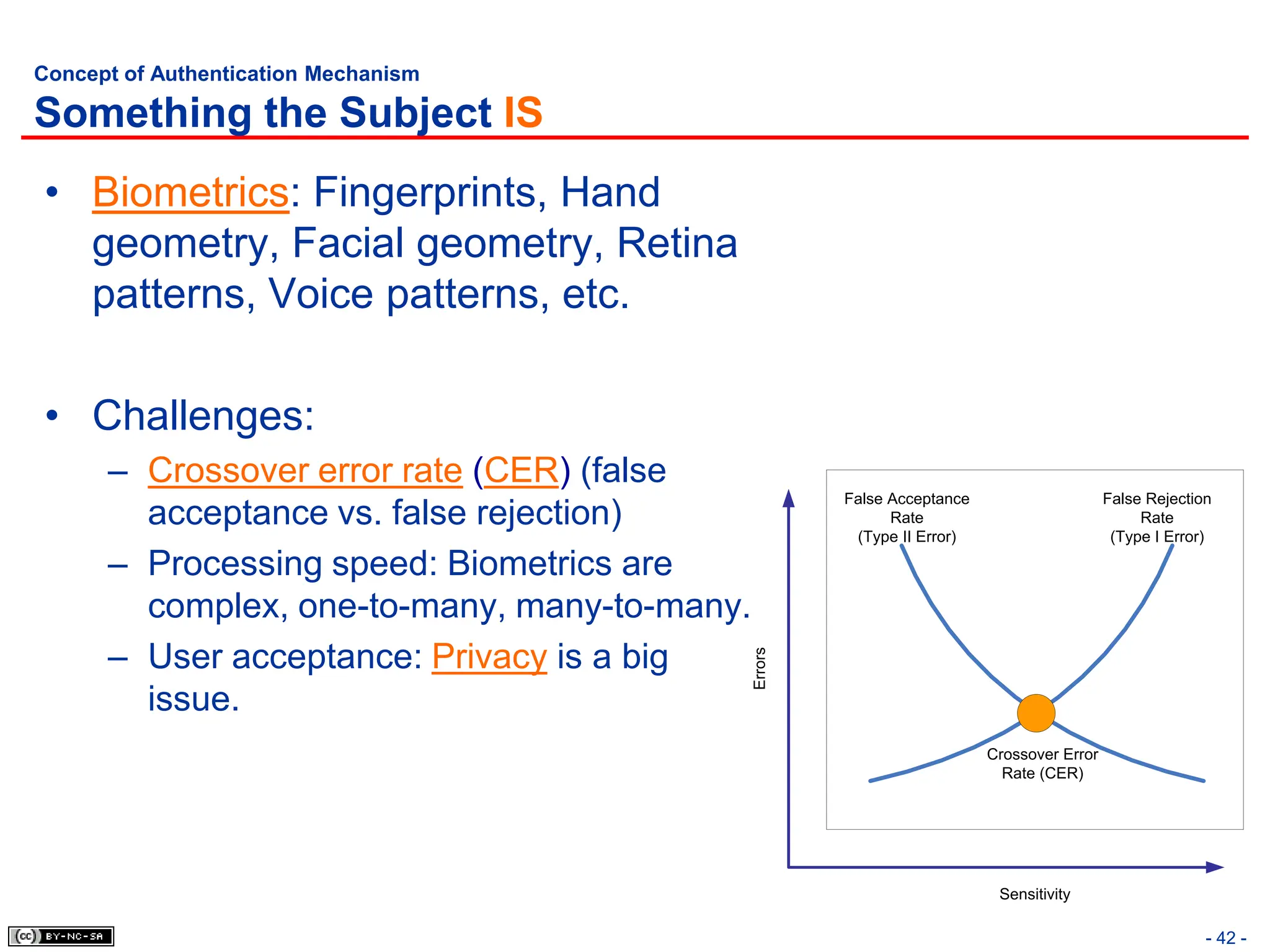
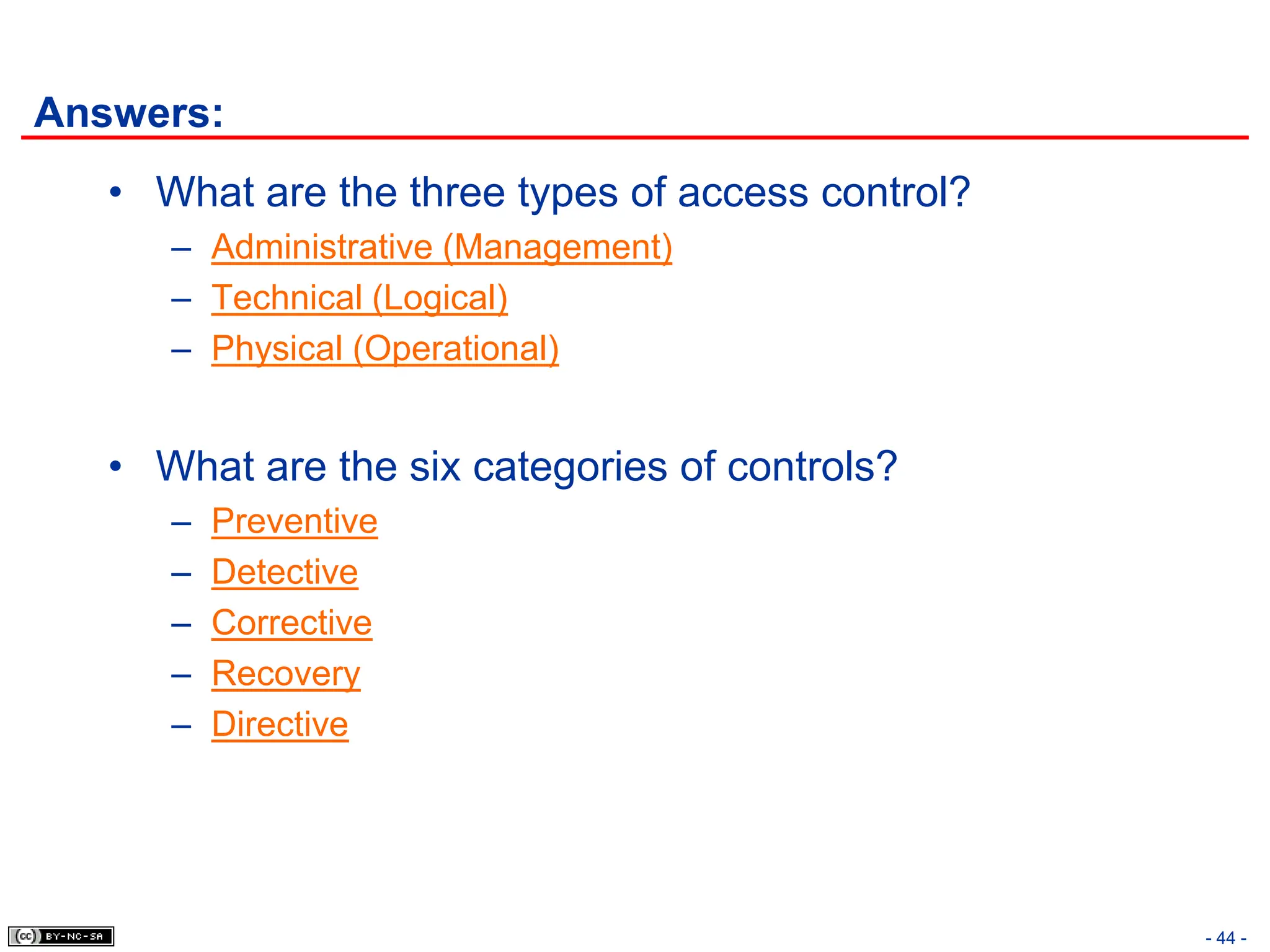
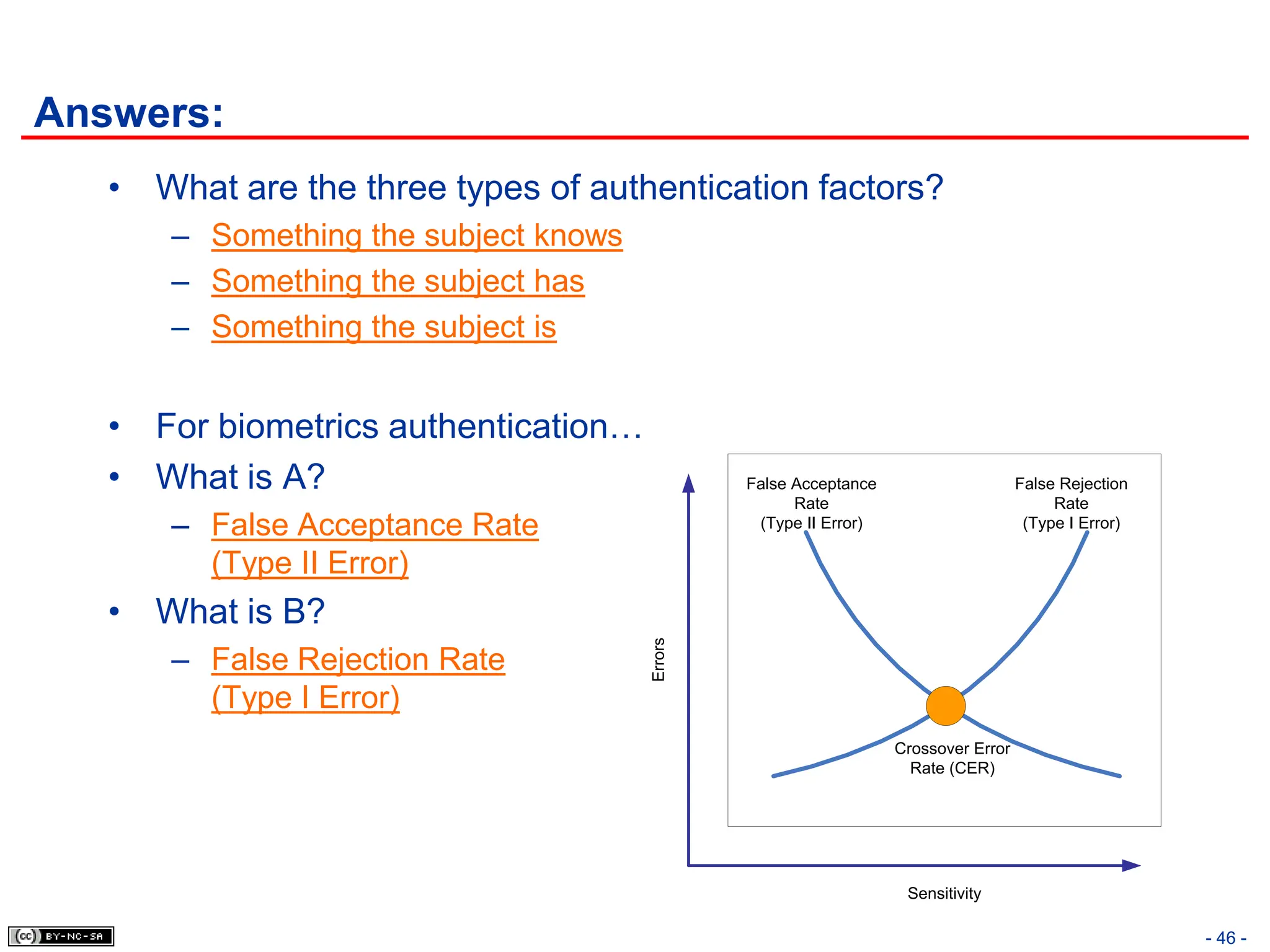
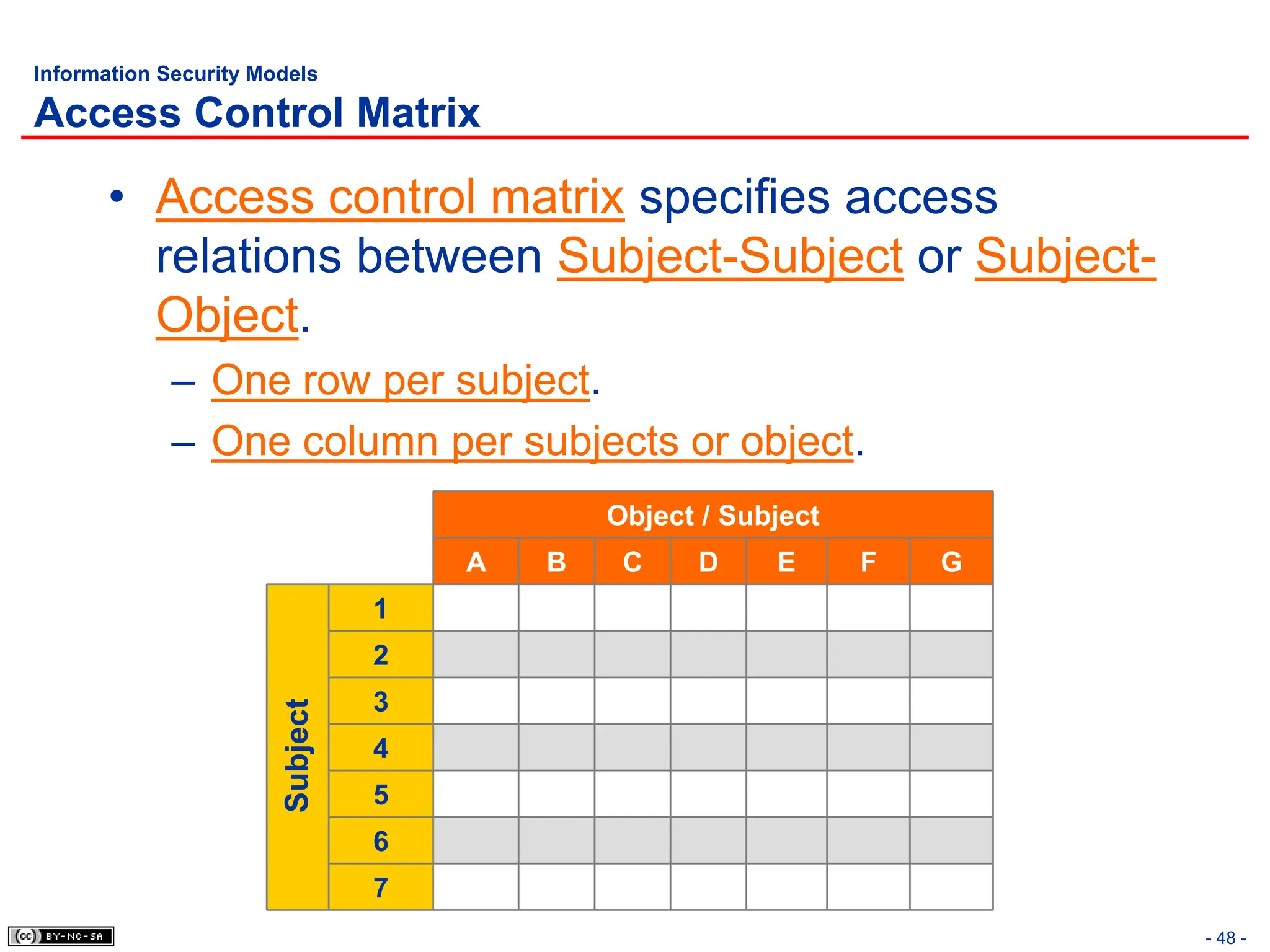
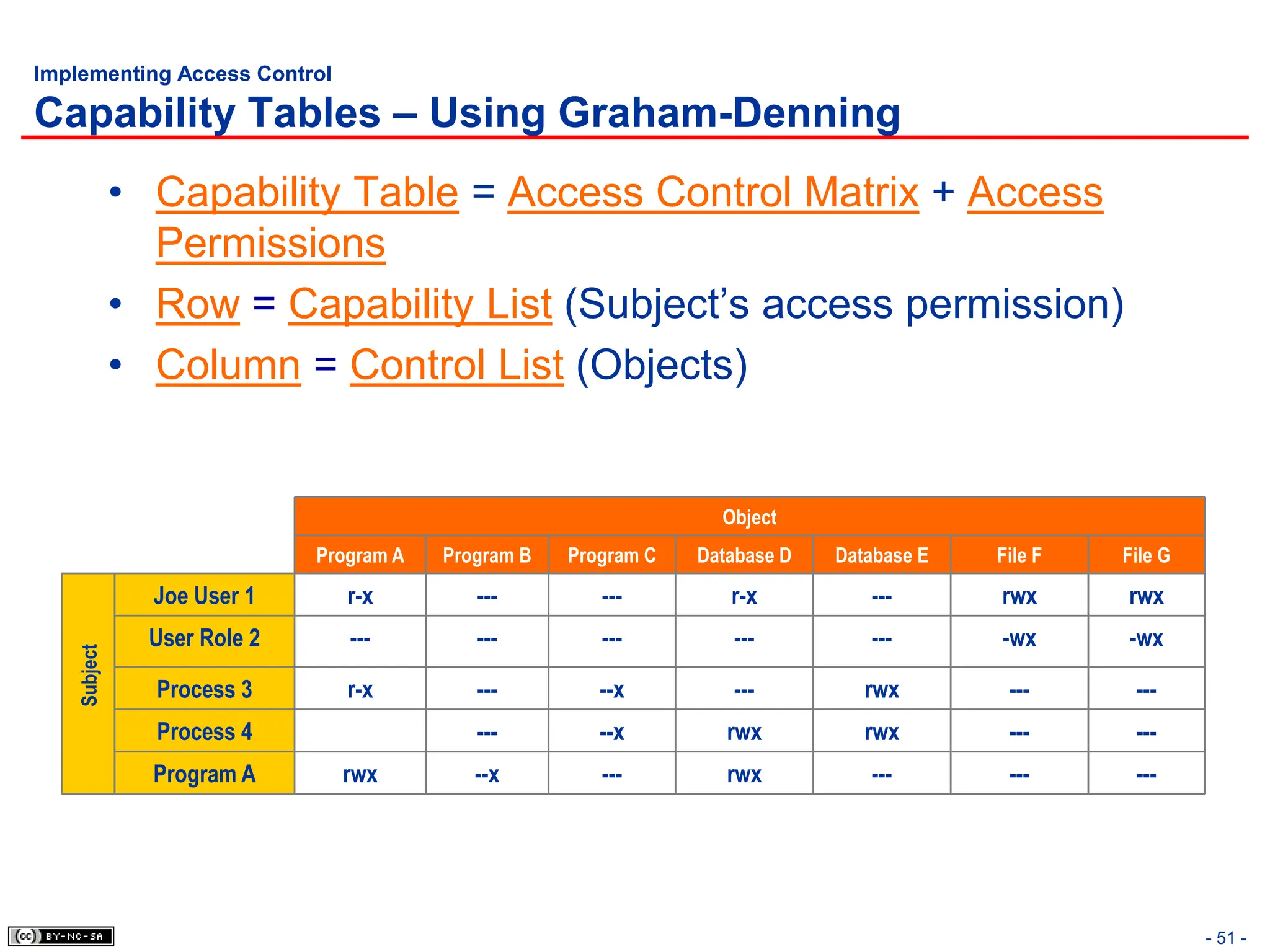
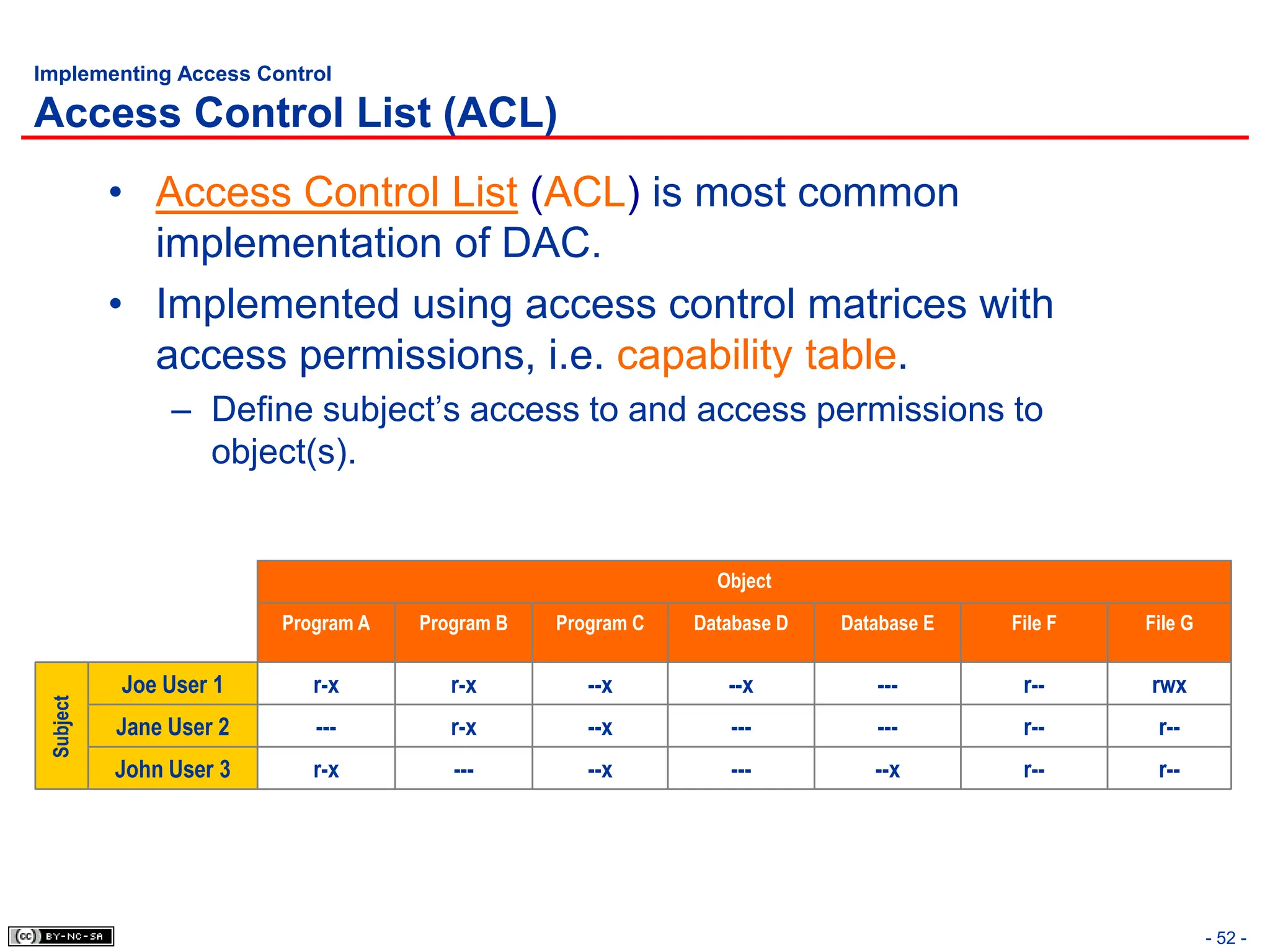
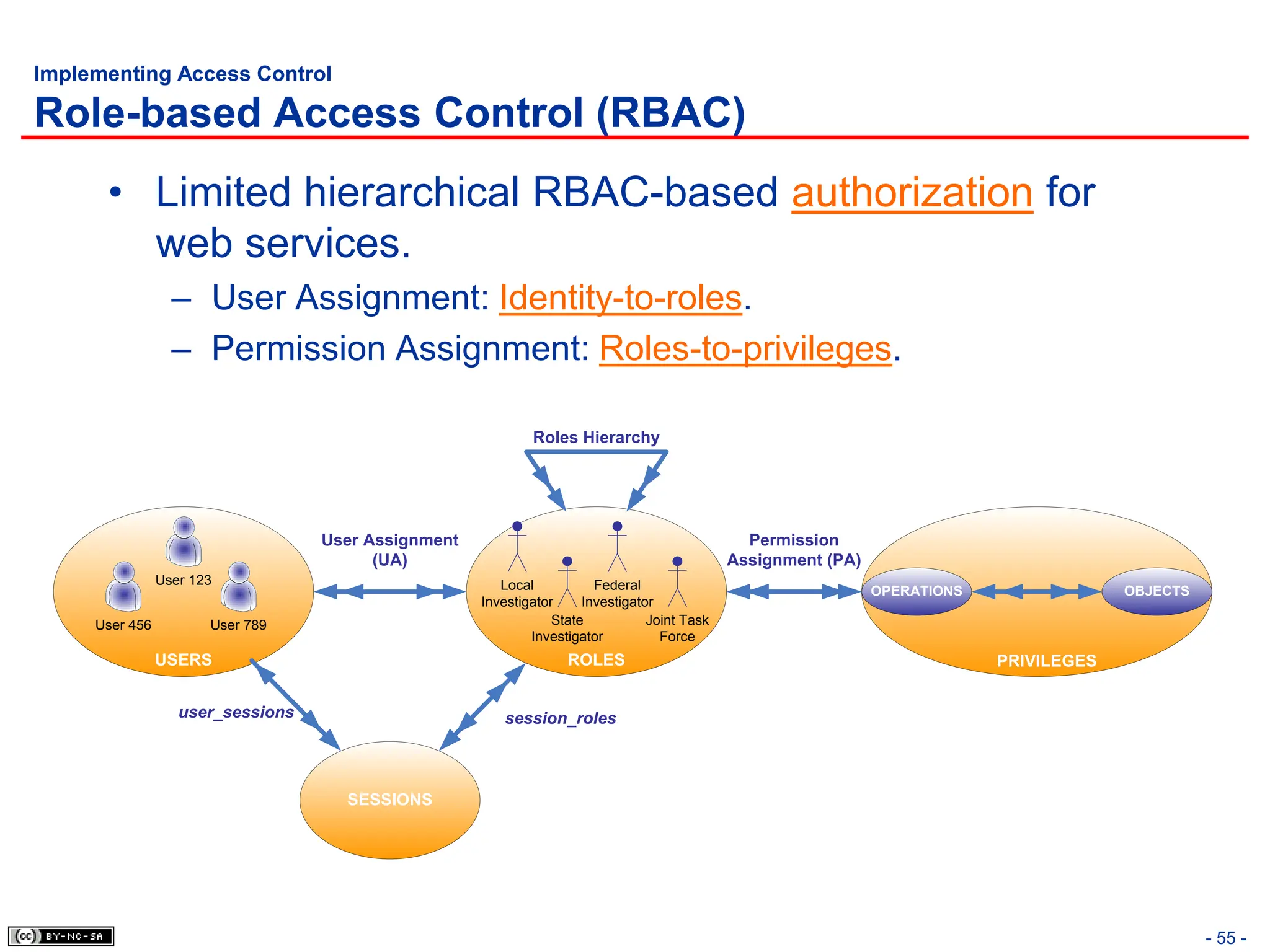
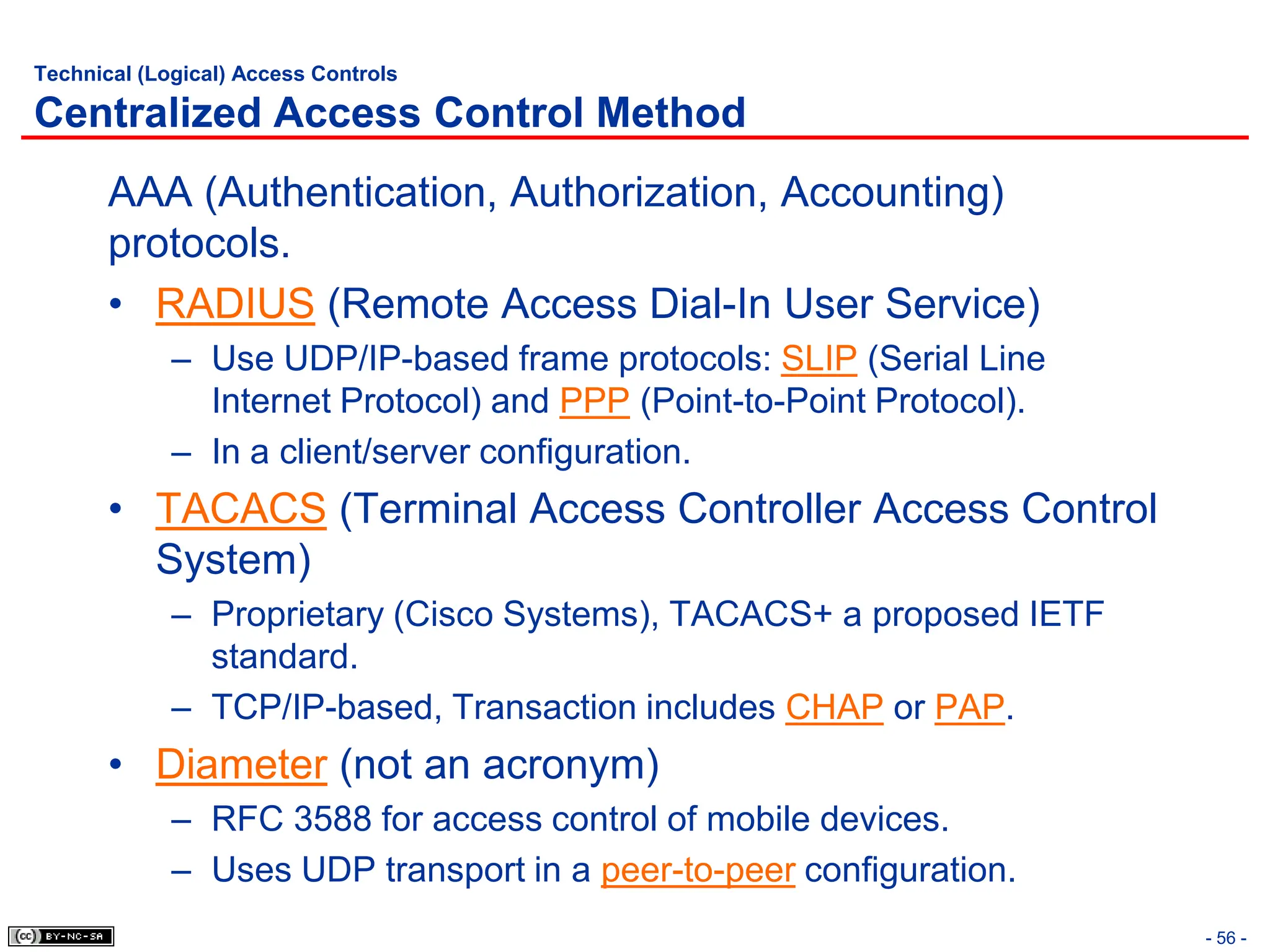
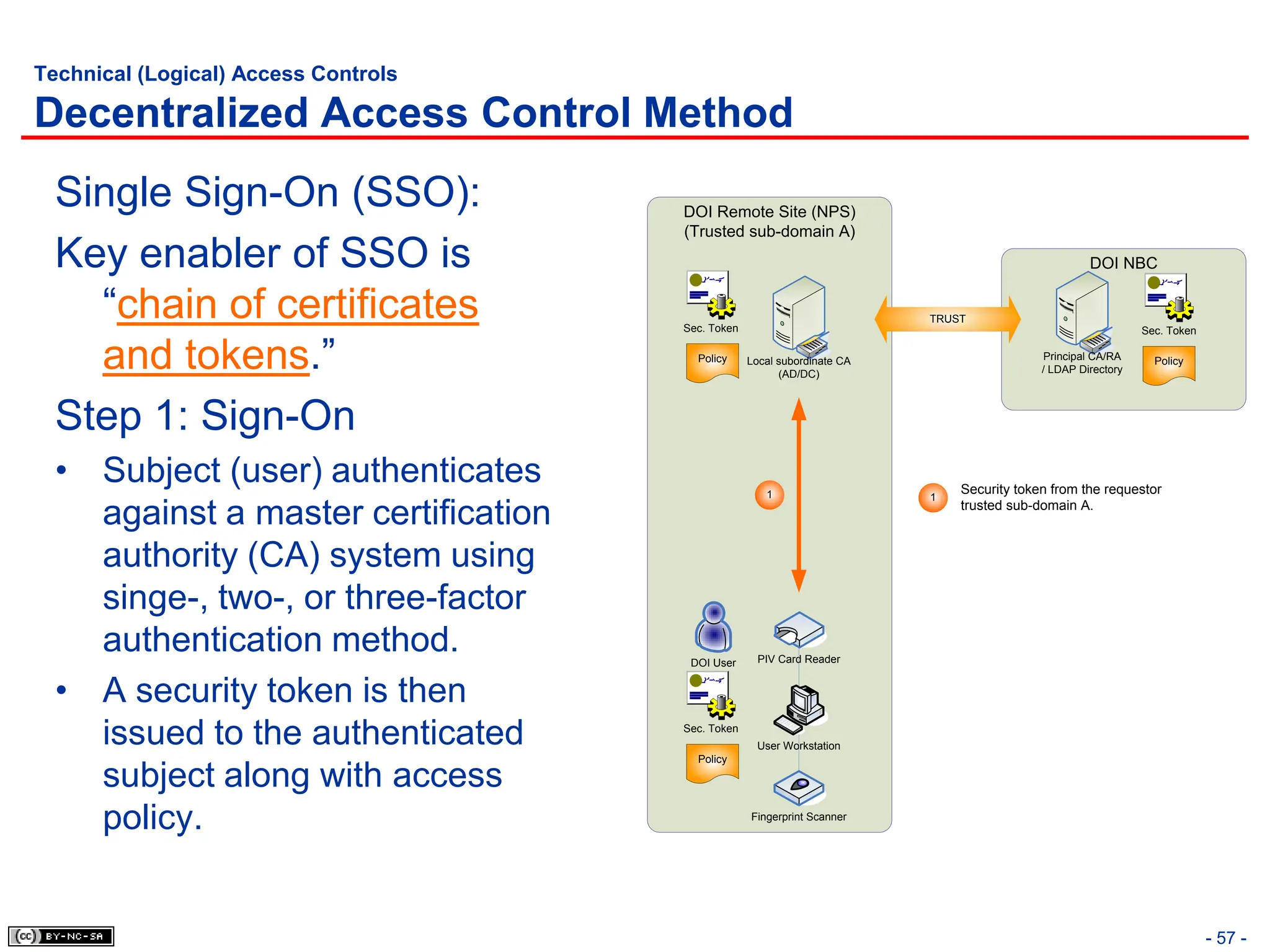
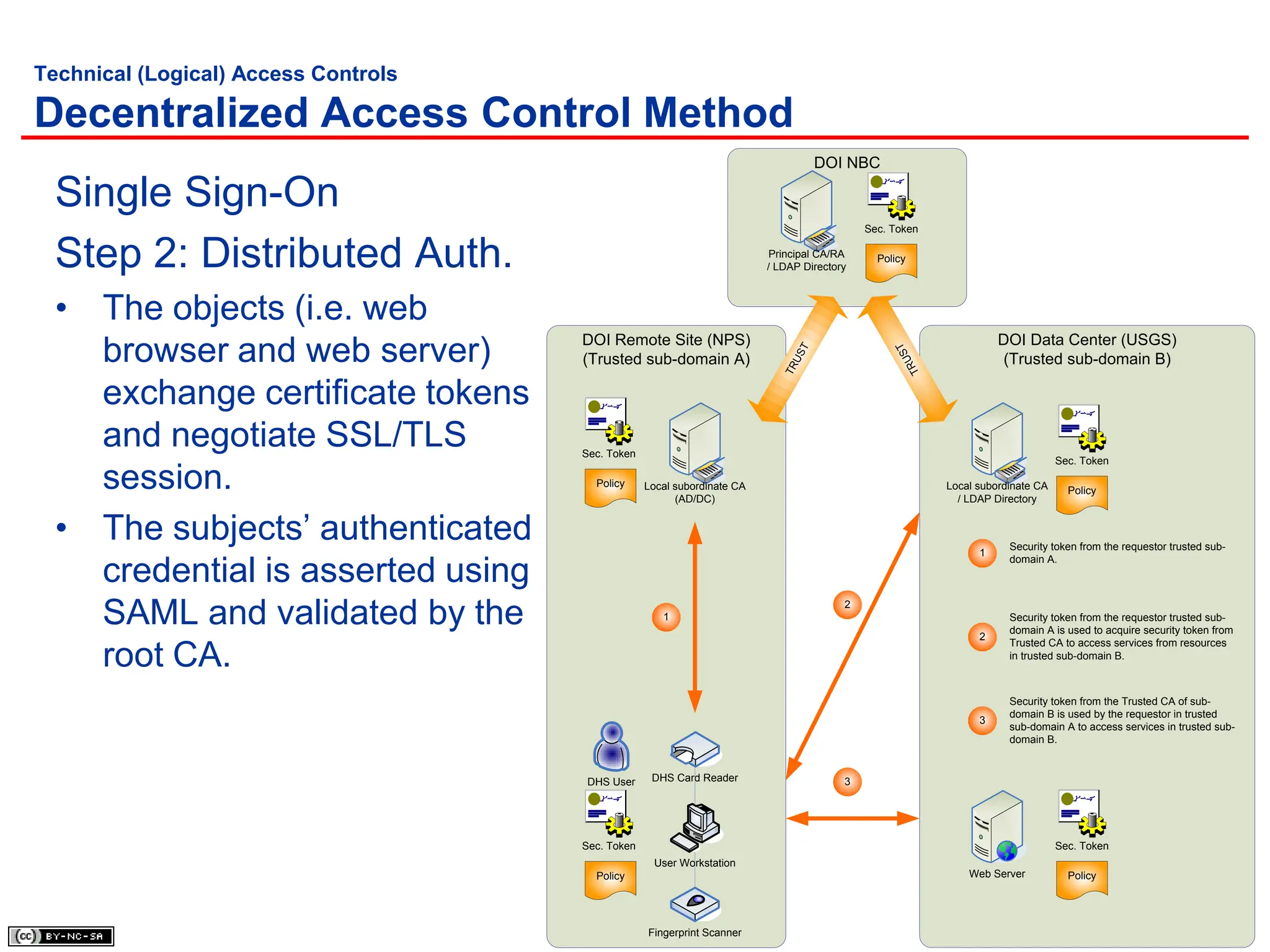
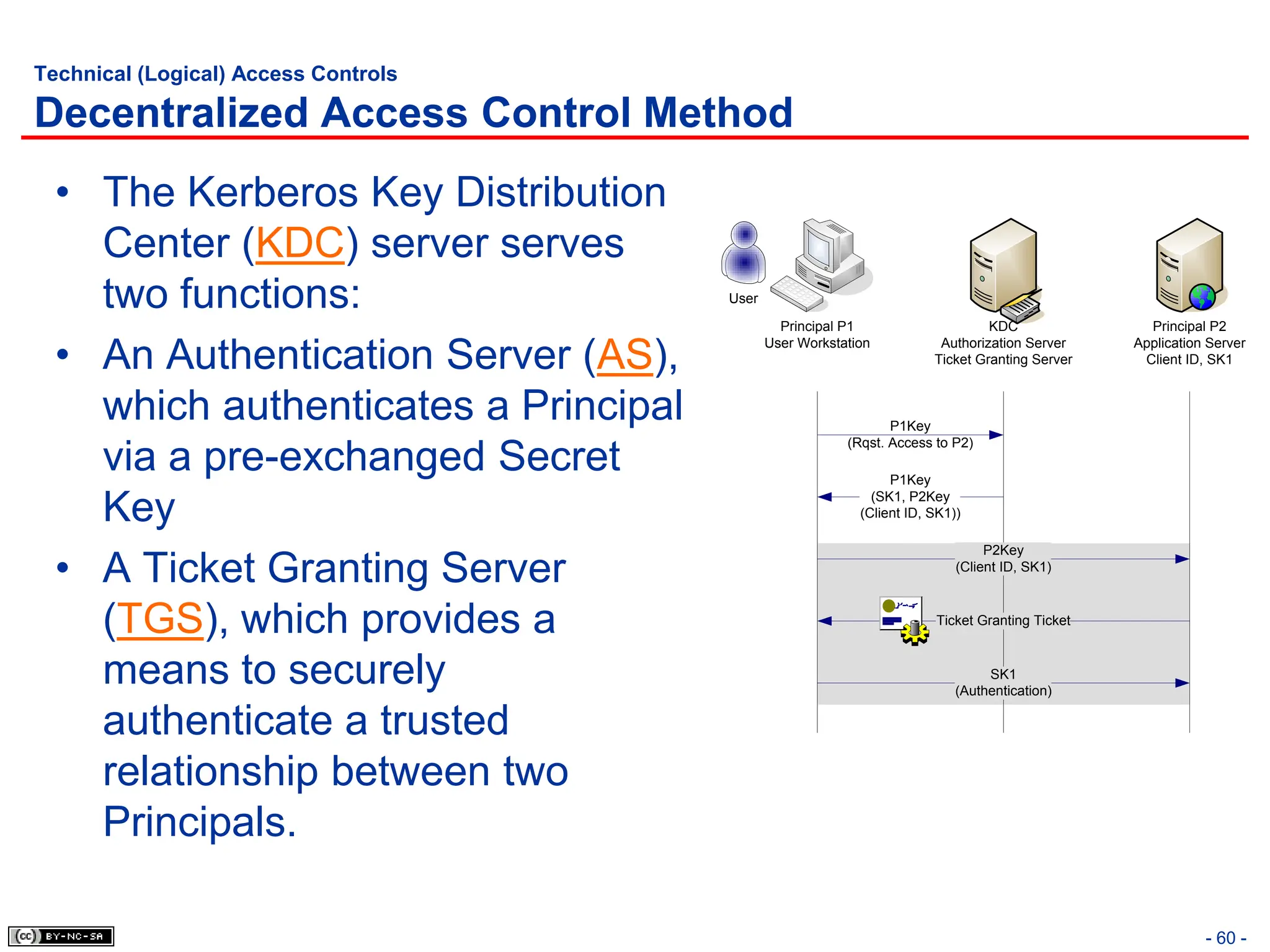
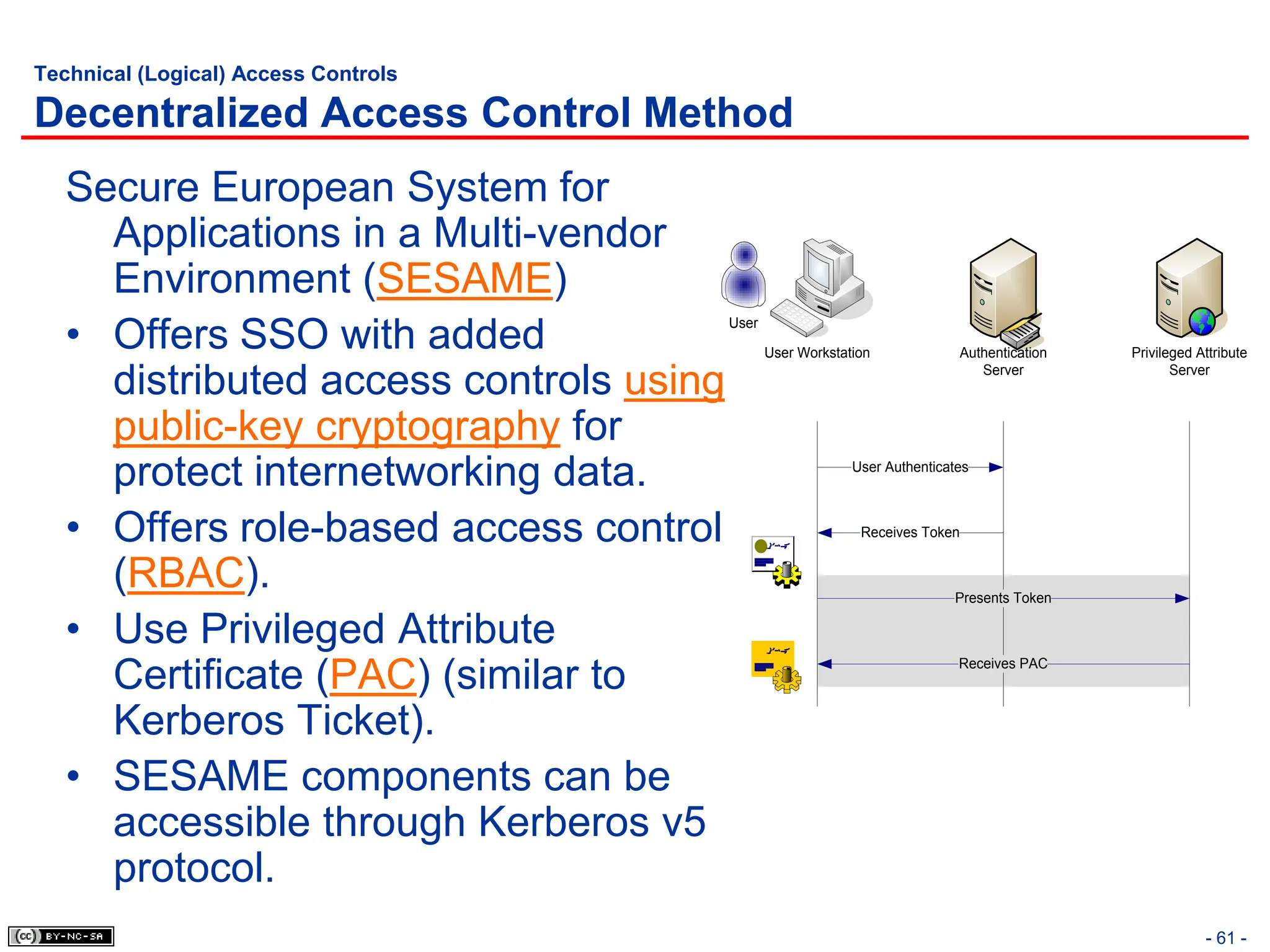
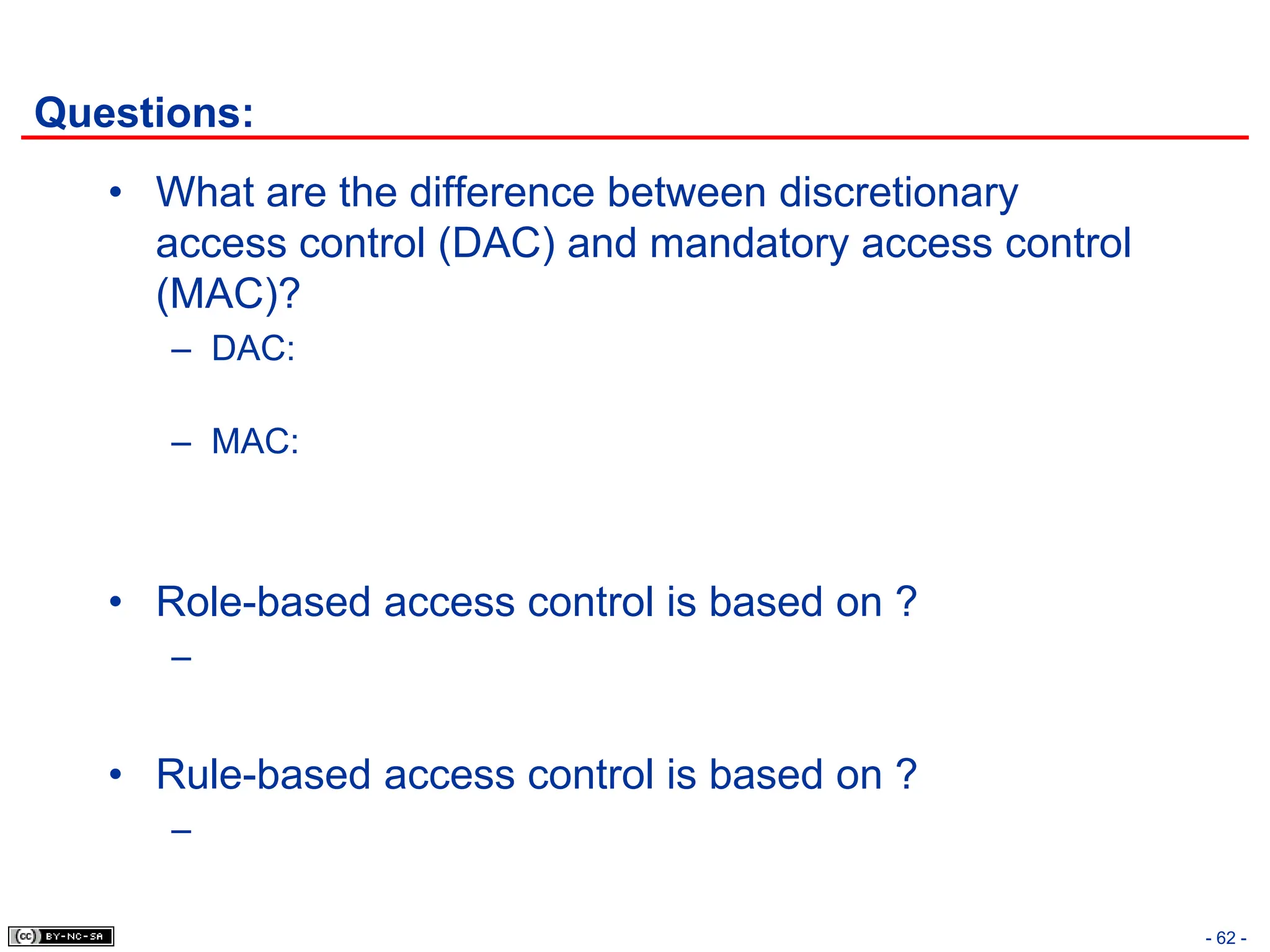
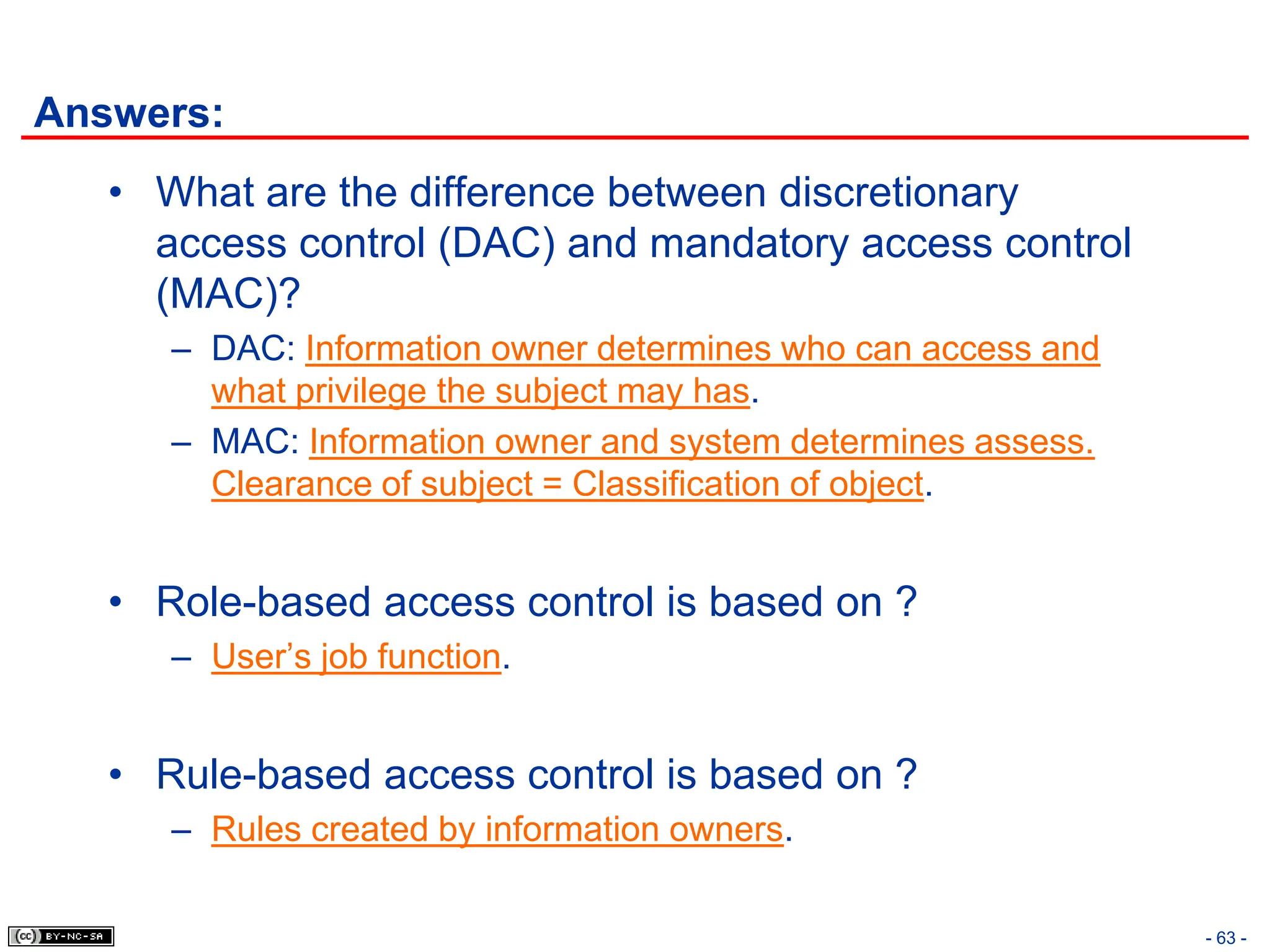
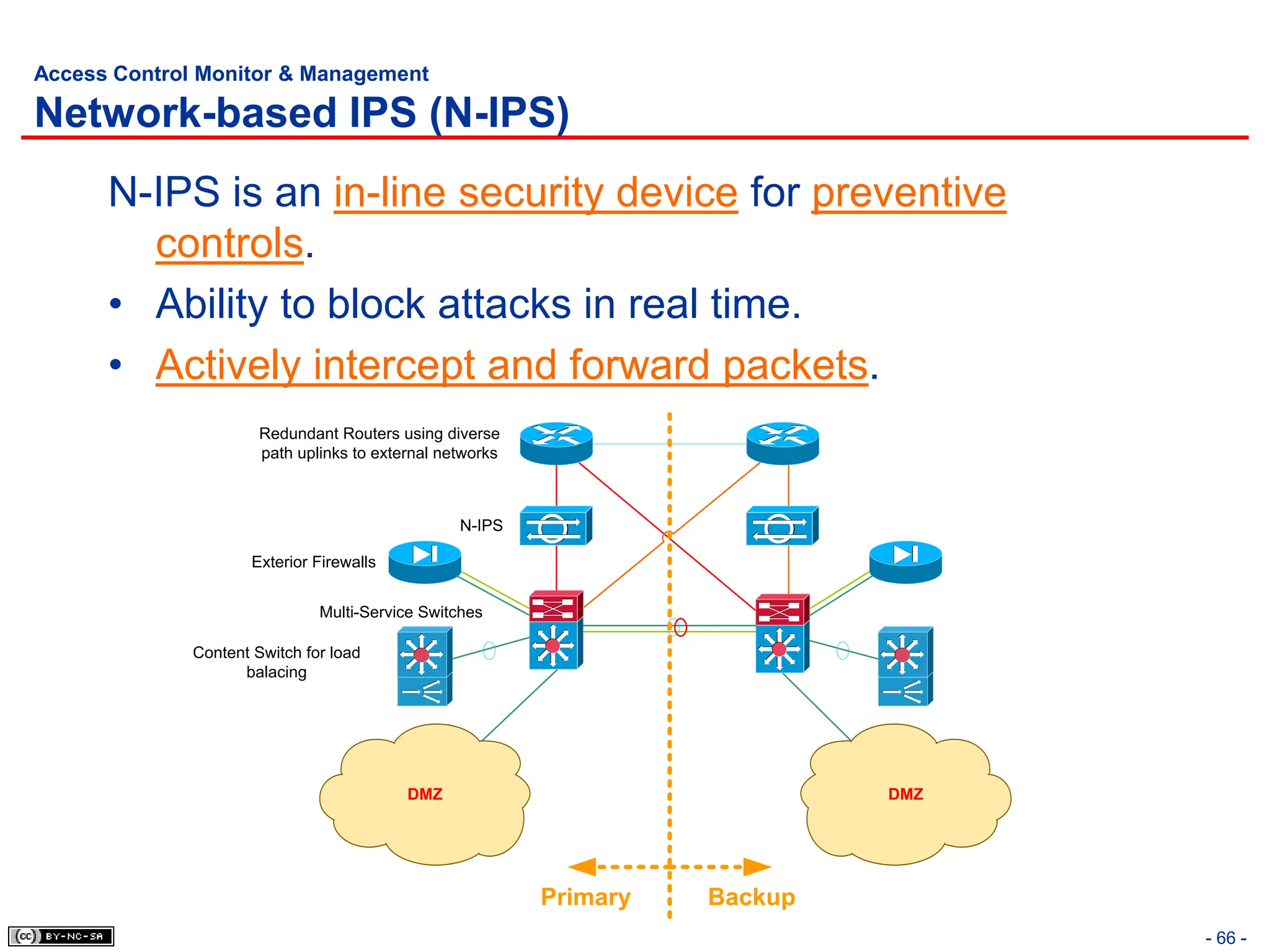
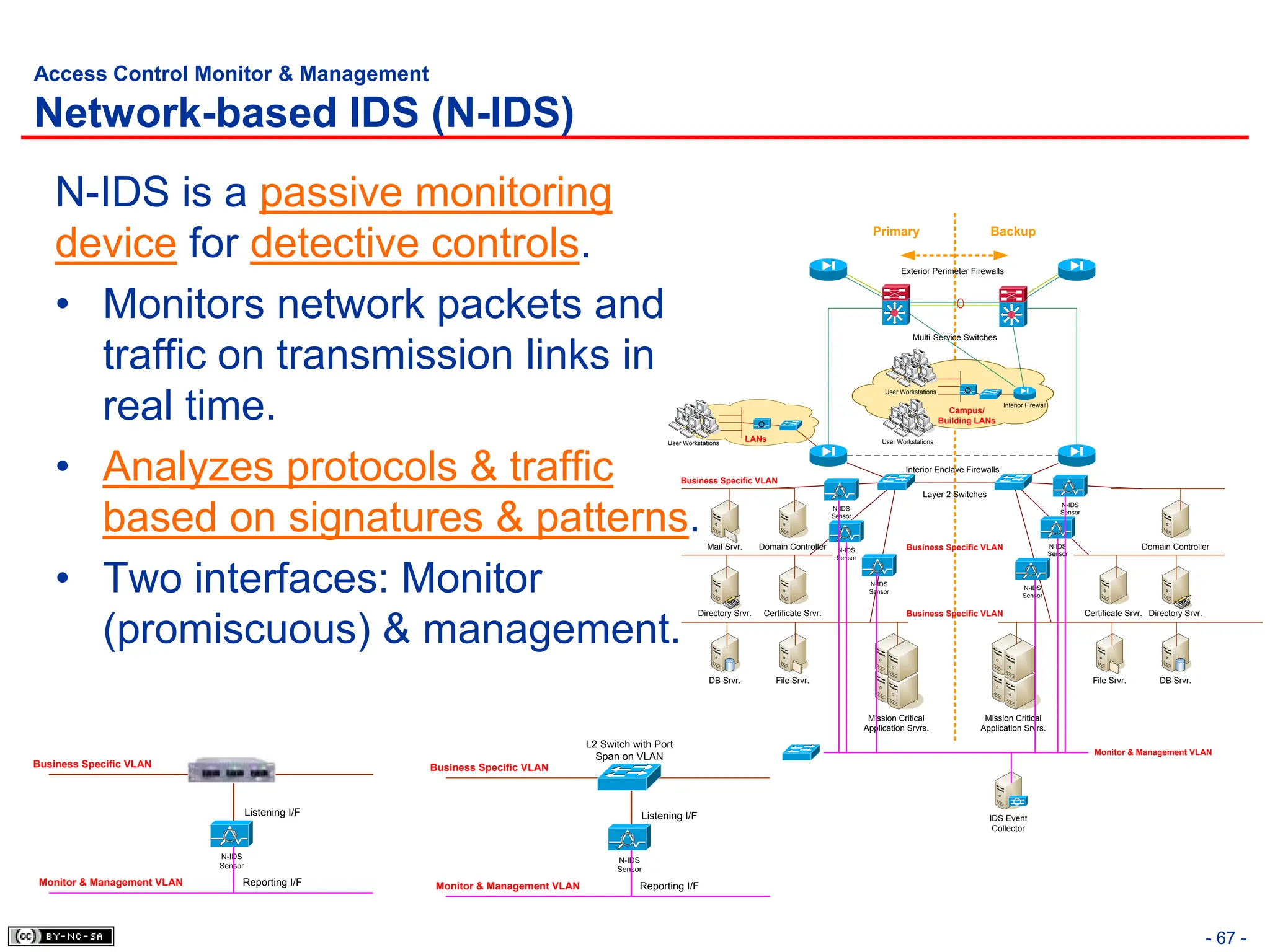
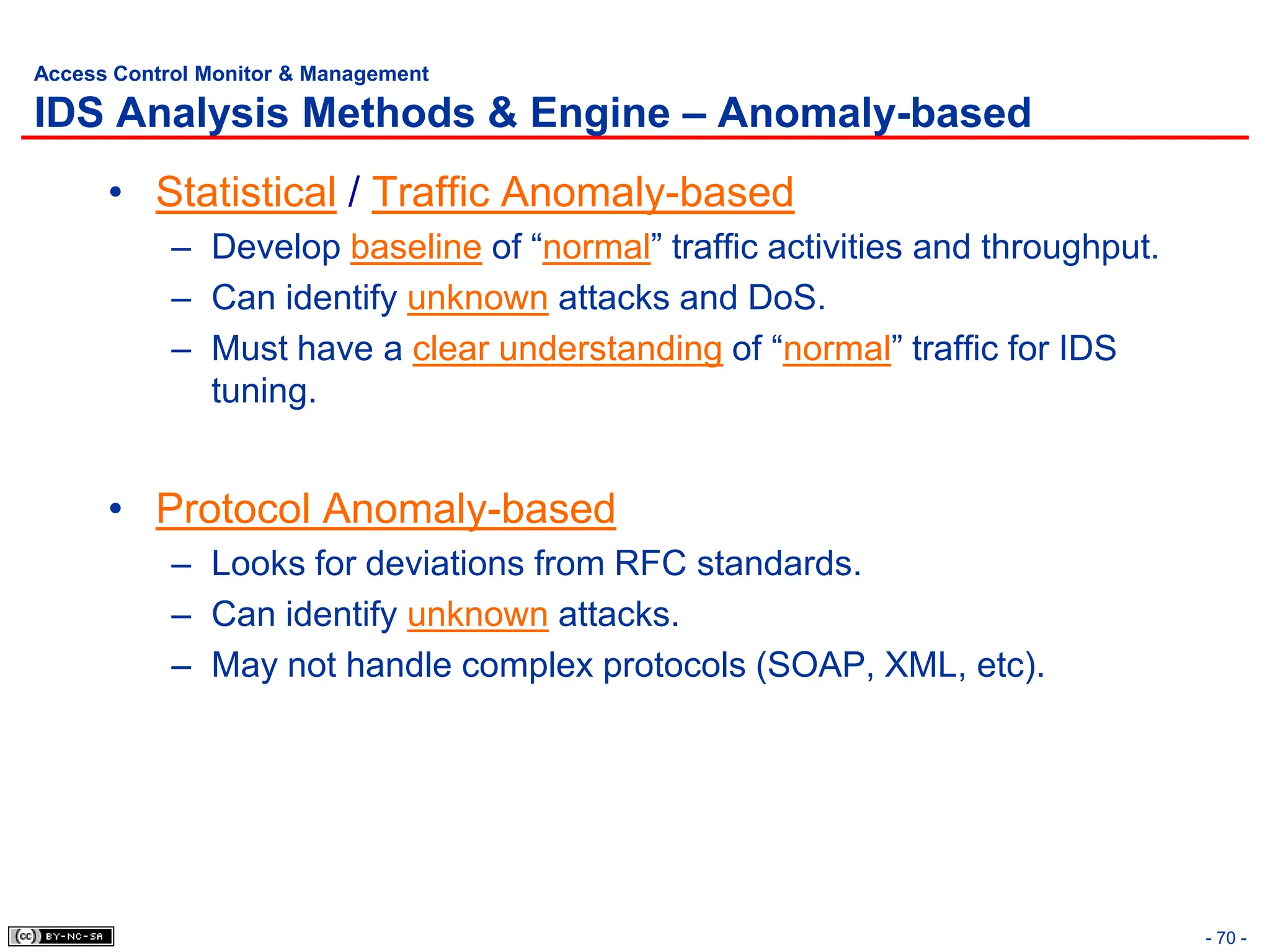
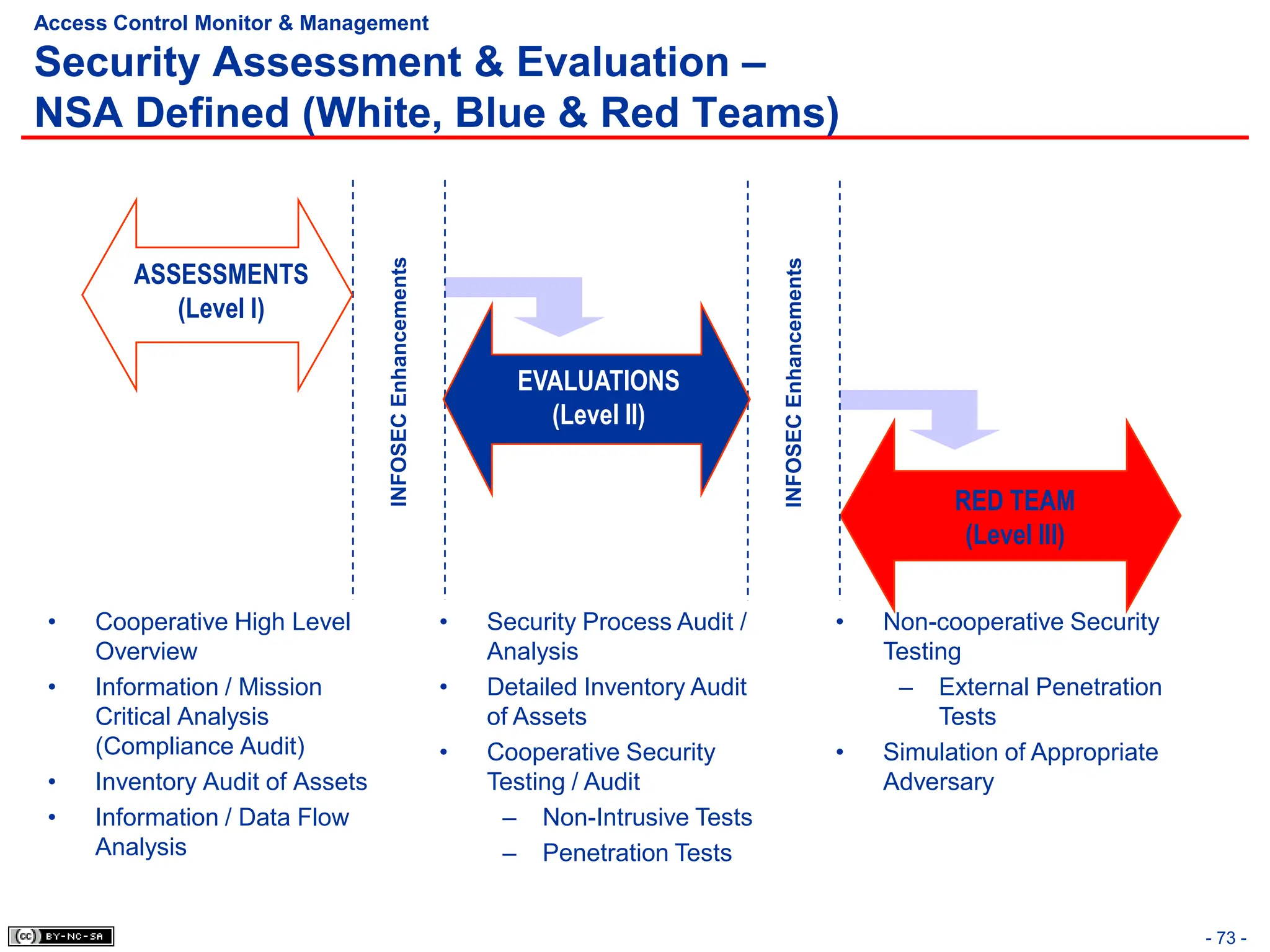
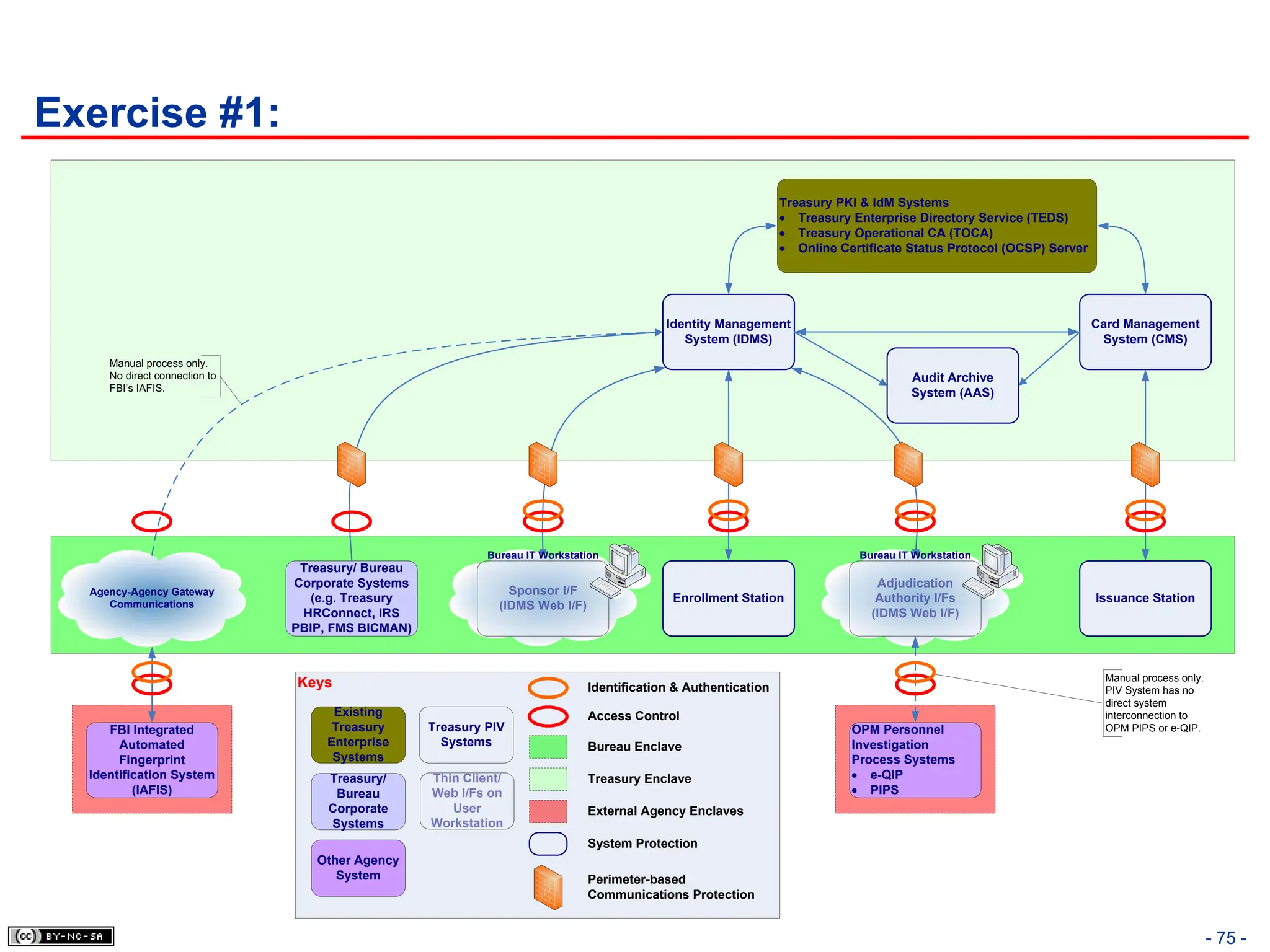
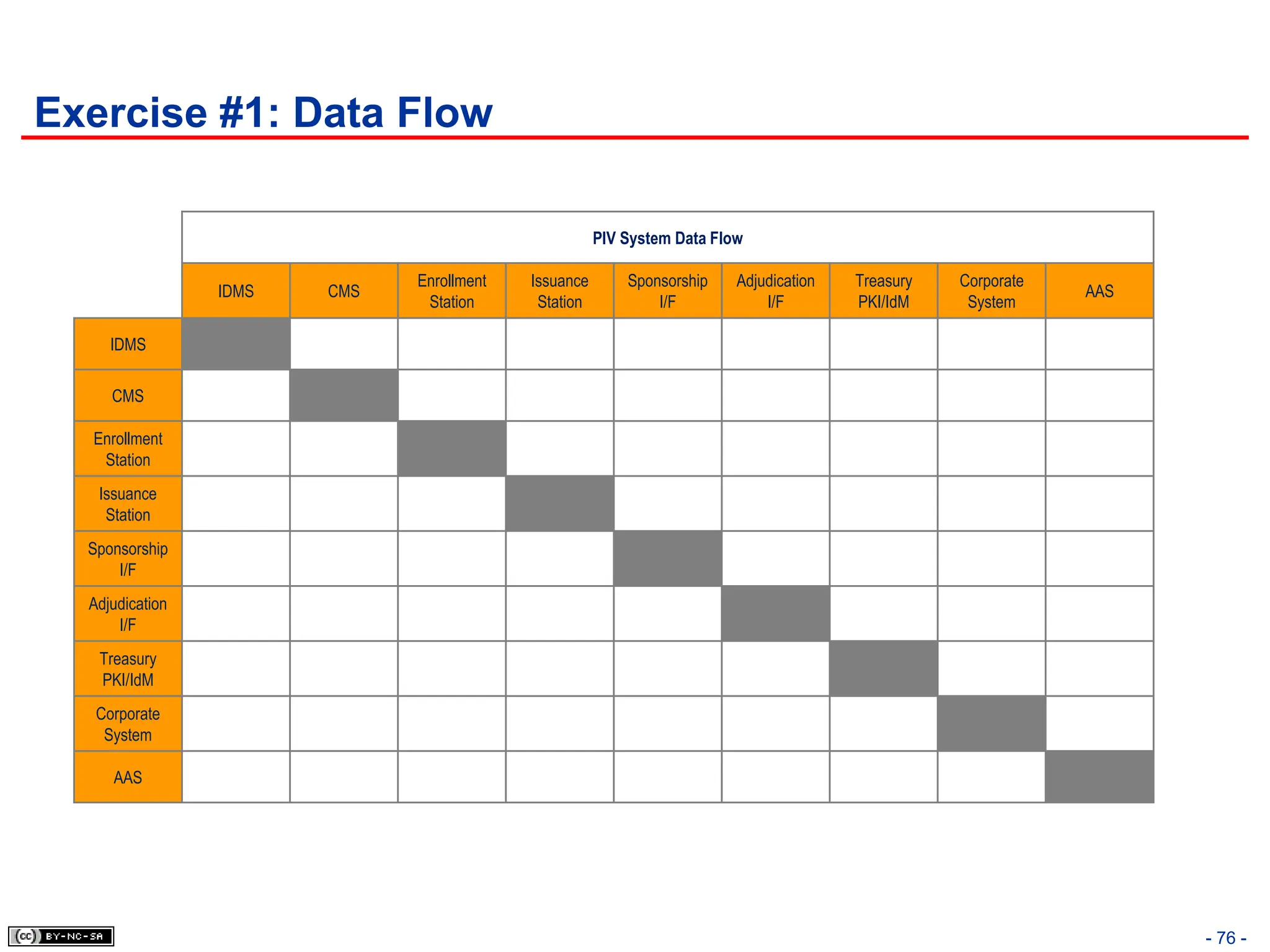
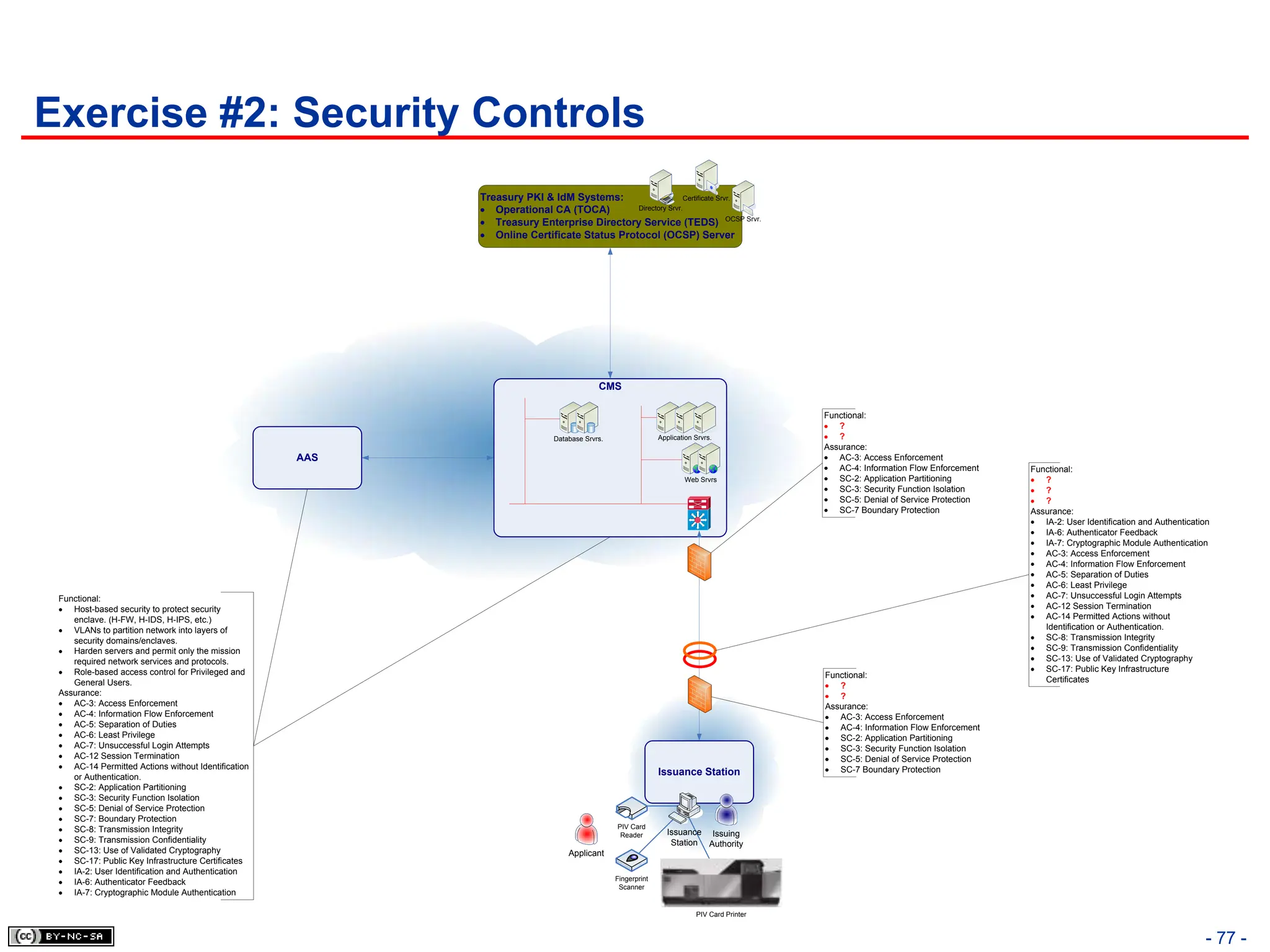
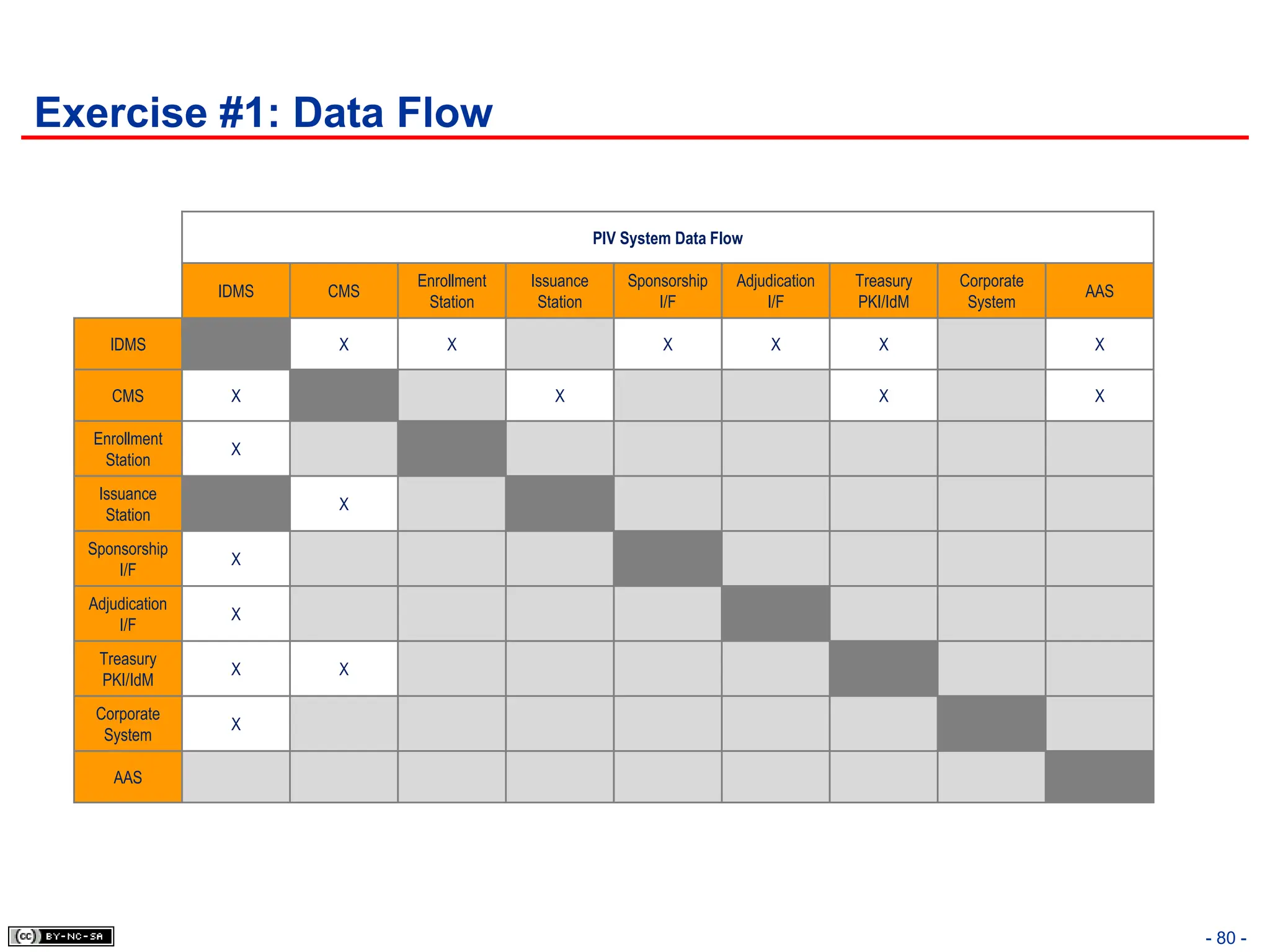
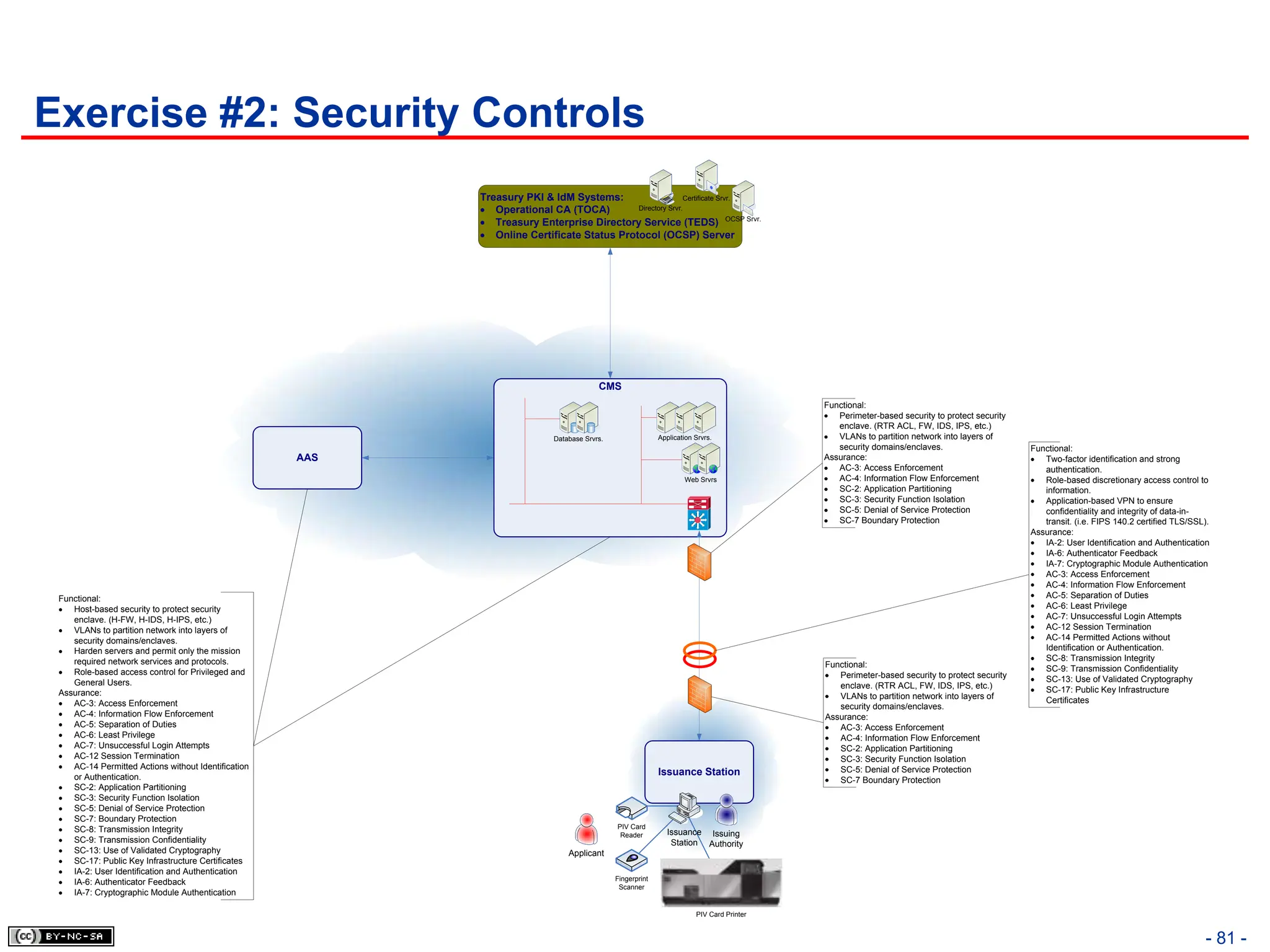
The document, 'CISSP Common Body of Knowledge Review' by Alfred Ouyang, outlines key principles and mechanisms of access control in information systems, stressing the importance of security implementation principles like least privilege and separation of duties. It also discusses various types of access controls, classification of information, and threats to access control, providing insights into management, operational, and technical controls. Overall, it serves as a comprehensive guide for understanding and implementing effective access control strategies within organizations.