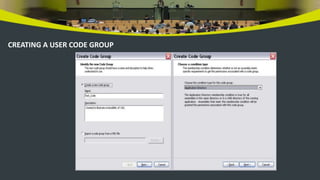
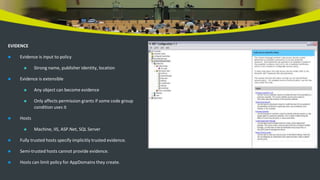
The document discusses code access security and evidence-based security models in .NET. It covers basic security concepts like authentication, authorization, and threats. It then describes how .NET uses evidence like strong names and publishers to determine the permissions granted to assemblies based on policy levels and code groups. The .NET configuration tools allow editing and creating custom permissions and code groups.