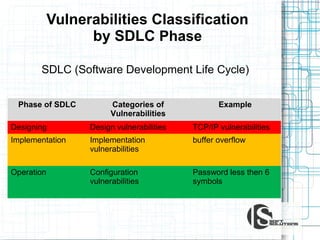
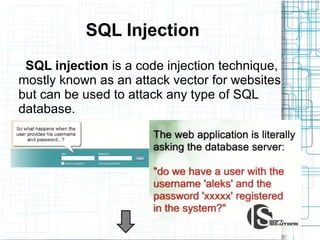
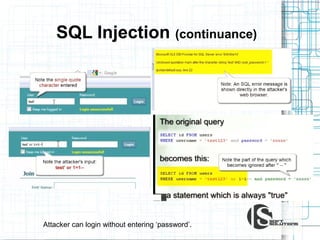
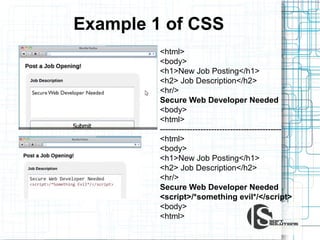
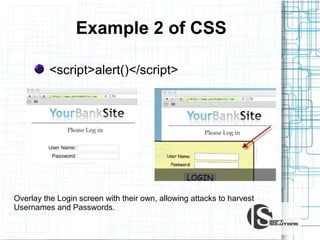
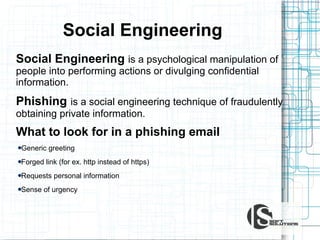
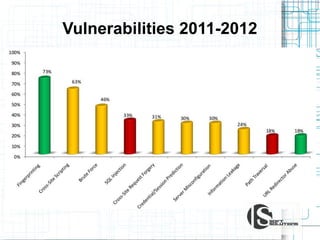
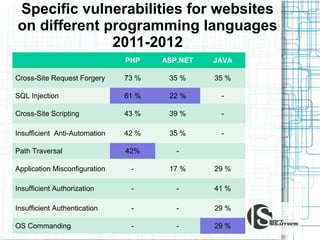
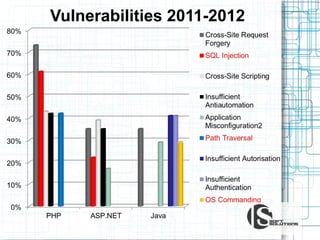
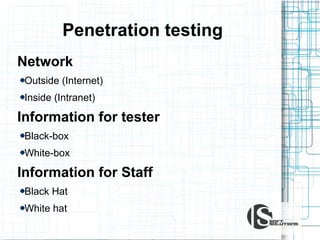
This document discusses the importance of security testing. It defines key security concepts like confidentiality, integrity, and availability. It describes common security testing methods like vulnerability scanning and penetration testing. It also provides examples of specific vulnerabilities like SQL injection, cross-site scripting, and social engineering attacks. The document seeks to demonstrate why organizations should invest in security testing now rather than just responding to attacks after they occur.