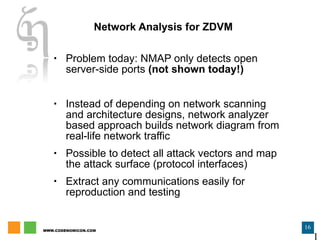
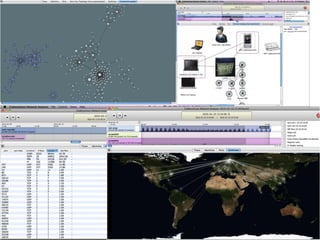
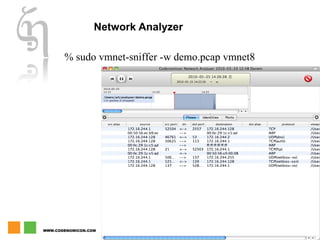
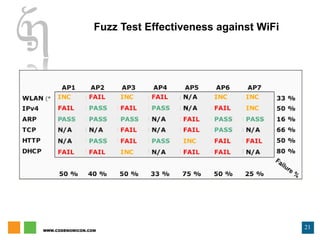
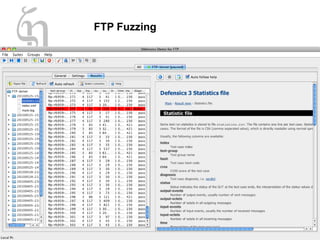
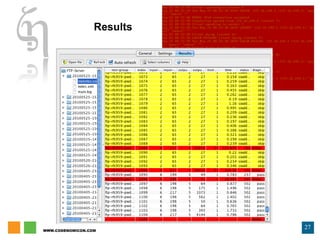
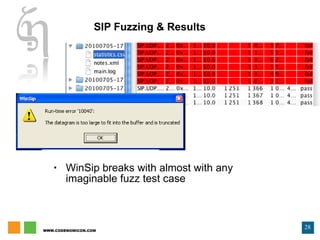
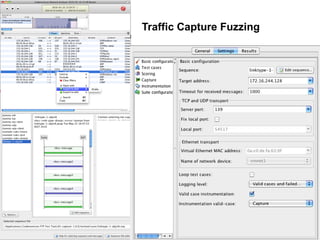
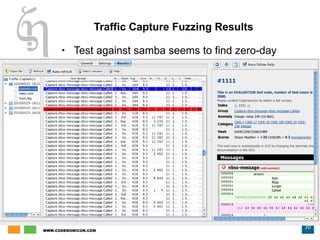
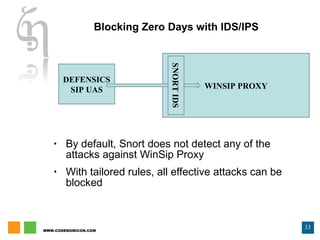
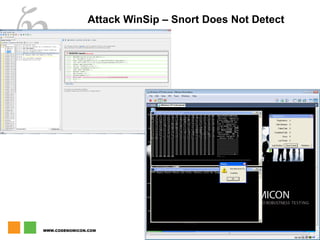
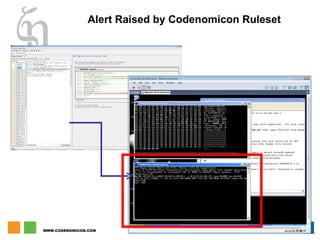
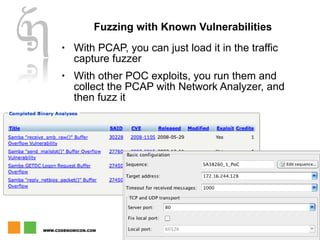
The document discusses zero day vulnerability management, emphasizing the need for proactive security measures and effective fuzzing techniques for detecting and remediating vulnerabilities. It details the fuzzing process, including types of fuzzing methodologies, and the importance of mapping the attack surface and testing against known vulnerabilities. Additionally, it highlights the challenges in vulnerability management and the significance of continuous monitoring and tailored intrusion detection systems.


















![PROACTIVE SECURITY AND ROBUSTNESS SOLUTIONS THANK YOU – QUESTIONS? “ Thrill to the excitement of the chase! Stalk bugs with care, methodology, and reason. Build traps for them. .... Testers! Break that software (as you must) and drive it to the ultimate - but don’t enjoy the programmer’s pain.” [from Boris Beizer]](https://image.slidesharecdn.com/zero-day-management-webinar-100716004610-phpapp01/85/Fuzzing-101-Webinar-on-Zero-Day-Management-43-320.jpg)