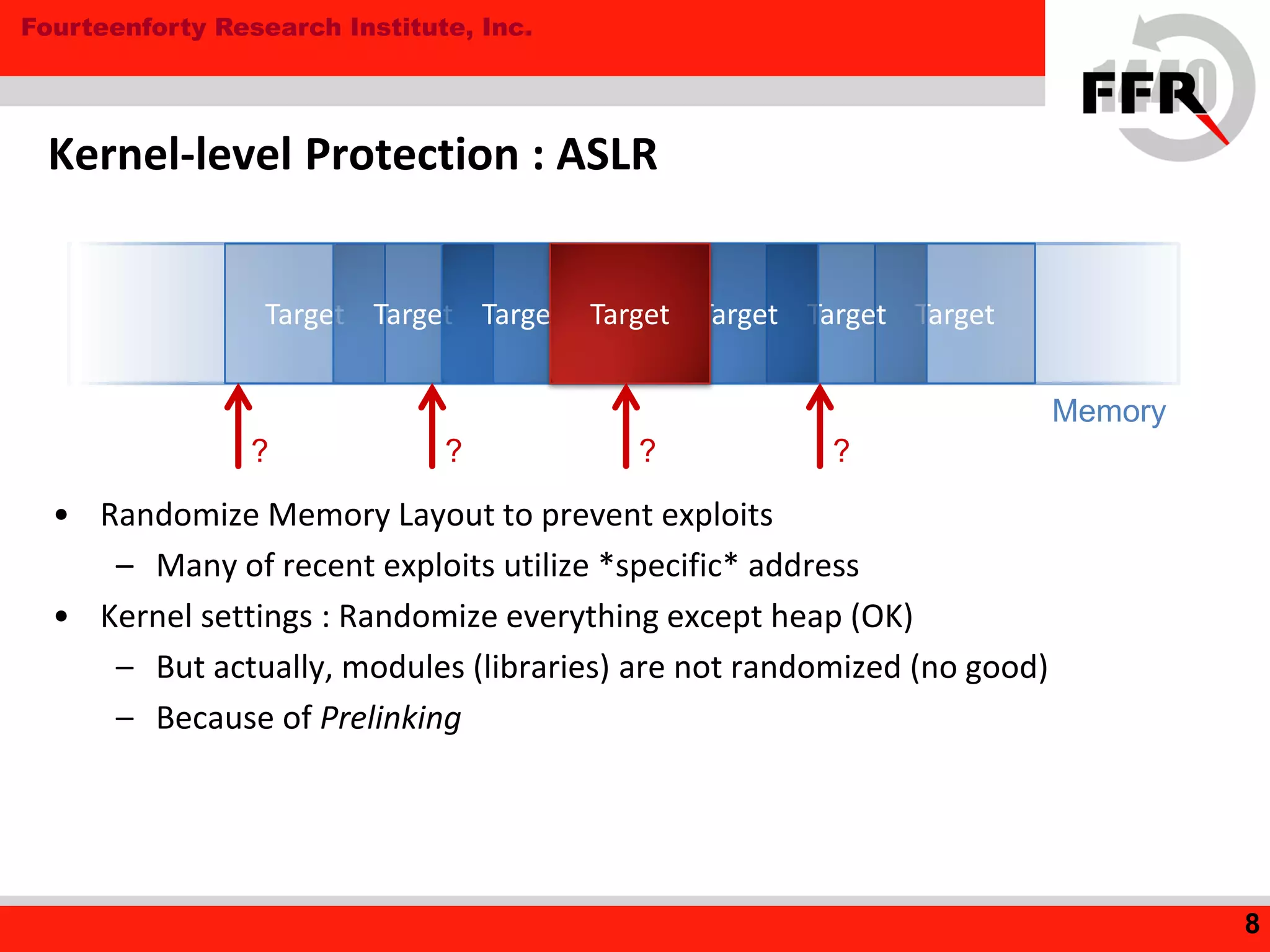
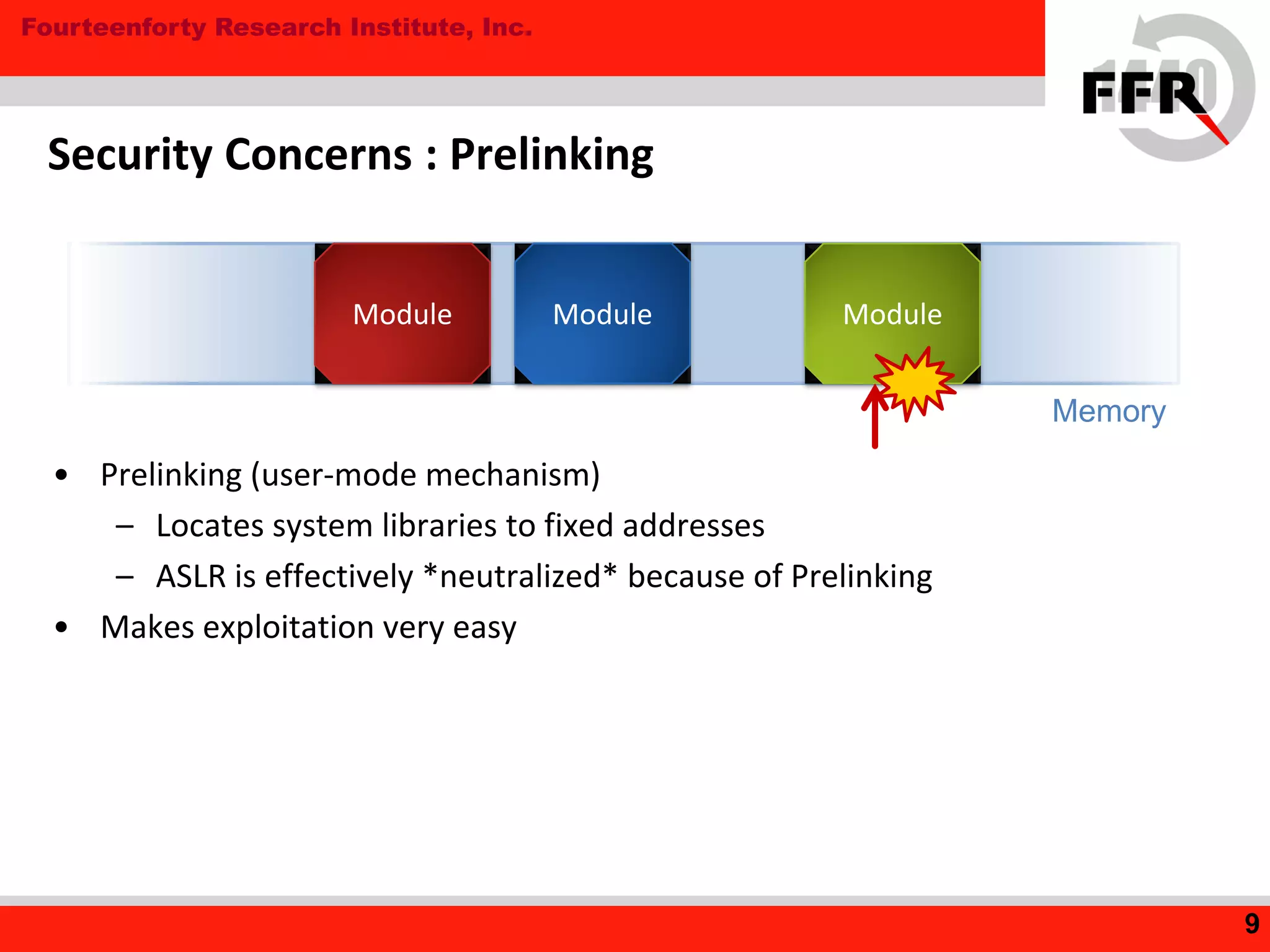
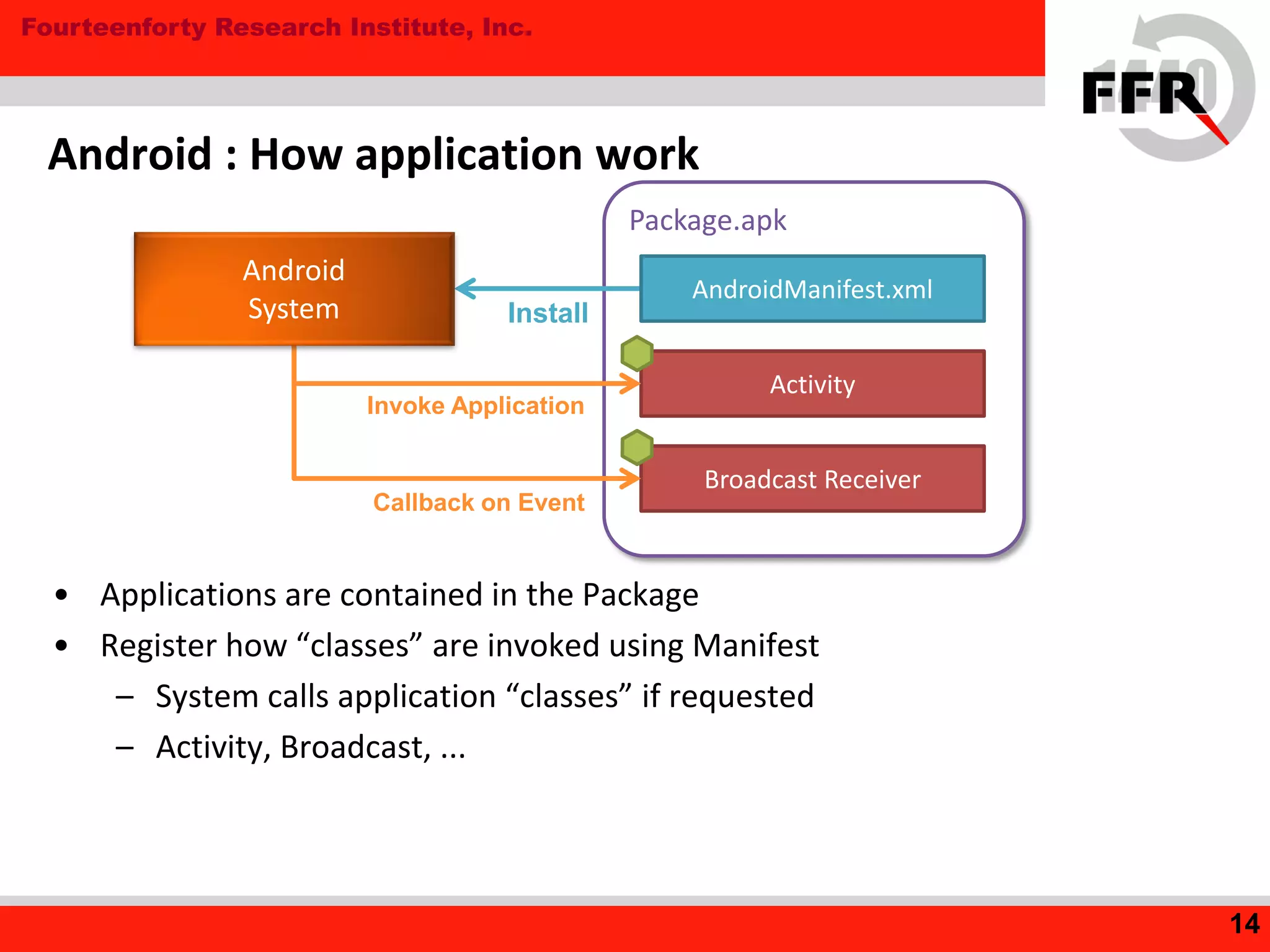
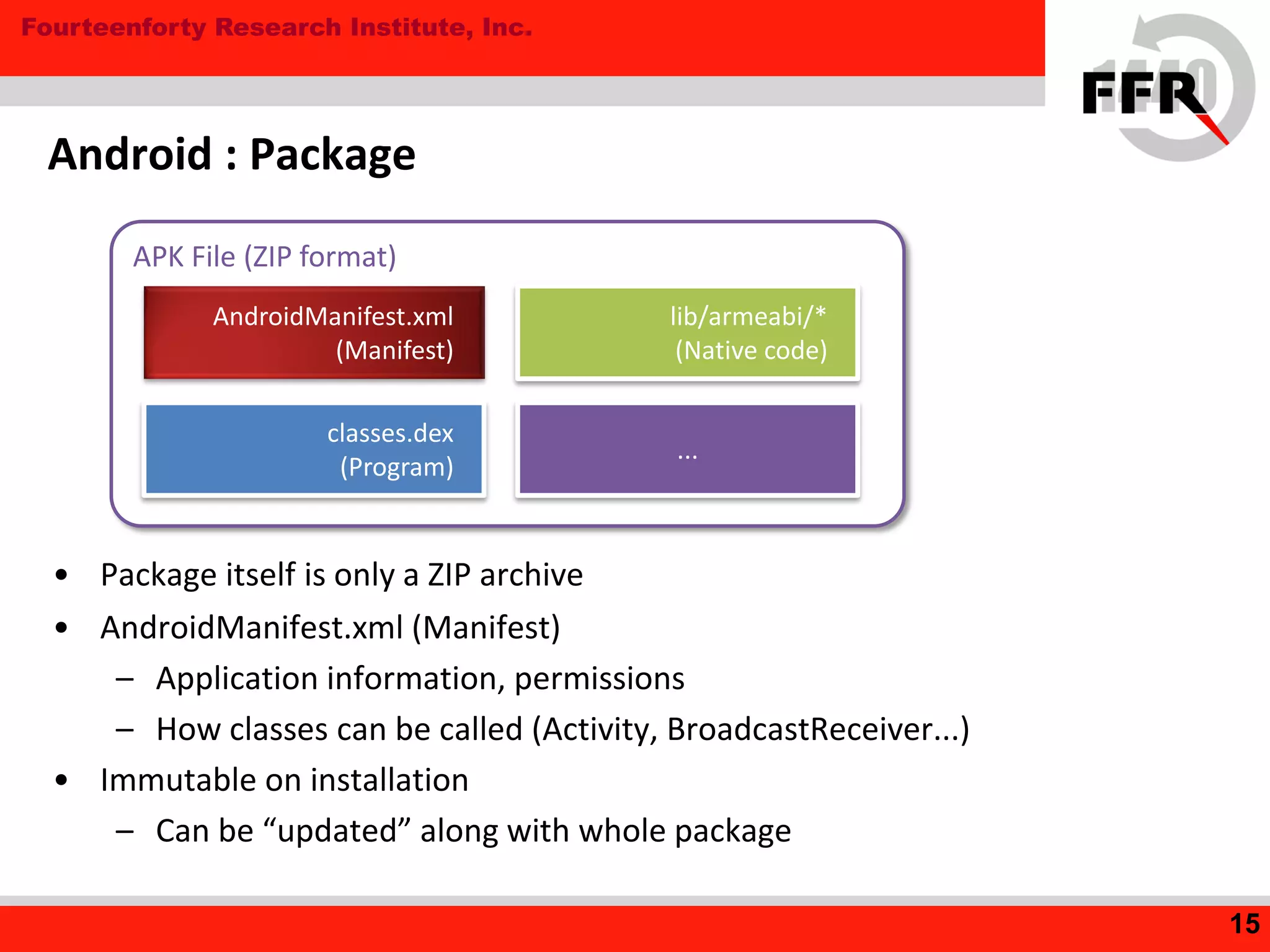
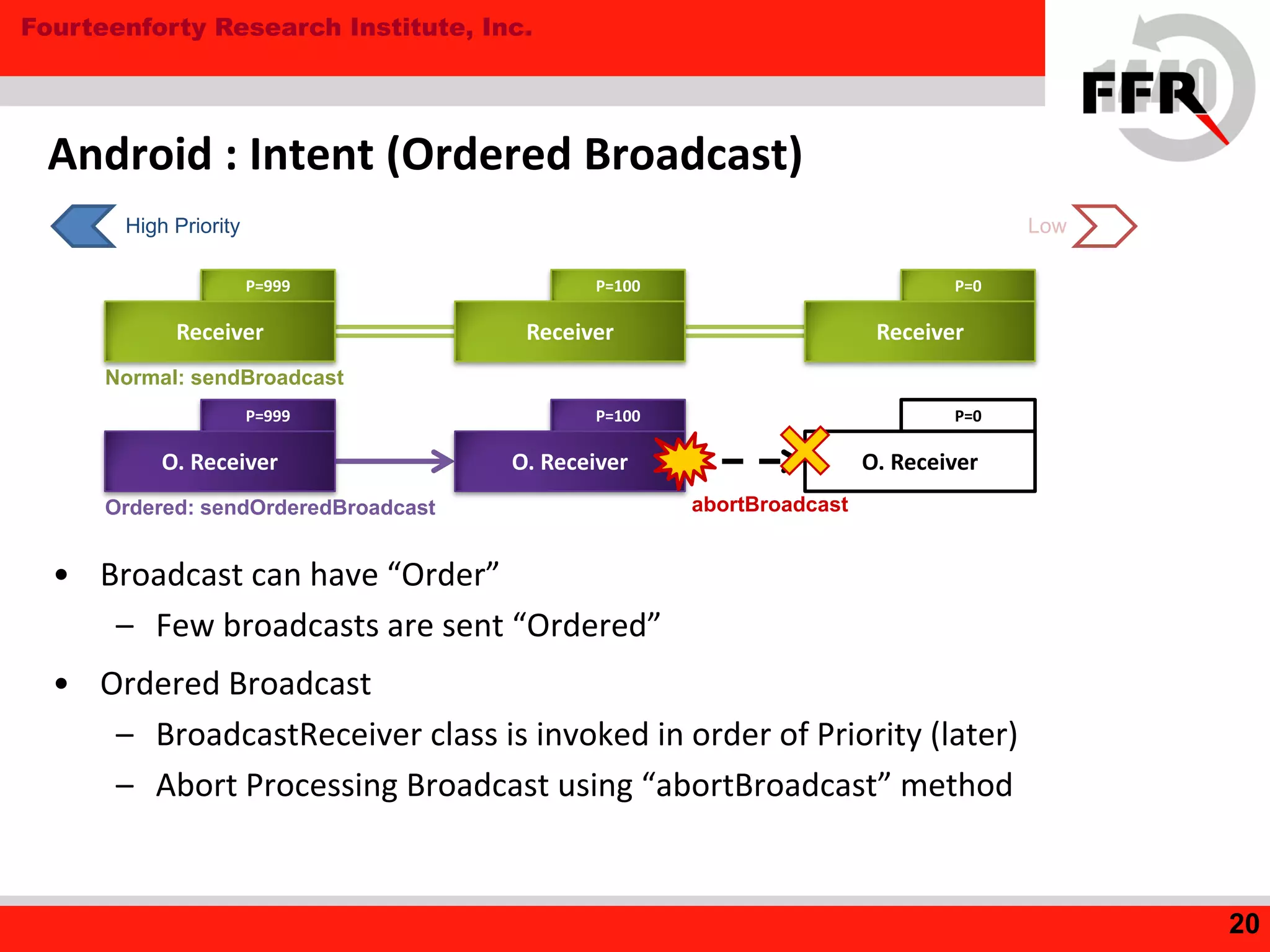
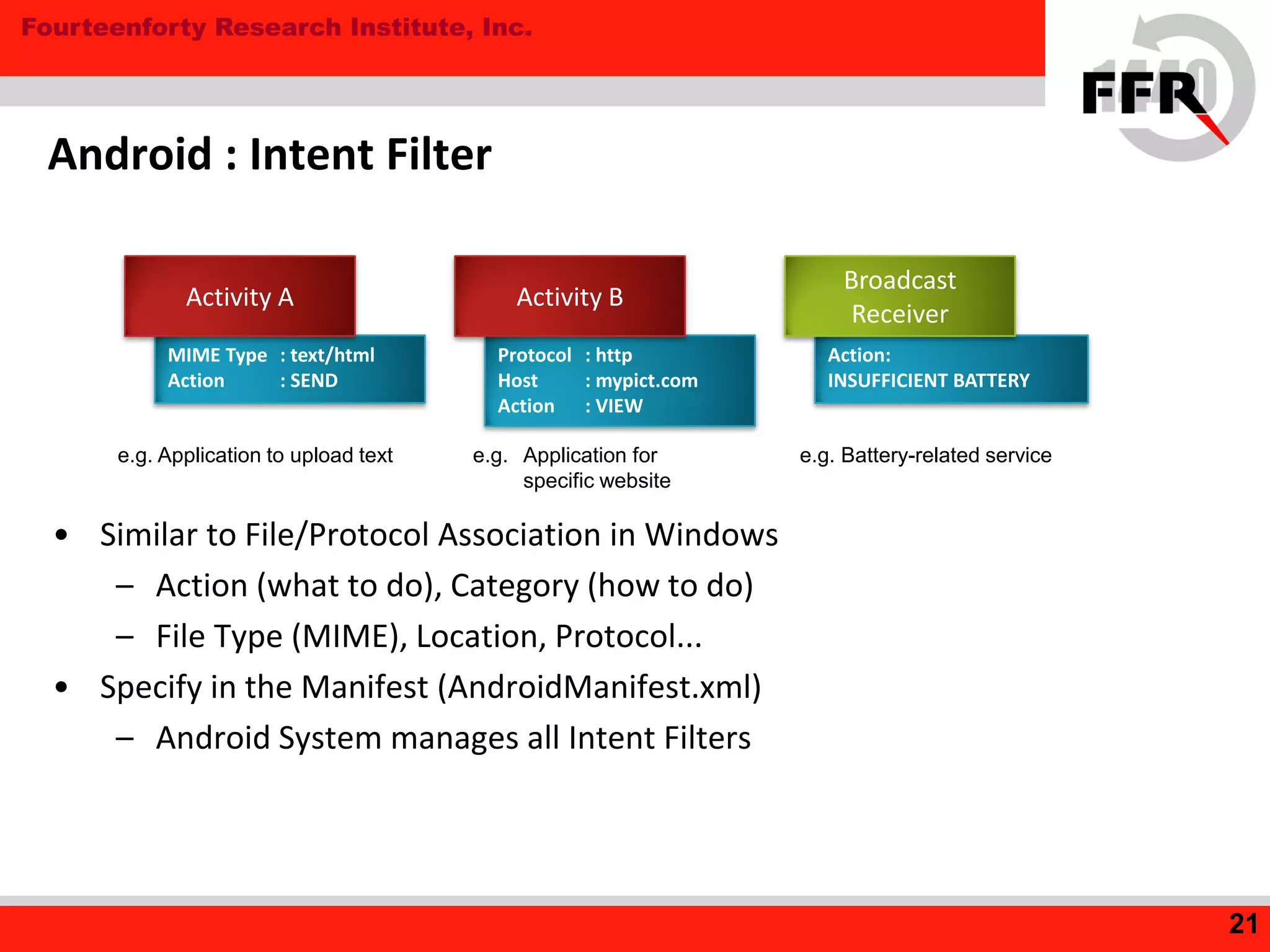
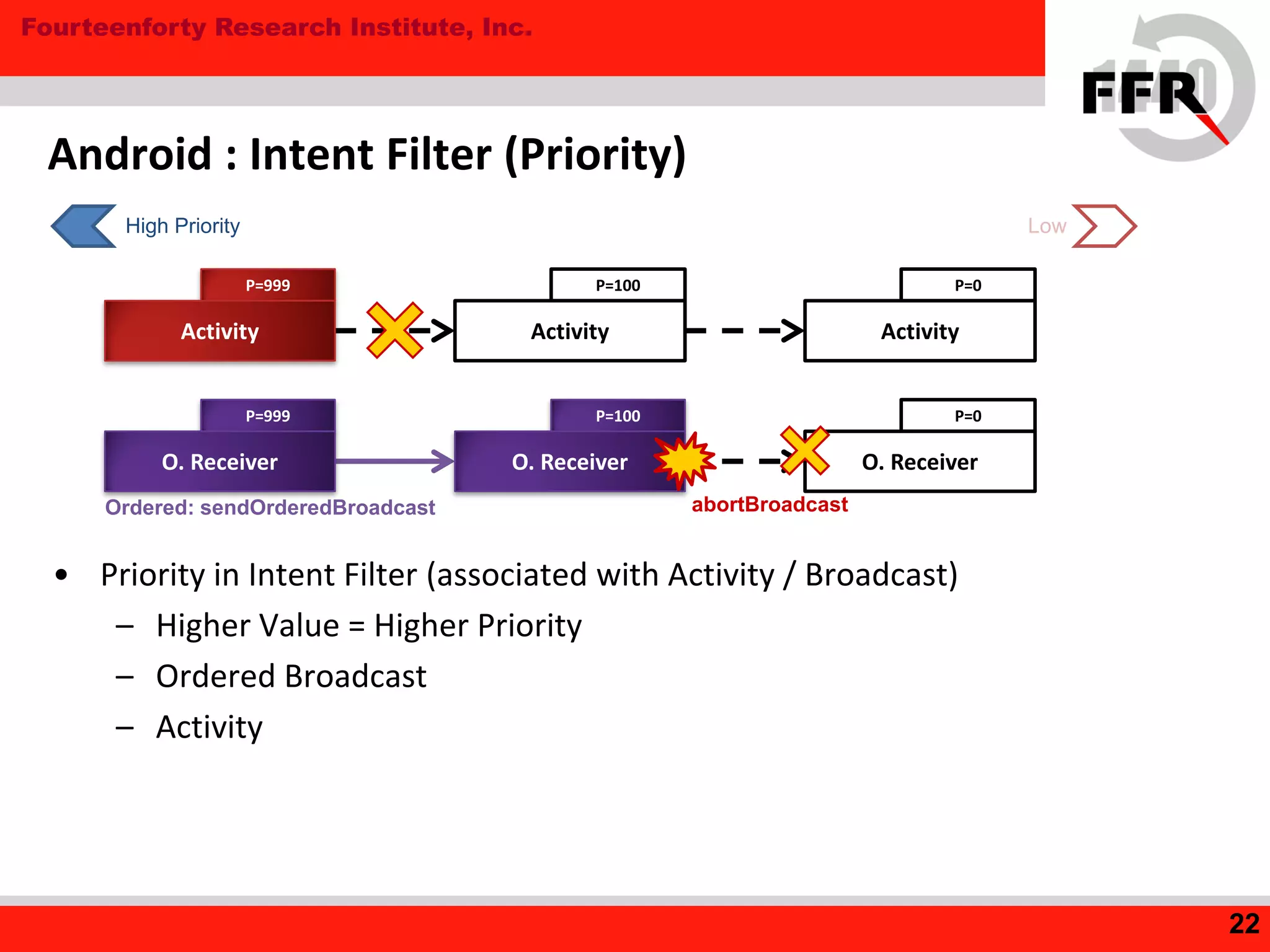
This document discusses security issues in the Android operating system and possibilities for malware infection. It begins by covering kernel-level protections like DEP and ASLR, which are not fully effective in Android due to issues like prelinking neutralizing ASLR. It then discusses the application layer, explaining Android application internals involving packages, permissions, and intent-based features like activities and broadcasts. Finally, it outlines the evolution of Android malware, characteristics like using intents and premium services, issues with anti-virus software's limited privileges, and how rooting breaks security by enabling malware to gain higher privileges.














![Fourteenforty Research Institute, Inc.
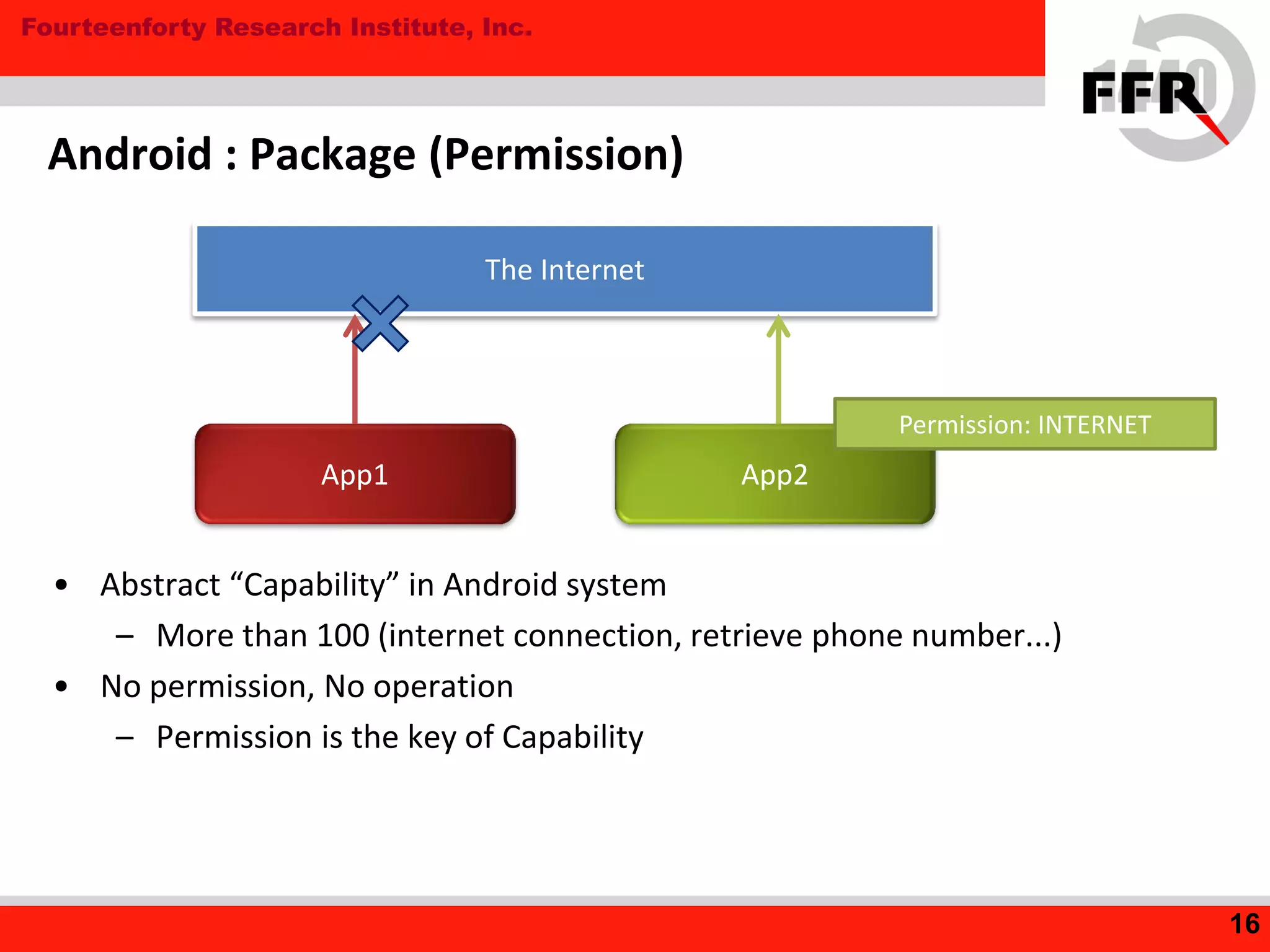
• Gaining Administrator Privileges (not available by default)
– Specially, utilizing local vulnerabilities
• rooting vulnerabilities
– CVE-2009-1185 (exploid)
– [no CVE number] (rage against the cage)
– CVE-2011-1149 (psneuter)
– CVE-2011-1823 (Gingerbreak)
– [no CVE number] (zergRush)
• Chip/Vendor-specific vulnerabilities!
rooting
38](https://image.slidesharecdn.com/how-security-broken-pacsec2011-131007235103-phpapp01/75/How-security-broken-Android-internals-and-malware-infection-possibilities-38-2048.jpg)
![Fourteenforty Research Institute, Inc.
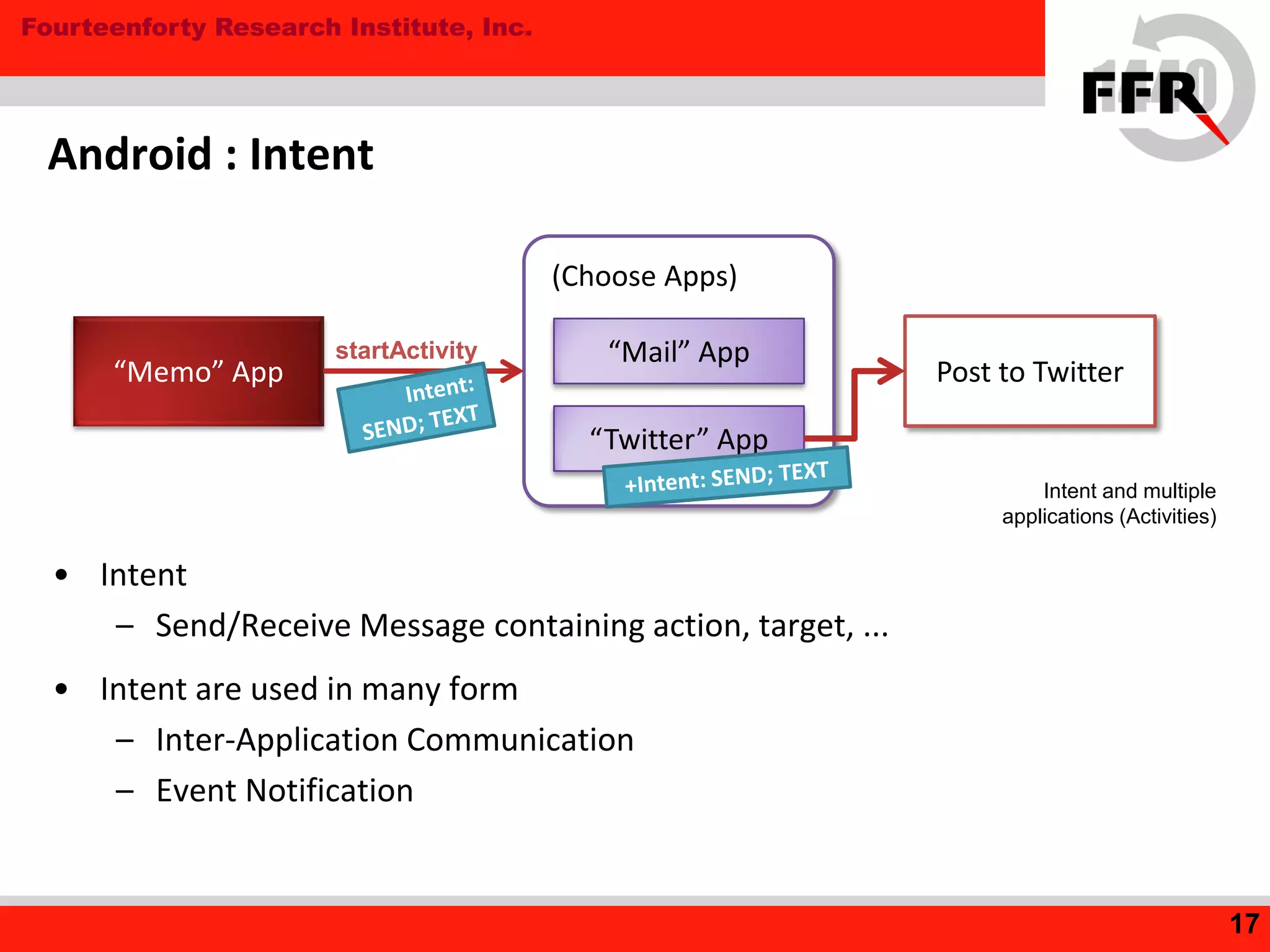
• Logic Error in suid program
– Some Android Tablet: OS command injection
rooting : Vulnerabilities (1)
39
Can invoke arbitrary command in root privileges.
[not available in public slides]](https://image.slidesharecdn.com/how-security-broken-pacsec2011-131007235103-phpapp01/75/How-security-broken-Android-internals-and-malware-infection-possibilities-39-2048.jpg)
![Fourteenforty Research Institute, Inc.
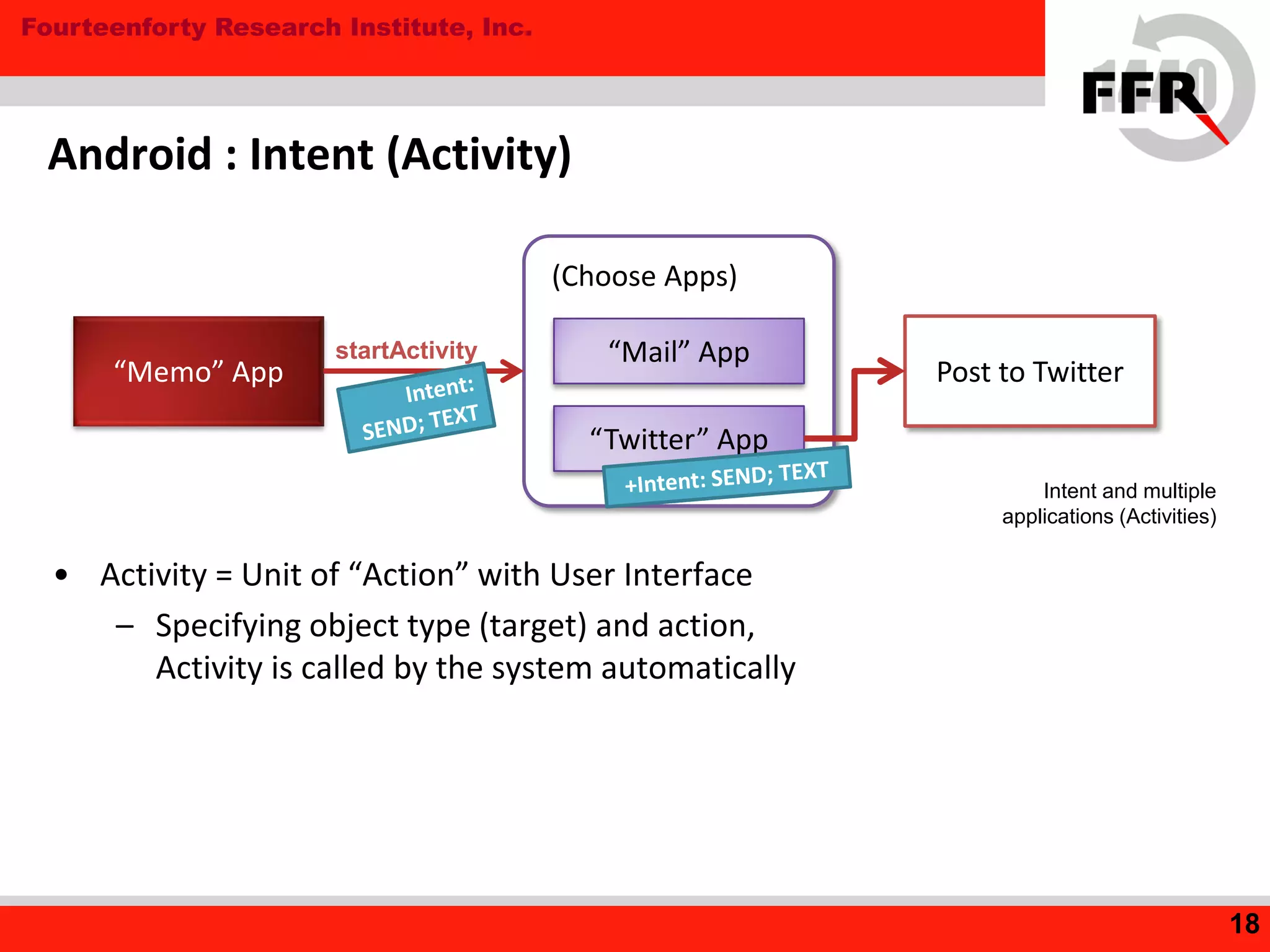
• Improper User-supplied buffer access
– Some Android smartphone: Sensor Device
rooting : Vulnerabilities (2)
40
Can write [not available] to arbitrary user memory, bypassing copy-on-write.
Destroying setuid function can generate root-privilege process.
[not available in public slides]](https://image.slidesharecdn.com/how-security-broken-pacsec2011-131007235103-phpapp01/75/How-security-broken-Android-internals-and-malware-infection-possibilities-40-2048.jpg)