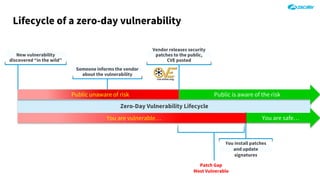
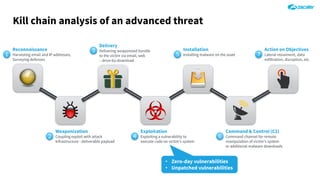
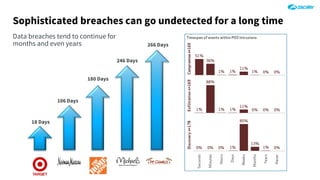
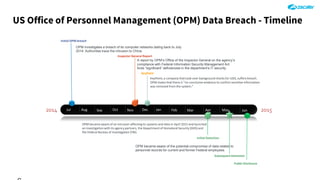
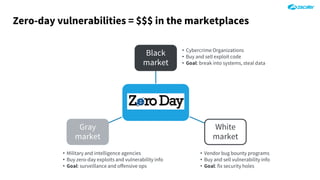
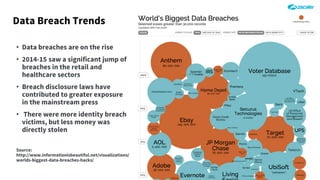
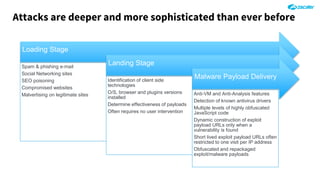
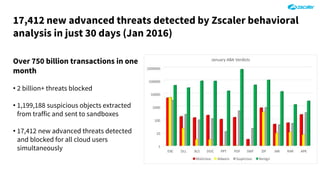
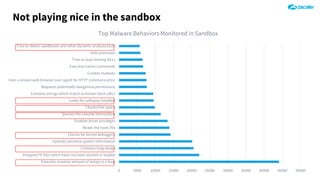
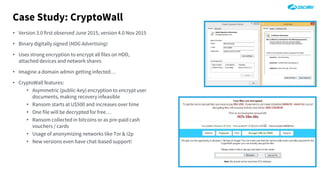
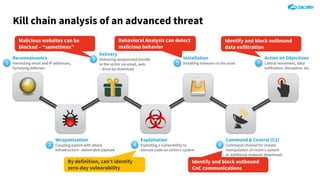
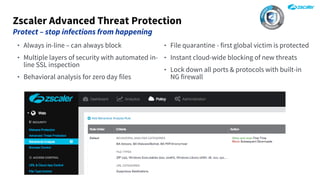
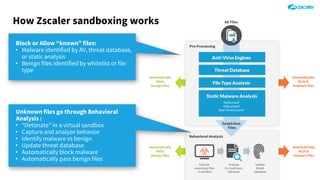
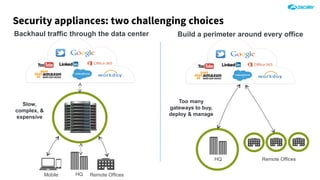
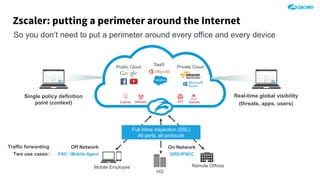
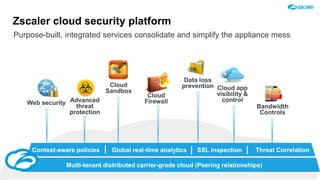
The document outlines the concept of zero-day threats, which are vulnerabilities not yet known to software vendors, and discusses the lifecycle of such vulnerabilities, including their discovery and the exploitation process used by attackers. It provides examples of notable zero-day vulnerabilities and emphasizes the rise of sophisticated attacks that leverage these weaknesses, highlighting the need for enhanced security measures and continuous monitoring. Additionally, the document reviews the current state of enterprise security defenses, exposing gaps and recommending advanced threat protection strategies to mitigate the risks associated with zero-day exploits.