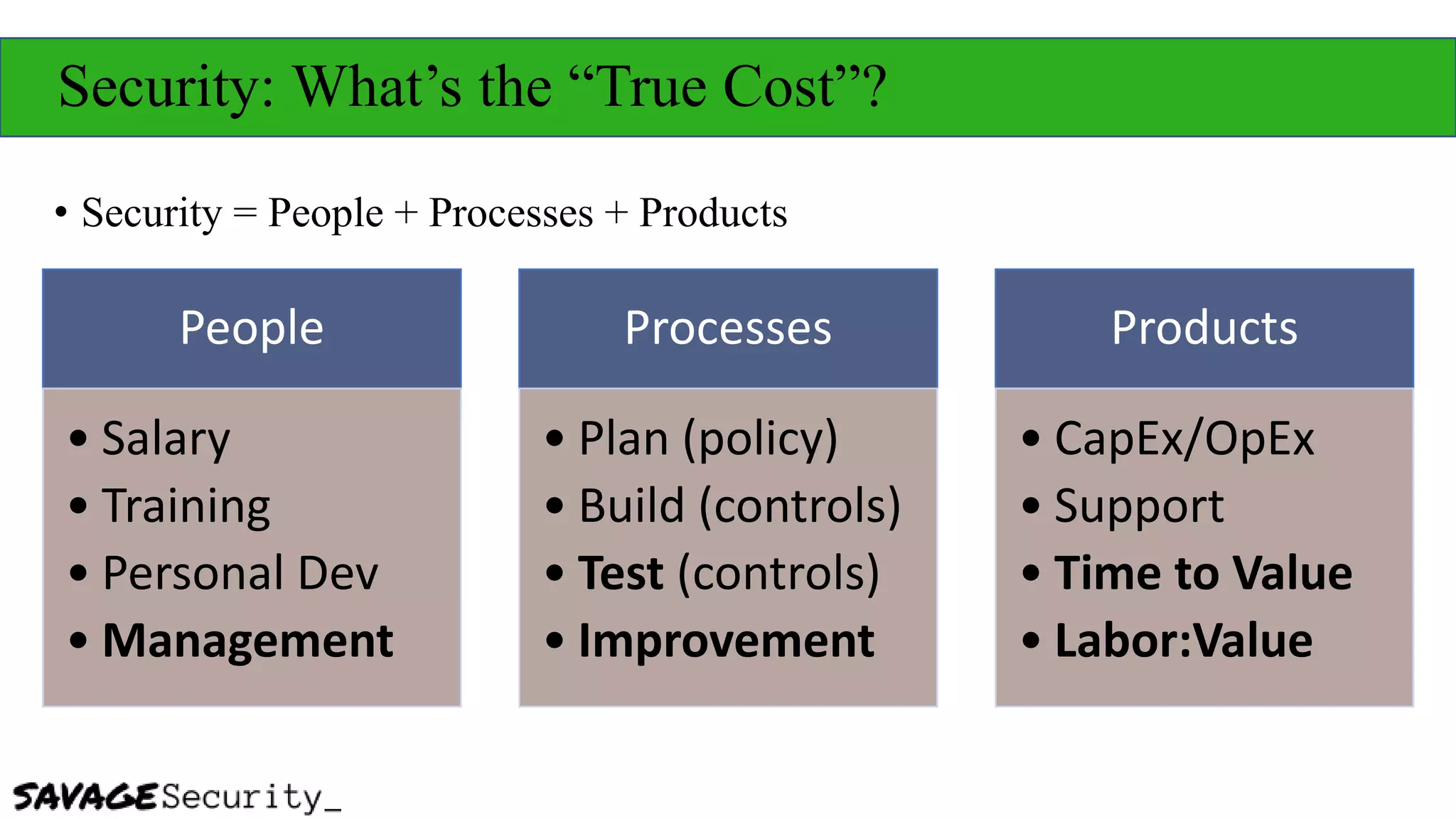
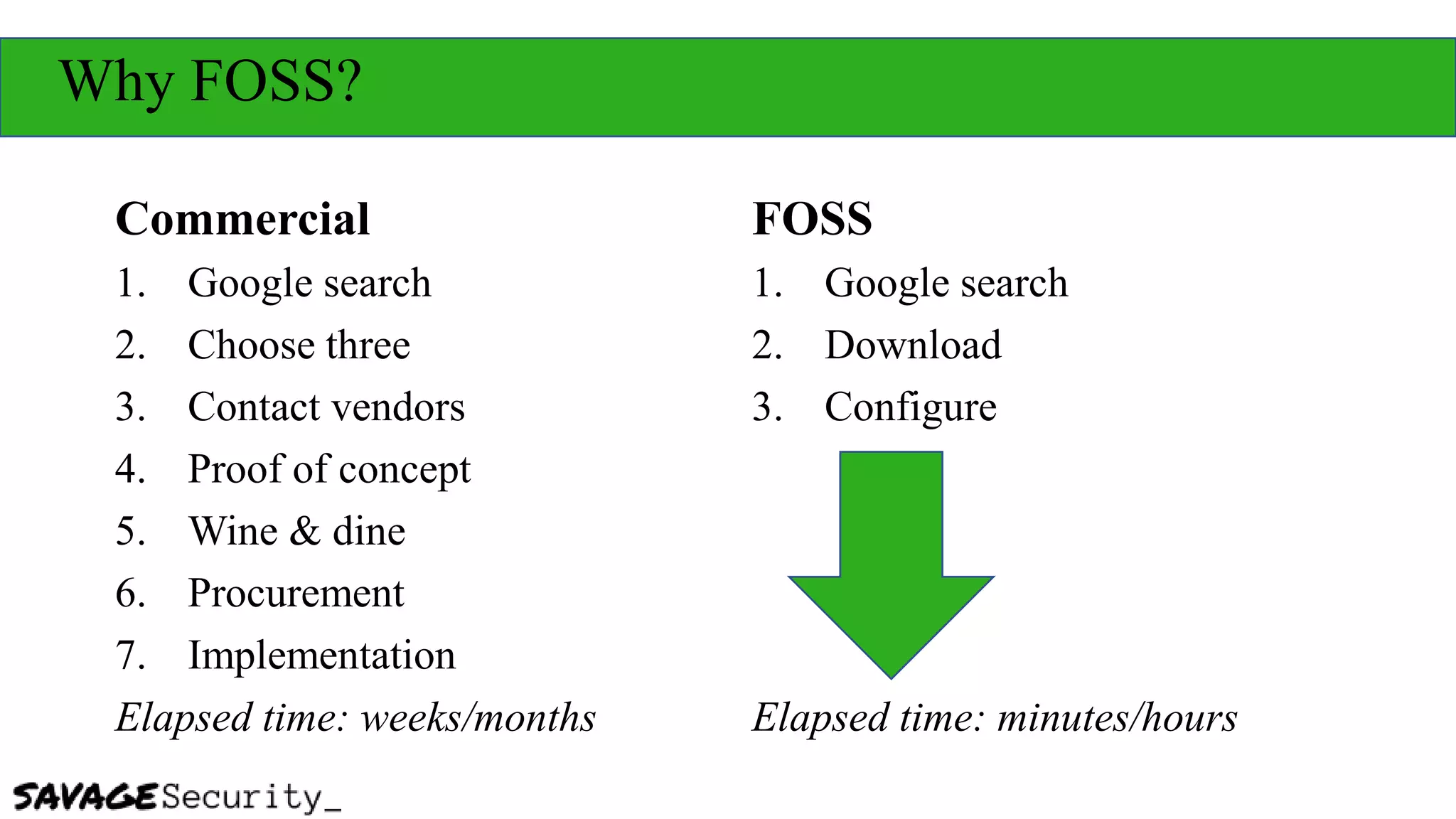
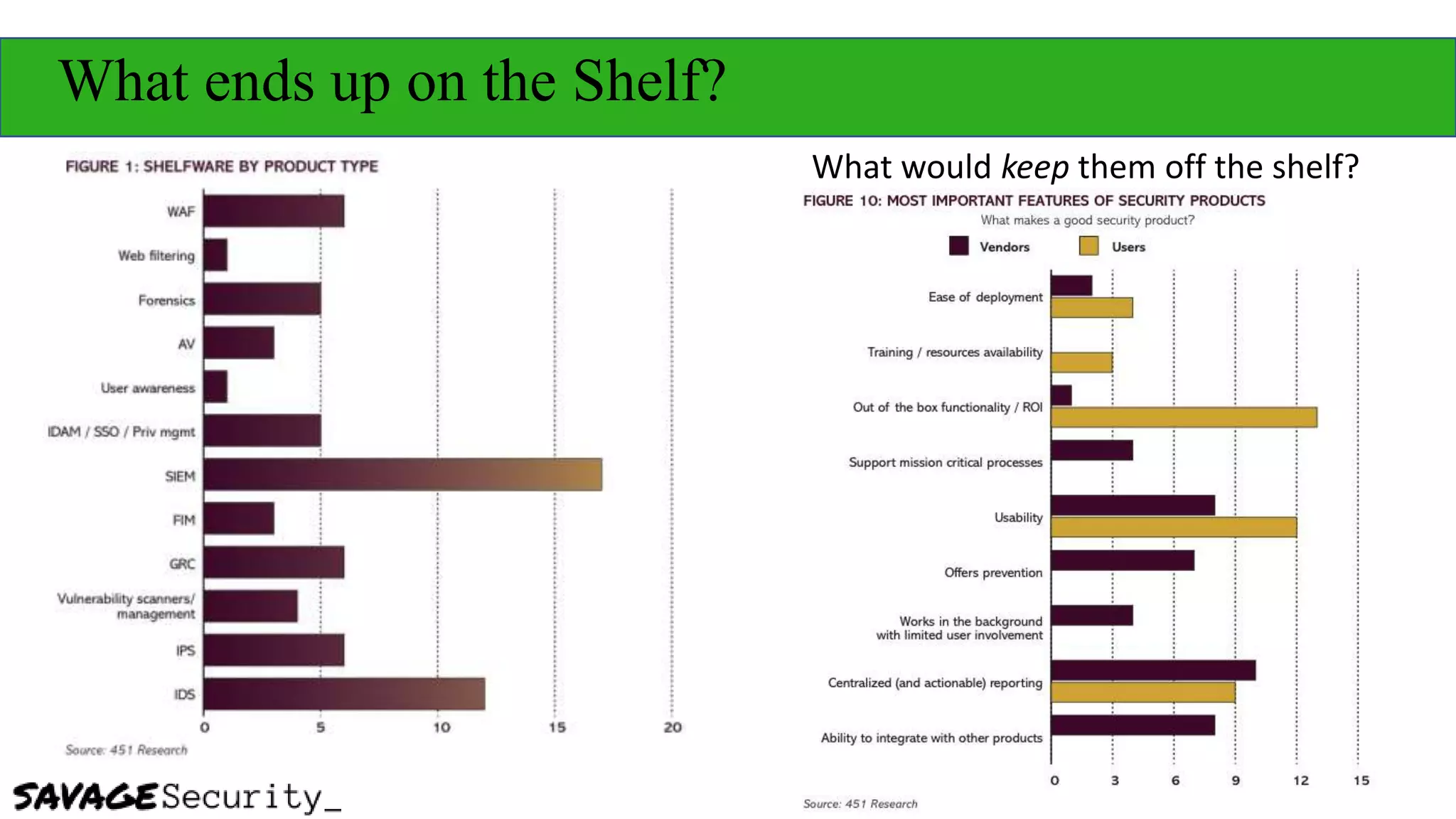
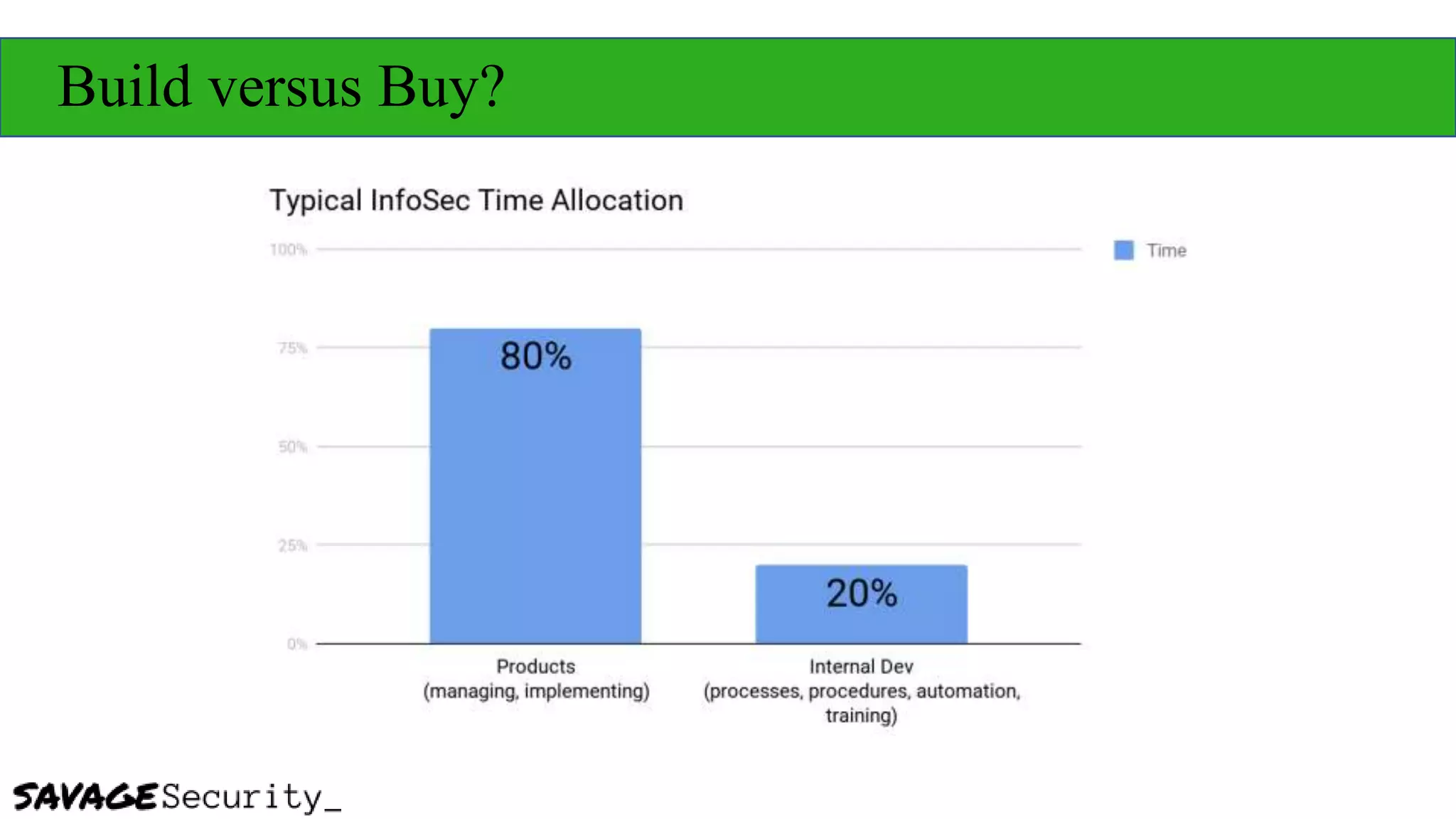
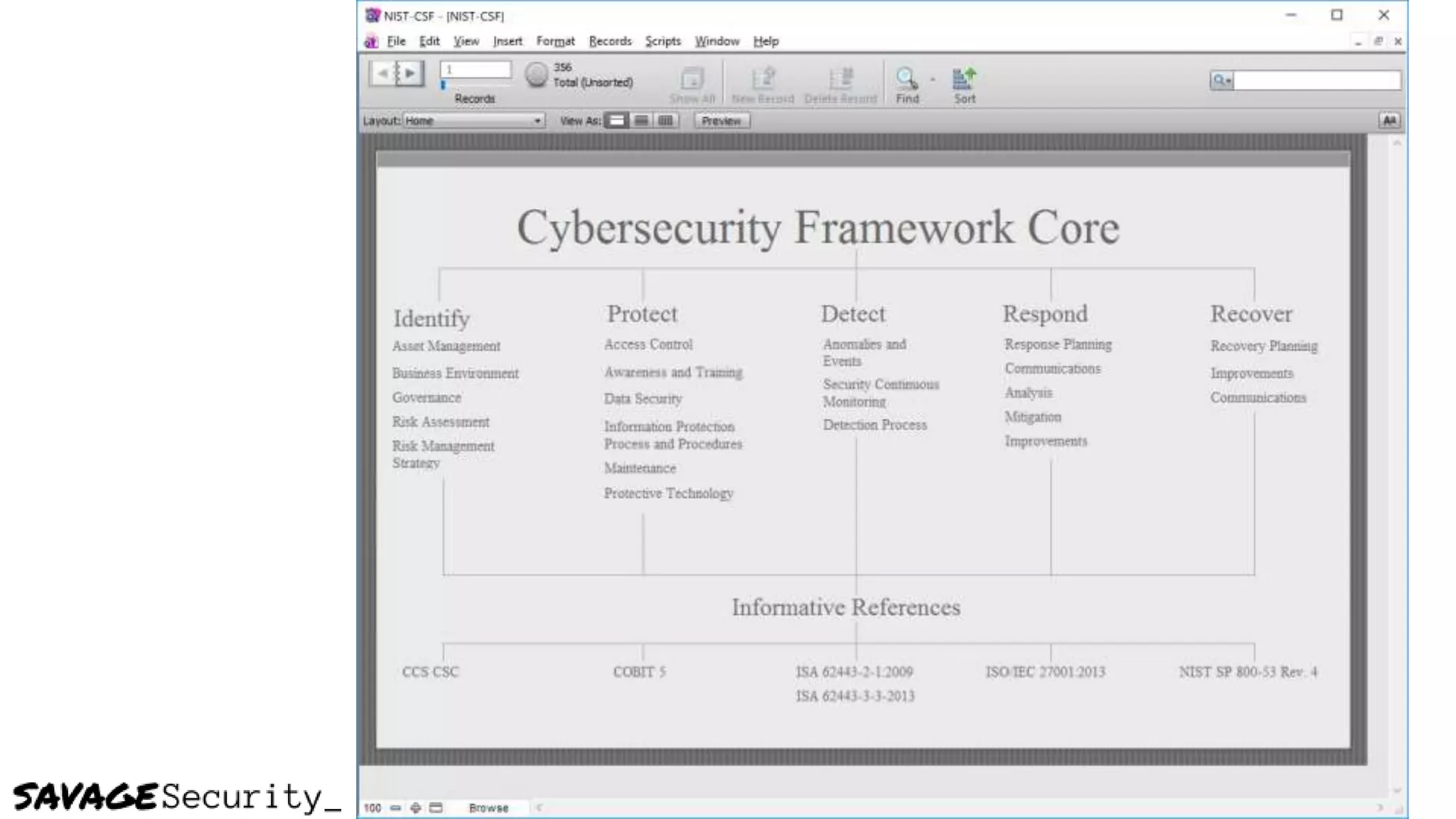
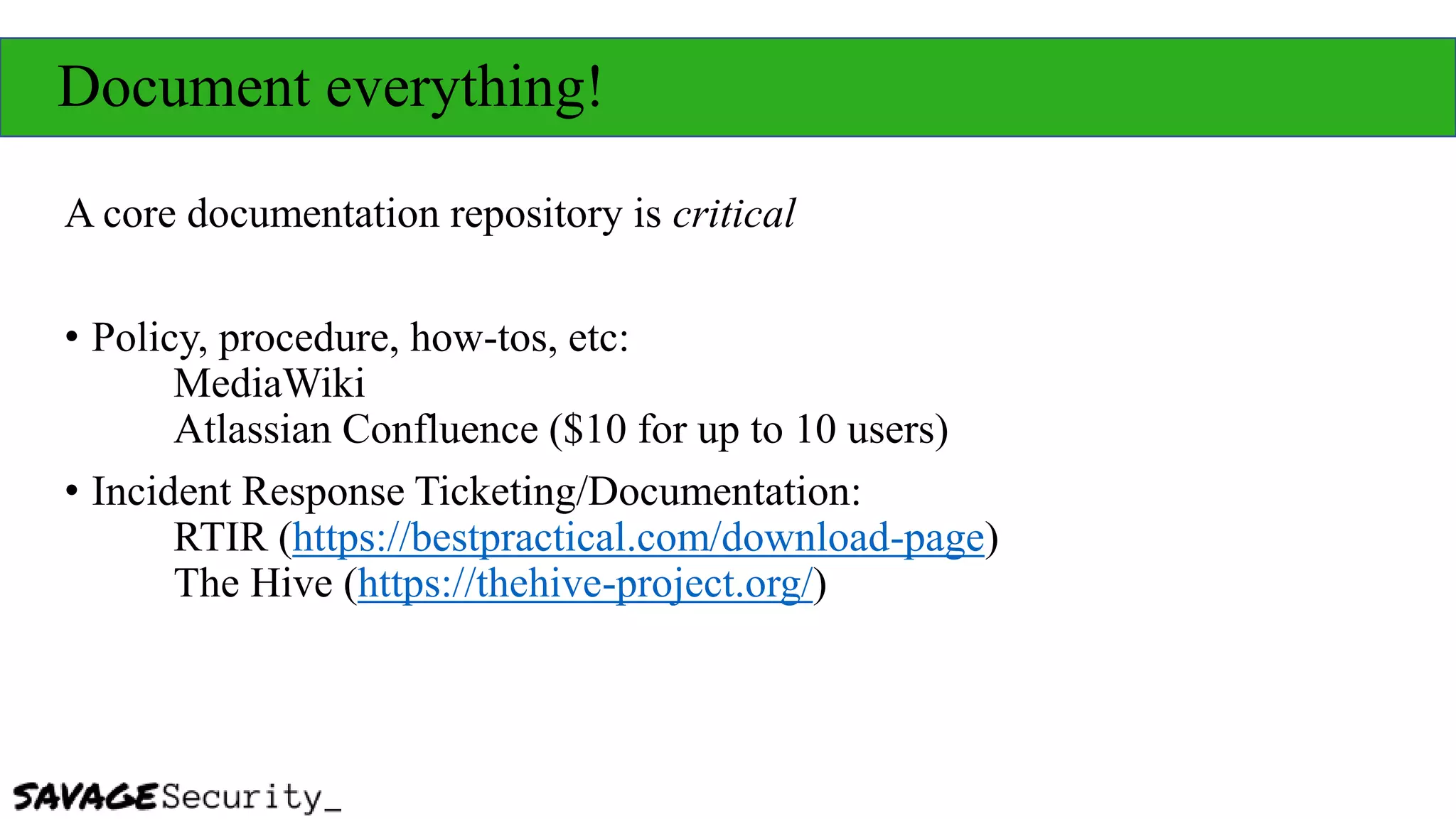
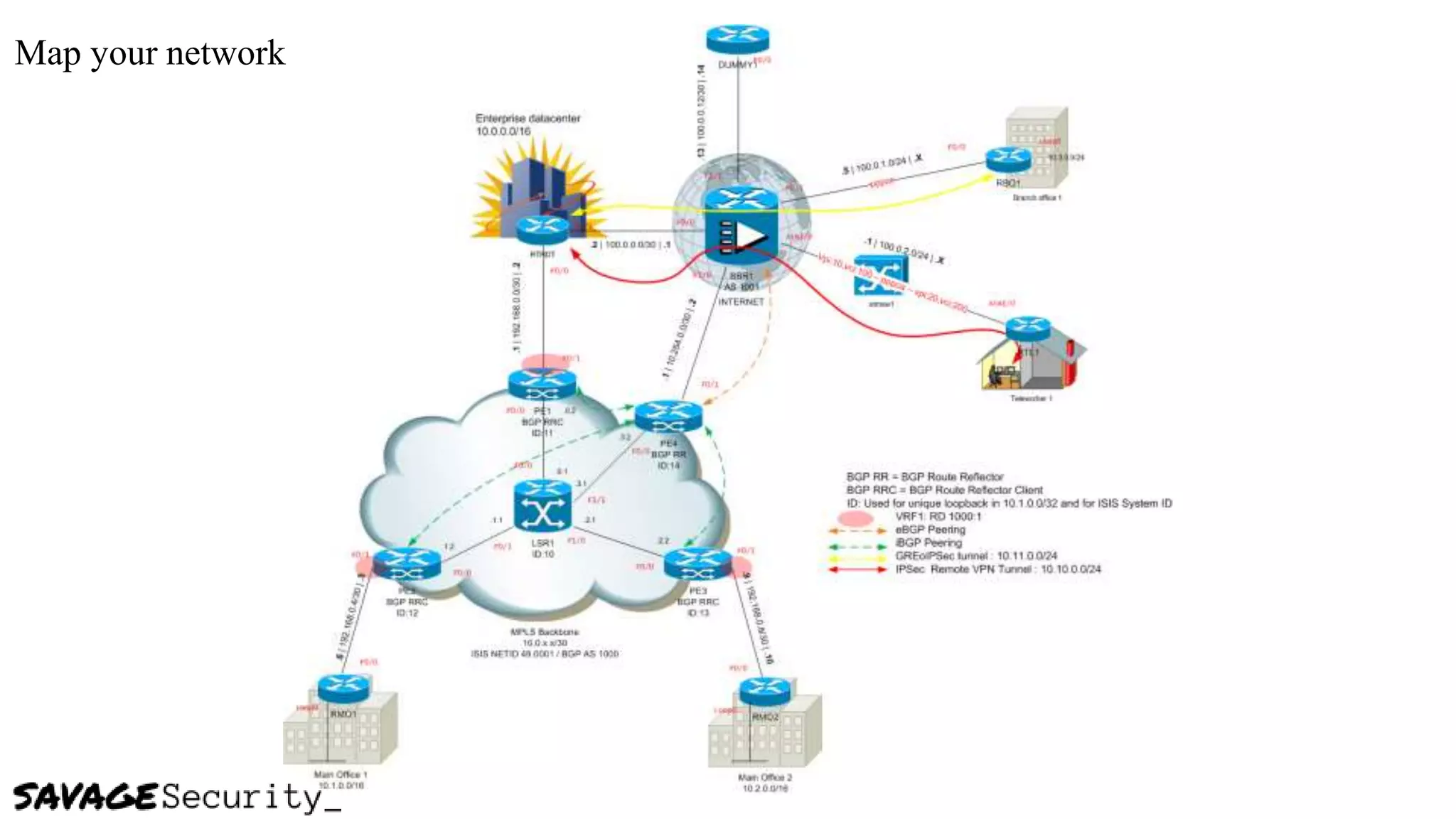
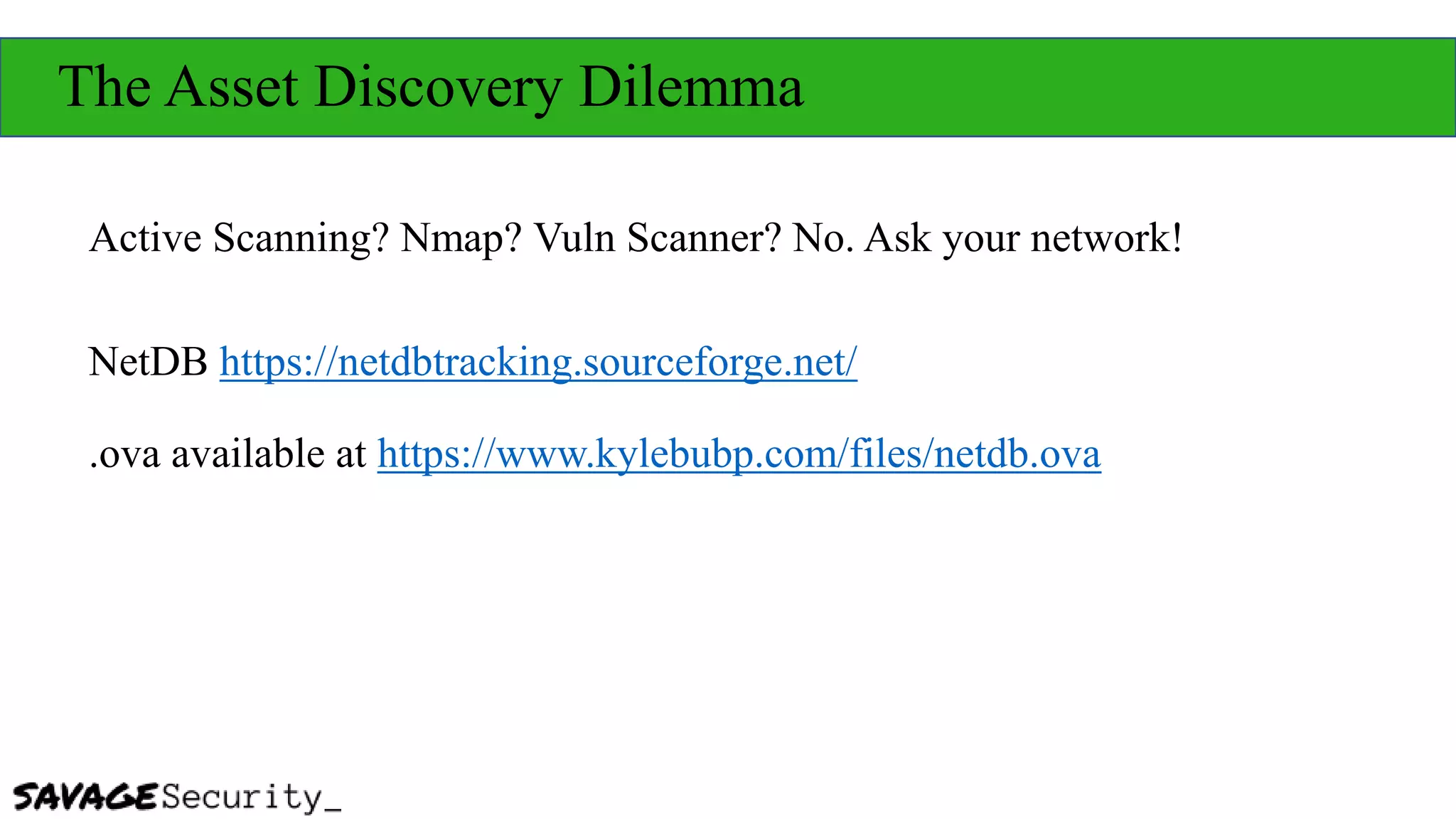
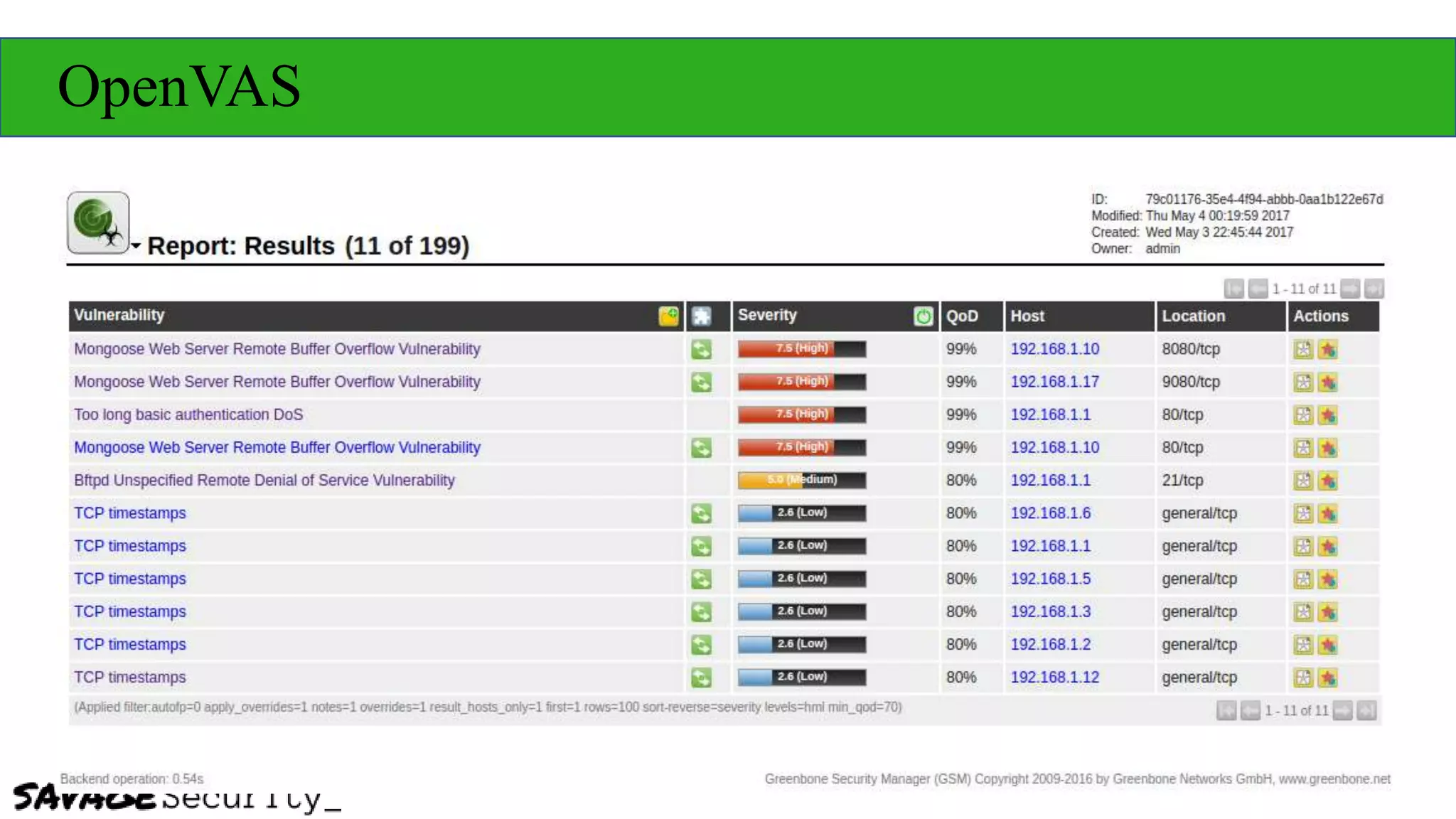
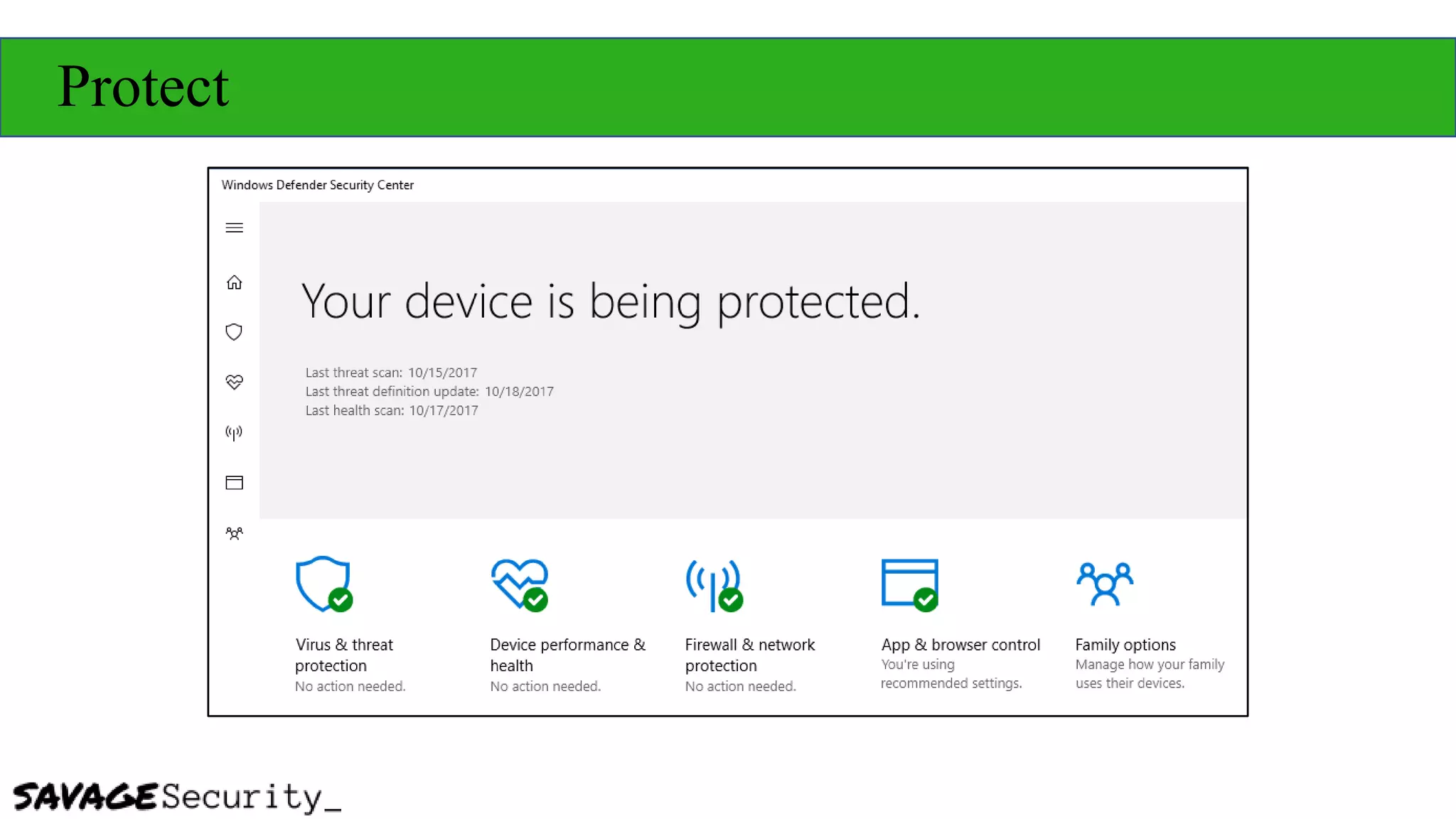
The document outlines strategies for building a security program with a zero budget, emphasizing the importance of people, processes, and open-source tools. It discusses foundational frameworks, network mapping, vulnerability scanning, and the necessity of documentation in managing security effectively. The author promotes a structured approach to security that focuses on identifying, protecting, detecting, responding, and recovering, while also encouraging community collaboration and continuous learning.