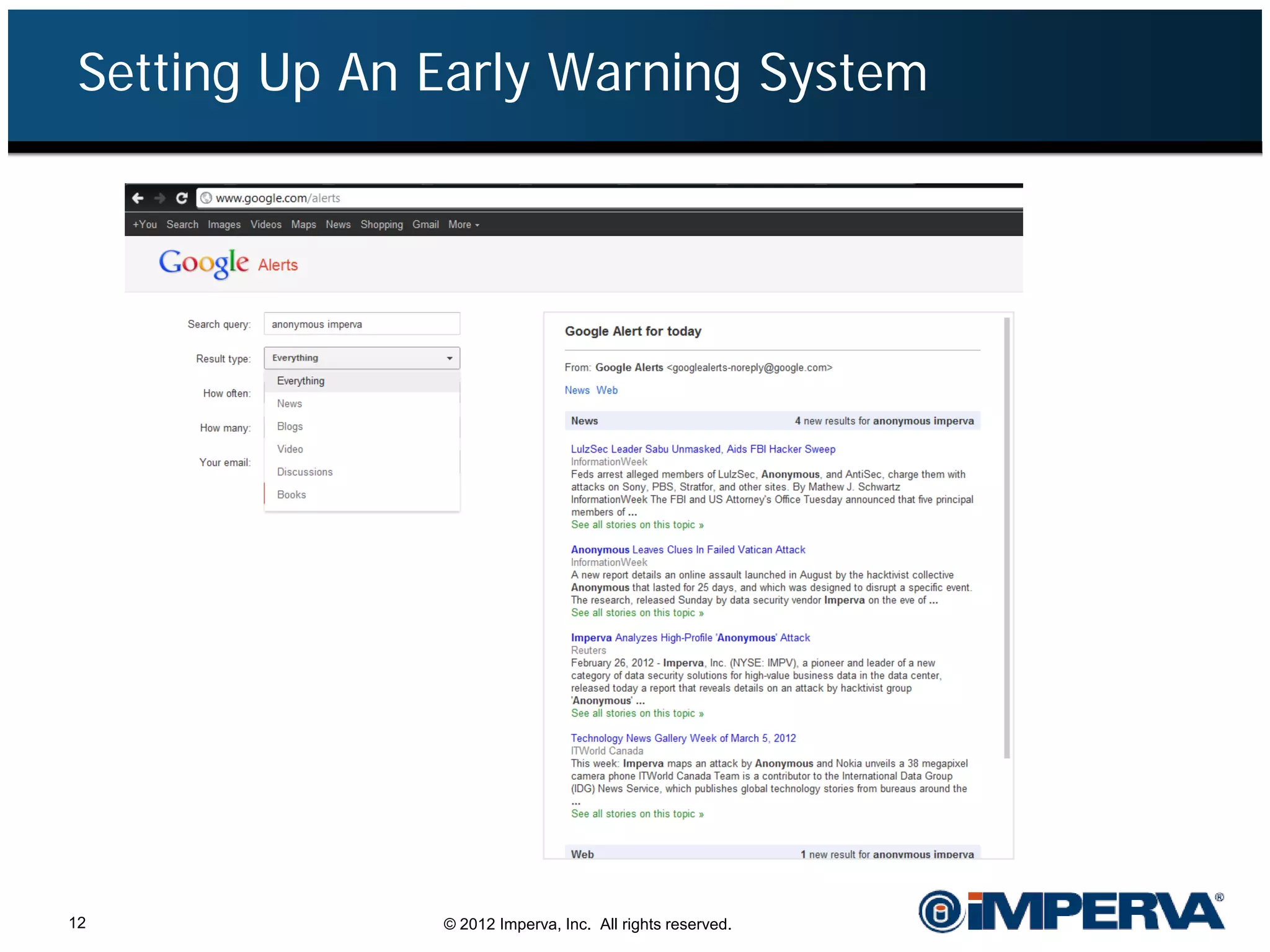
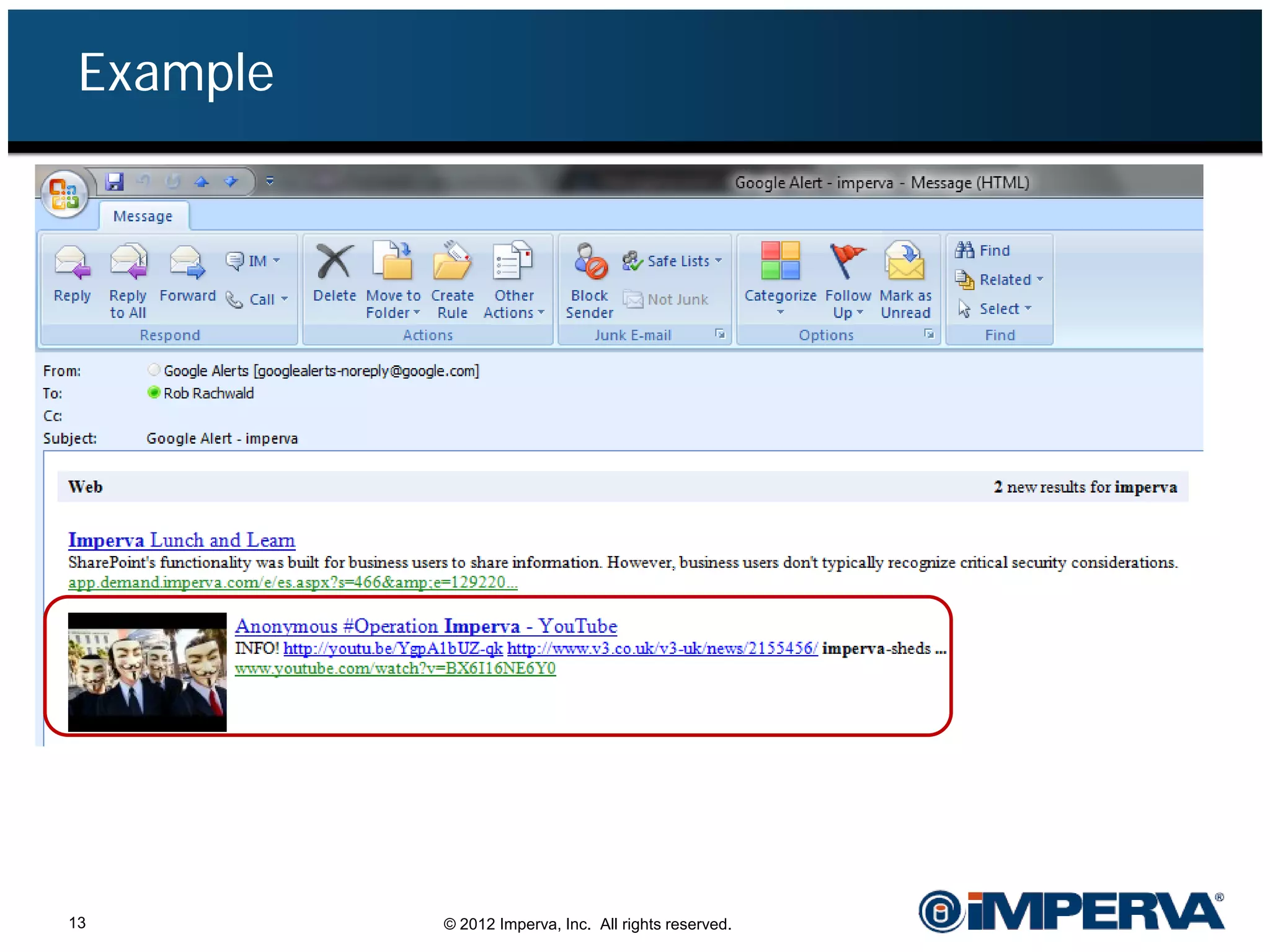
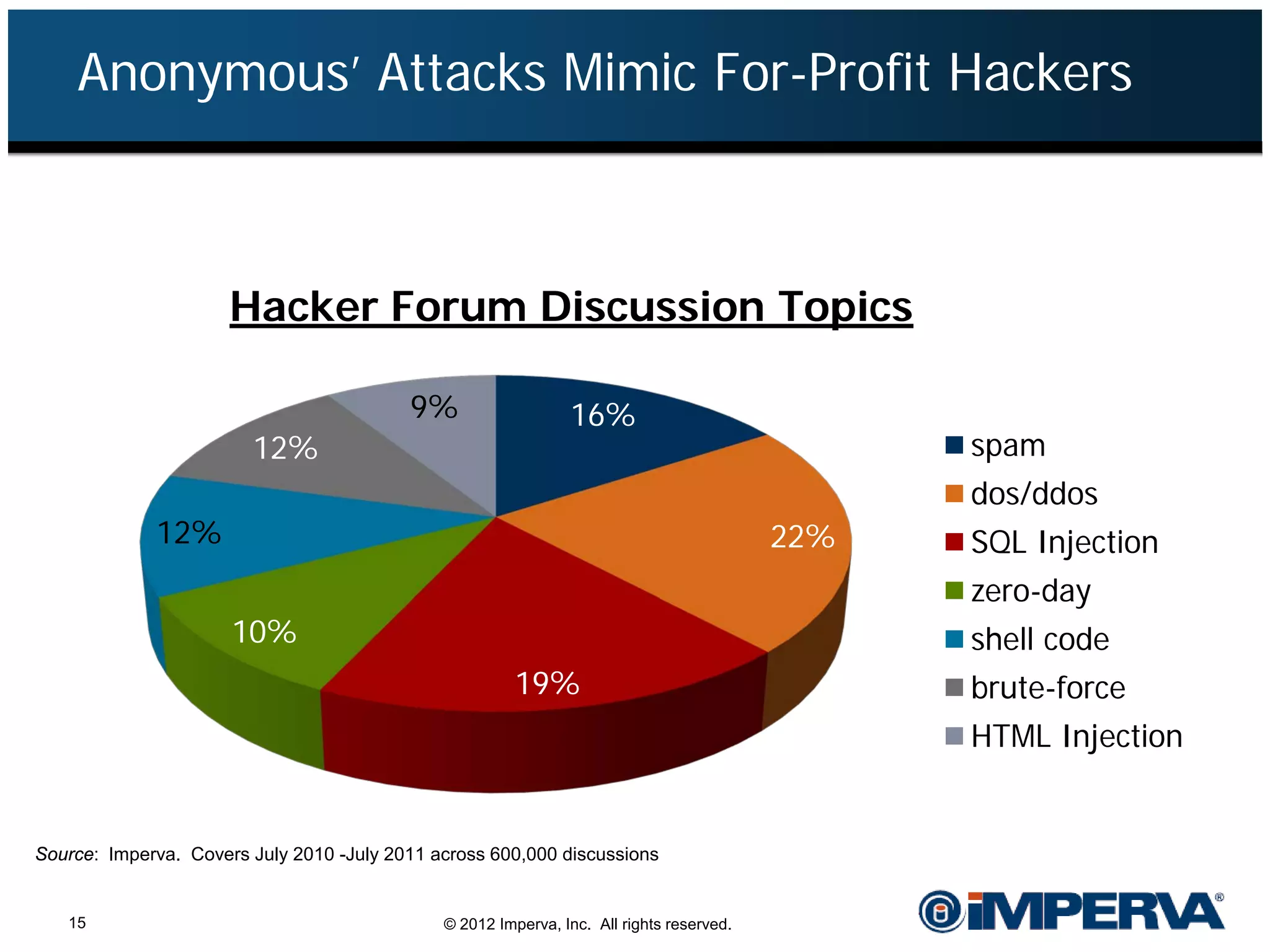
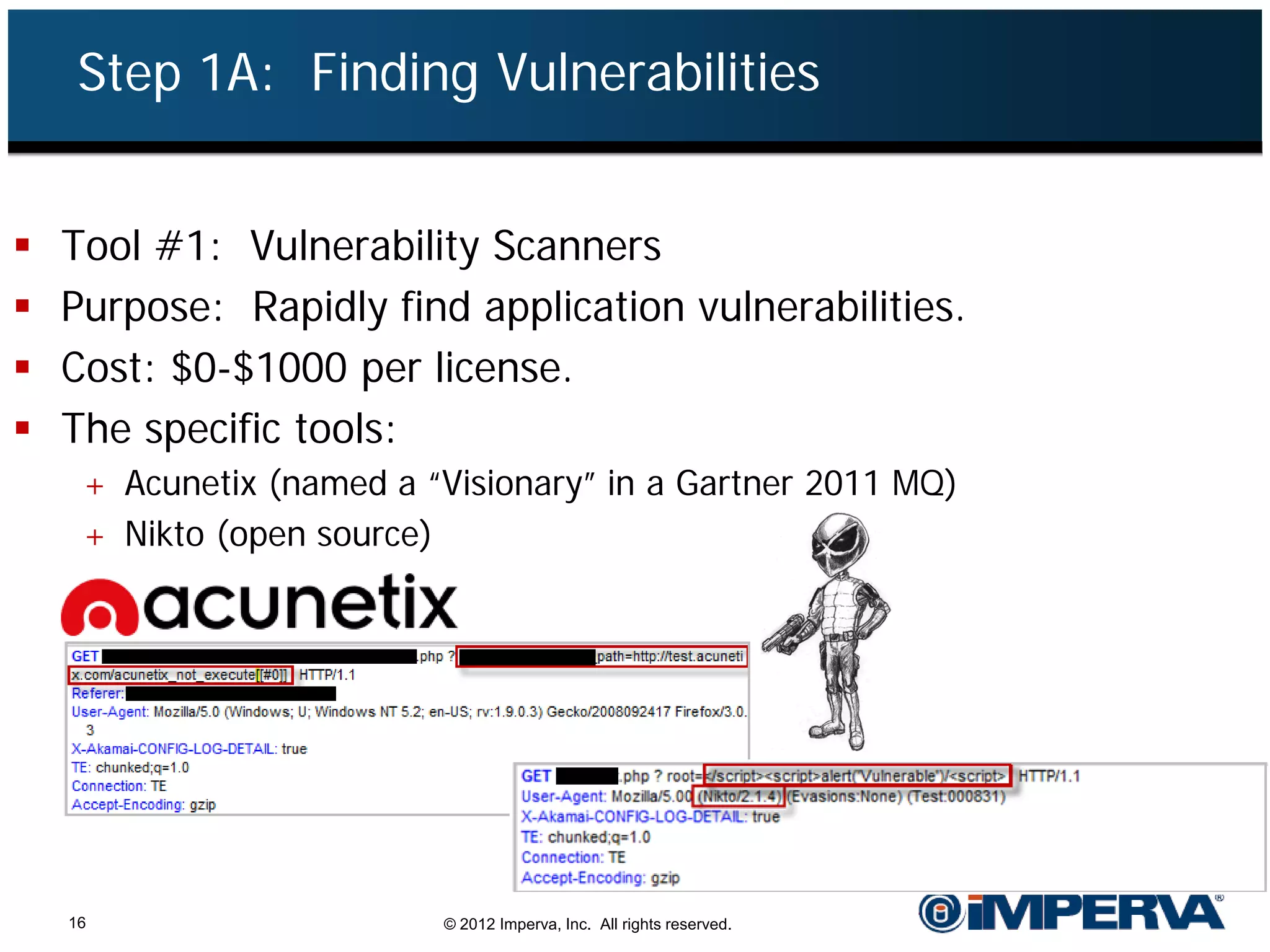
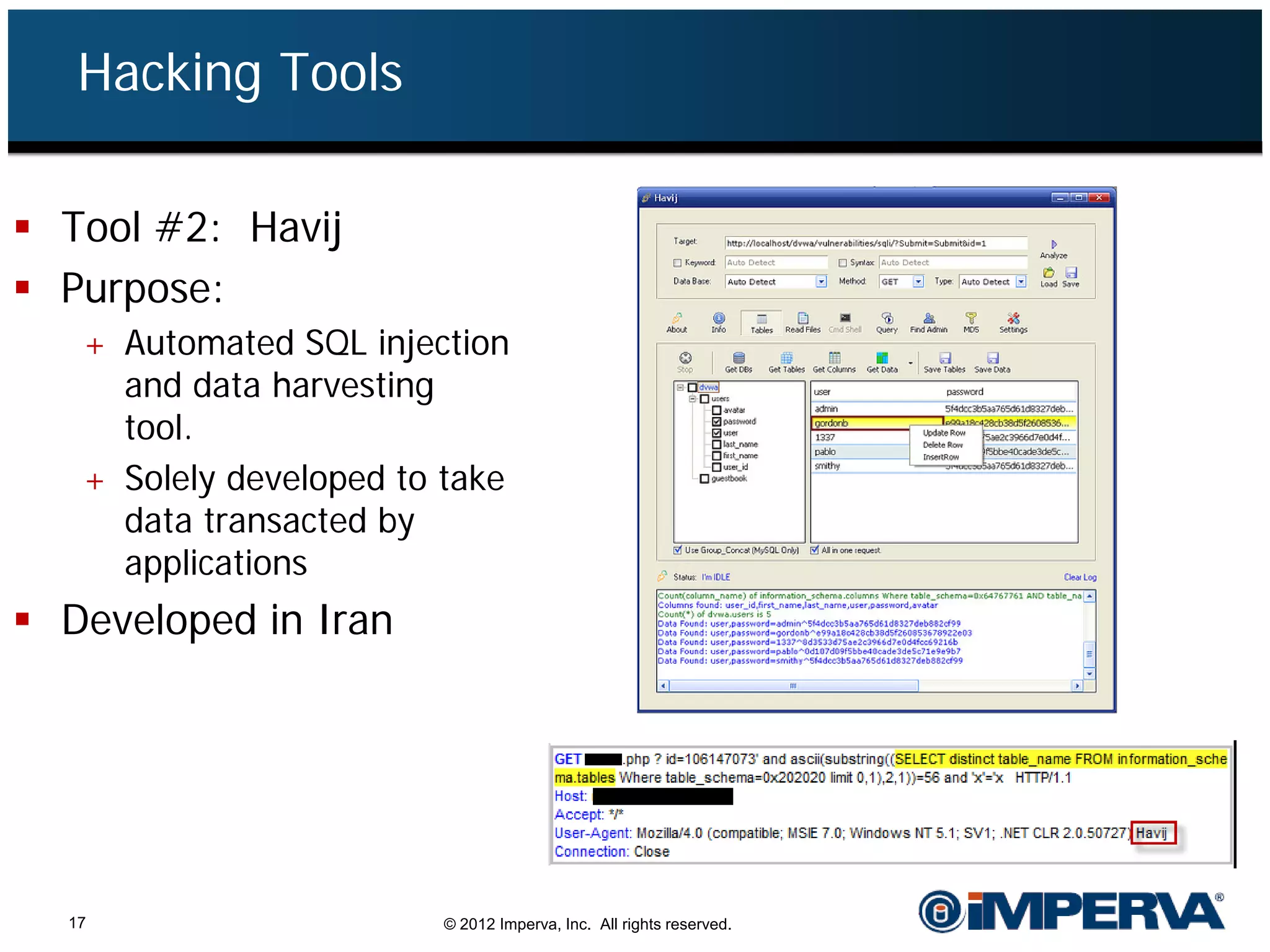
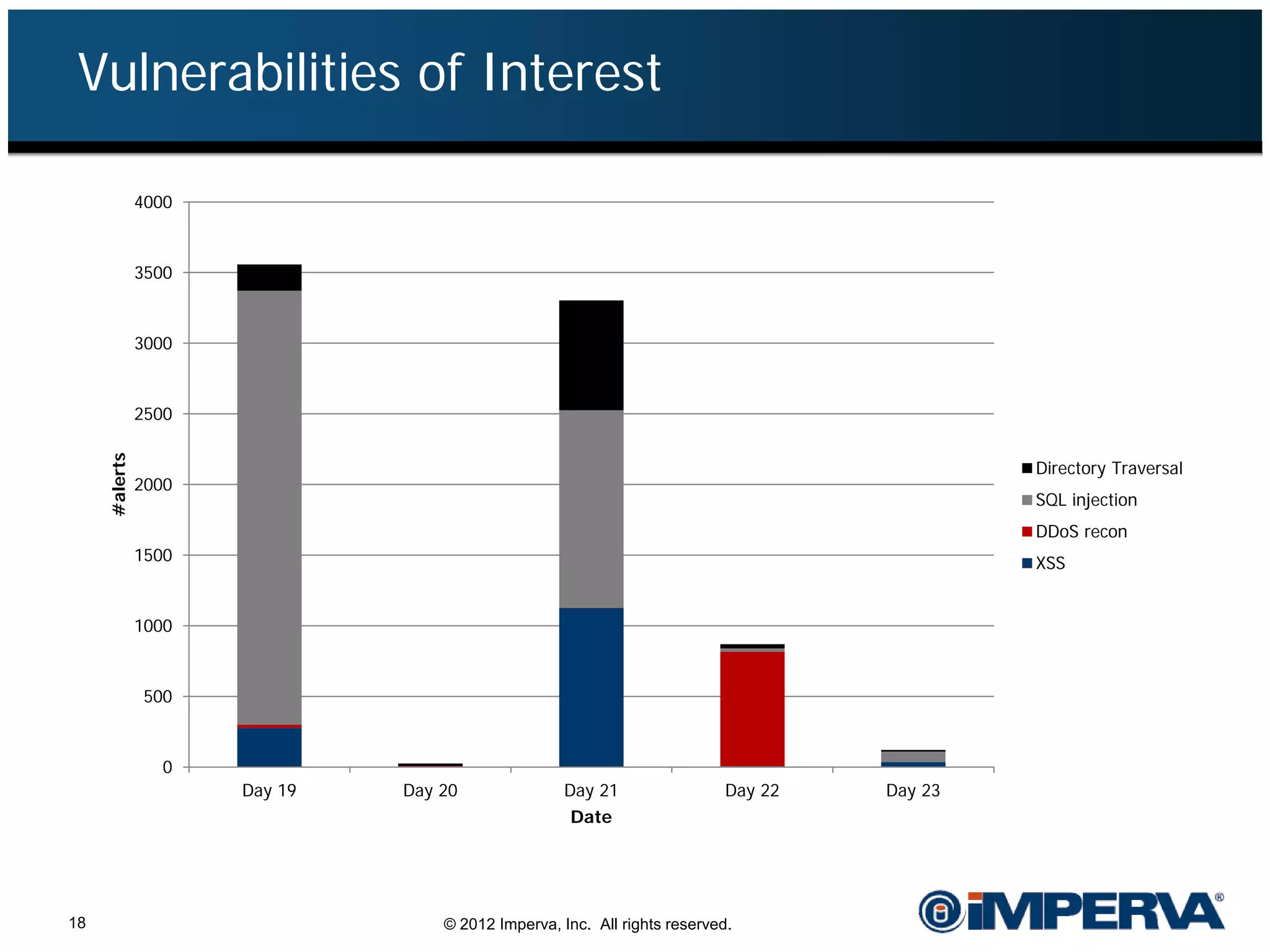
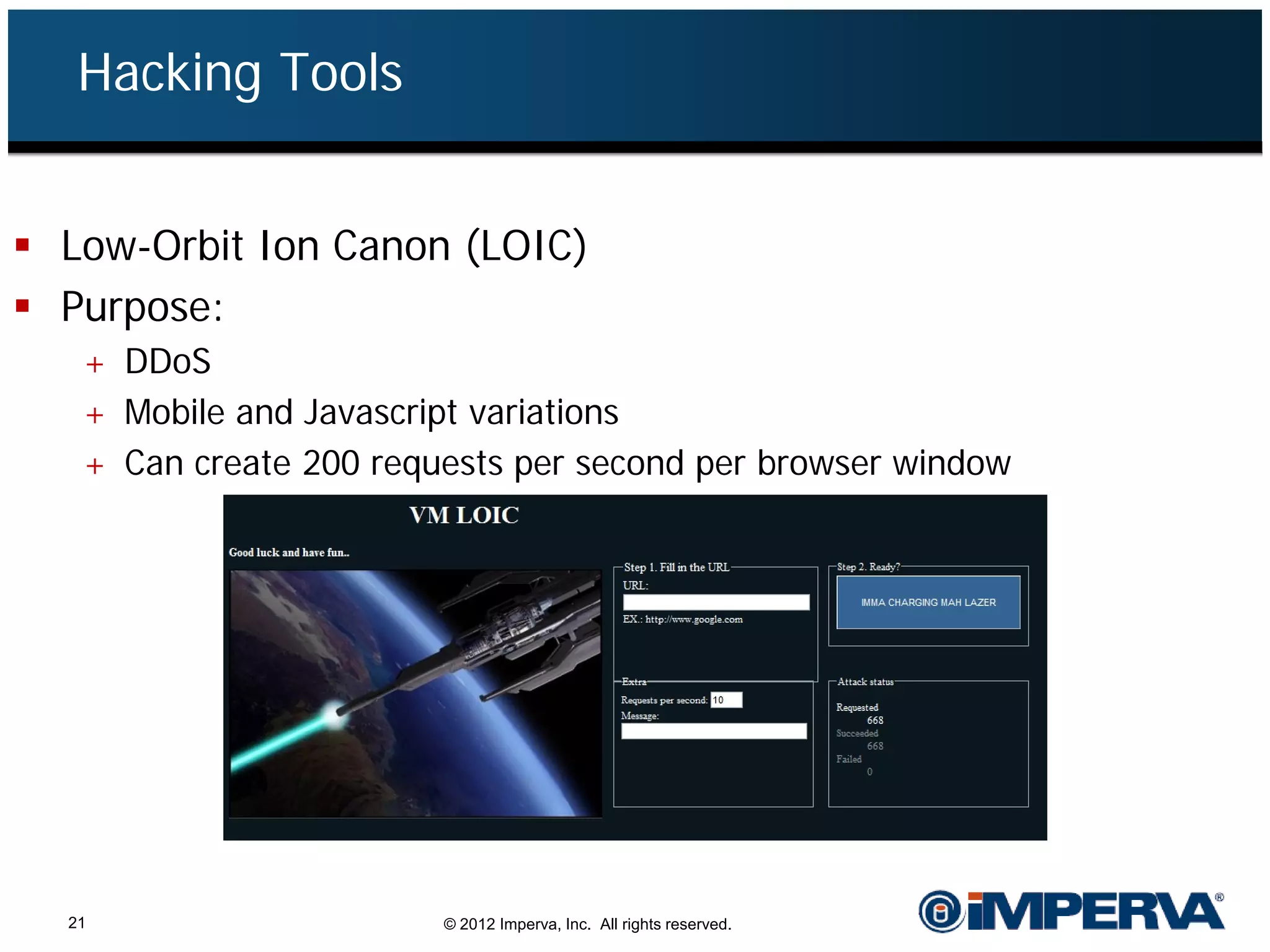
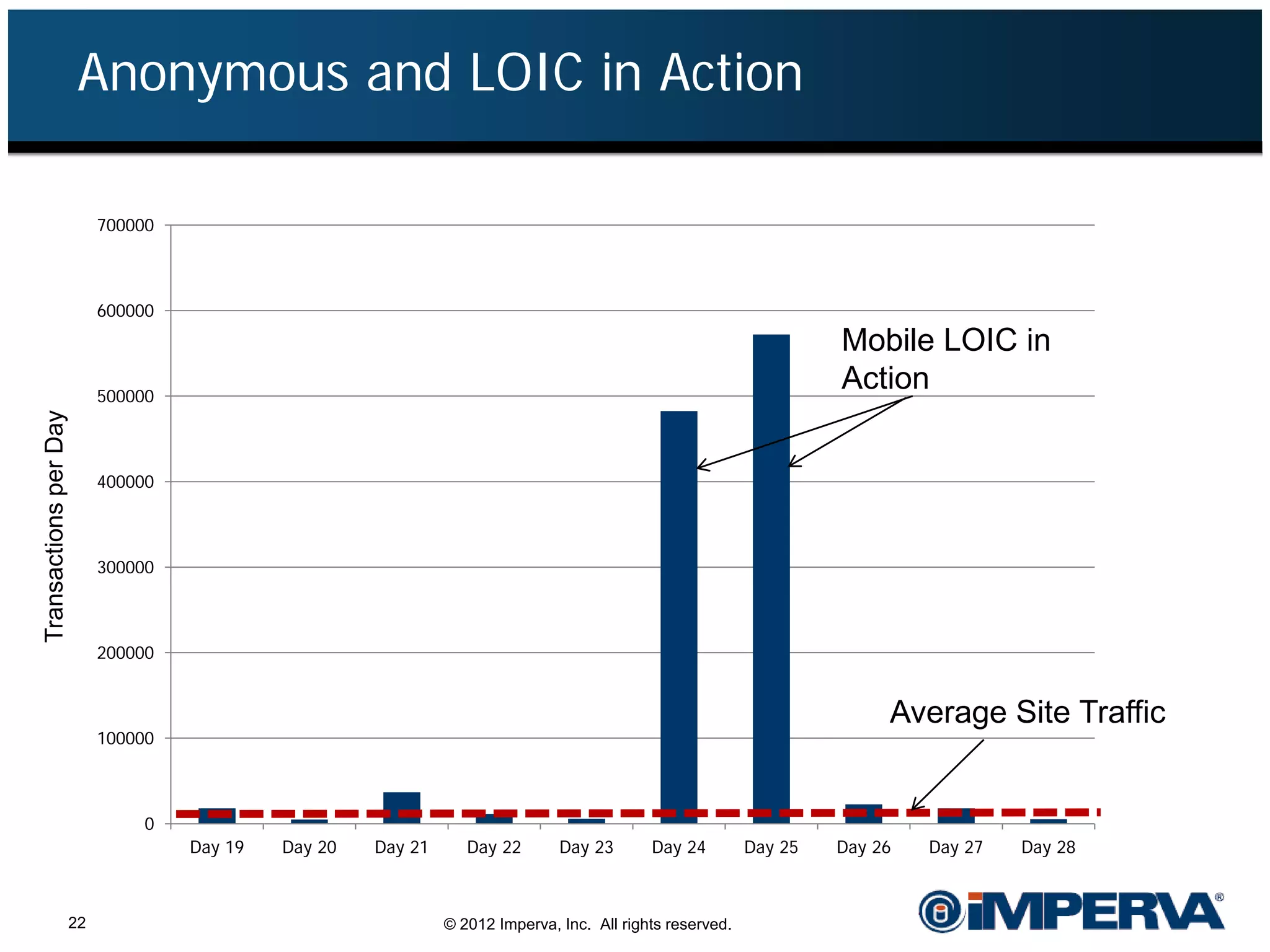
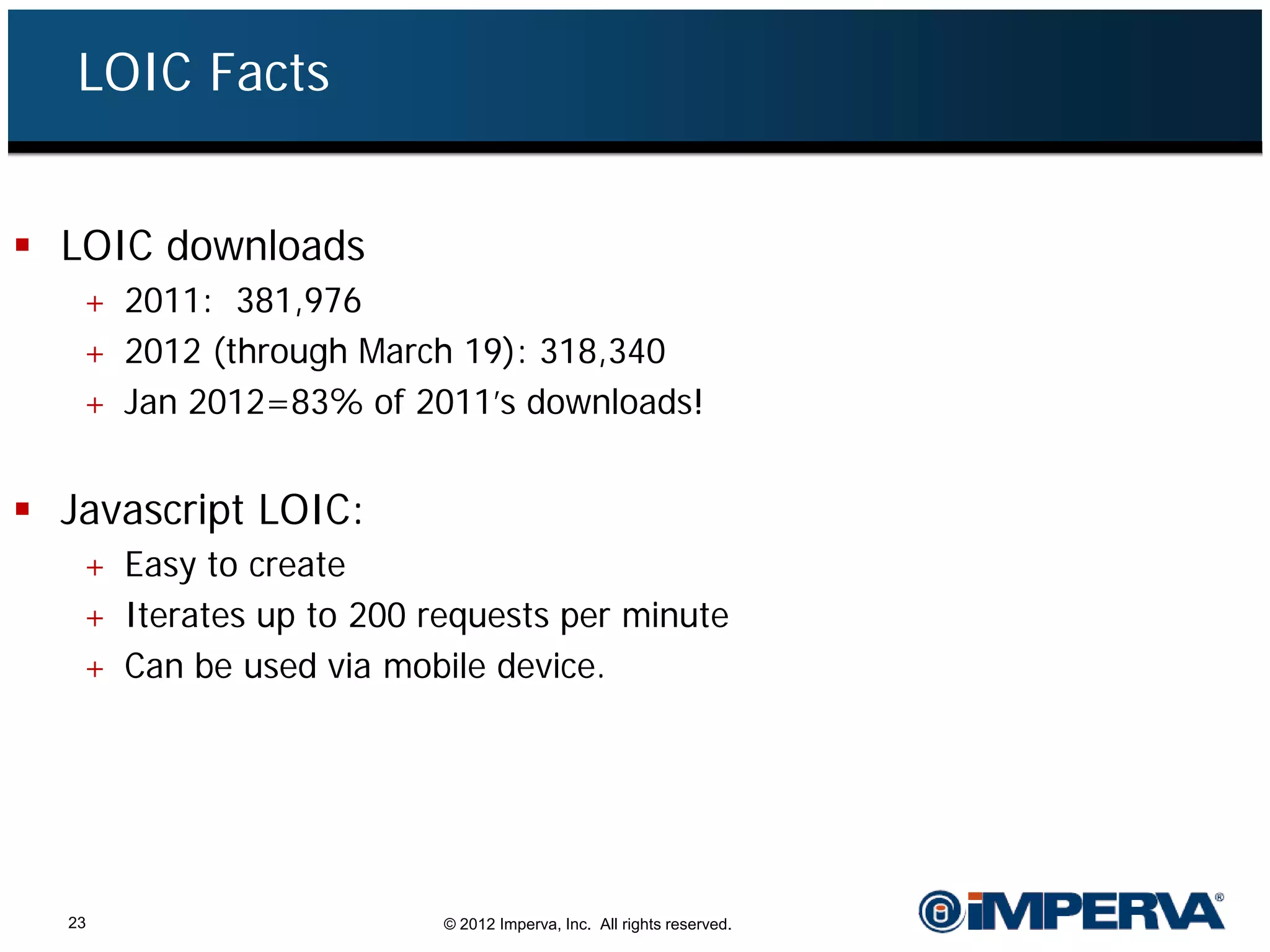
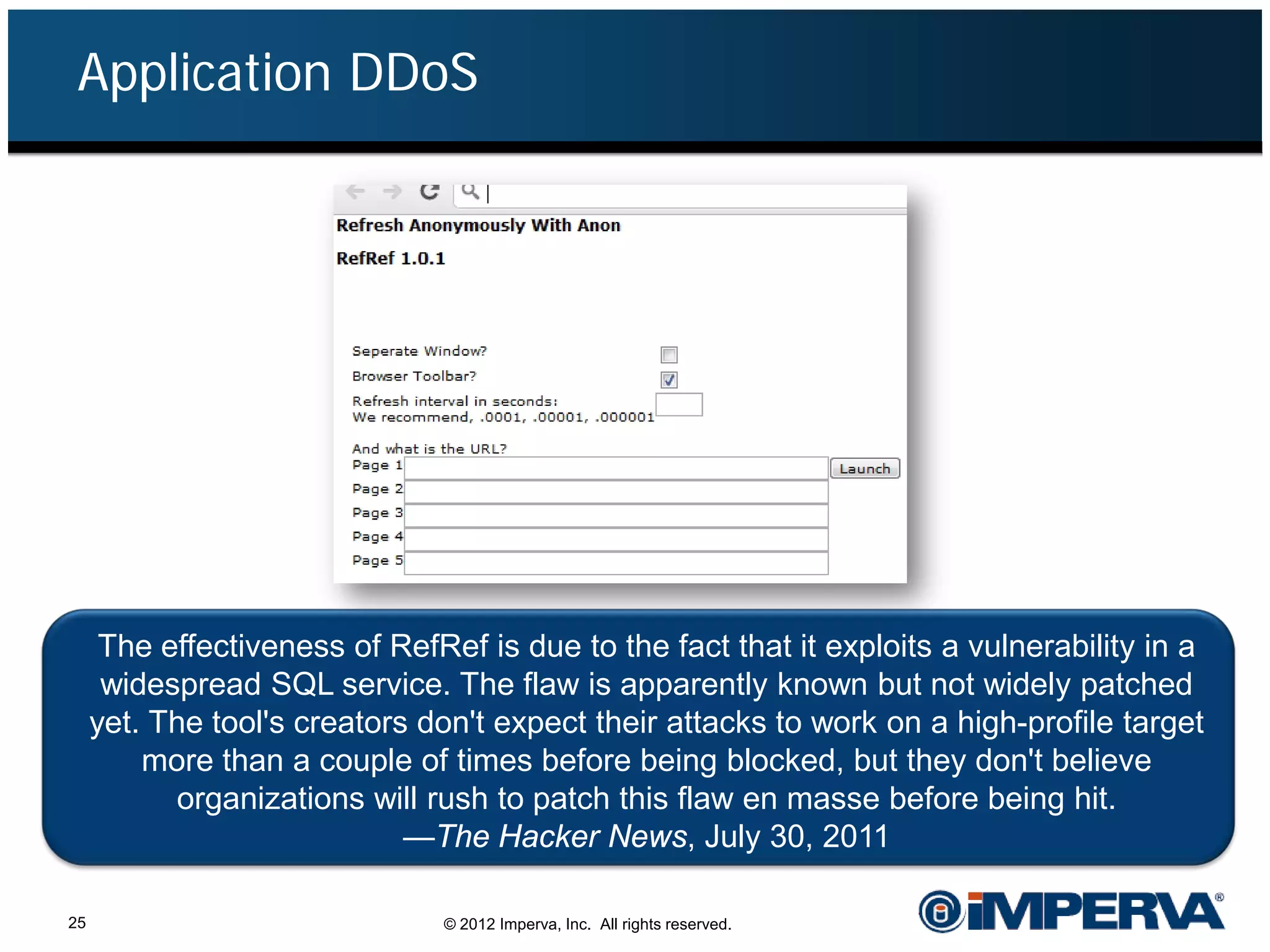
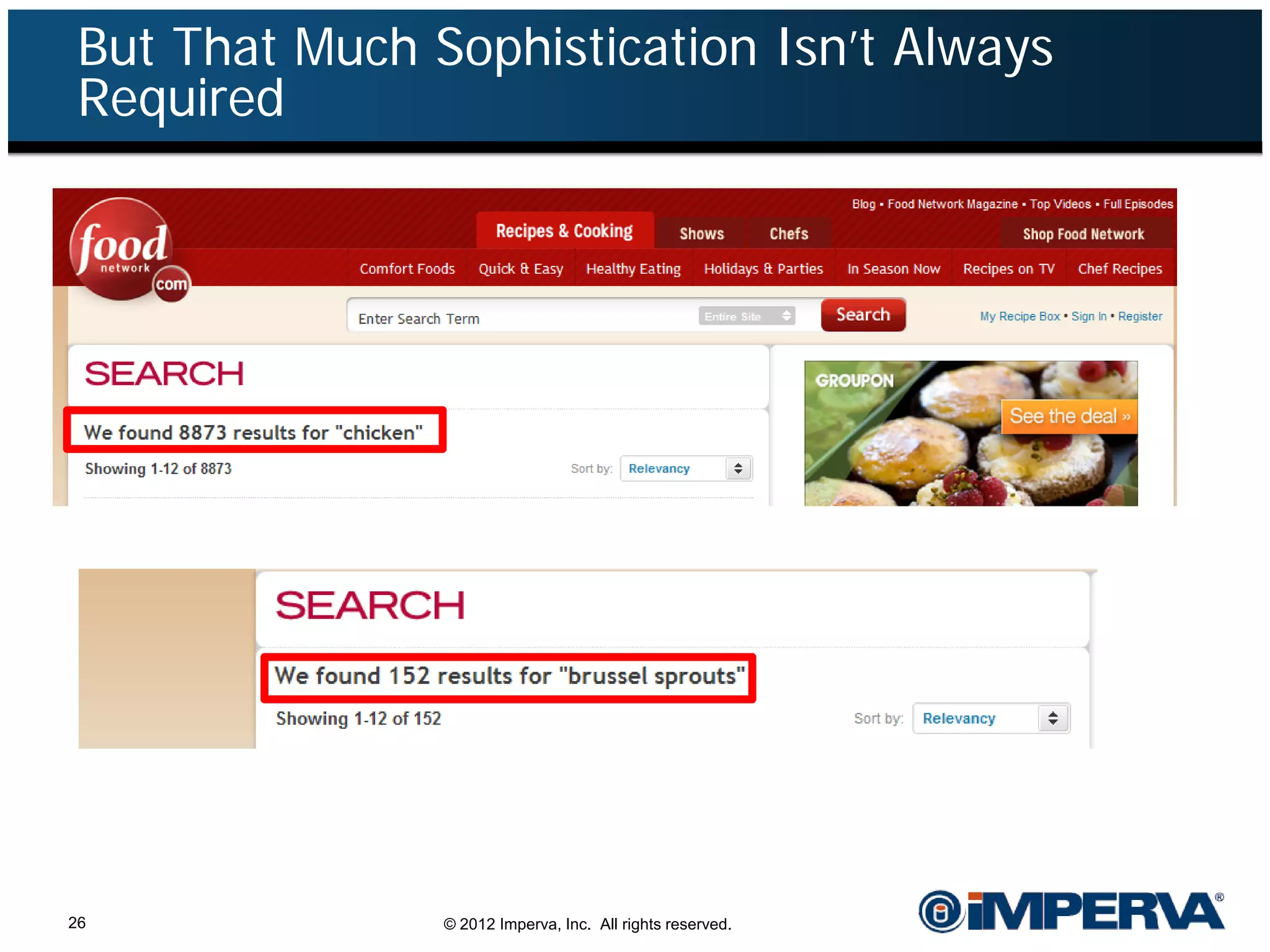
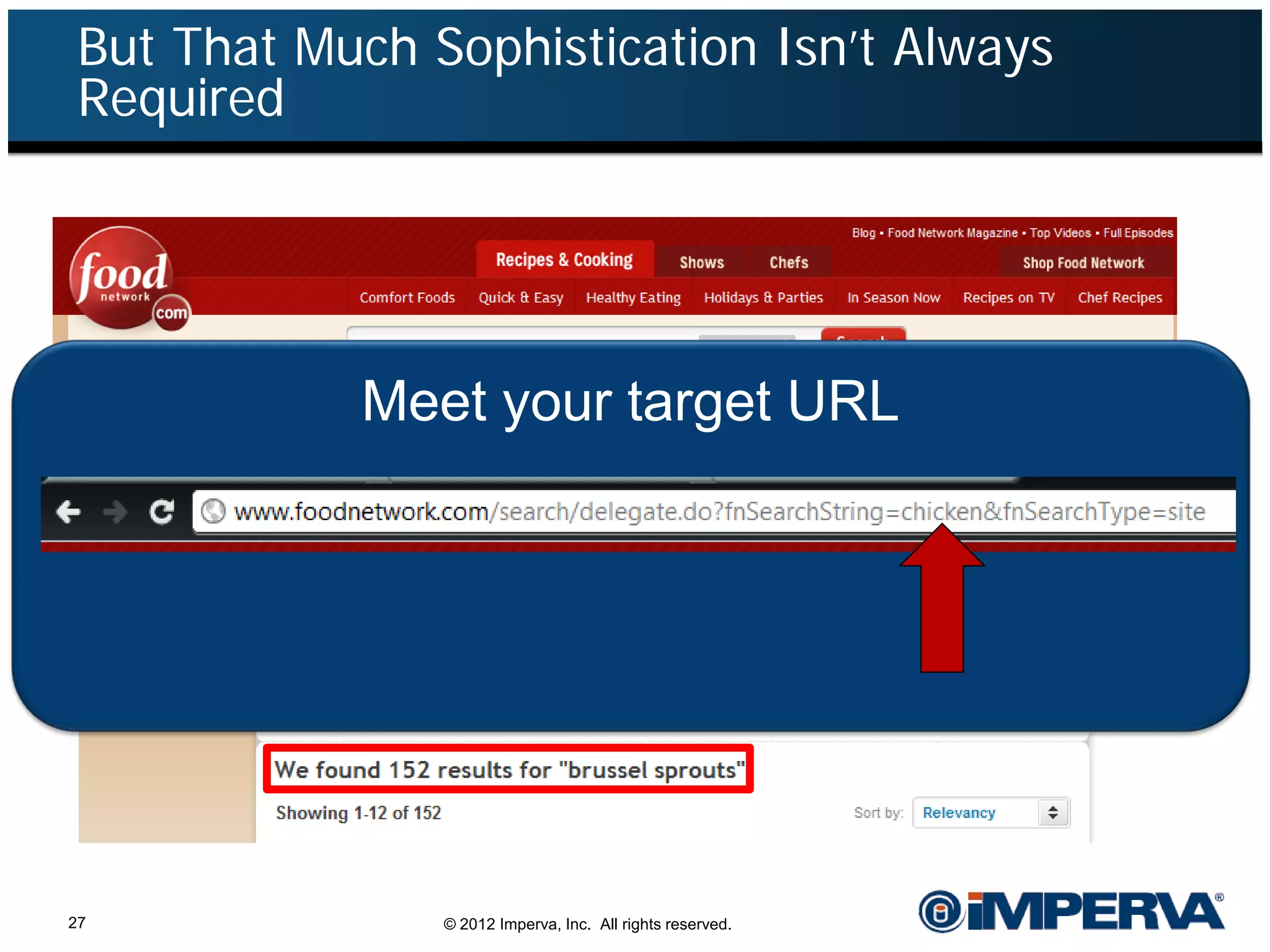
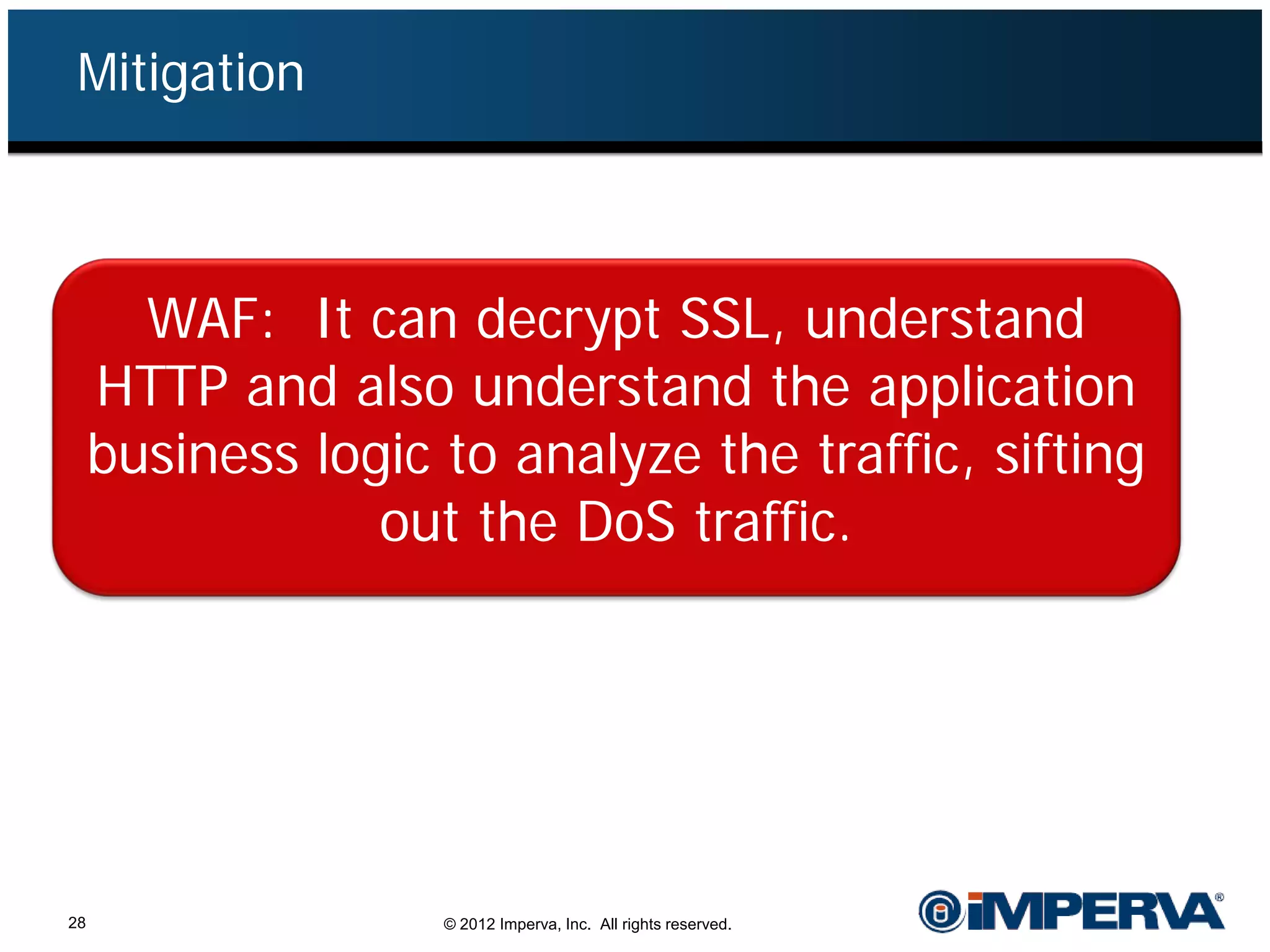
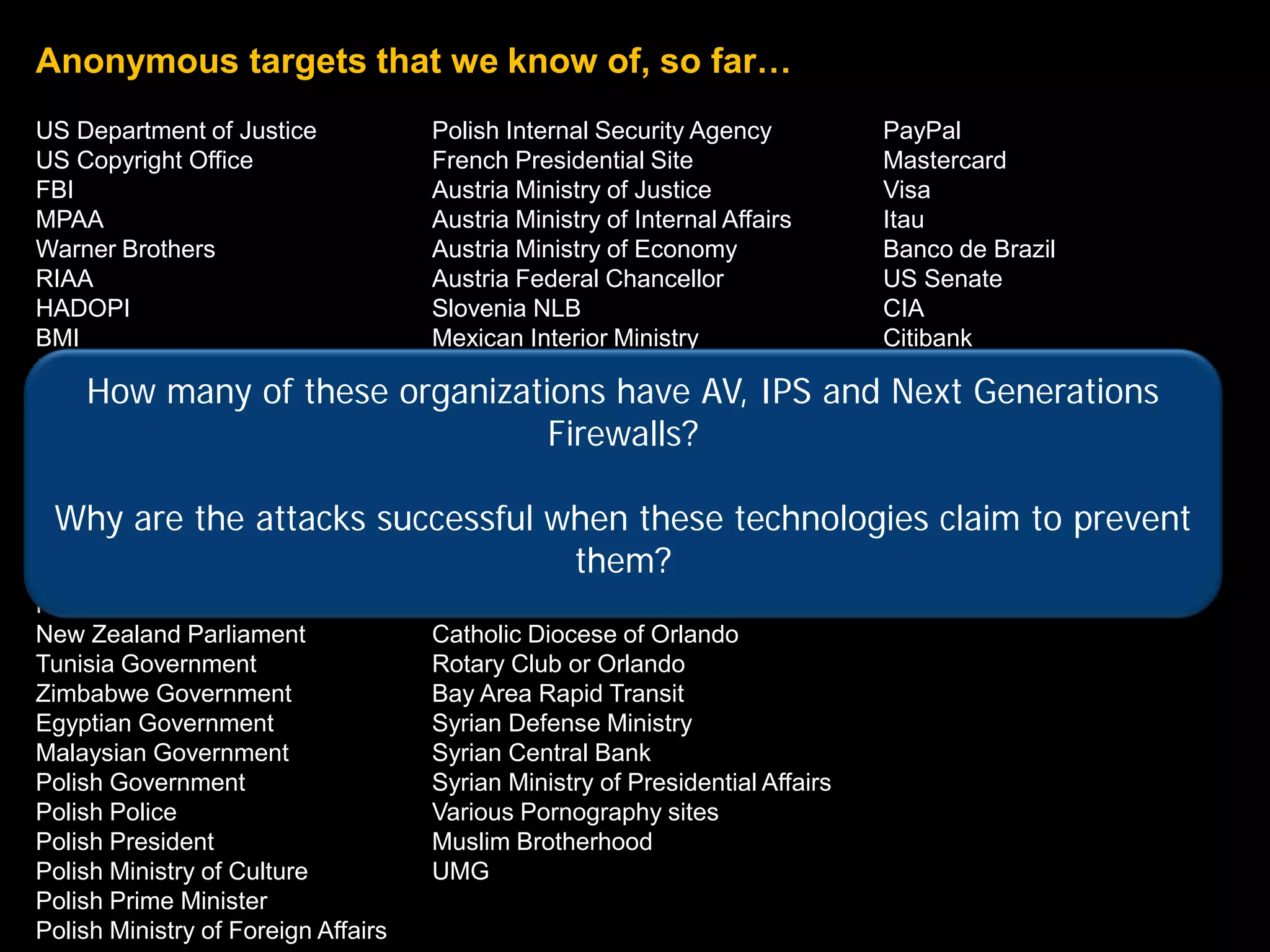
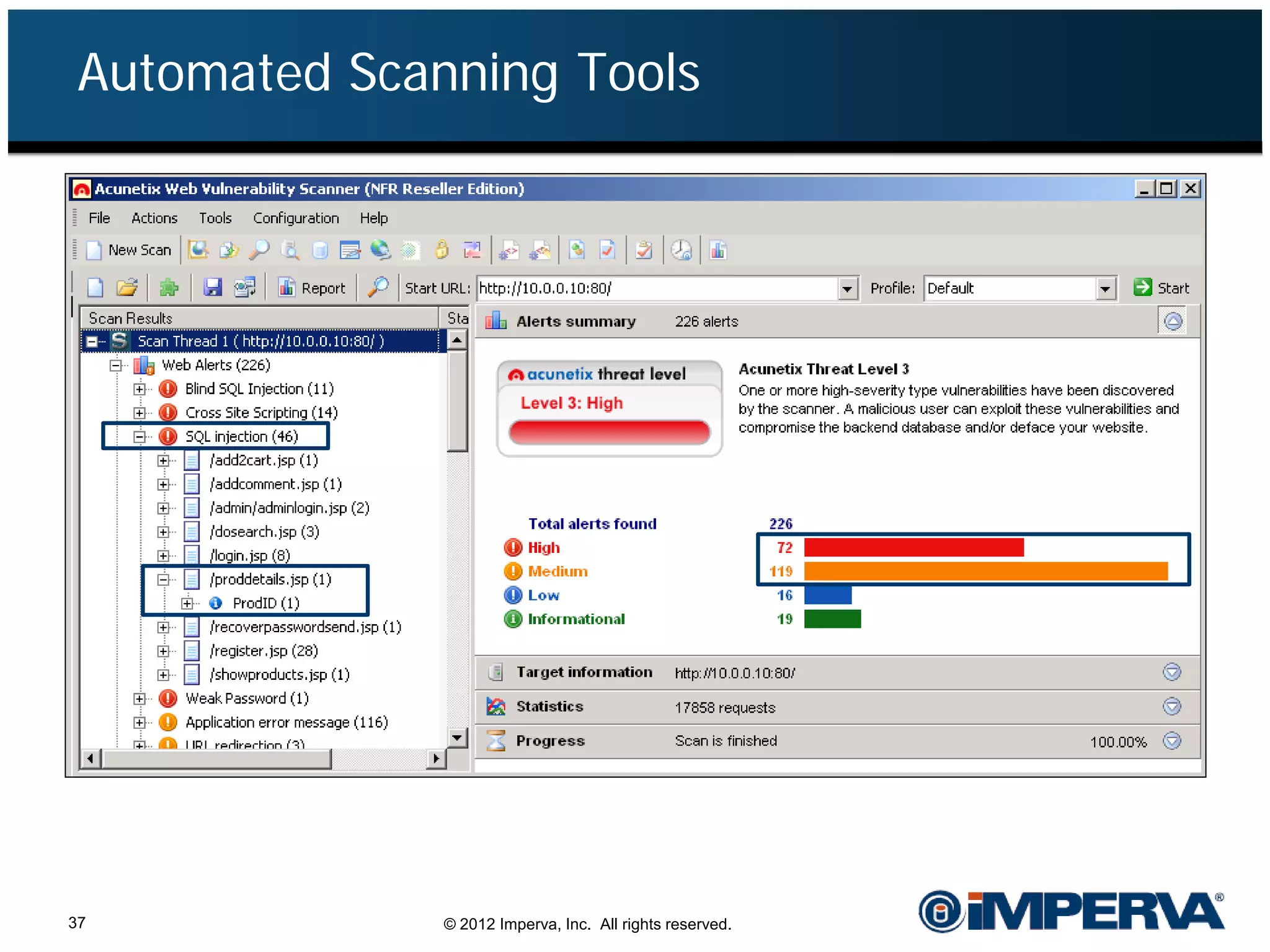
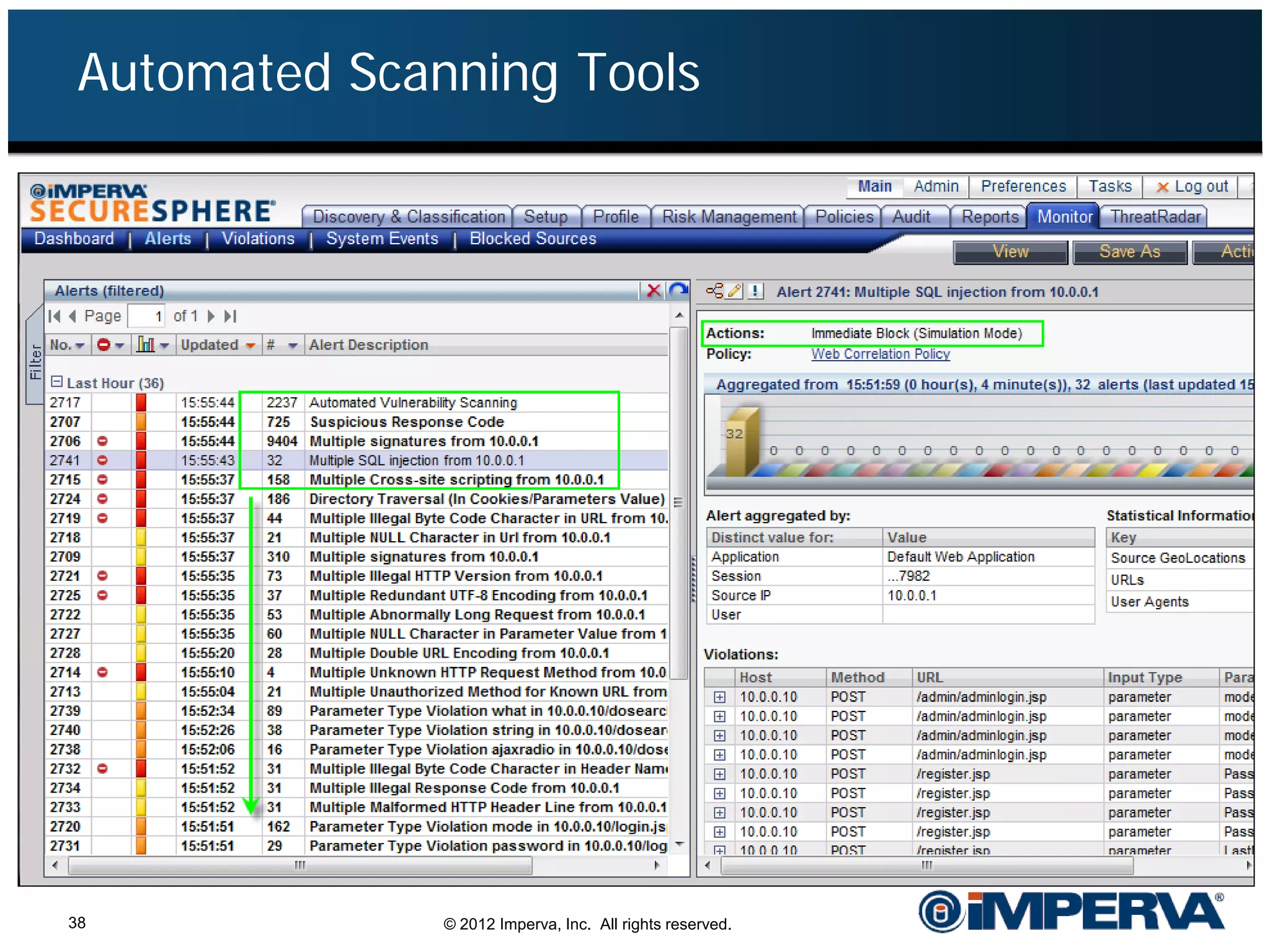
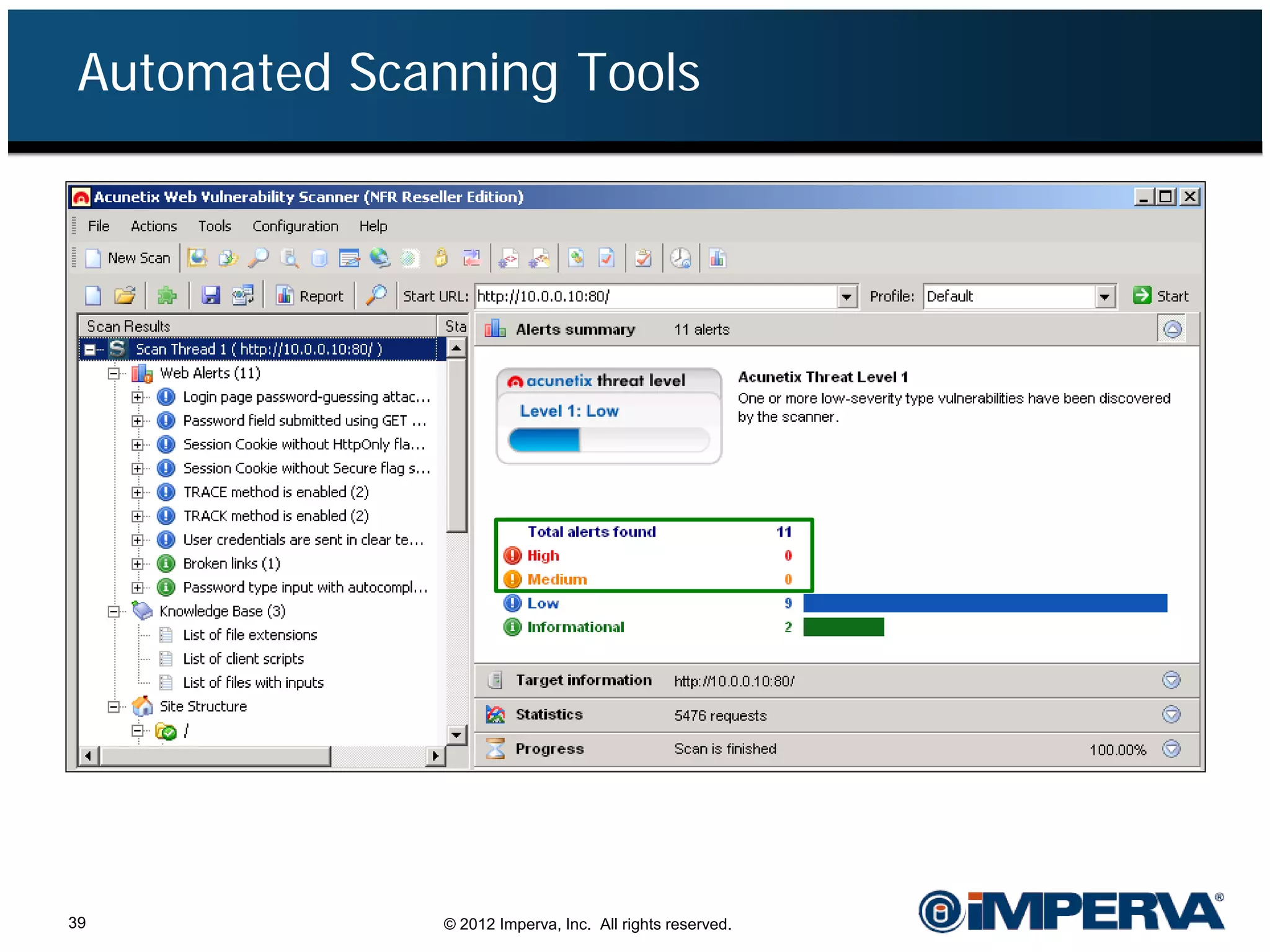
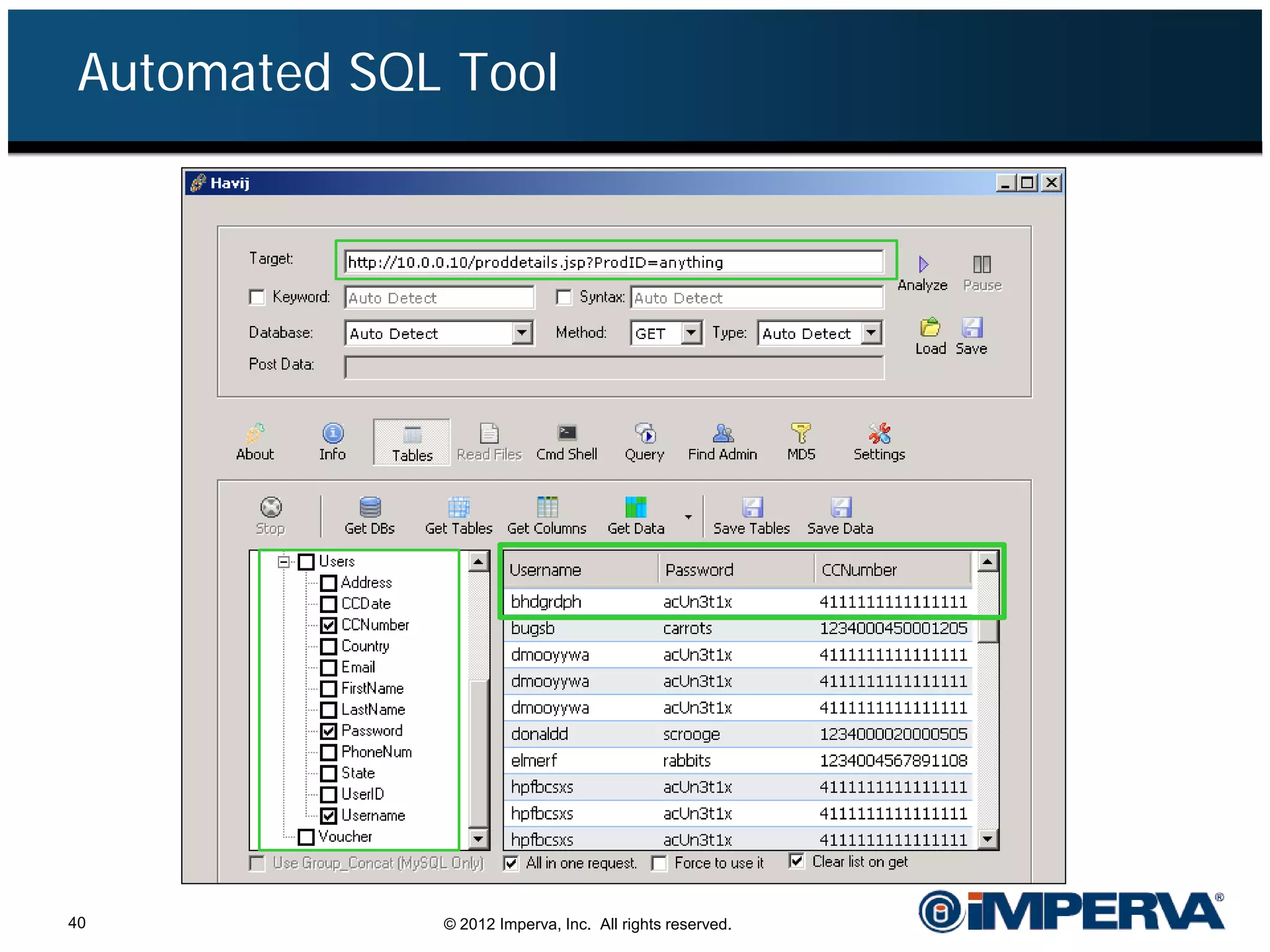
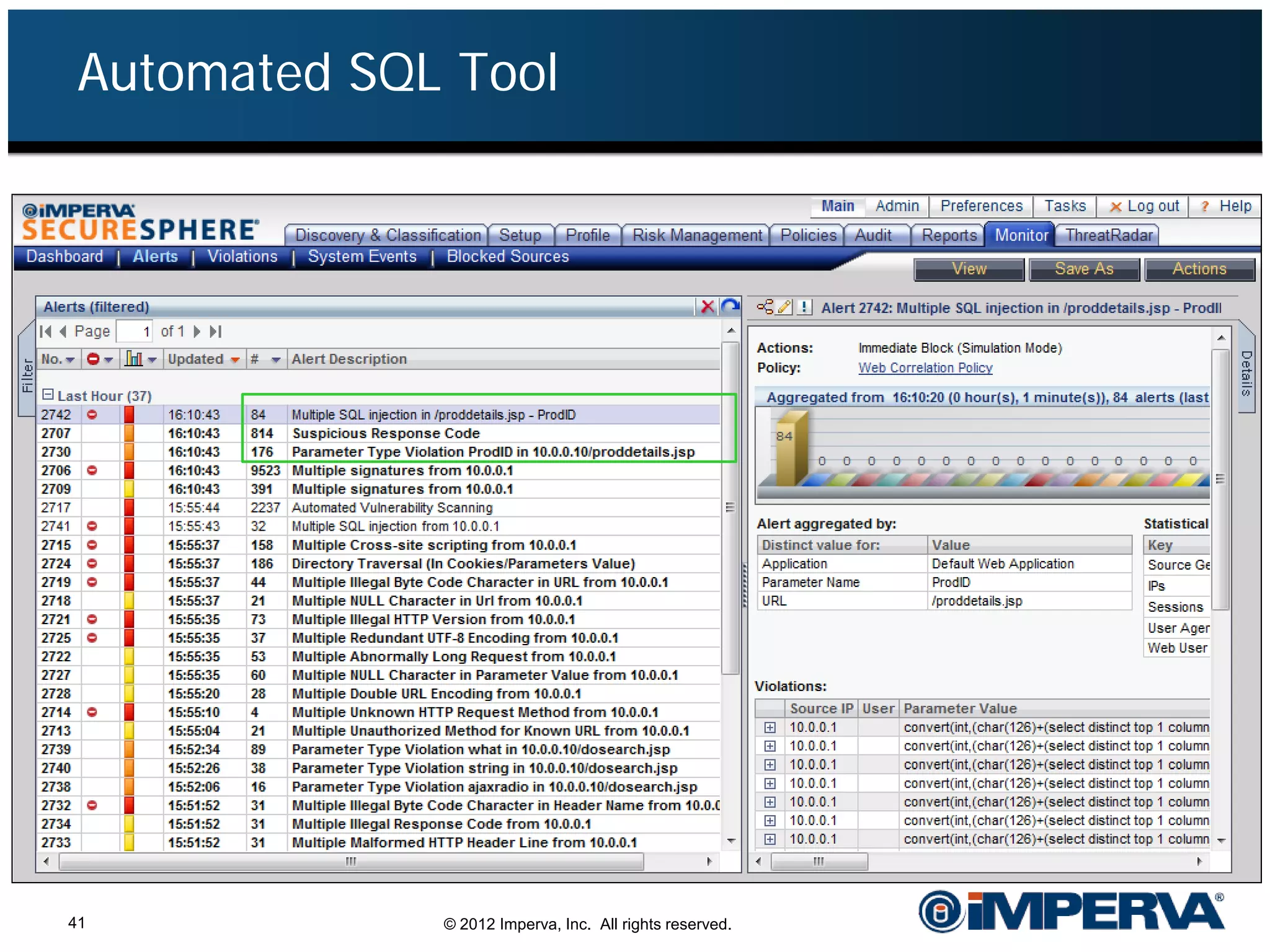
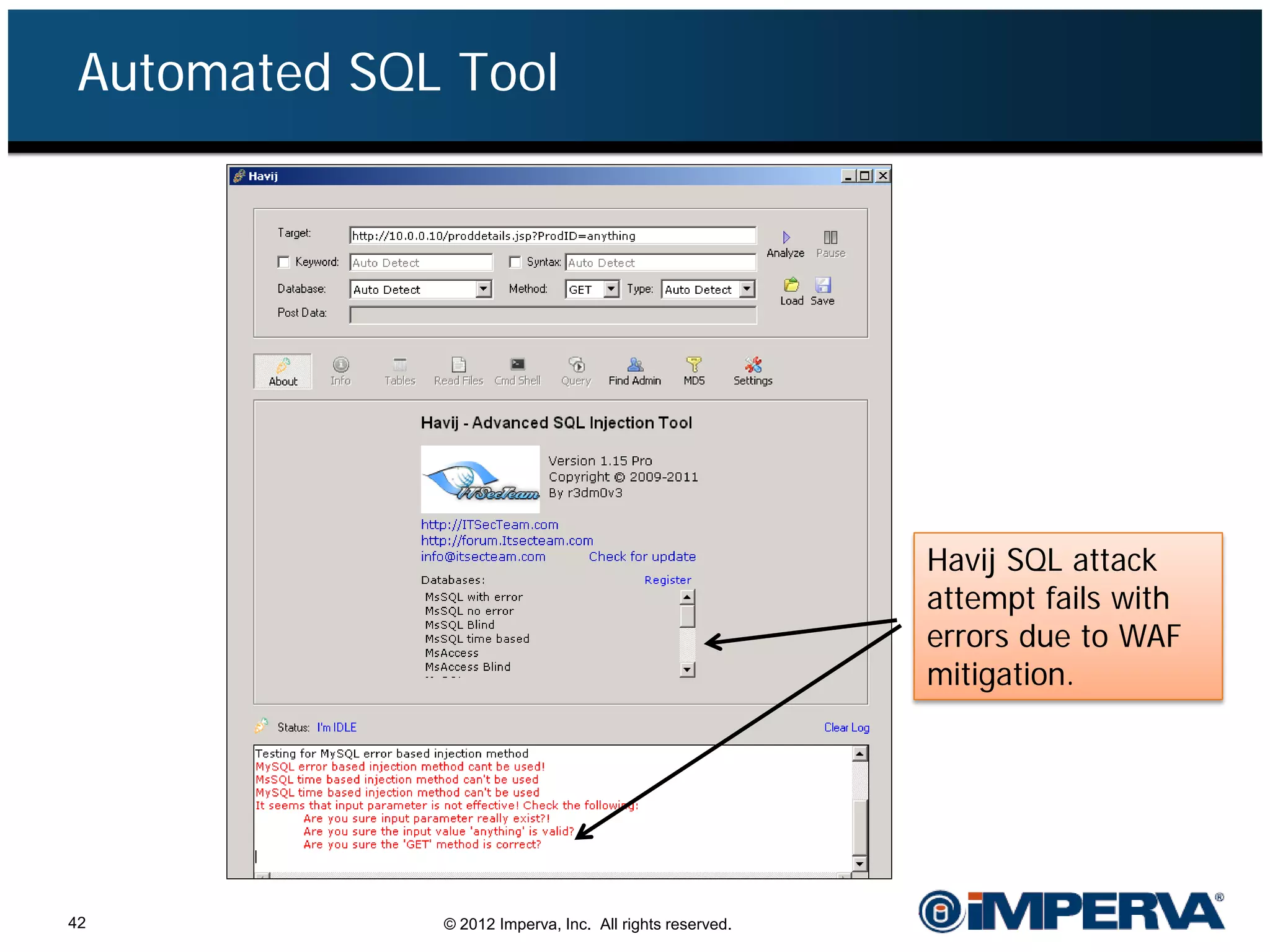
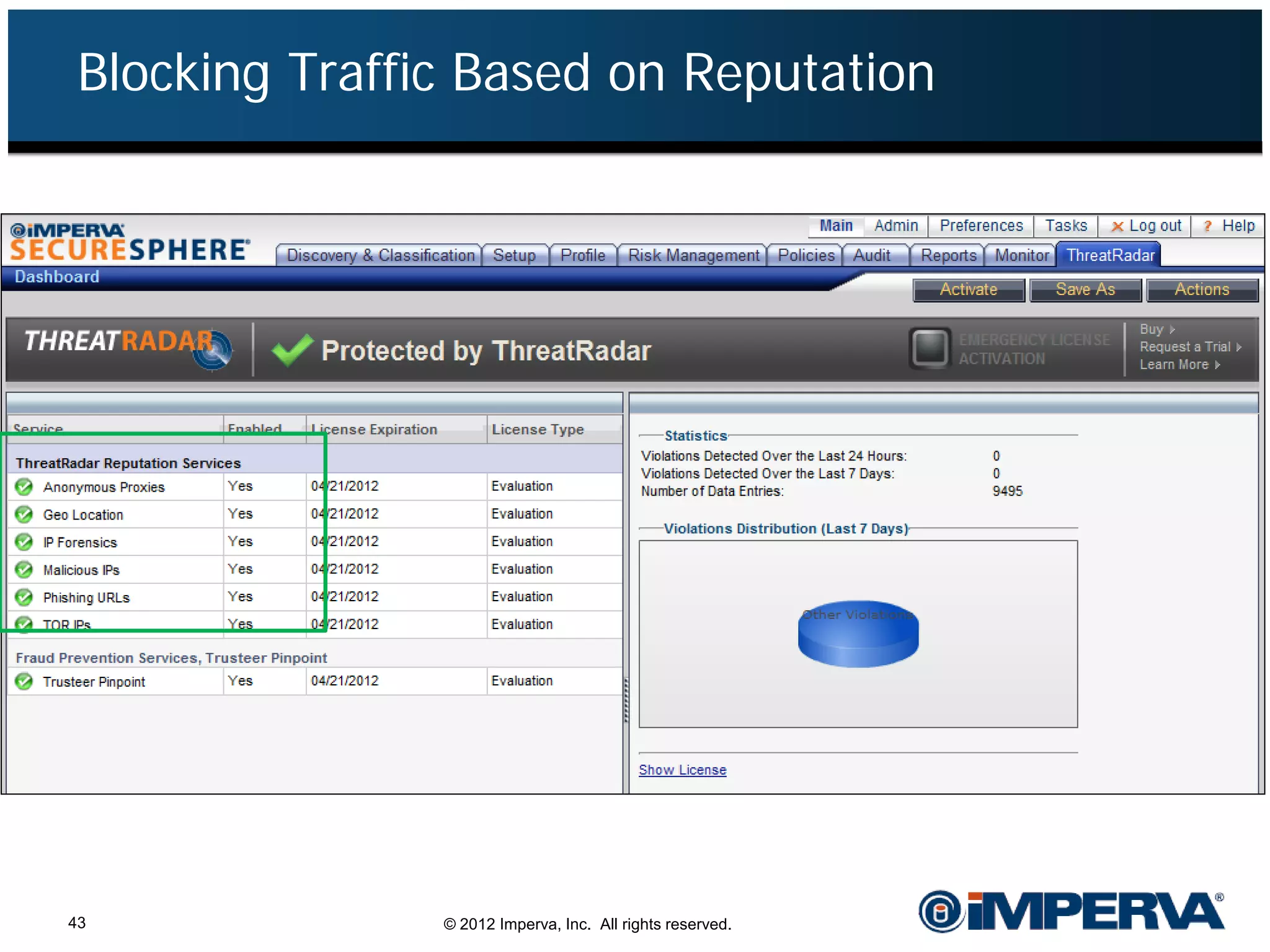
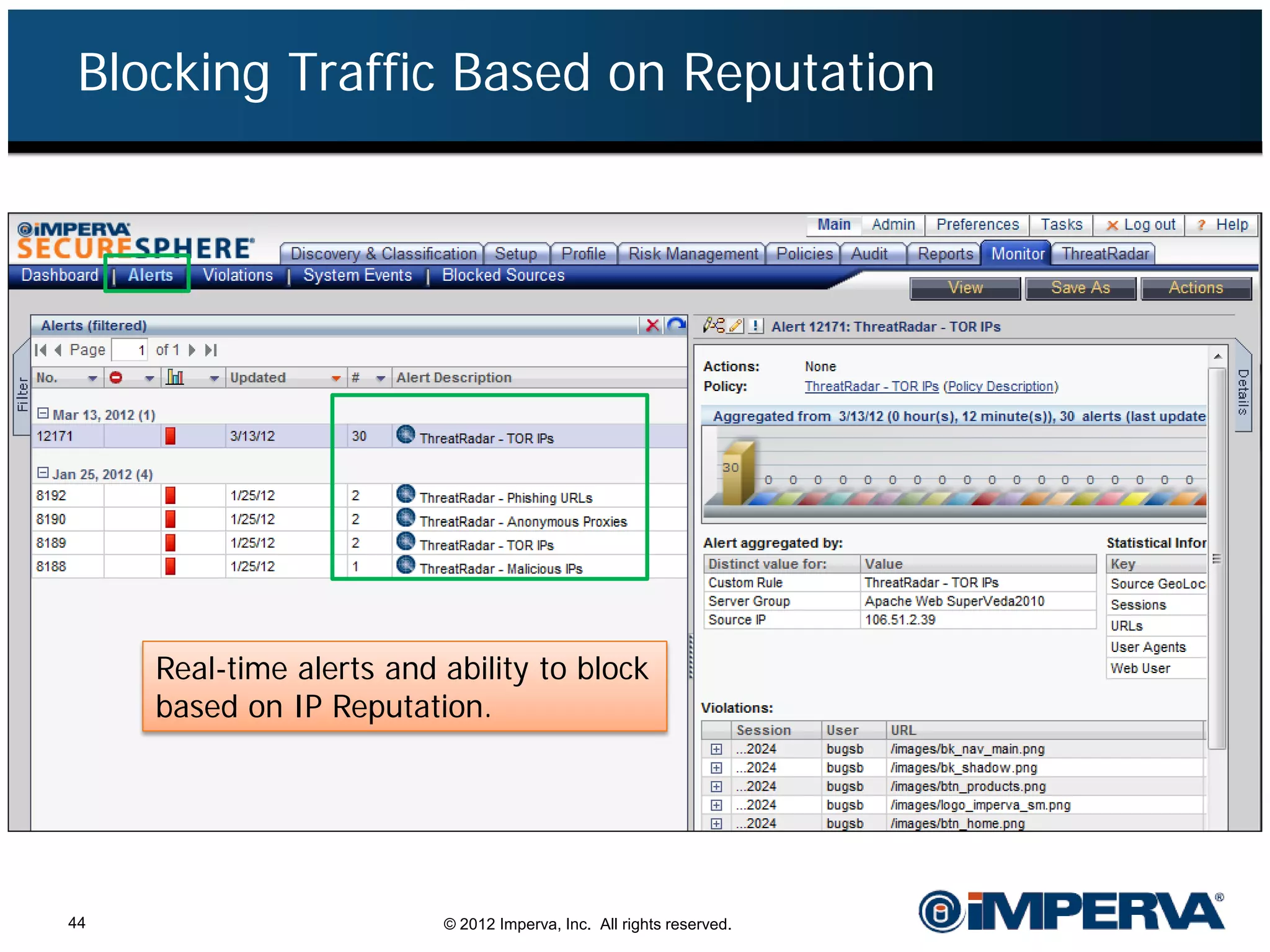
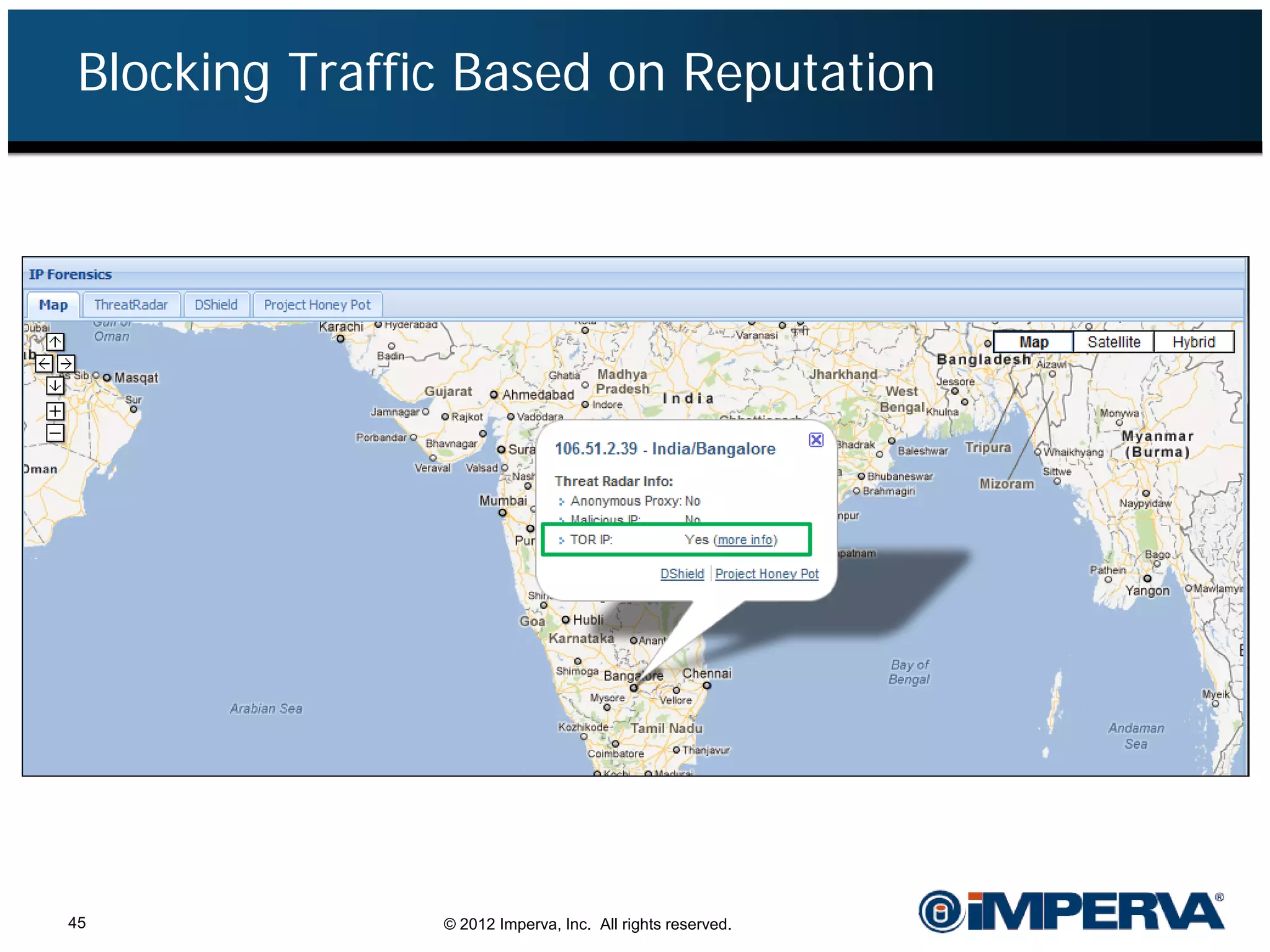
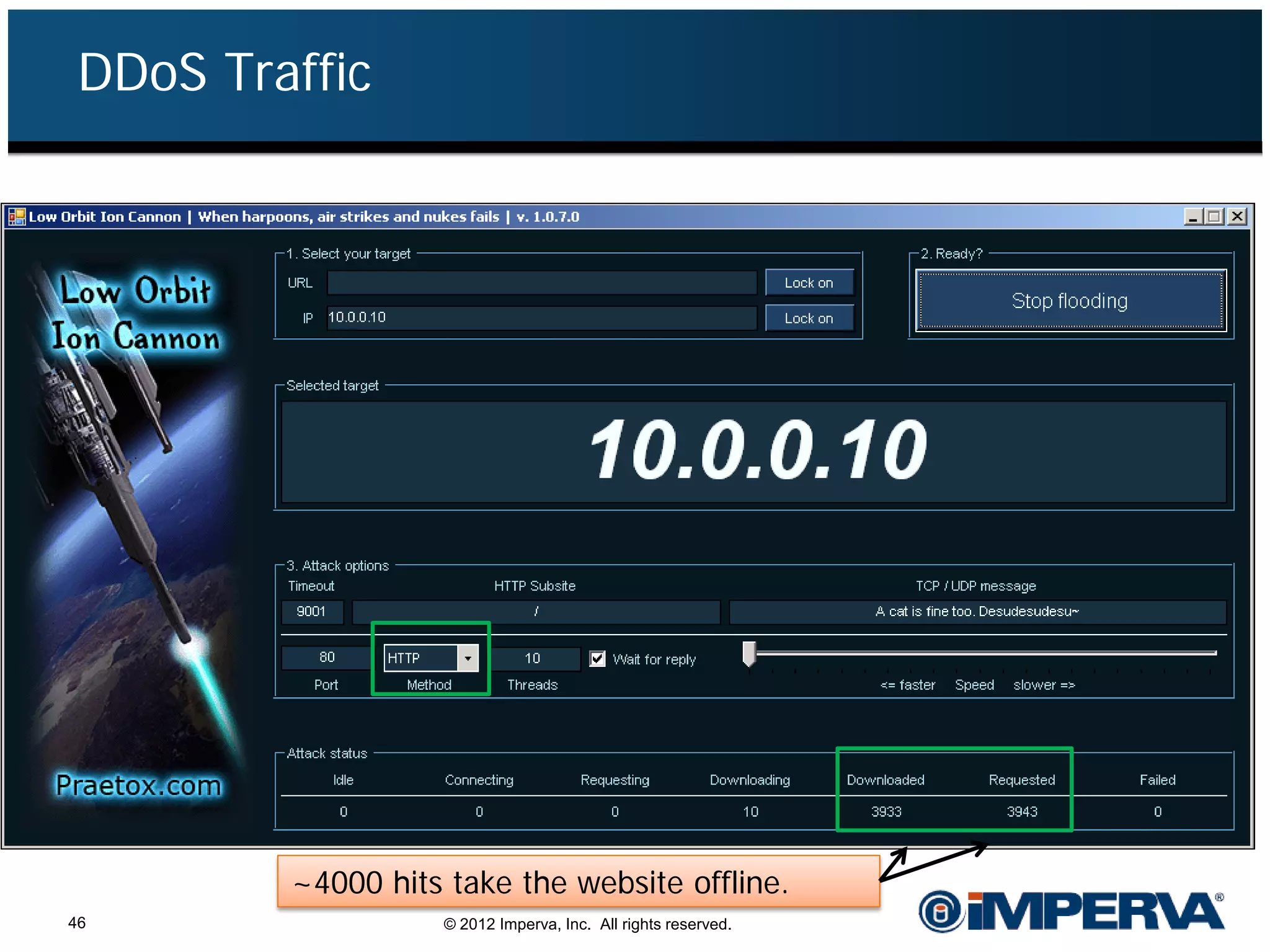
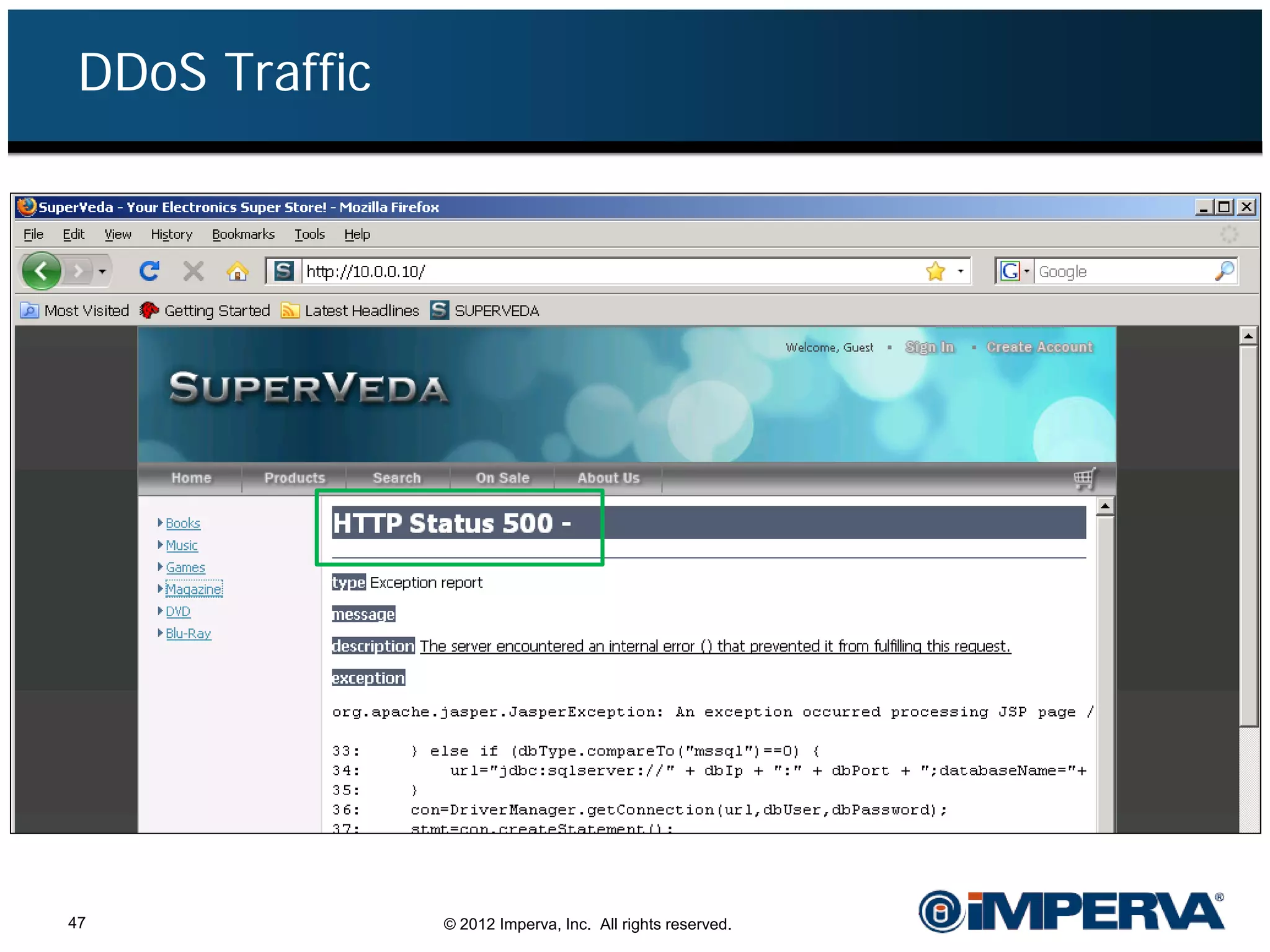
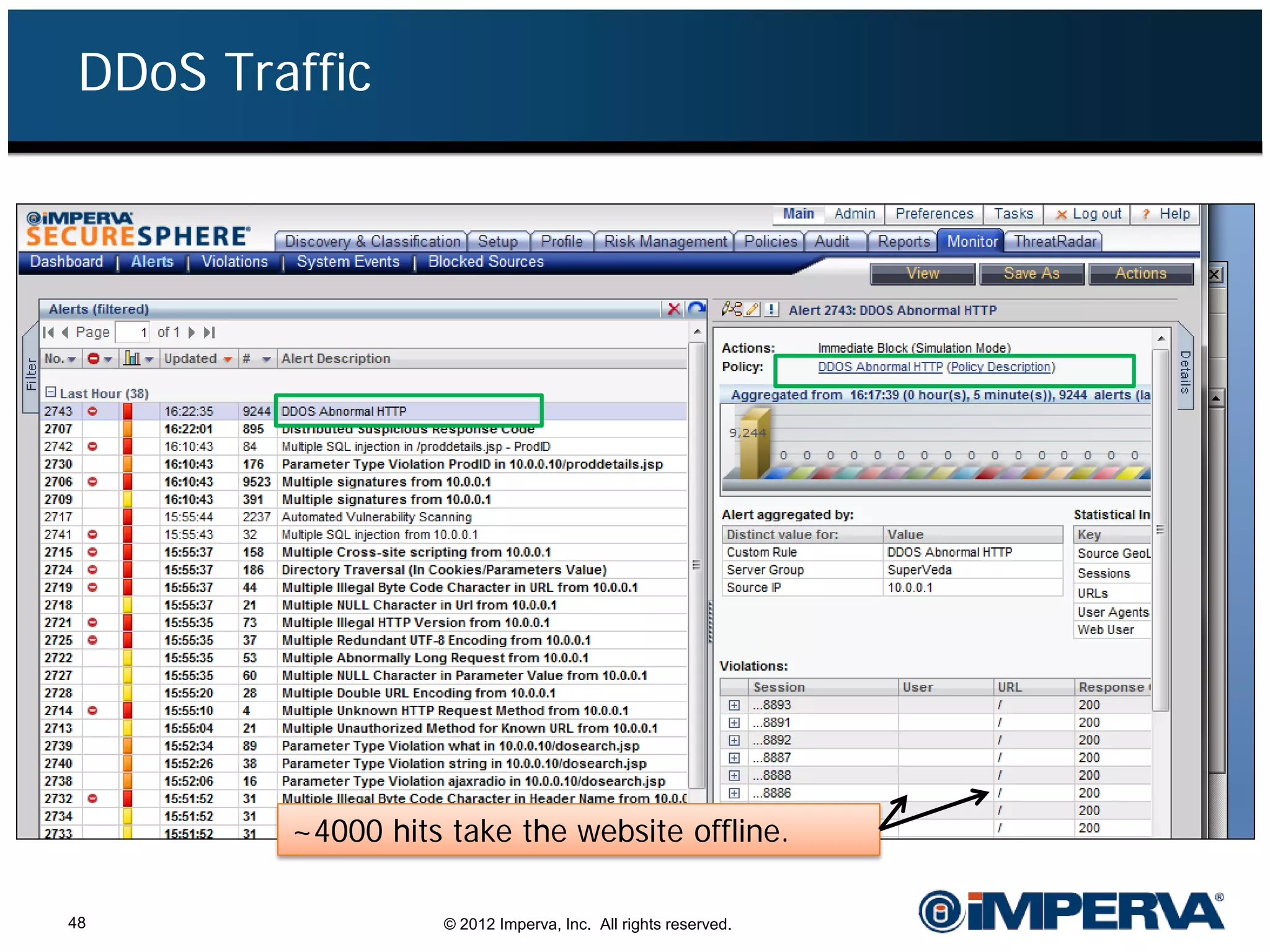
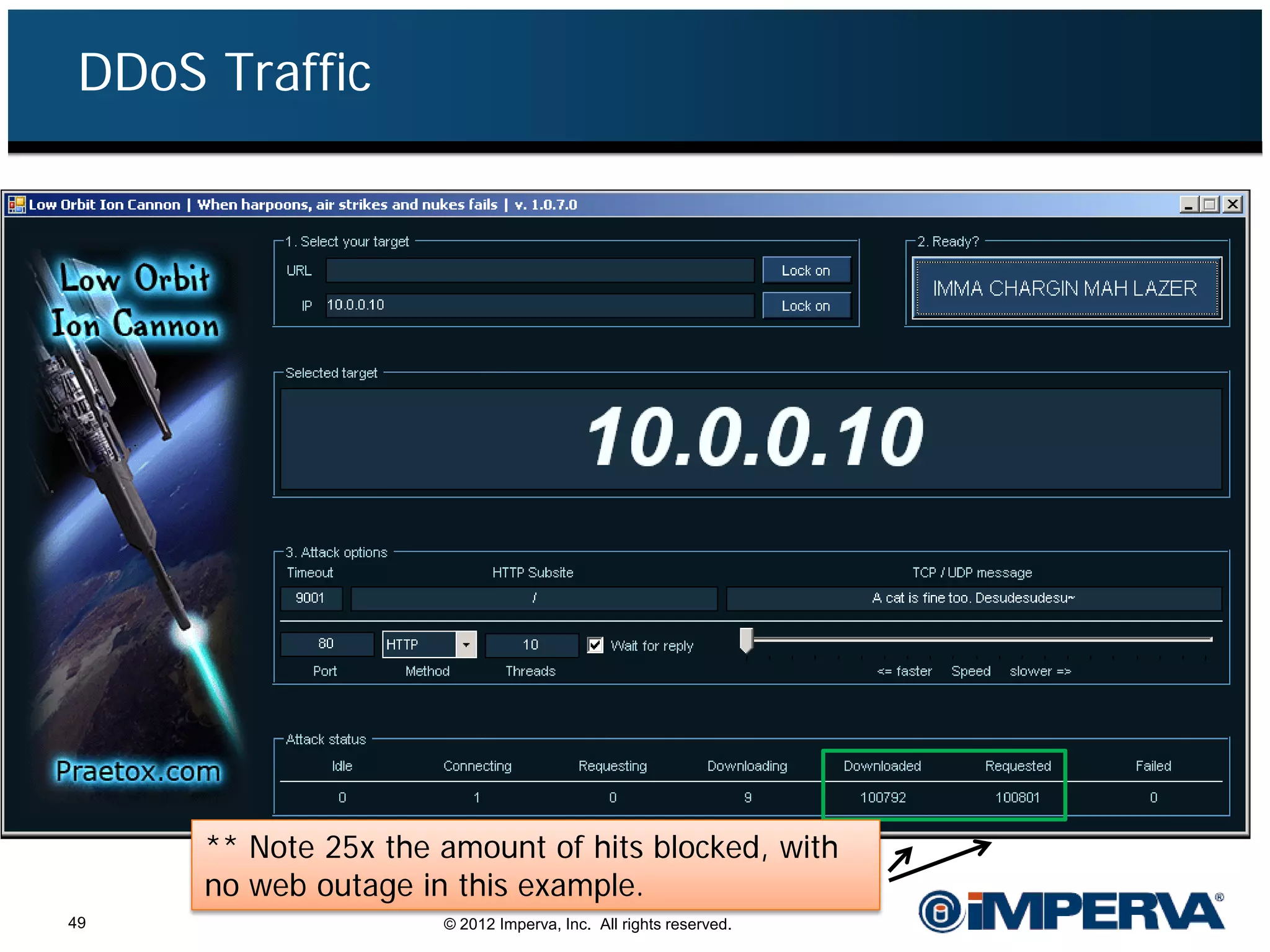
The document provides an overview of a hacktivist attack attributed to the group Anonymous, detailing their recruitment, attack methodology, and defenses used. The attack occurred in 2011 over 25 days but ultimately did not succeed, despite employing various tactics including denial of service (DDoS) and application vulnerabilities. It emphasizes the effectiveness of web application firewalls (WAFs) against such attacks and highlights the limitations of traditional cyber security measures.