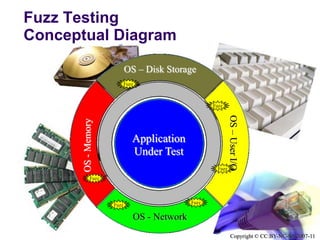
The document presents an overview of fault models and fuzz testing techniques aimed at evaluating software robustness, dependability, and security. It discusses various approaches, examples of faults, and common pitfalls associated with these testing methods. Additionally, it highlights the importance of using specific tools for fault injection and fuzz testing to uncover hard-to-detect bugs.