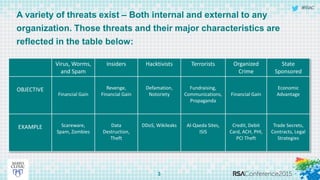
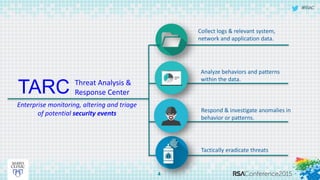
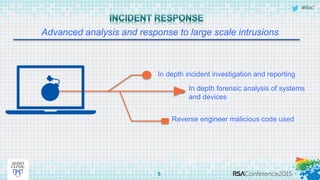
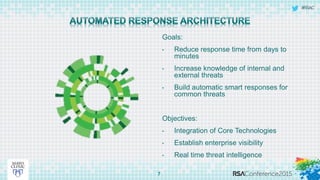
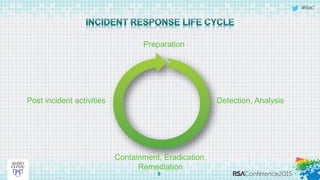
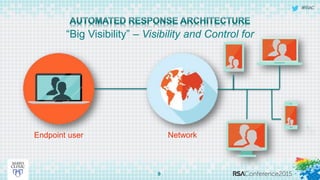
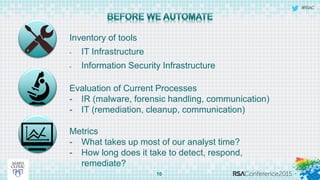
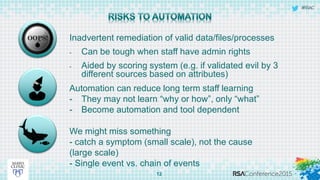
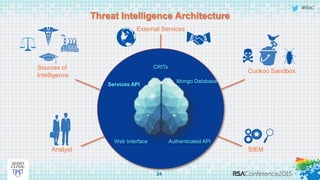
This document discusses an approach to automating incident response through integrated technologies. It begins by outlining common threats faced by organizations, then describes a Threat Analysis & Response Center (TARC) for monitoring, detecting, and responding to anomalies. Various use cases are presented where an automated response architecture could reduce response times from weeks to minutes by integrating tools for detection, analysis, containment and remediation. Key goals are reducing response times, increasing threat intelligence and establishing enterprise visibility.