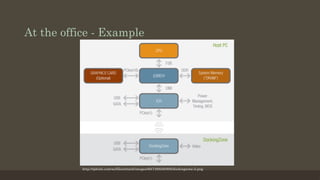
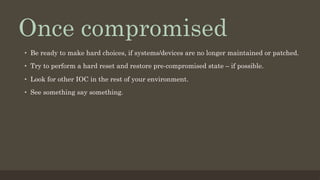
This document discusses emerging security threats in an increasingly connected world. It outlines how technologies in homes, vehicles, and workplaces are becoming more connected and integrated with networked devices and services. This brings new conveniences but also creates new security vulnerabilities and potential threats. Examples discussed include ransomware targeting smart home appliances, hacking in-vehicle infotainment systems to endanger drivers, and exploiting wireless docking stations to perform DMA attacks at offices. The presenters recommend practicing good security hygiene like keeping systems patched and monitoring for indicators of compromise, as well as designing new connected devices with security compromises in mind from the start.