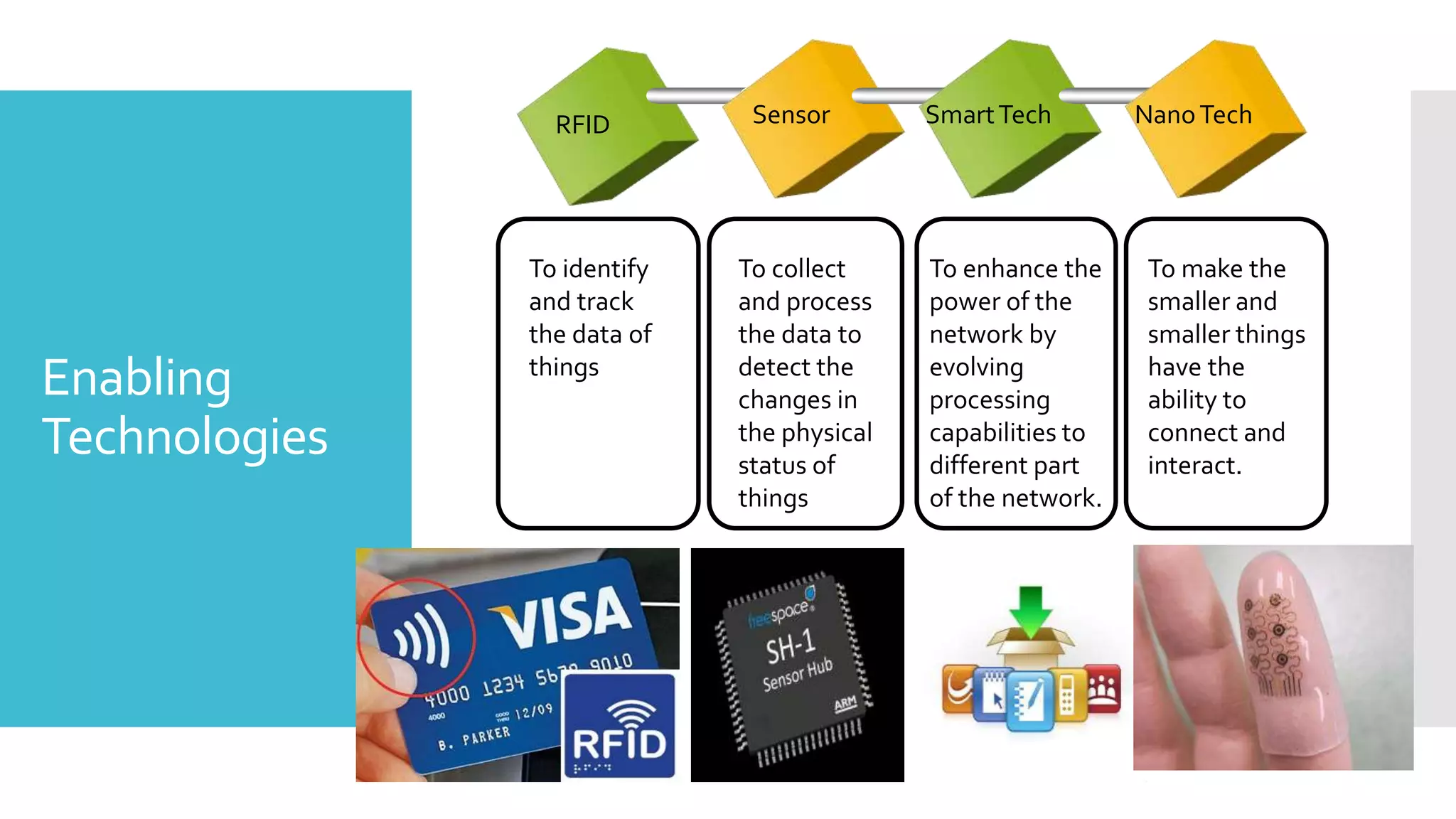
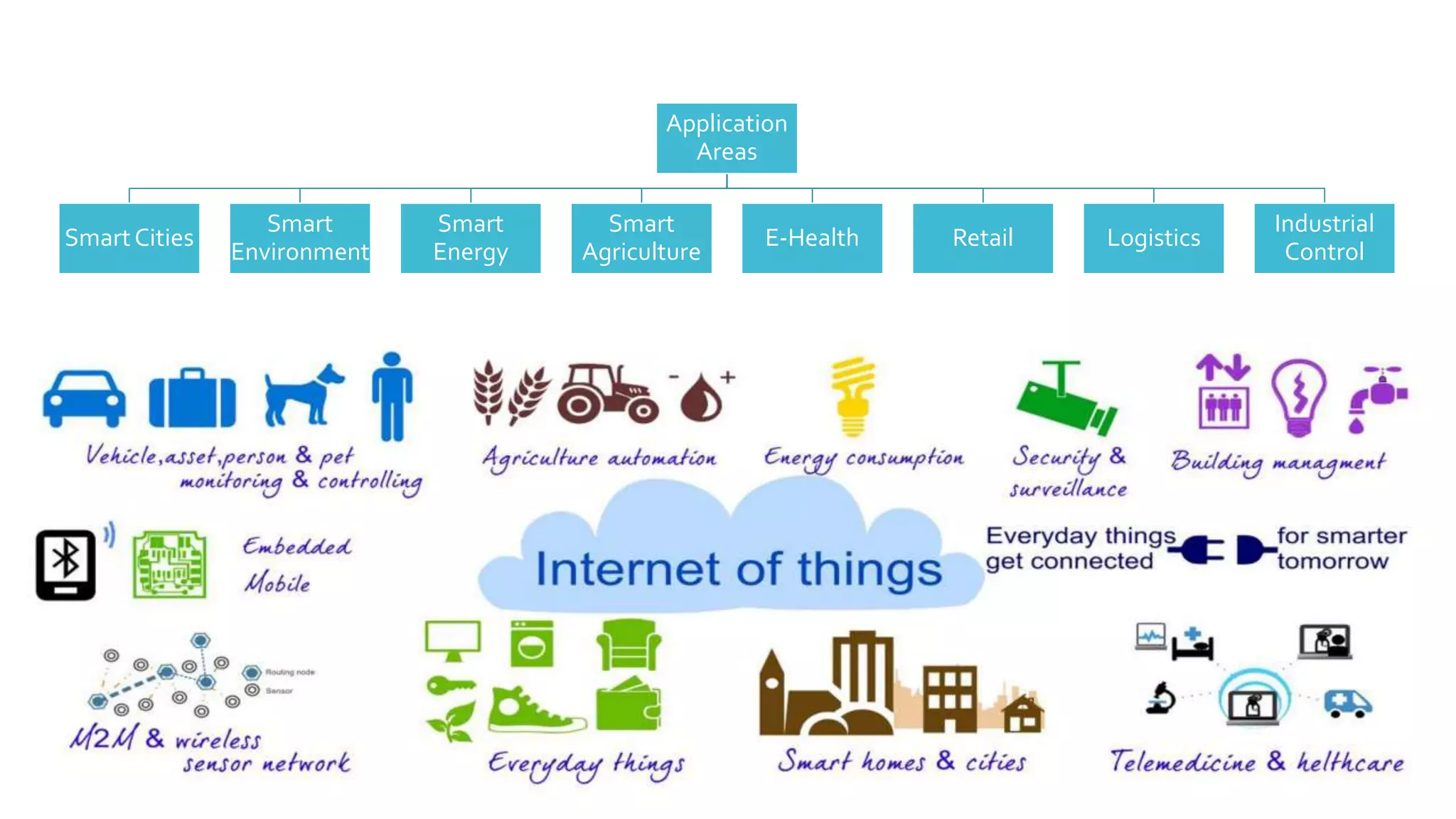
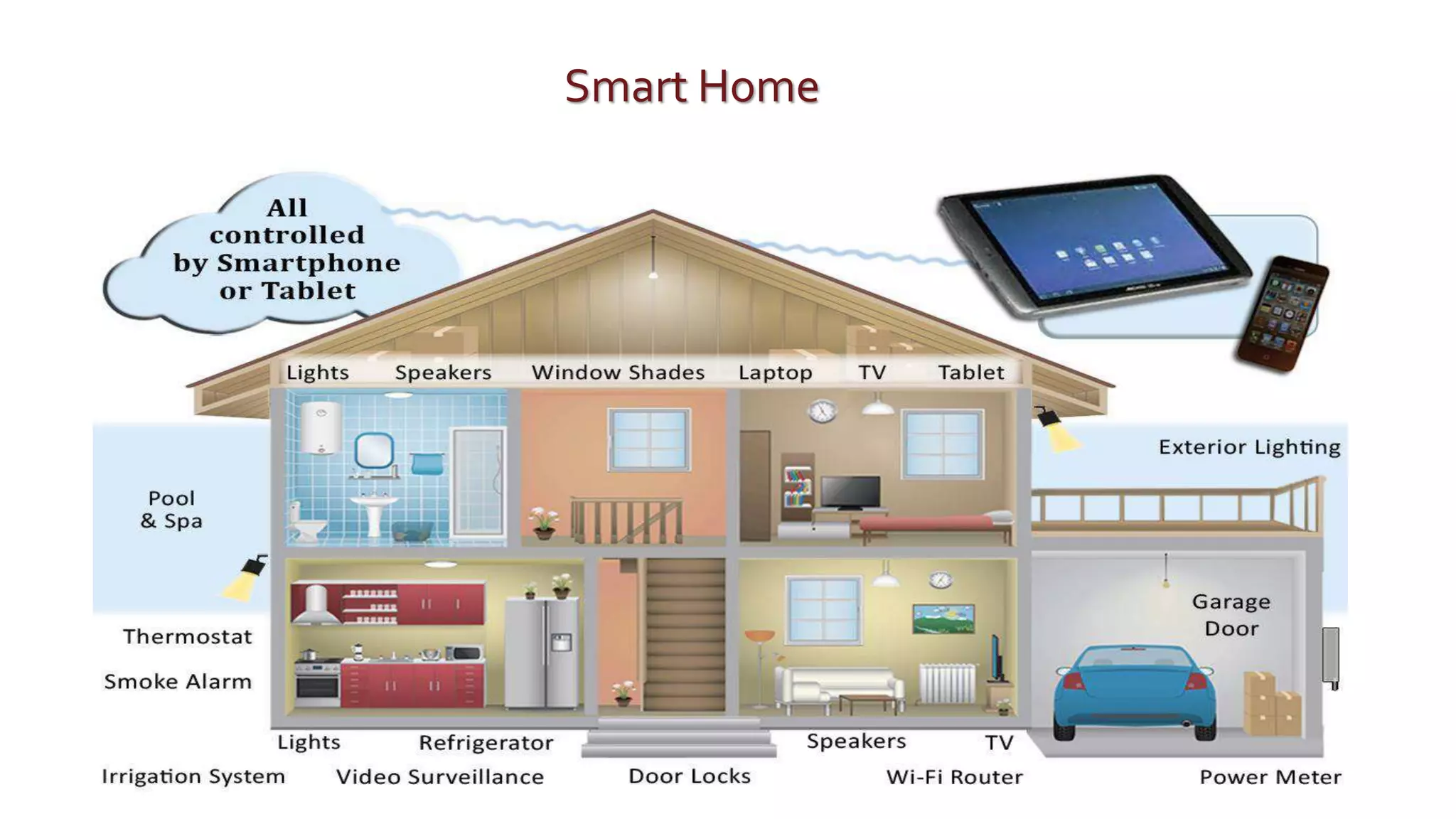
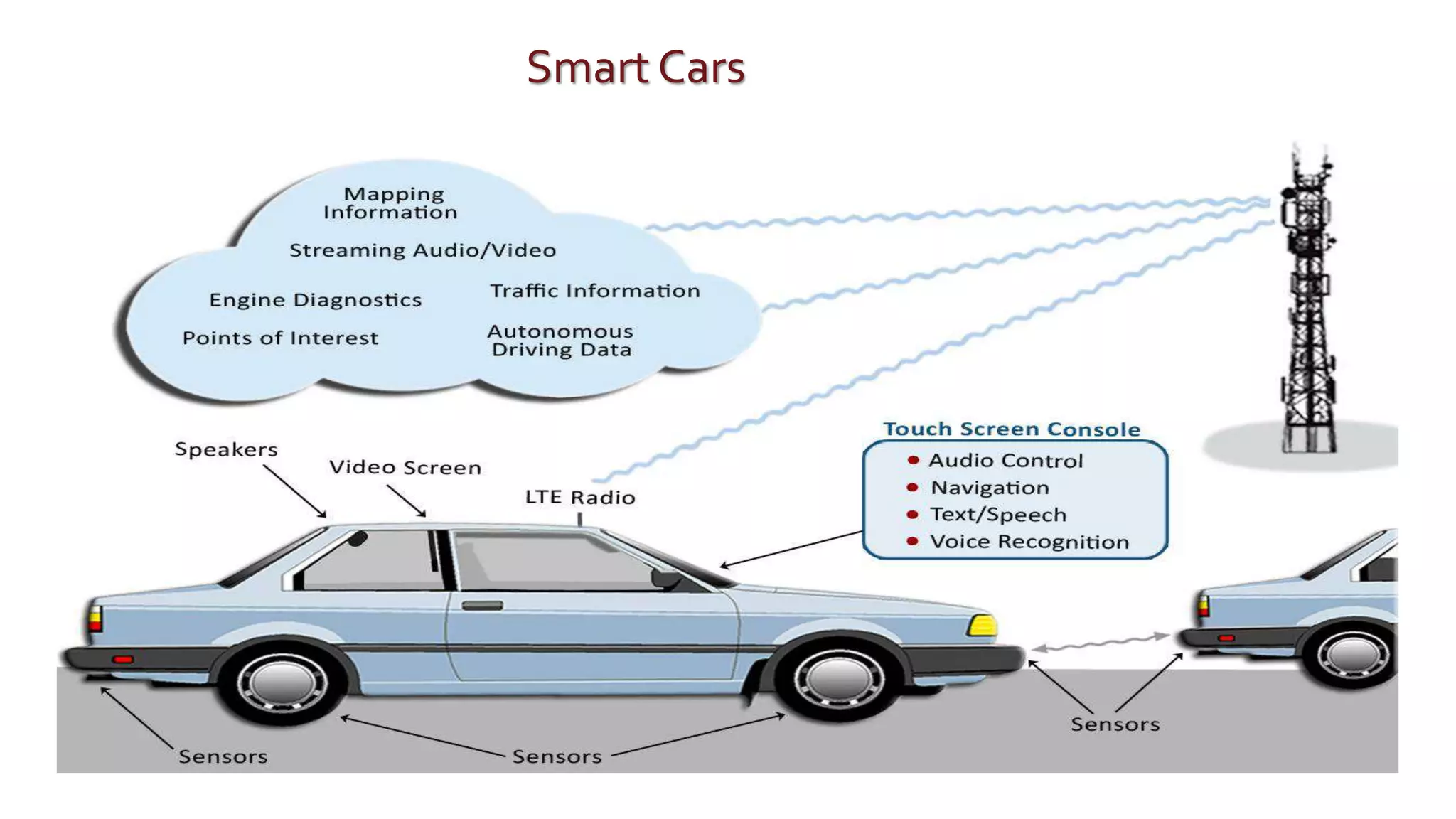
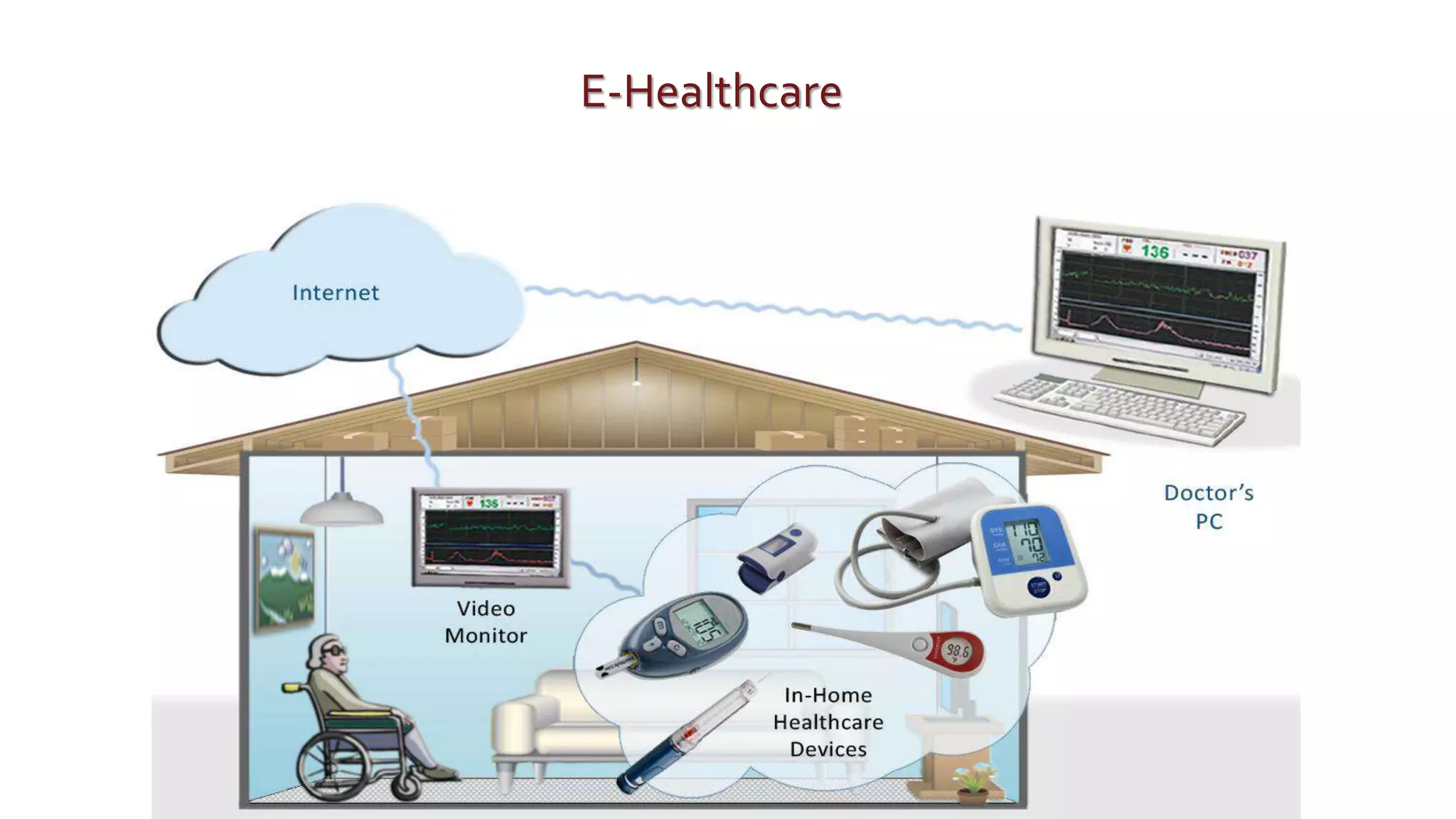
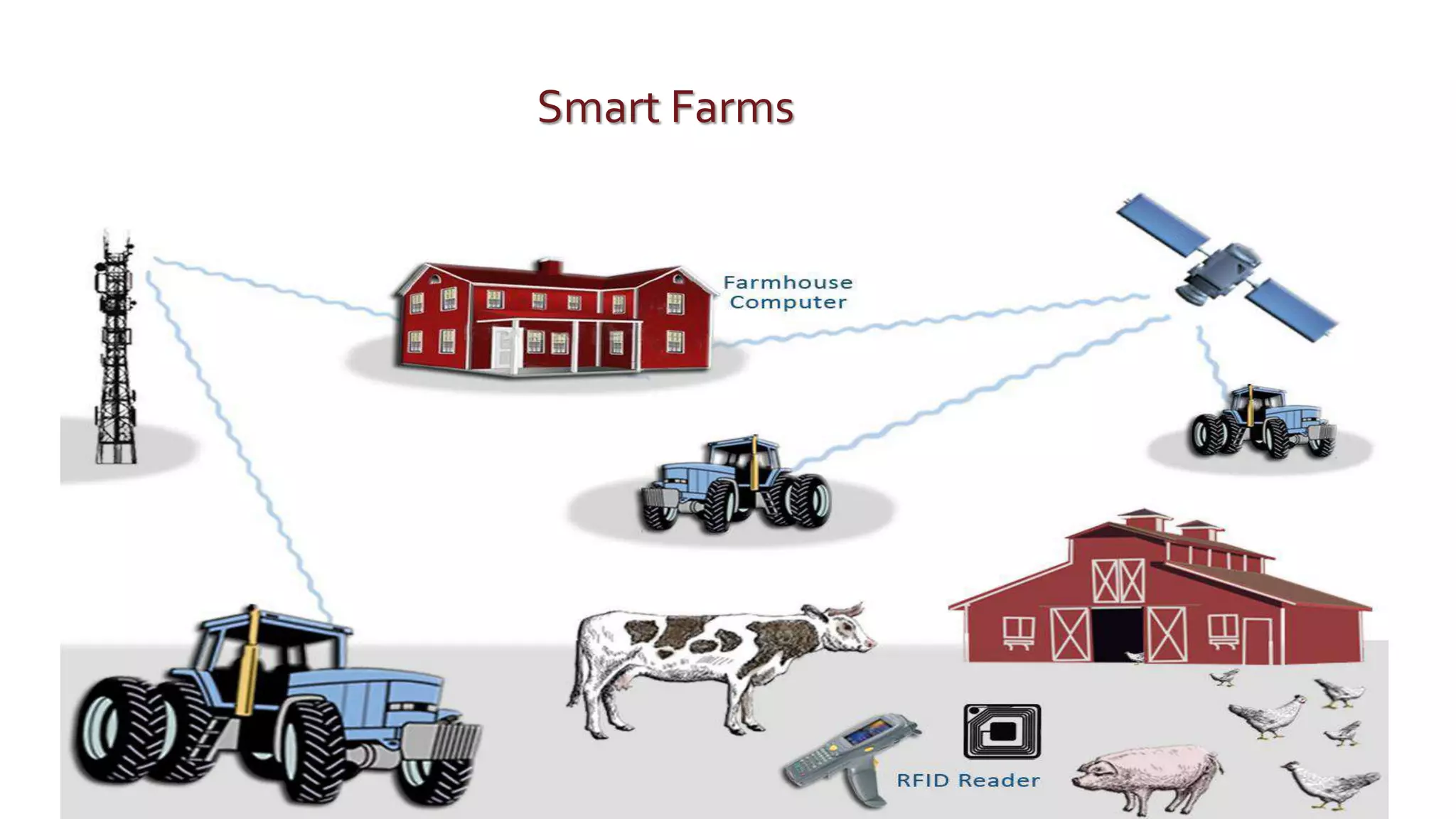
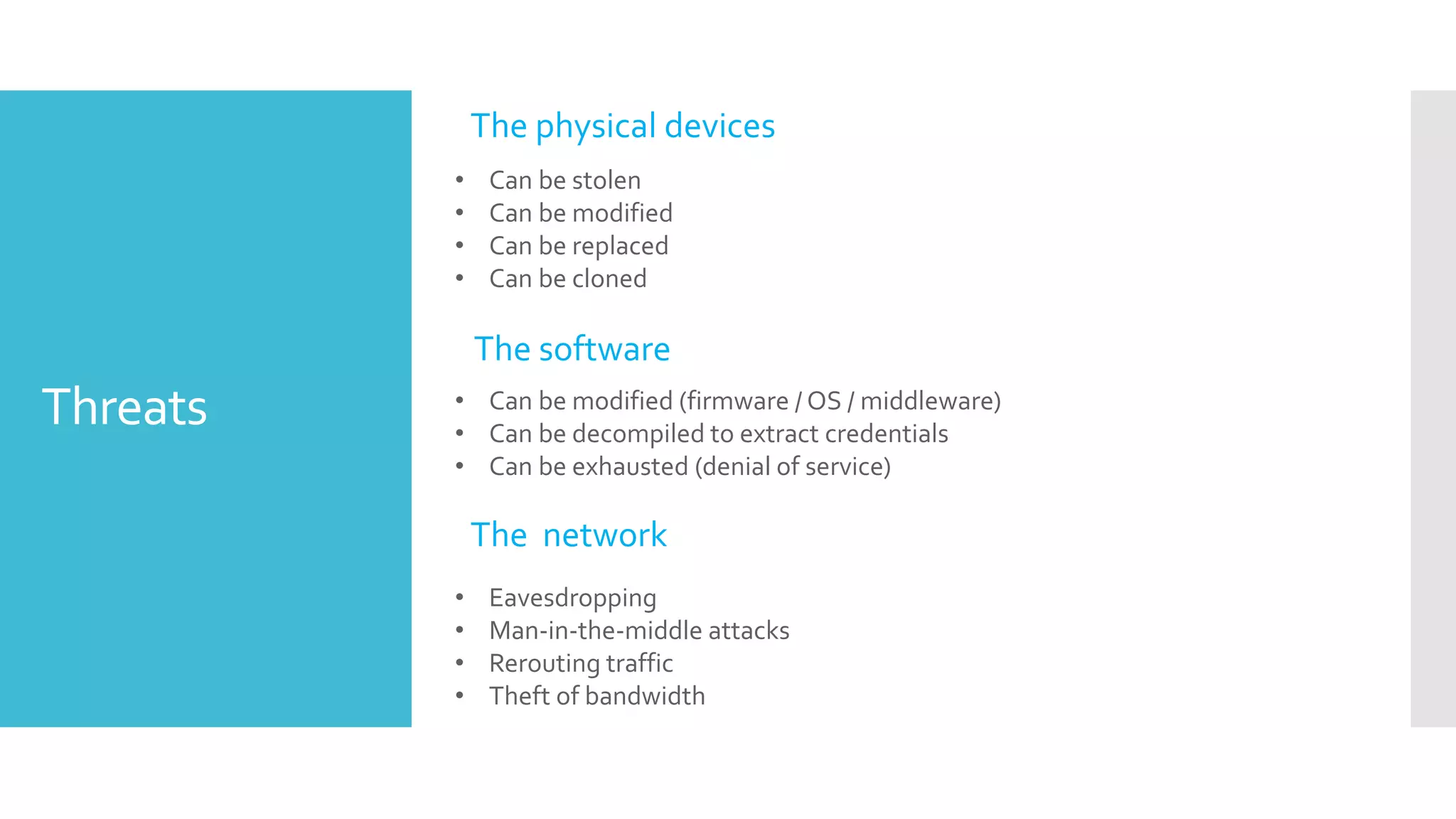
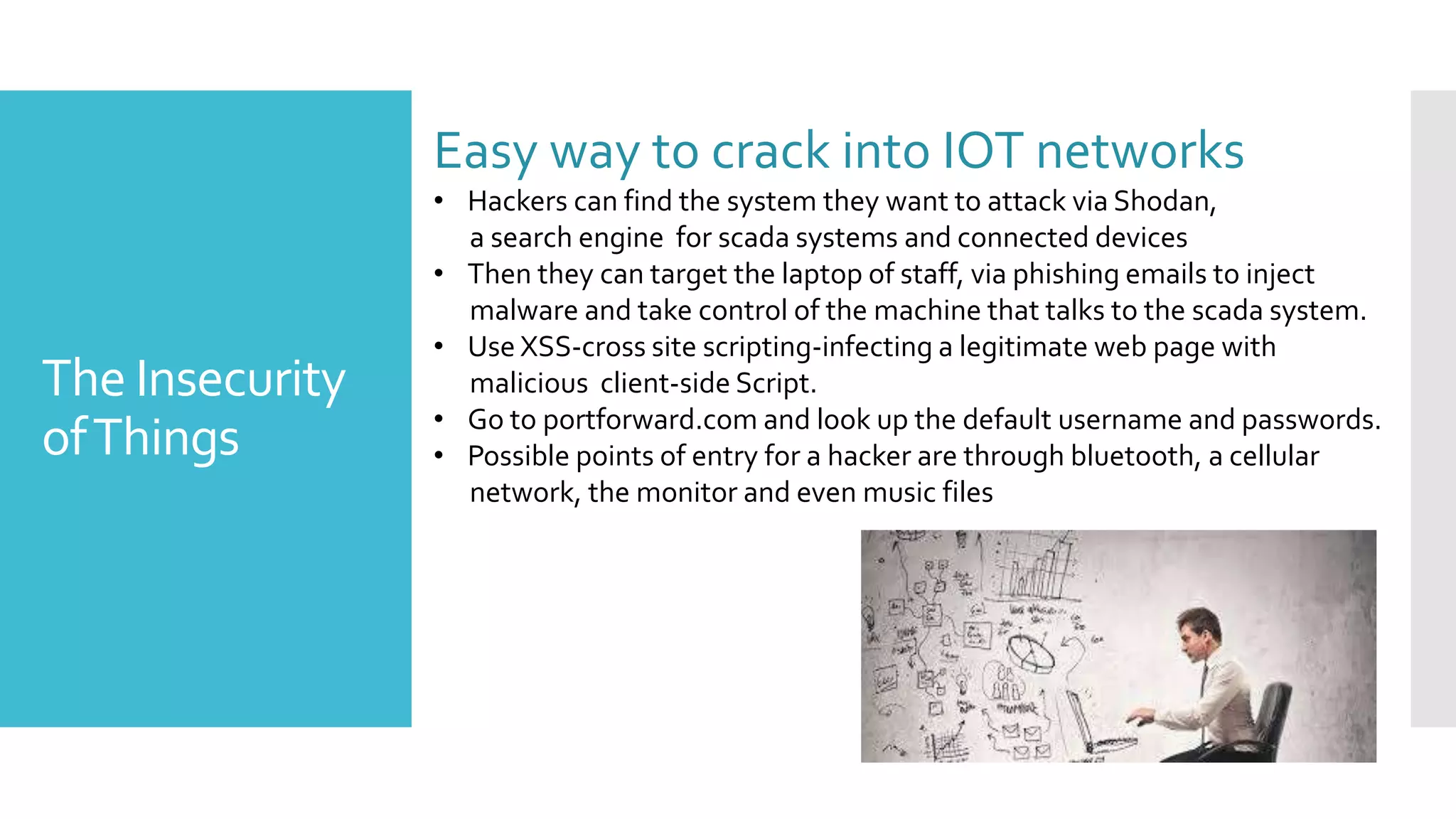
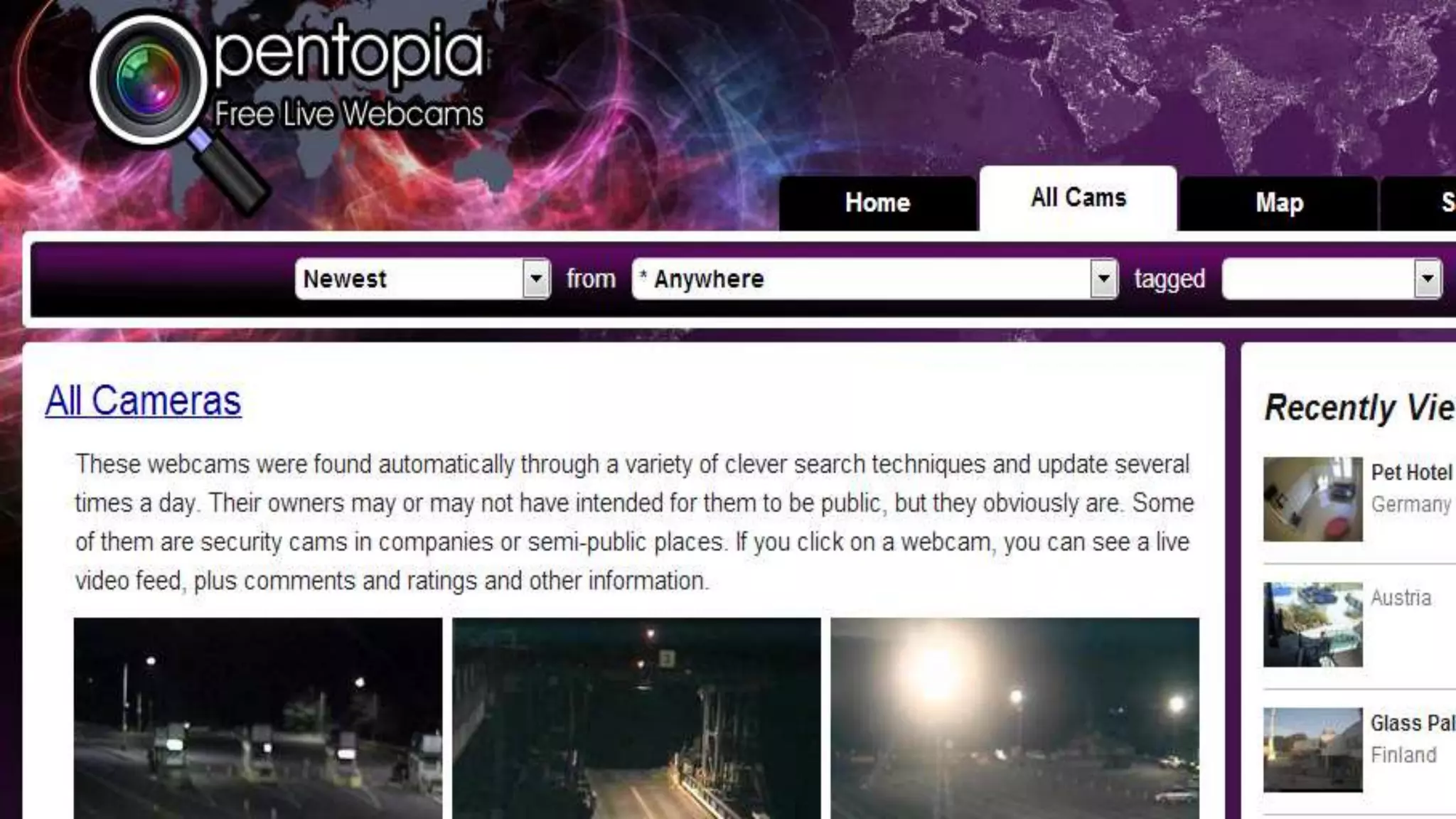
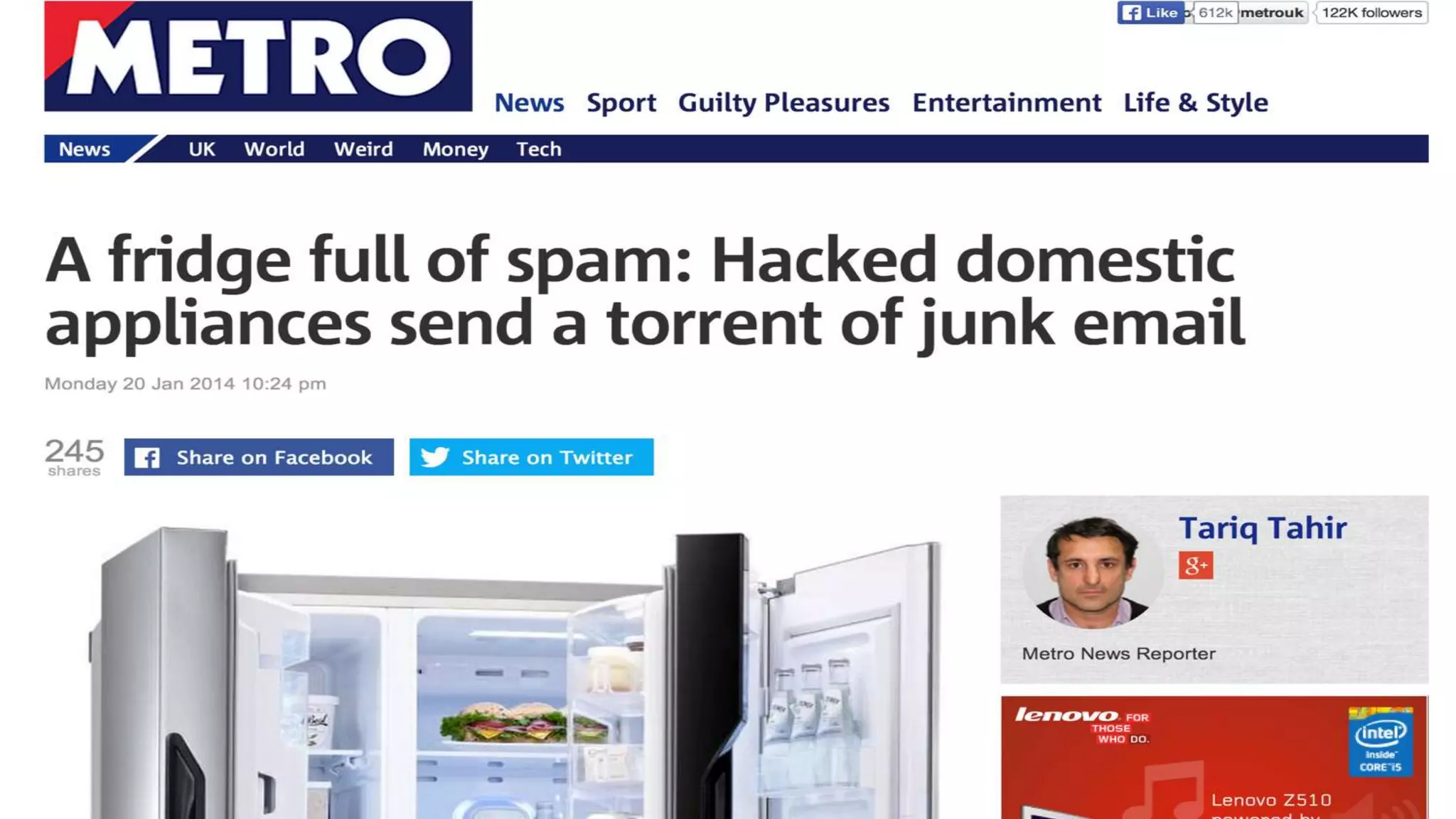
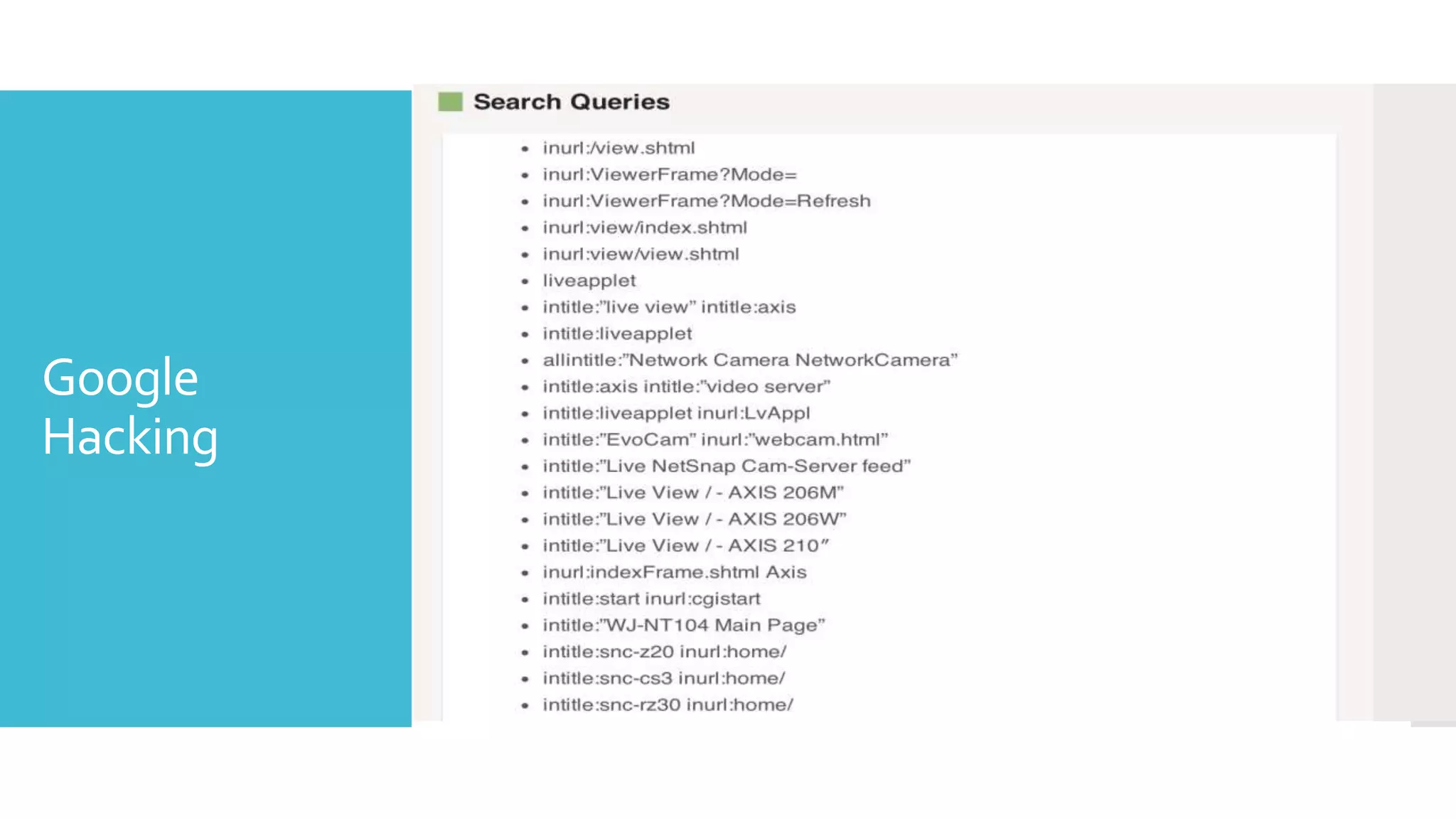
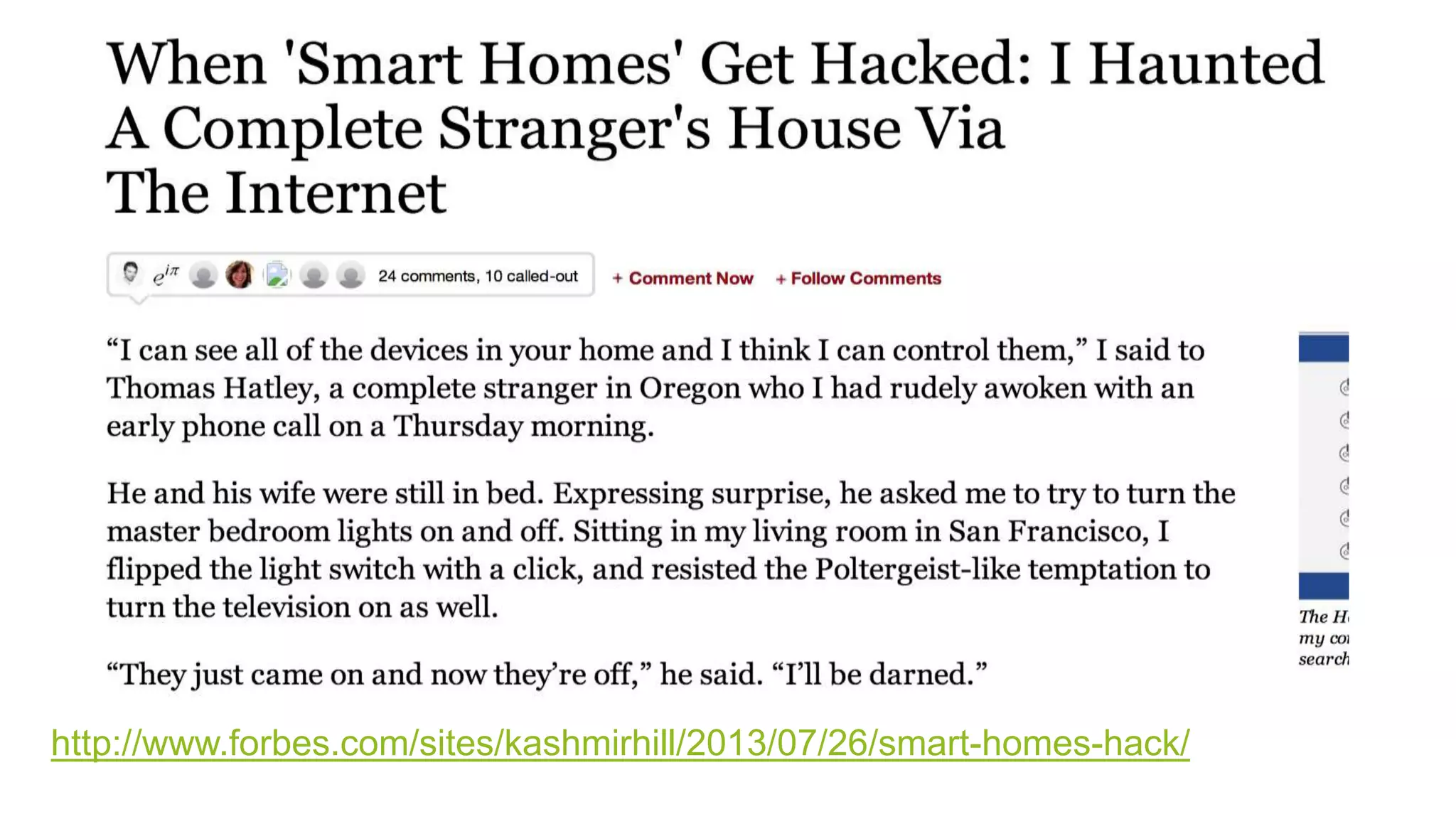
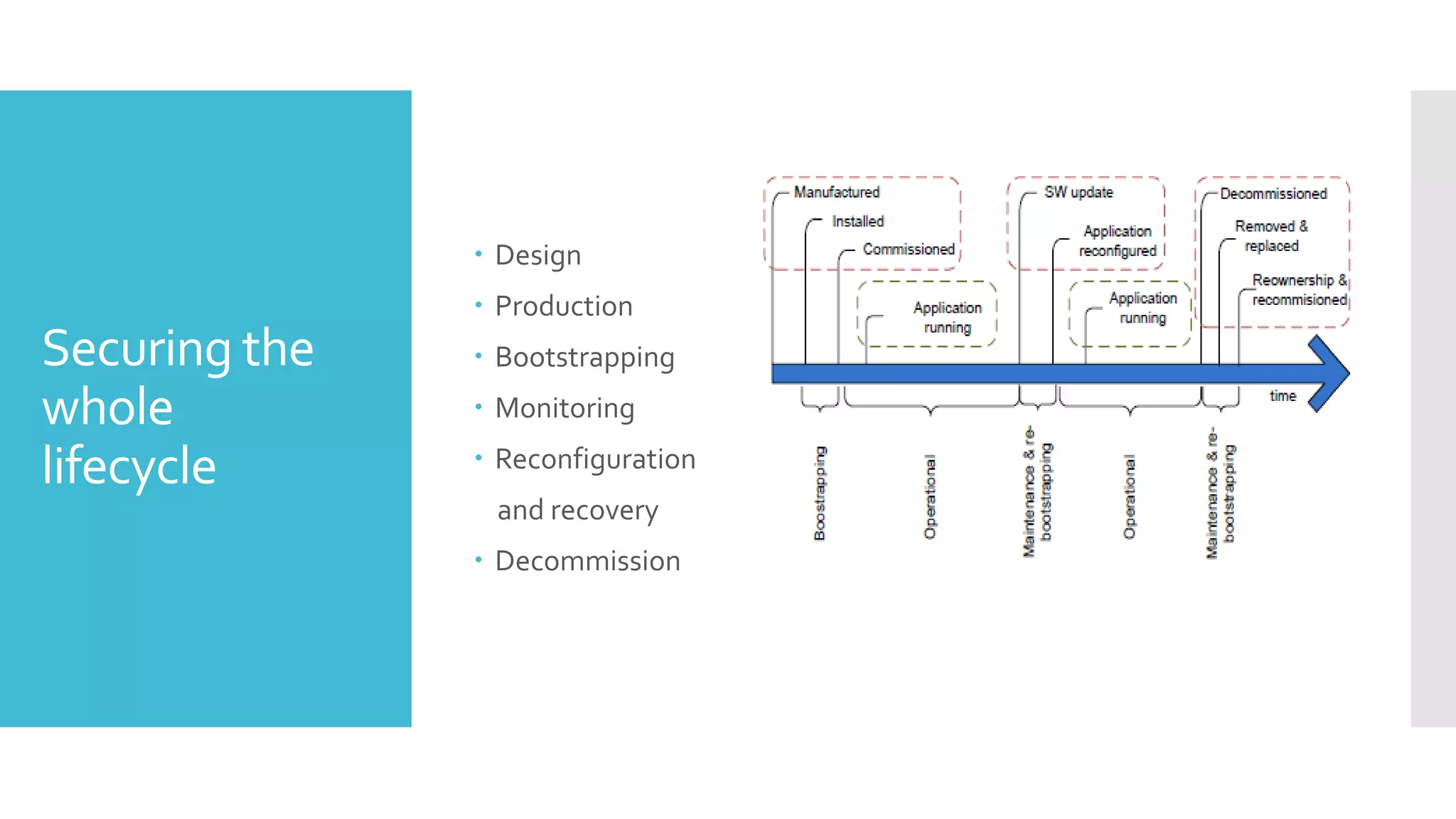
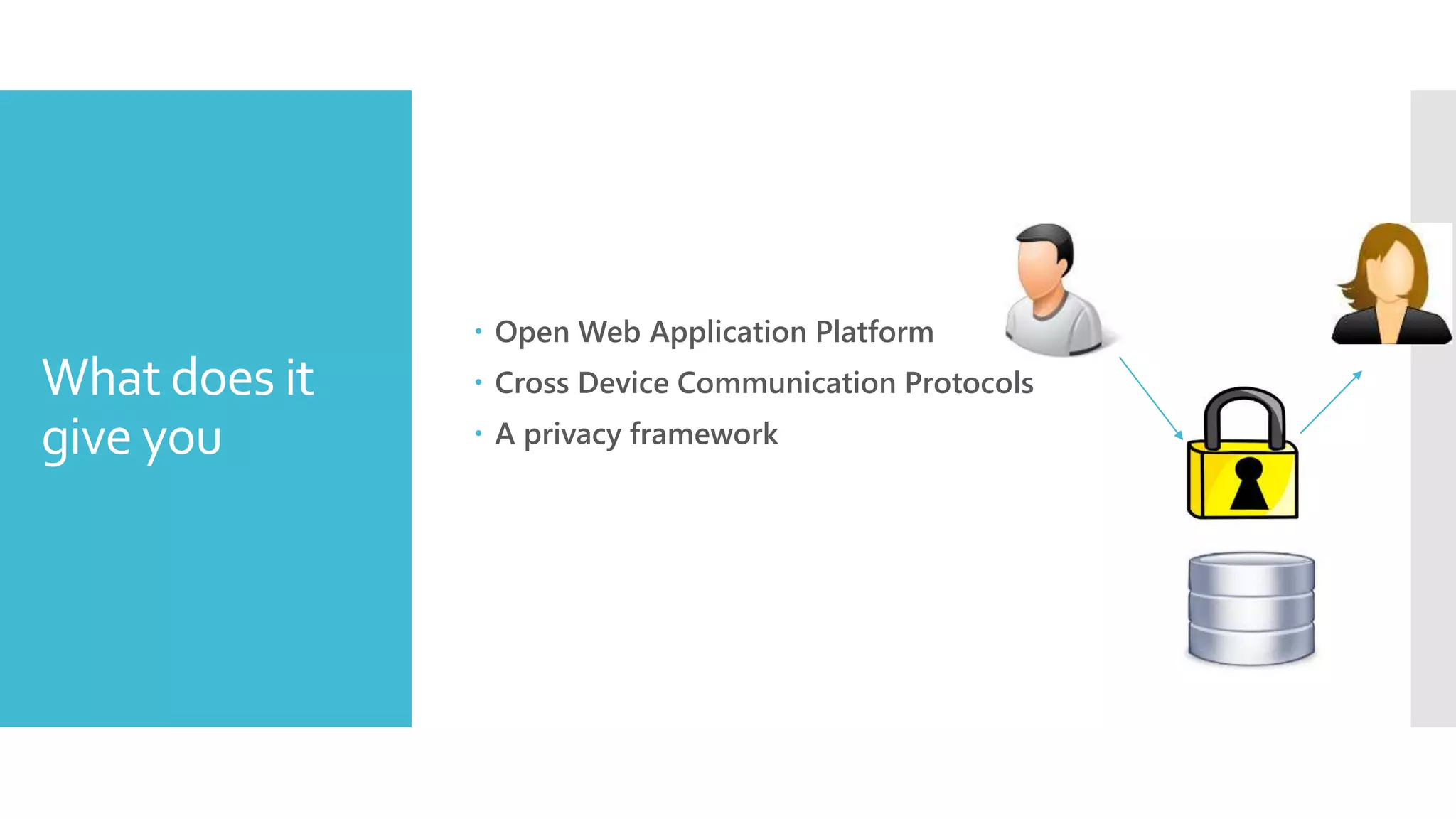
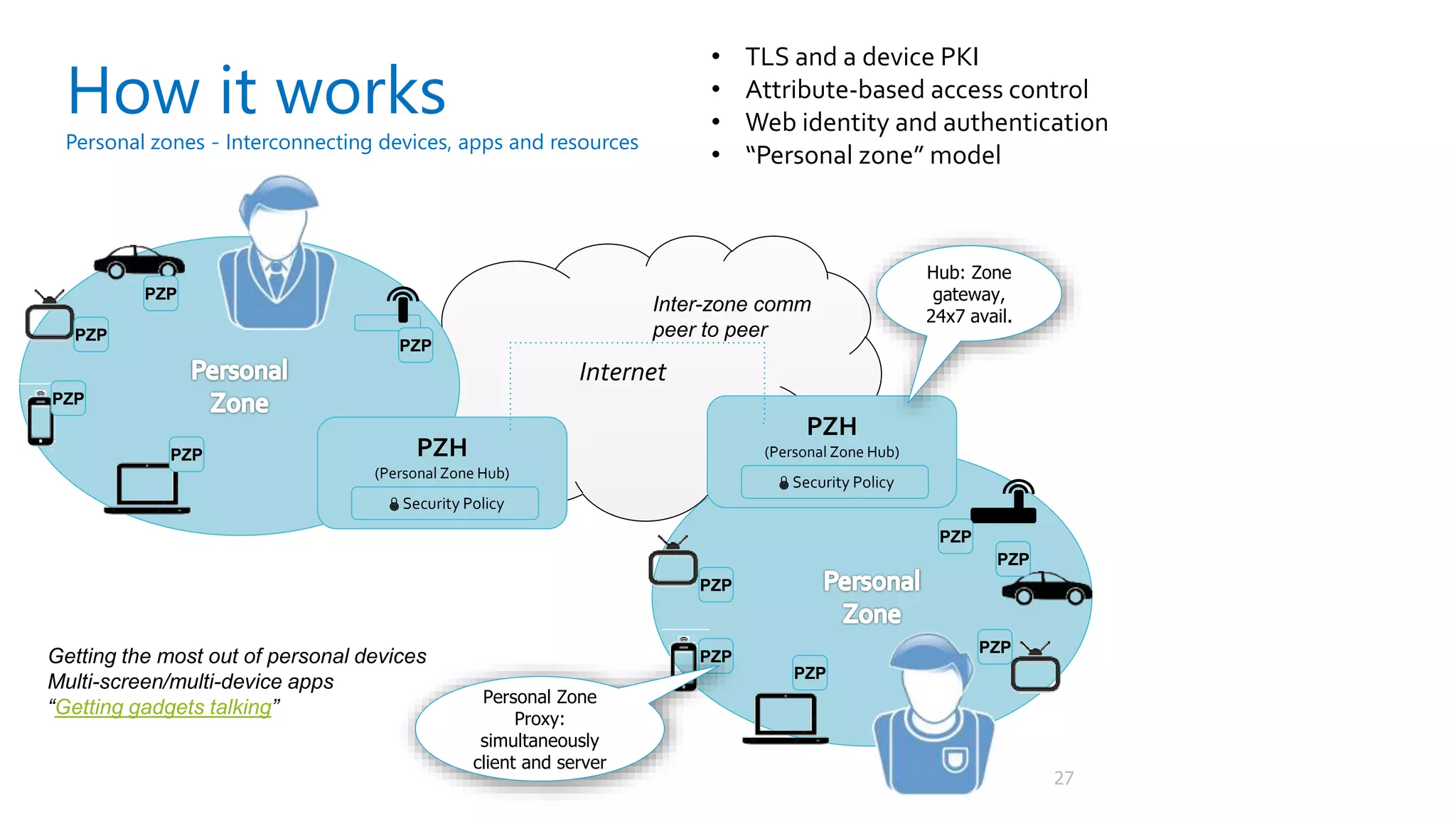
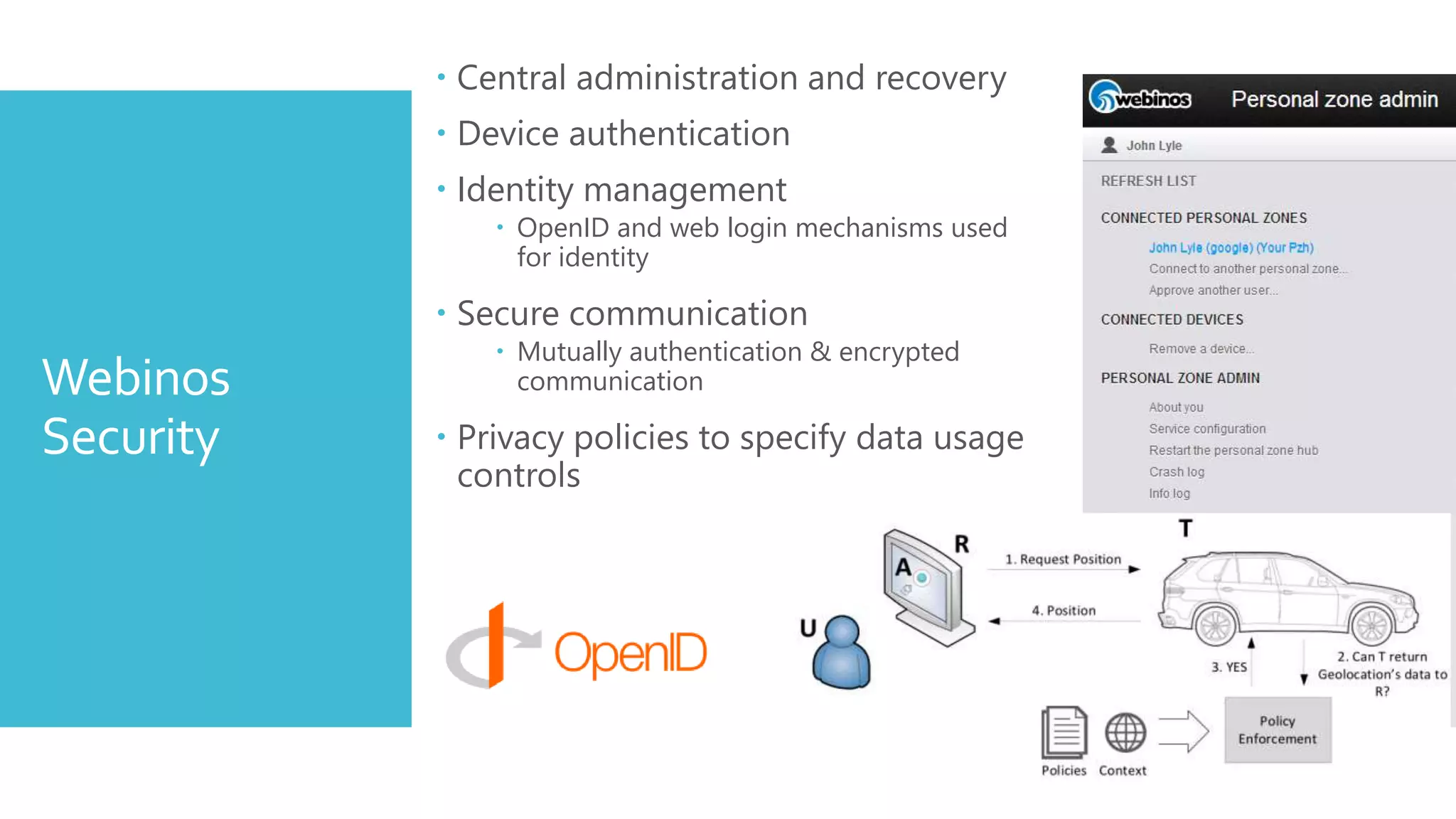
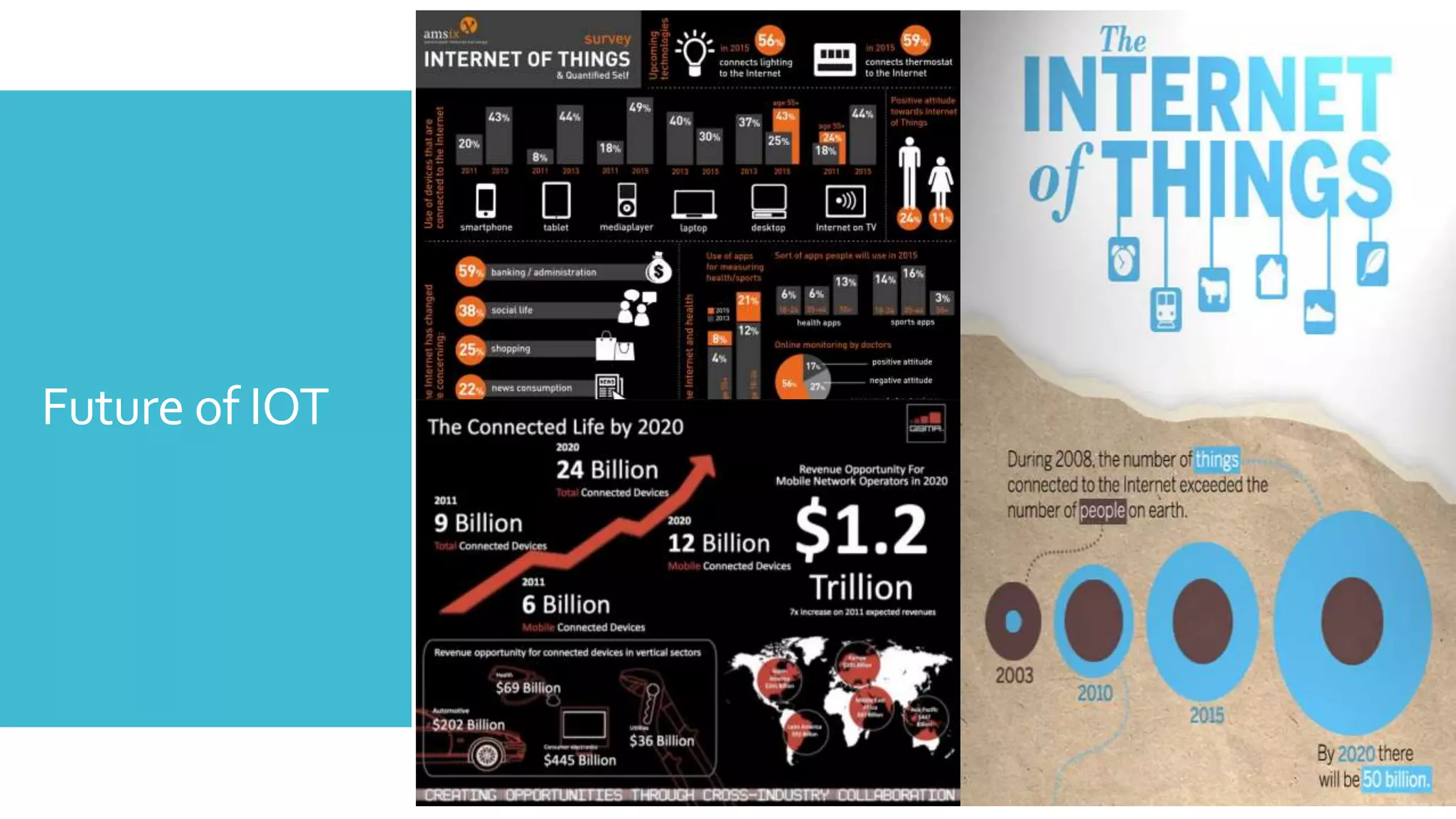
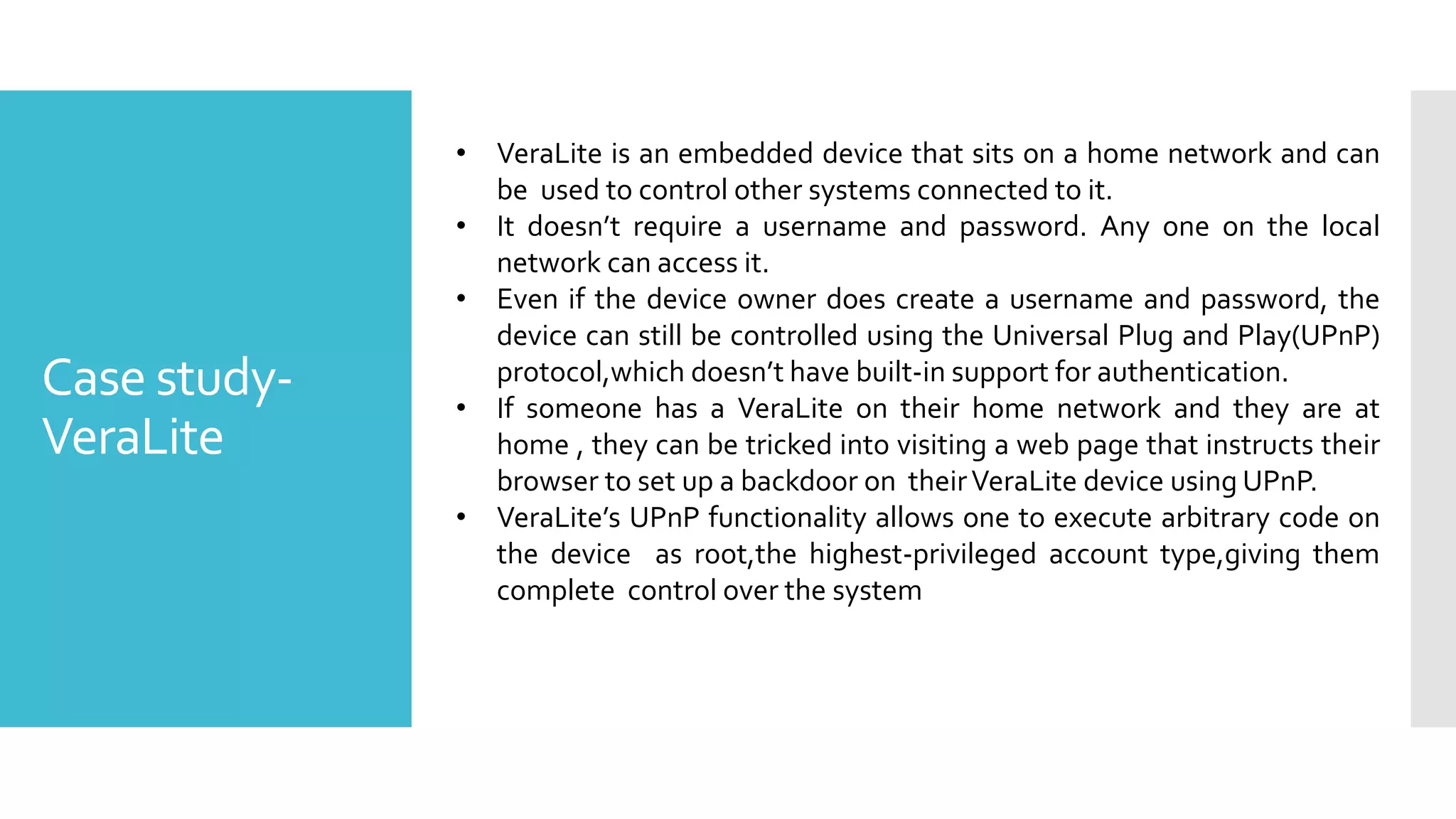
The document discusses security challenges for the Internet of Things (IoT). It begins with an introduction to IoT and then discusses some of the enabling technologies like RFID, sensors, and nanotechnology. It also covers various applications of IoT such as smart cities, smart homes, smart farms, and e-healthcare. The document then outlines why IoT security is difficult due to issues like wireless communication, physical insecurity of devices, lack of standards, and classic internet threats. It also discusses some threats to IoT systems and potential security approaches like designing for security and implementing identity management. In the end, it provides some basic security precautions and thoughts on ongoing development of technologies and protocols for IoT security.