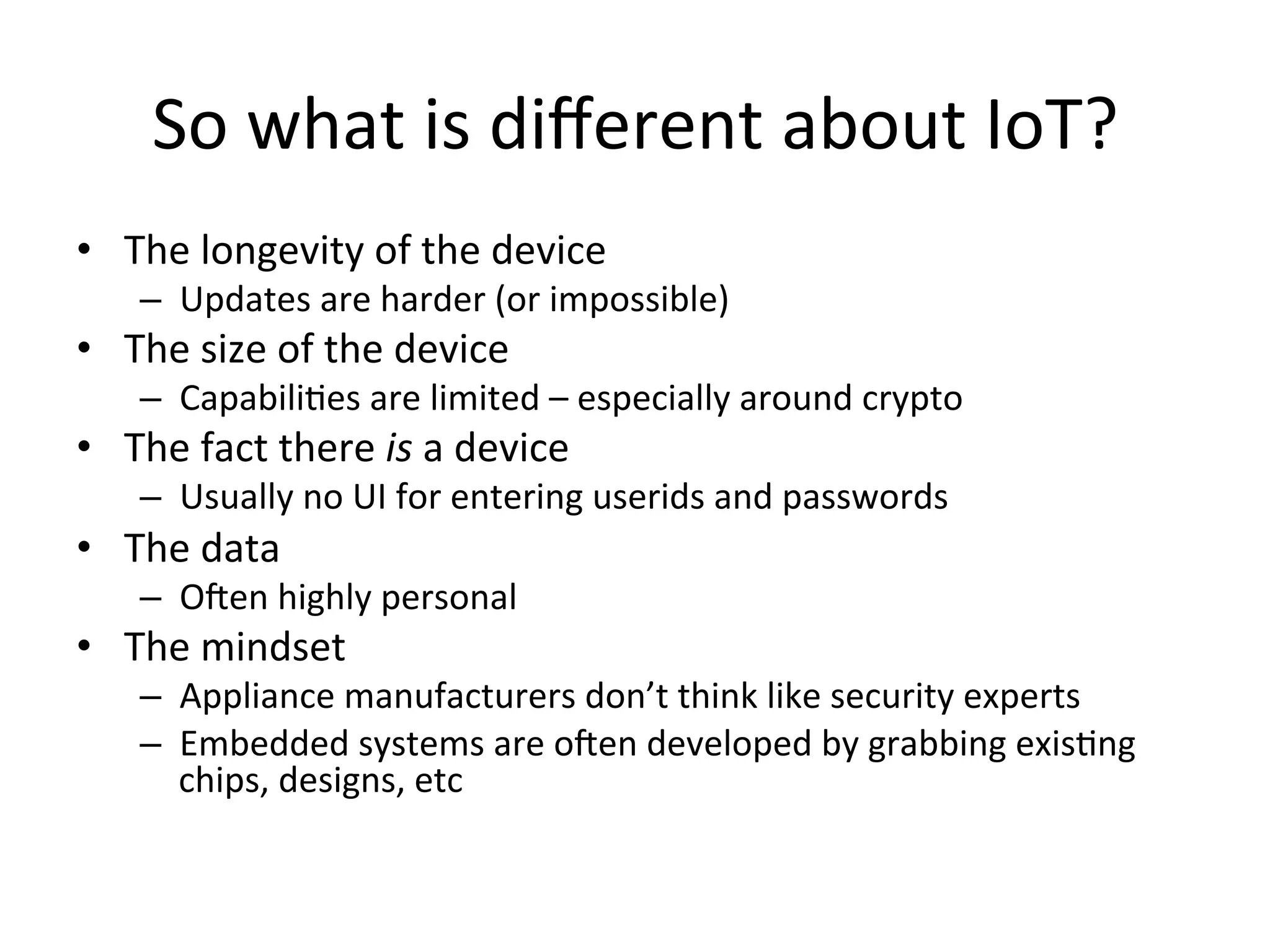
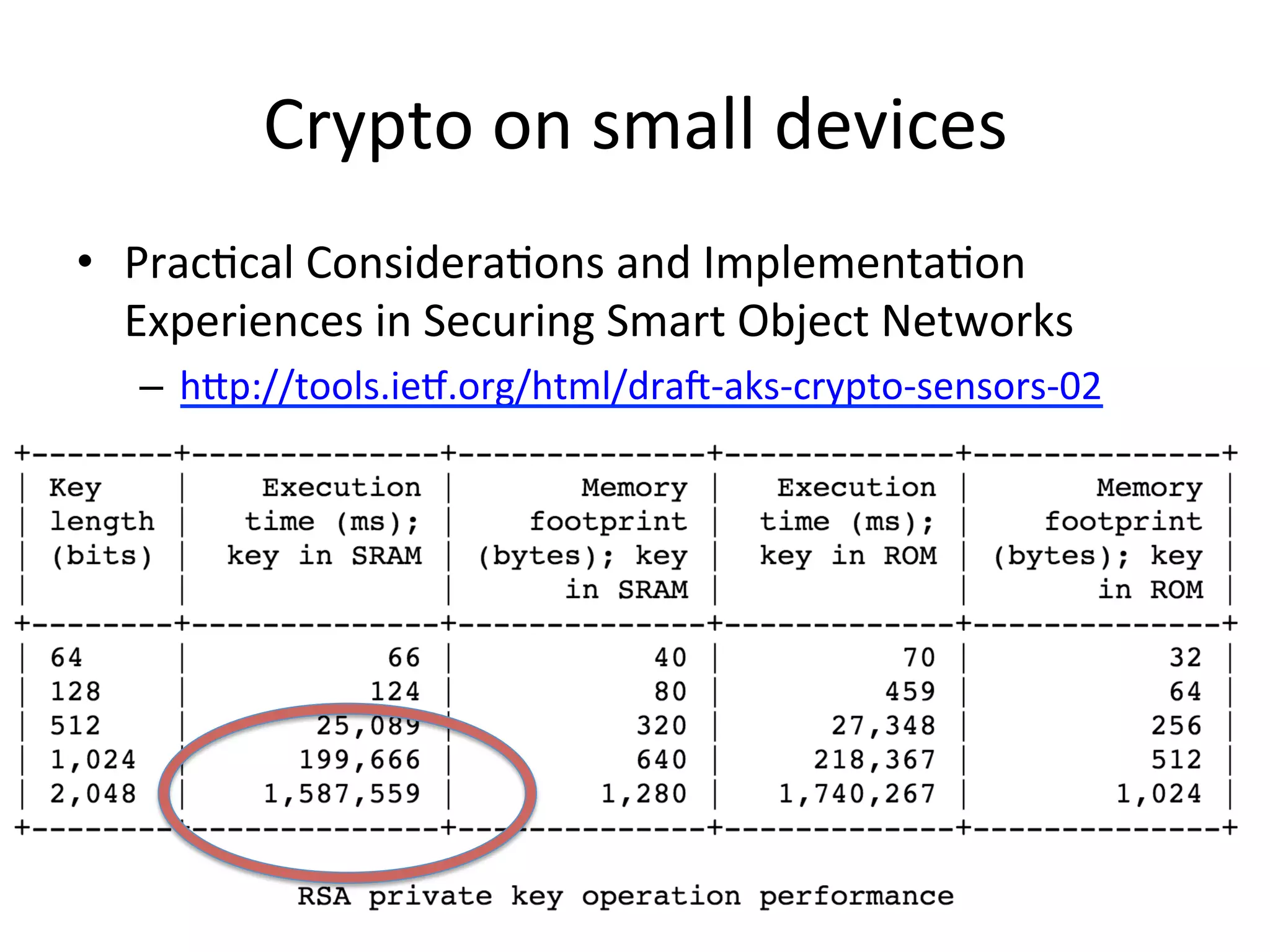
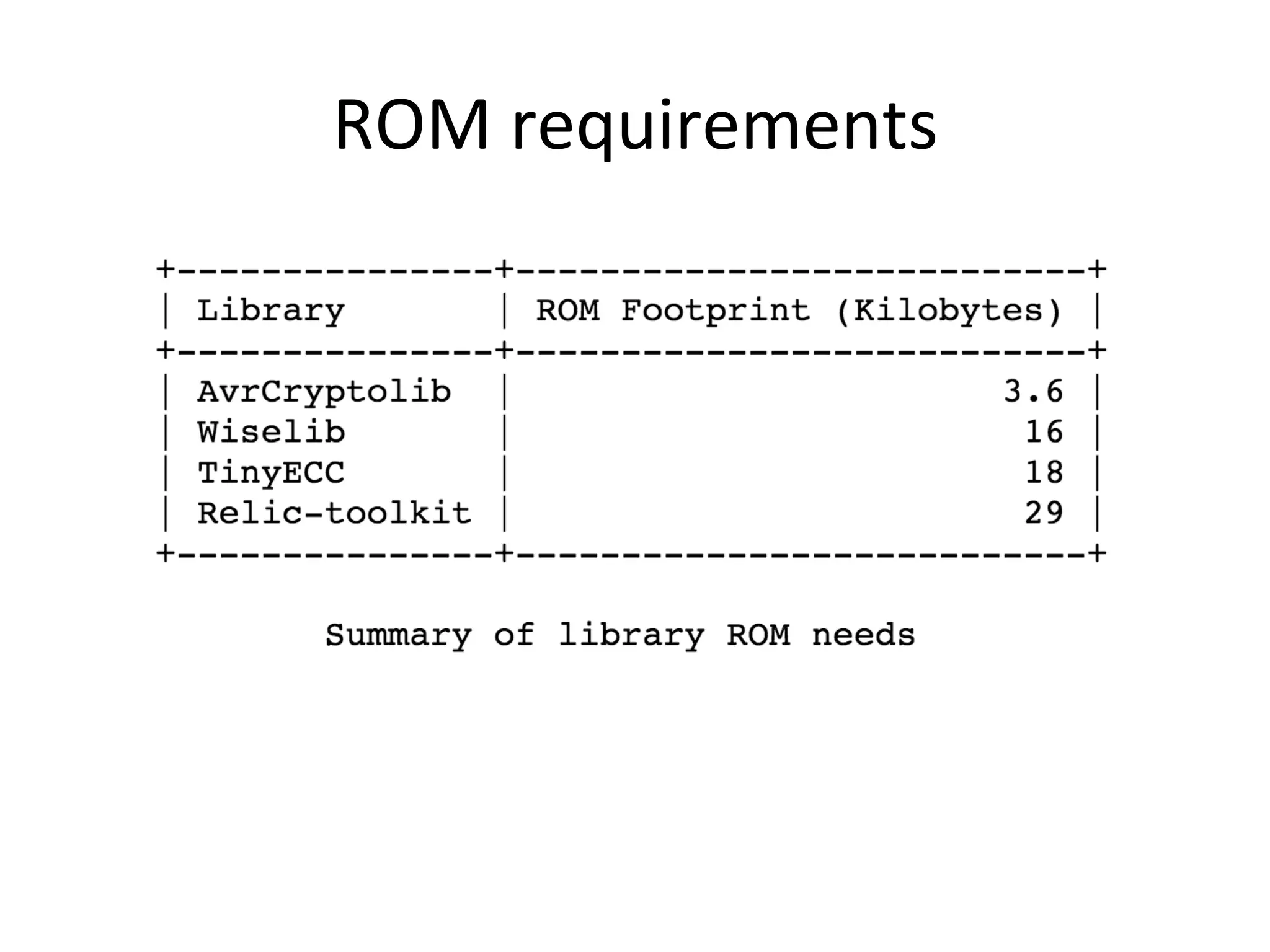
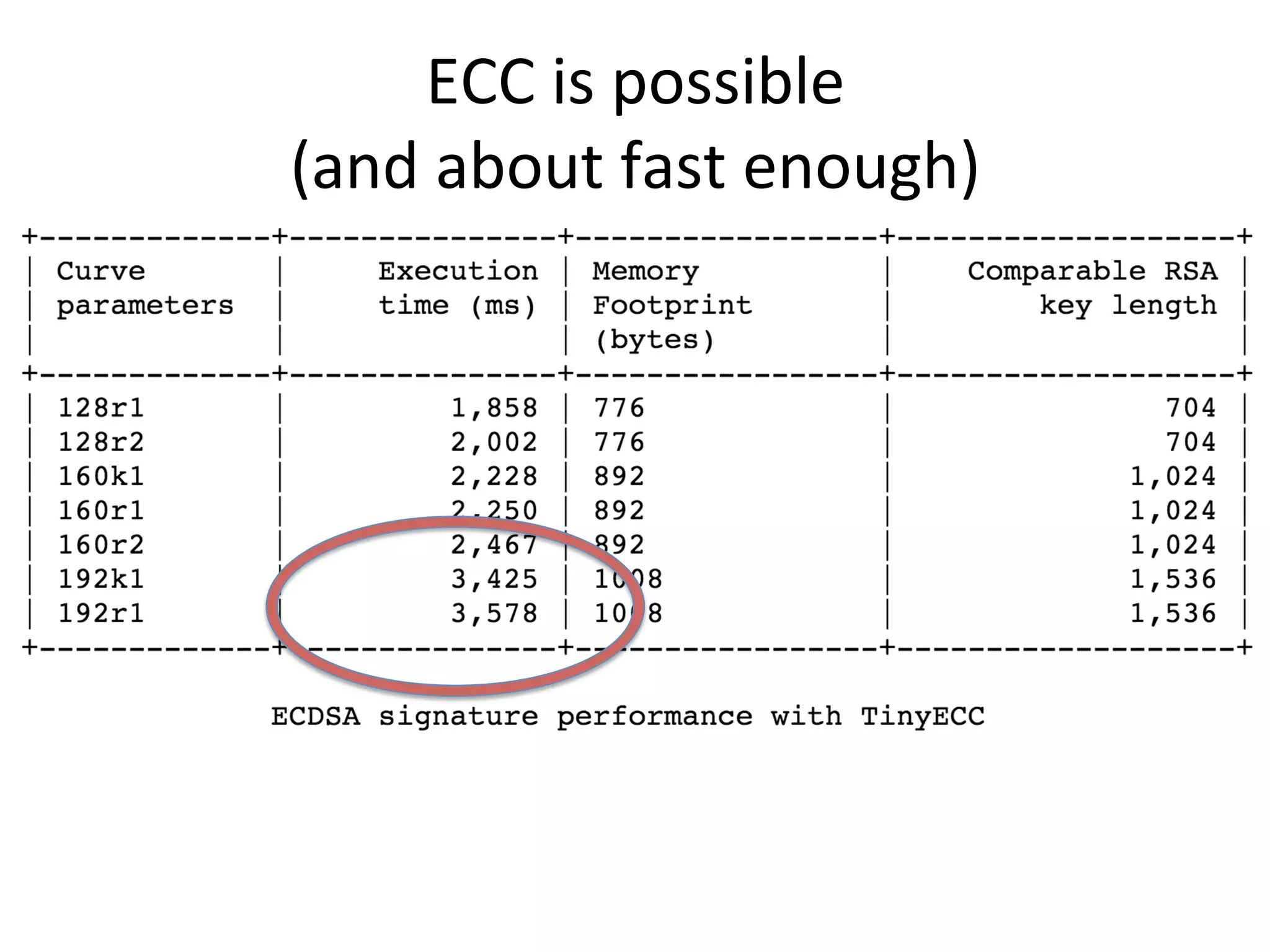
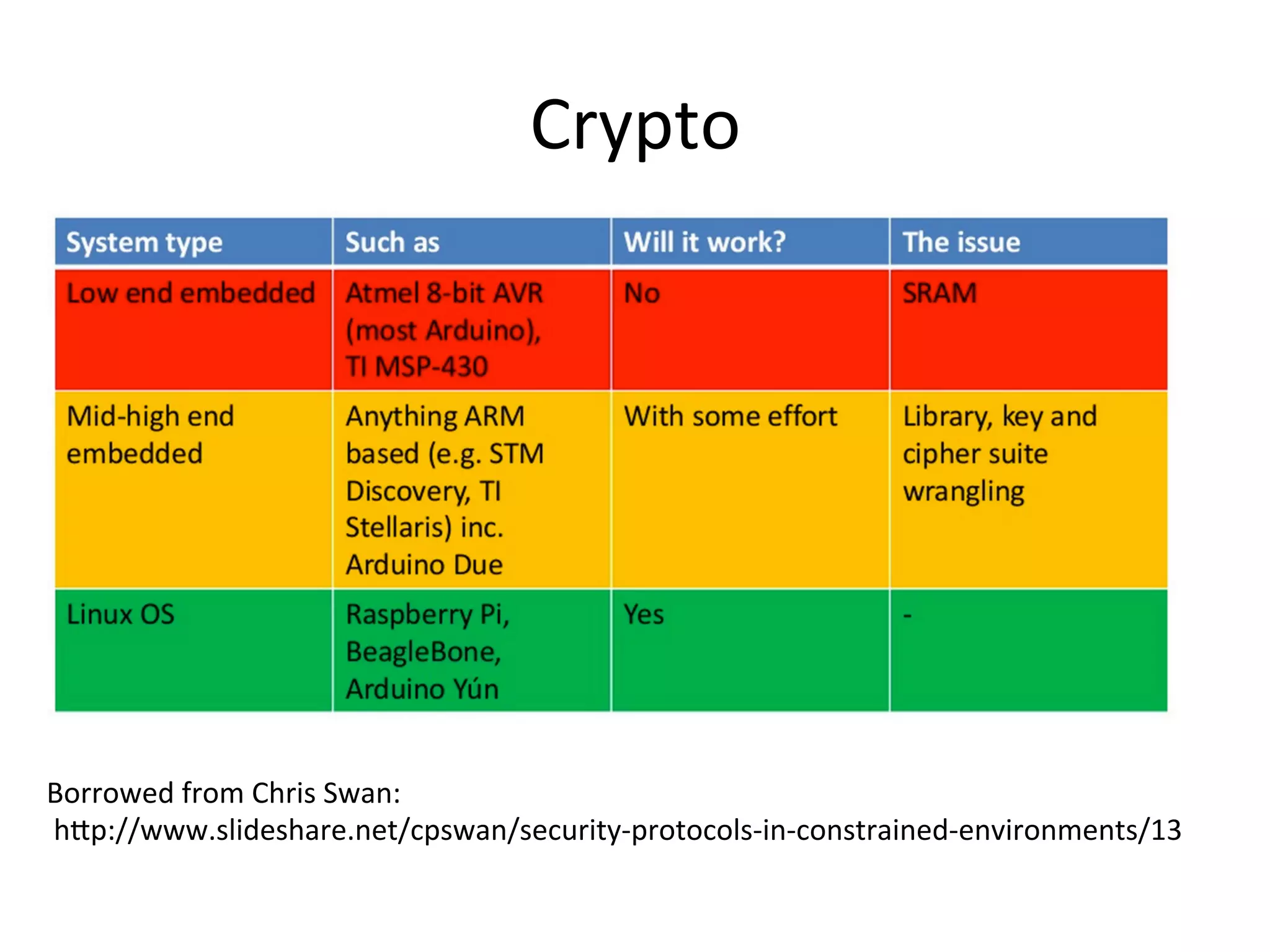
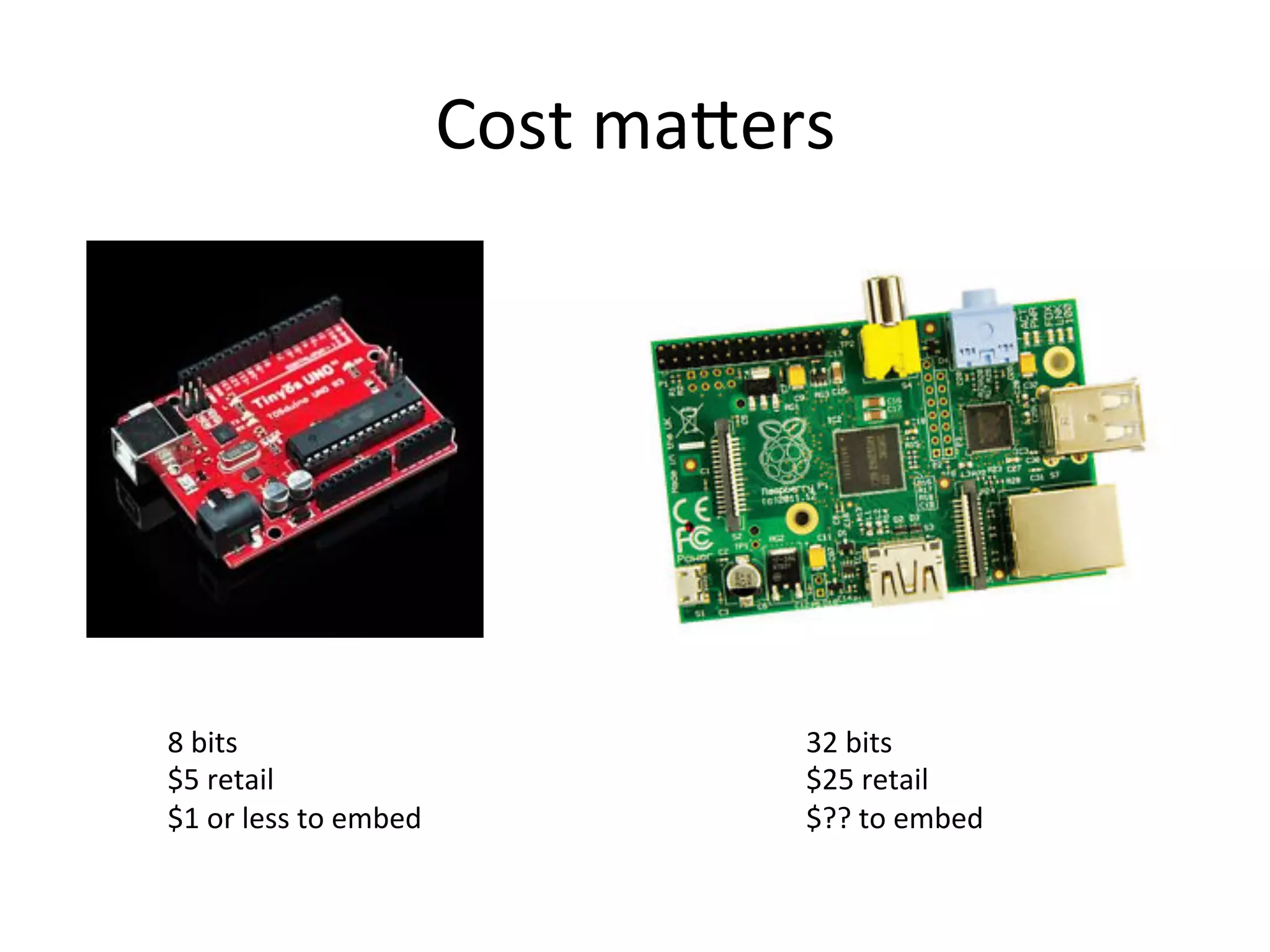
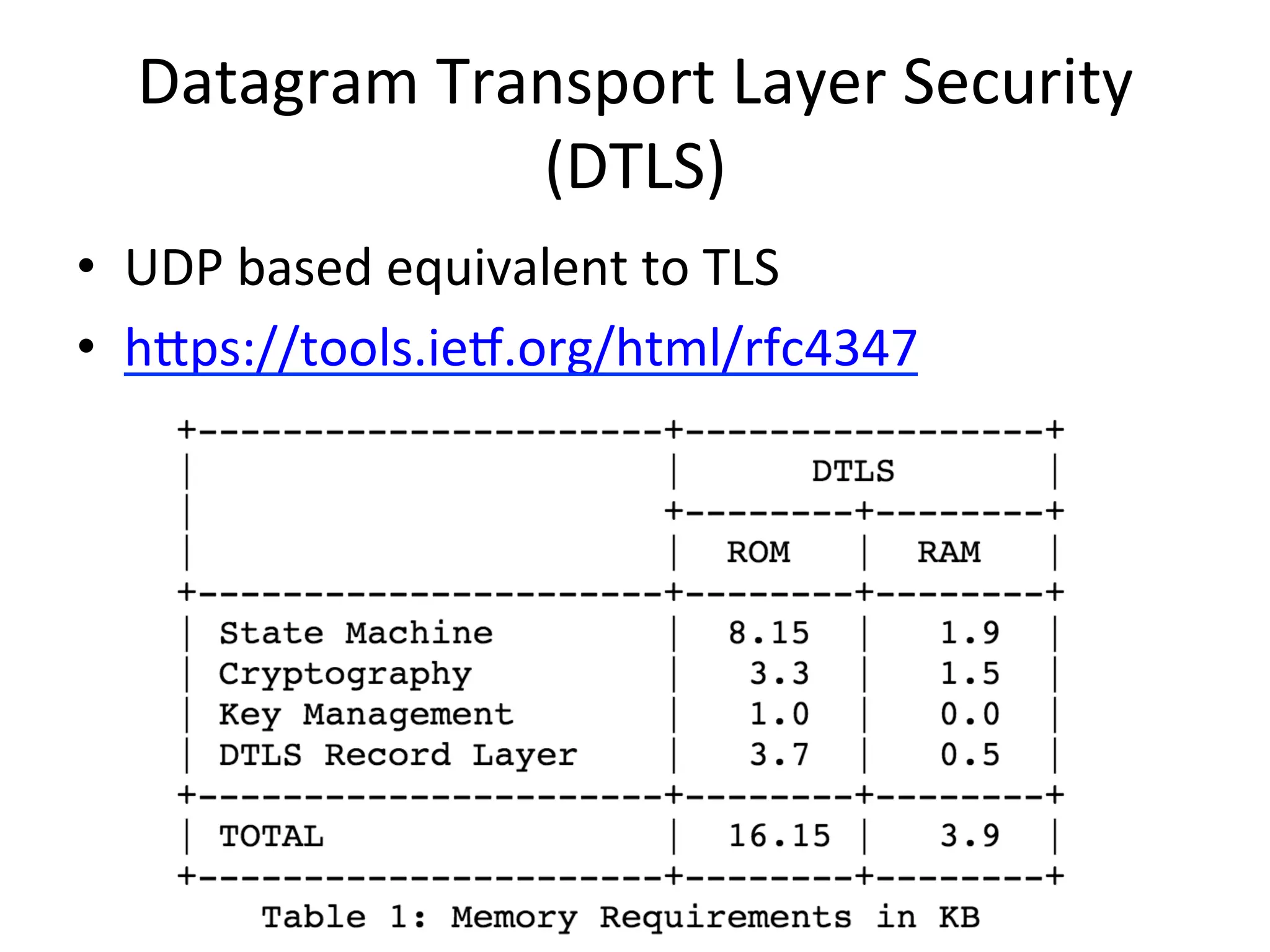
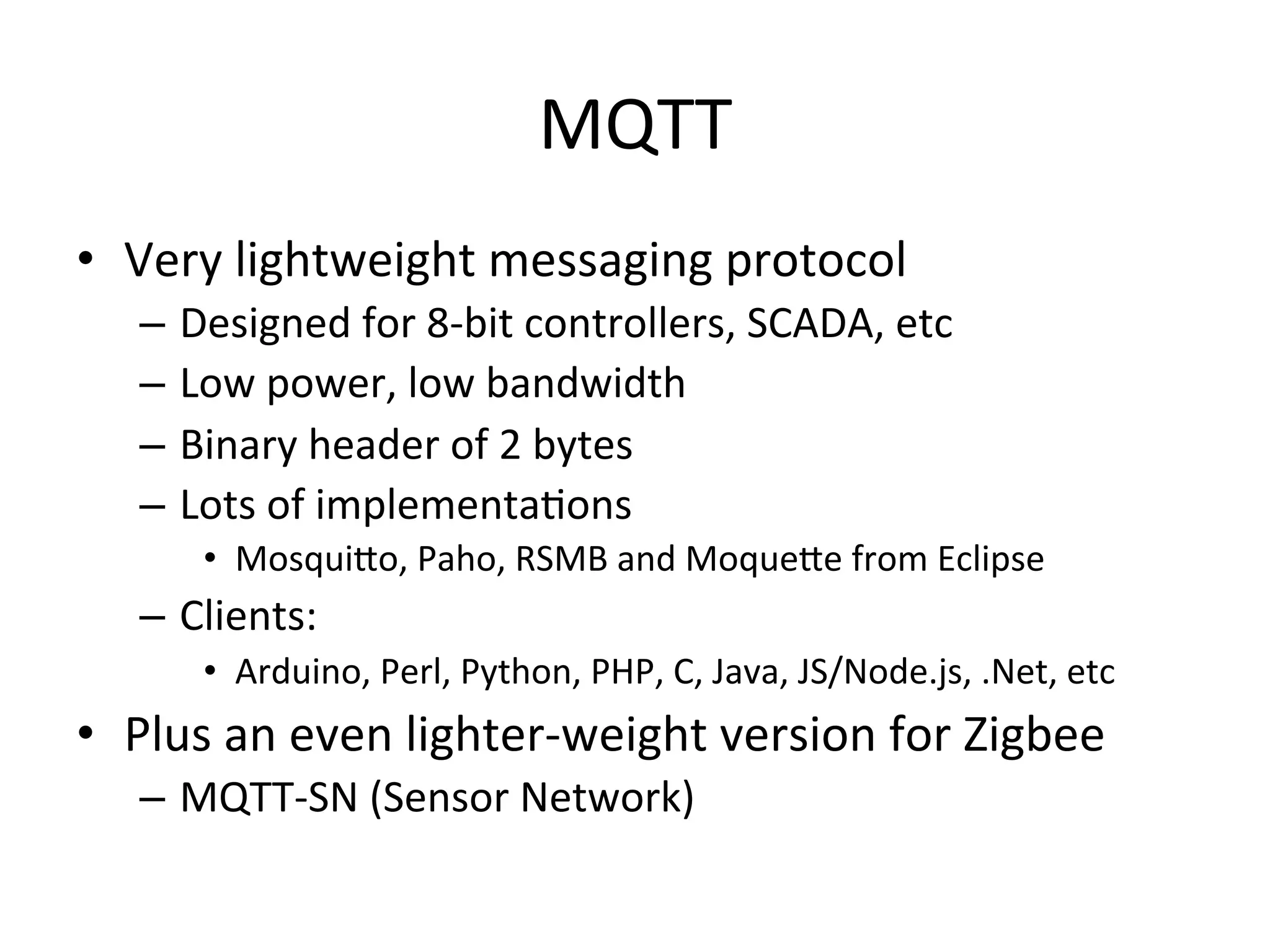
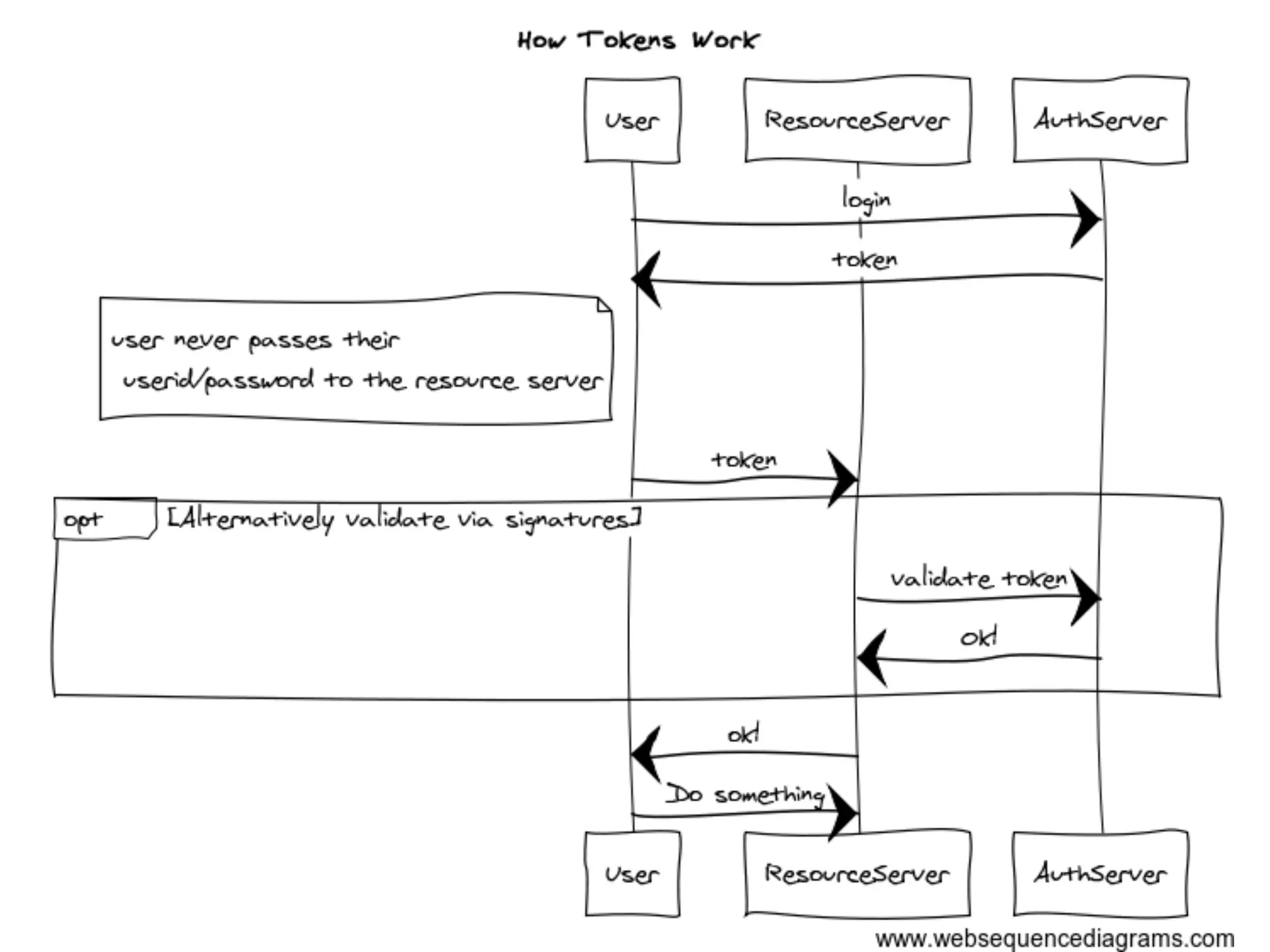
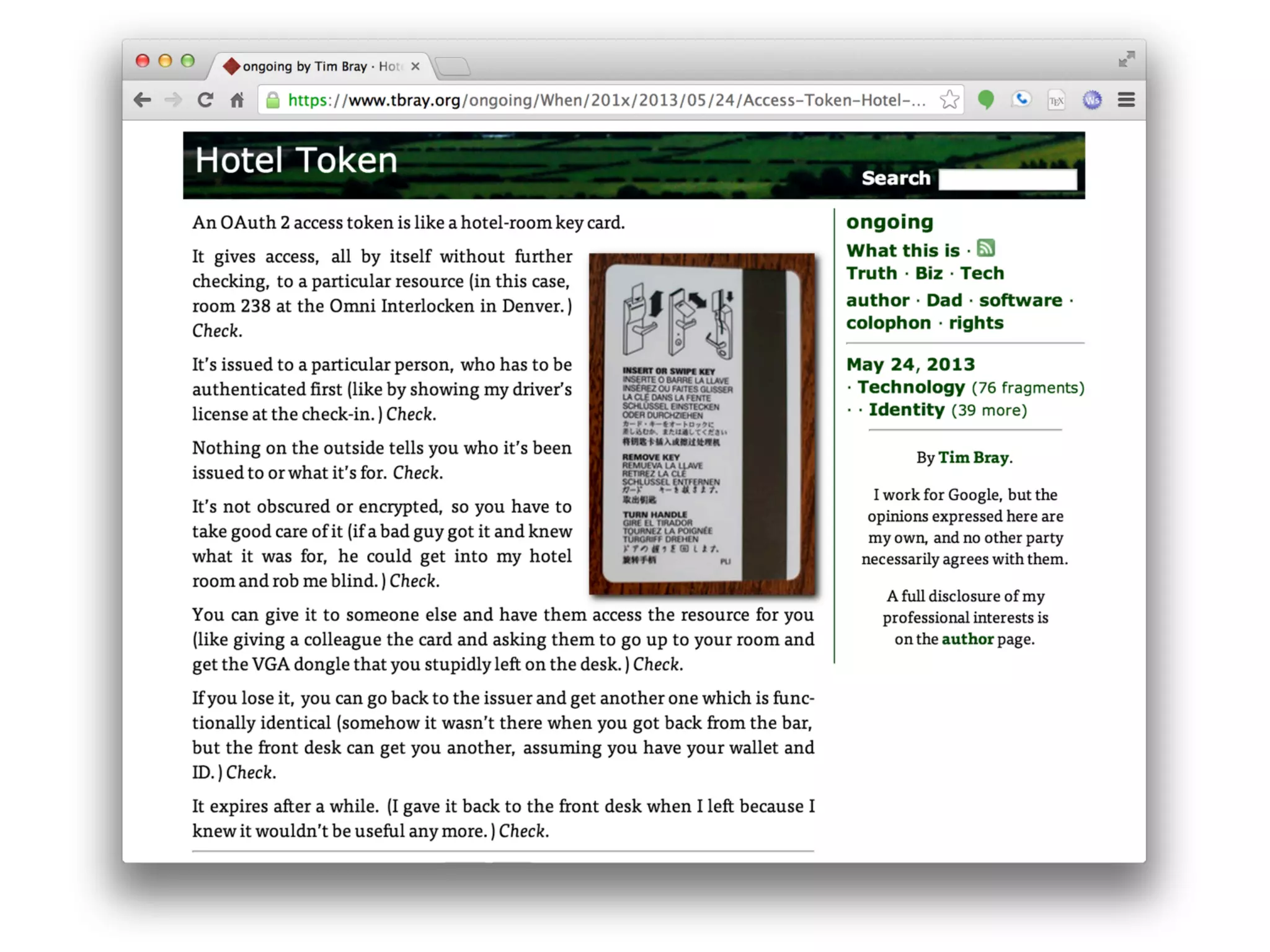
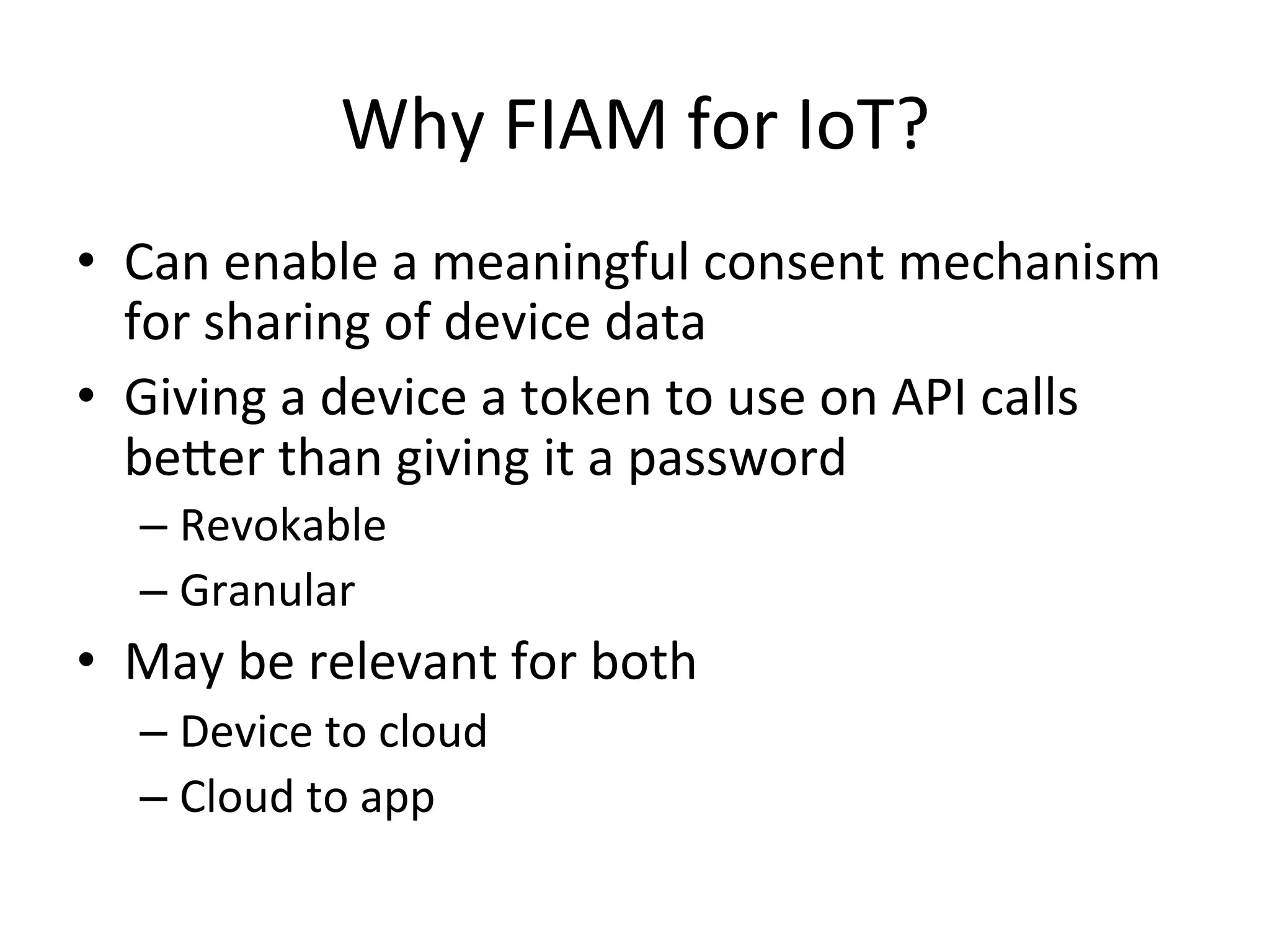
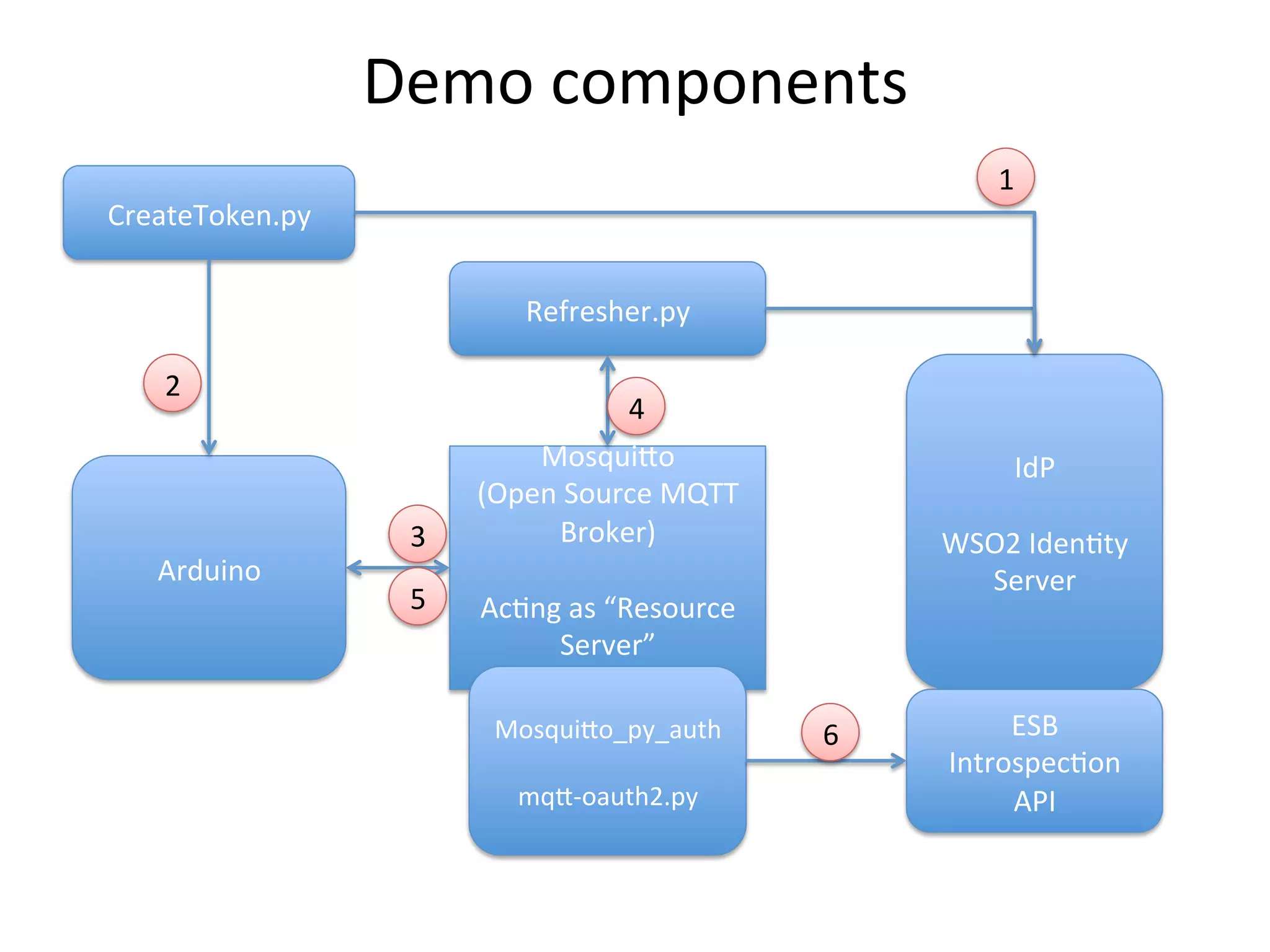
This document discusses securing the Internet of Things (IoT). It notes that IoT devices differ from traditional devices in ways that impact security, such as limited ability to update firmware. It recommends not relying on security through obscurity and discusses practical crypto implementations for small devices. The document also covers securing communication protocols like MQTT, CoAP and DTLS, as well as approaches like OAuth2 for authentication without passwords on devices. It describes a demonstration of using OAuth2 with MQTT to limit a device's access to an API by giving it a revocable token rather than a static password.