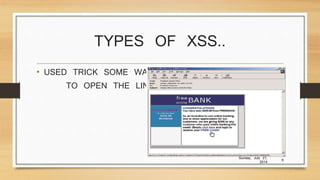
Cross-site scripting (XSS) is a type of attack where malicious scripts are injected into vulnerable websites. There are two main types: persistent XSS, where the script is permanently stored on the website, and non-persistent XSS, which uses a specially crafted link. XSS can be prevented through input validation, disabling scripting languages, user education, and browser security updates. The worst-case scenario is that an XSS vulnerability could allow a site to be used as a platform for further attacks against users and connected websites. While XSS malware is still emerging, its techniques continue to evolve posing growing risks.