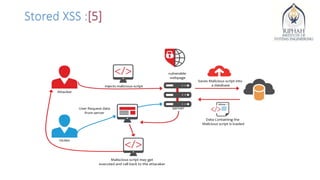
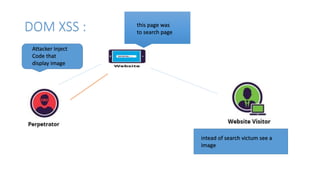
Cross-site scripting (XSS) is a type of web application vulnerability where malicious scripts are injected into otherwise benign web pages. There are three main types of XSS attacks: stored XSS, reflected XSS, and DOM-based XSS. XSS vulnerabilities have affected many major websites and can enable account hijacking, cookie theft, and other malicious activities. Developers can prevent XSS by encoding untrusted inputs, validating inputs, and using security libraries that filter malicious scripts.

![Who’s affected by cross-site scripting?
• Everyone. No, really – almost every site you can think of has had XSS
problems at one time or another (and probably still does) :
• Universal XSS in Internet Explorer (2015) [1]
• Tweetdeck (2014) [2]
• PayPal (2013) – BONUS: discovered by a 17 year old kid [3]
• Google Finance (2013) [4]
• 25 “Verasign-secured” online stores (2012) [5]
• McAfee (2011) [6]
• Visa (2010) [7]](https://image.slidesharecdn.com/crosssitescripting-170419071007/85/Cross-site-scripting-4-320.jpg)
![Reflected XSS:
• <?php
(!array_key_exists ("name", $_GET) || $_GET['name'] == NULL ||
$_GET['name'] == ''){
• $isempty = true;
• } {
•
• echo '<pre>';
• echo 'Hello ' . $_GET['name'];
• echo '</pre>'; }
• http://192.168.182.136/dvwa/vulnerabilities/xss_r/?name=bilal%3Cscript%3
Ealert%28%22hello%22%29%3C%2Fscript%3E#](https://image.slidesharecdn.com/crosssitescripting-170419071007/85/Cross-site-scripting-7-320.jpg)