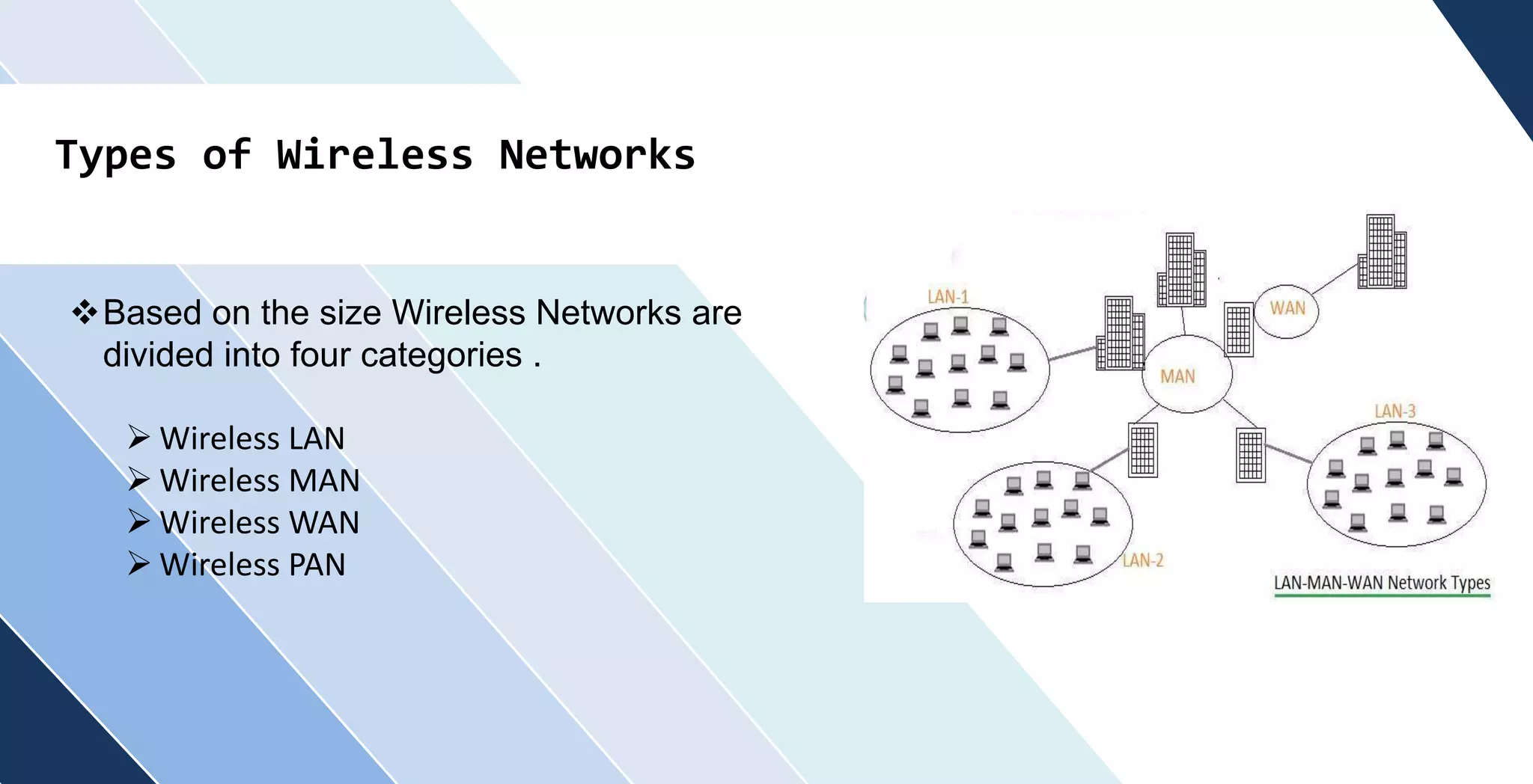
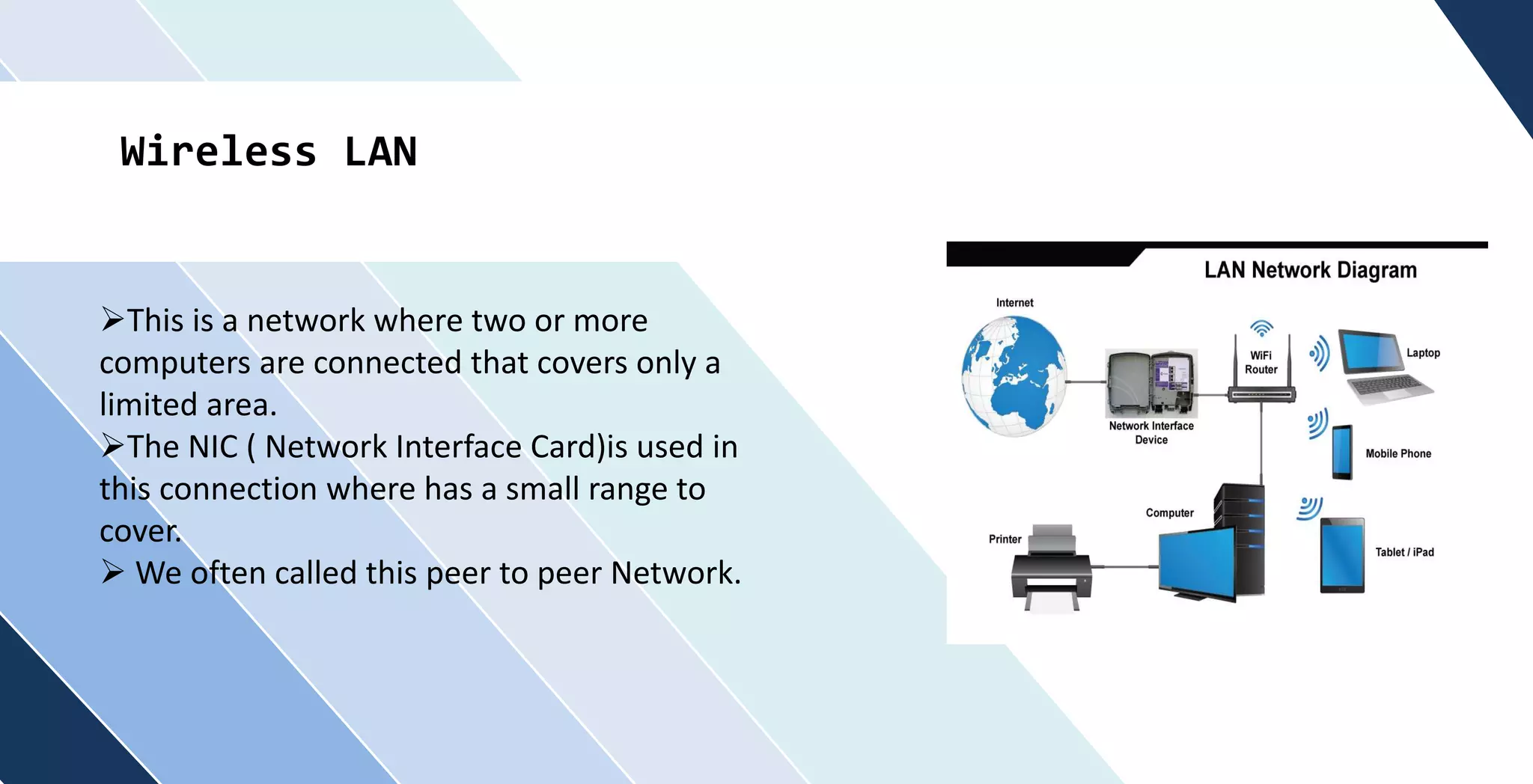
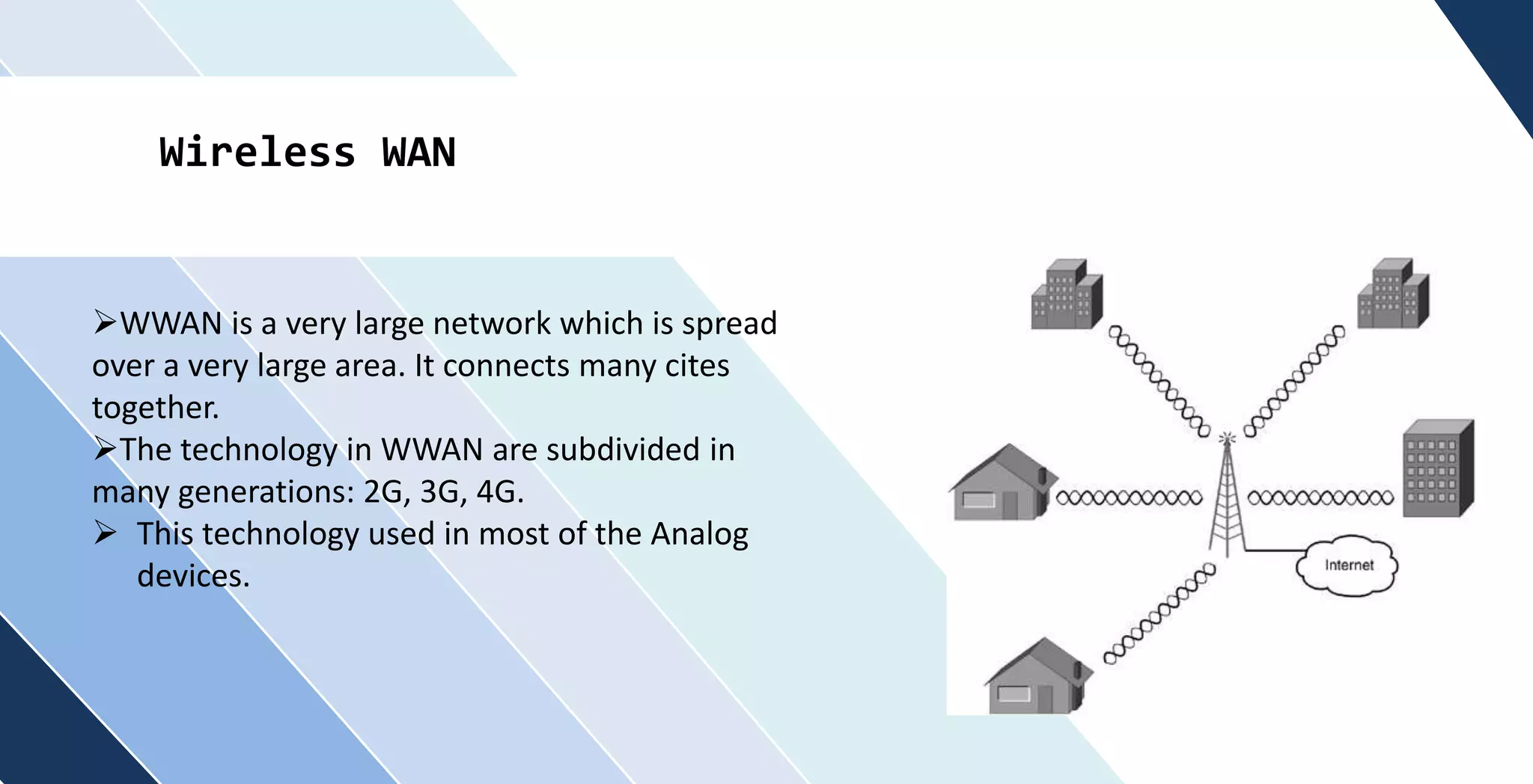
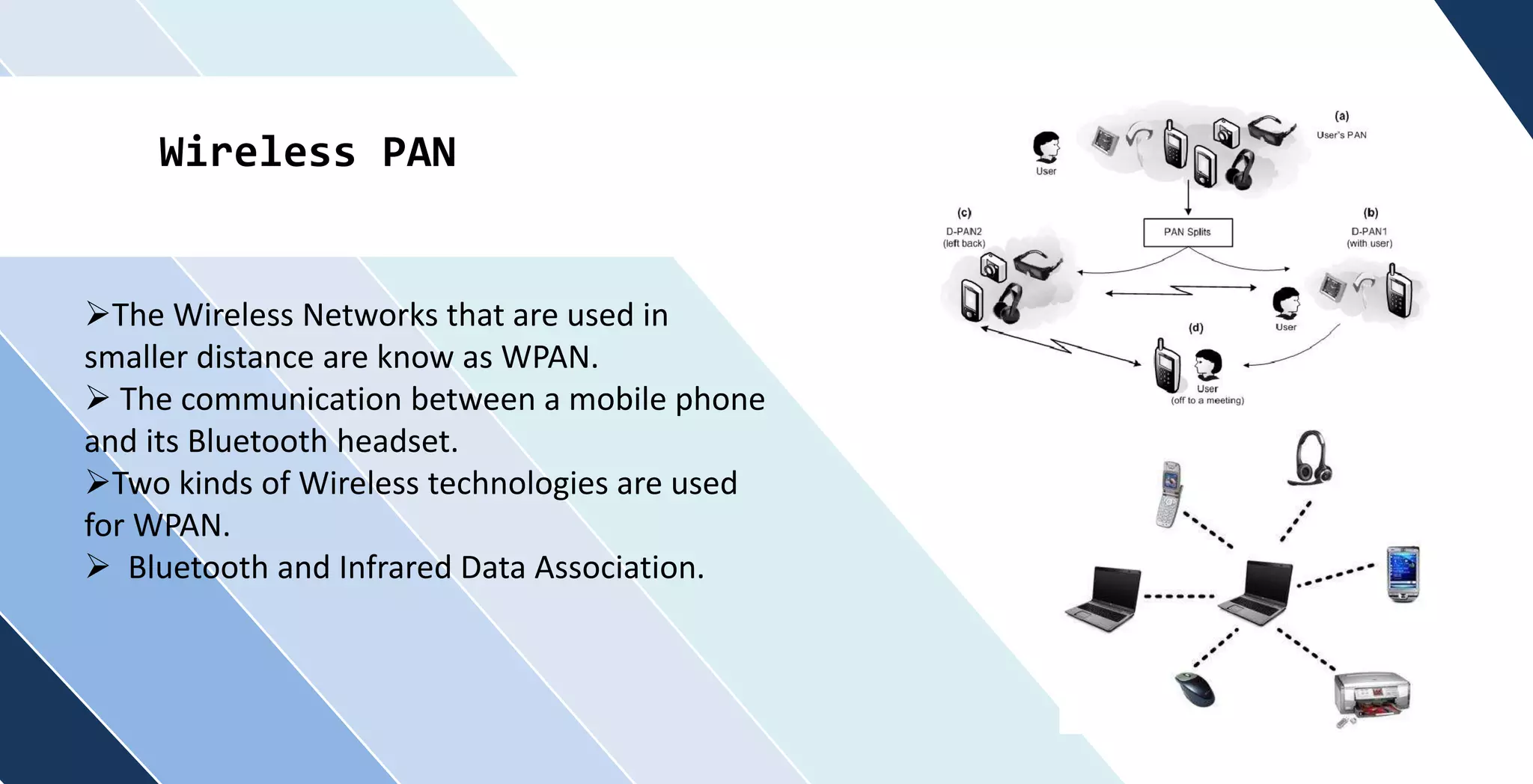
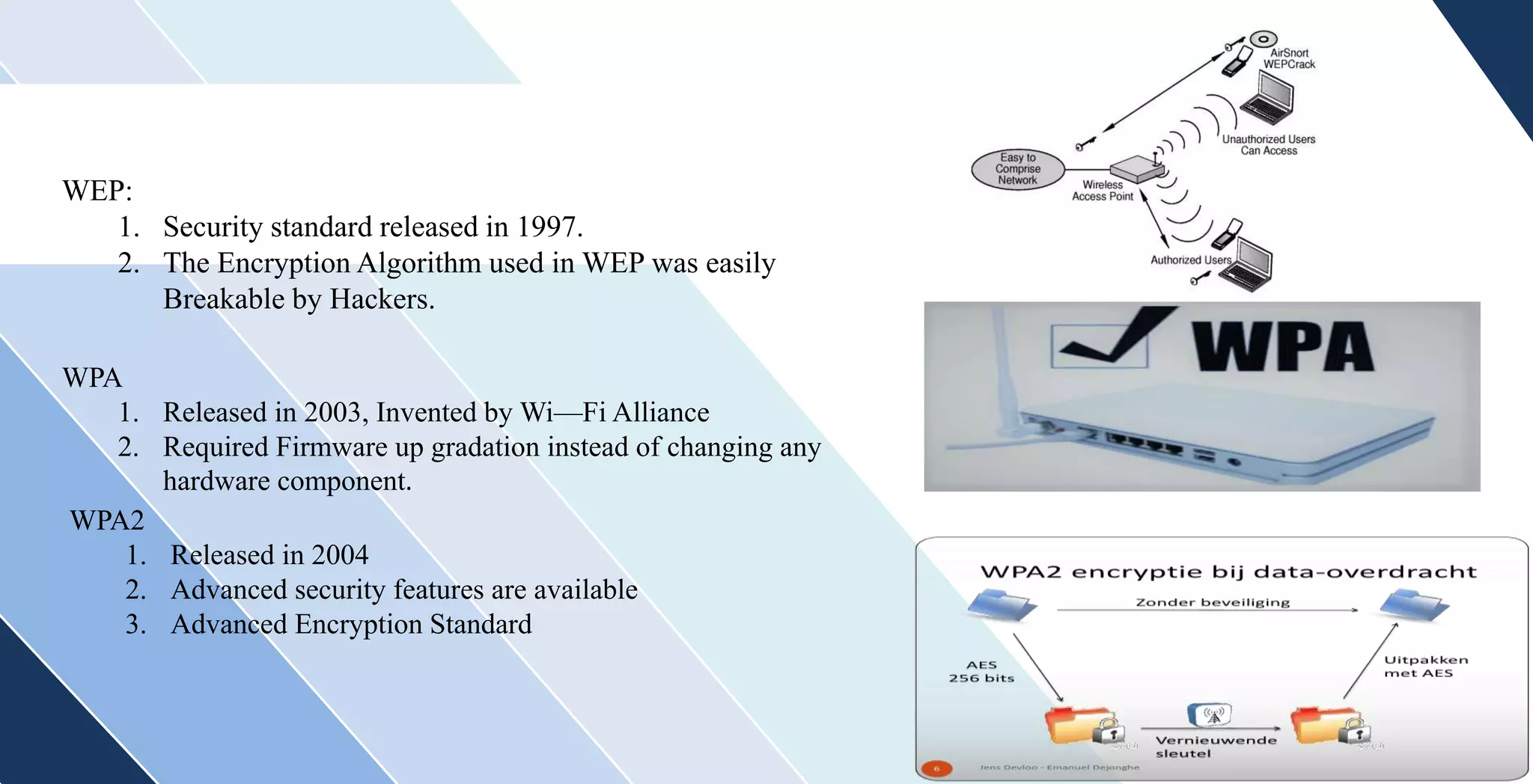
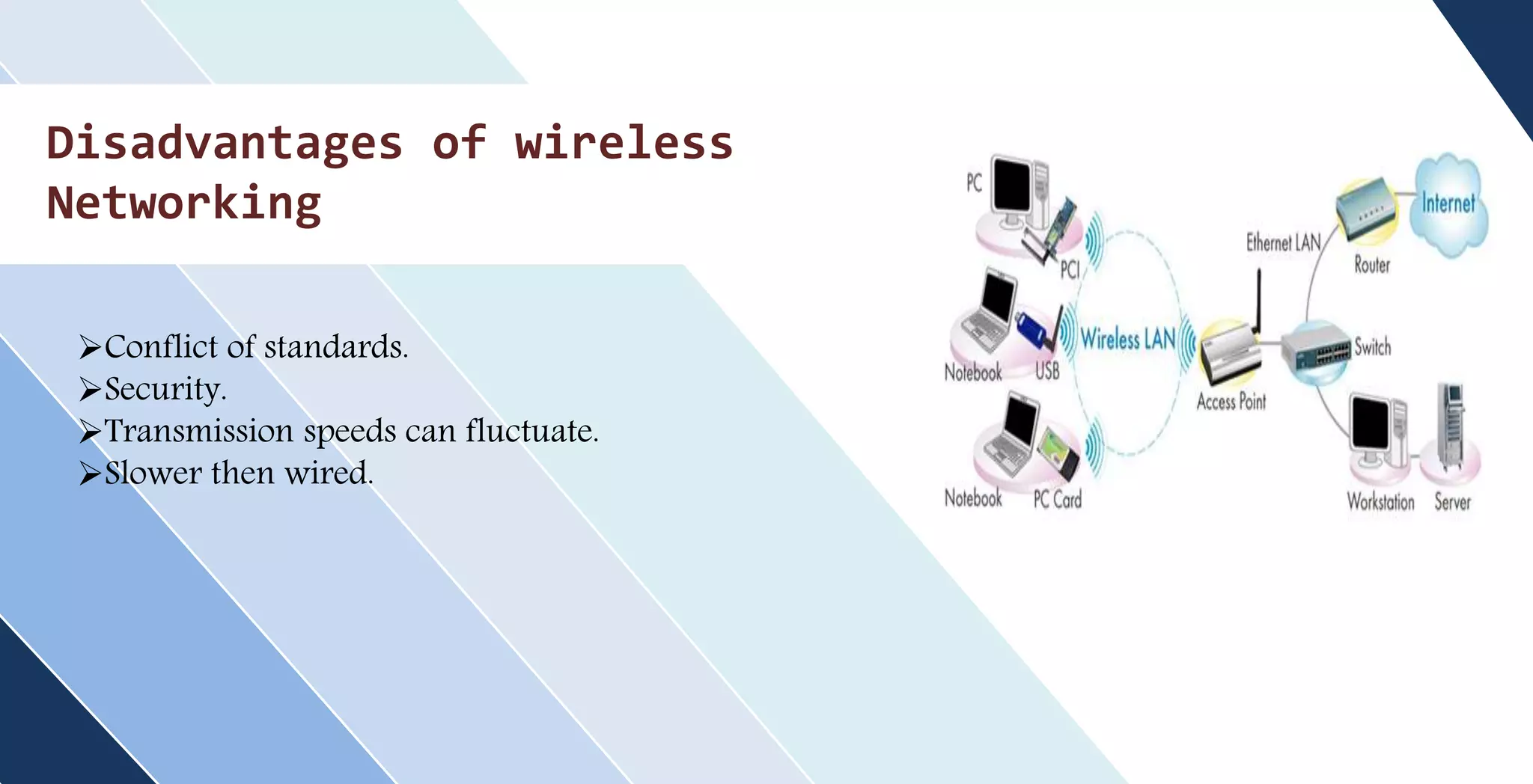
This document discusses wireless networking. It defines wireless networking as transferring data between devices without wires or cables using technologies like radio transmission. It describes the components needed for a wireless network like antennas and wireless adapters. It categorizes wireless networks into LANs, MANs, WANs and PANs based on their size and range. It also discusses security options and standards for wireless networks like WEP, WPA, and WPA2. Finally, it outlines advantages like improved access and mobility and disadvantages like potential security issues and fluctuating transmission speeds.