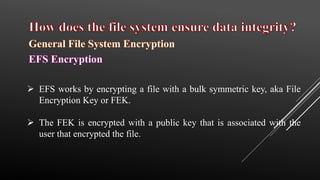
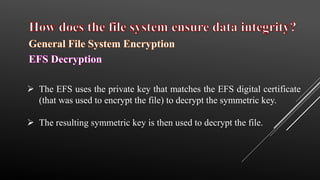
This document provides an overview of file system security, detailing the organization and management of files and directories on storage devices. It discusses various file systems such as FAT, NTFS, and HFS, and highlights security mechanisms including access control, encryption, and RAID configurations. Additionally, the document addresses common security threats like race condition attacks and alternate data streams, emphasizing the importance of access management to maintain data integrity.