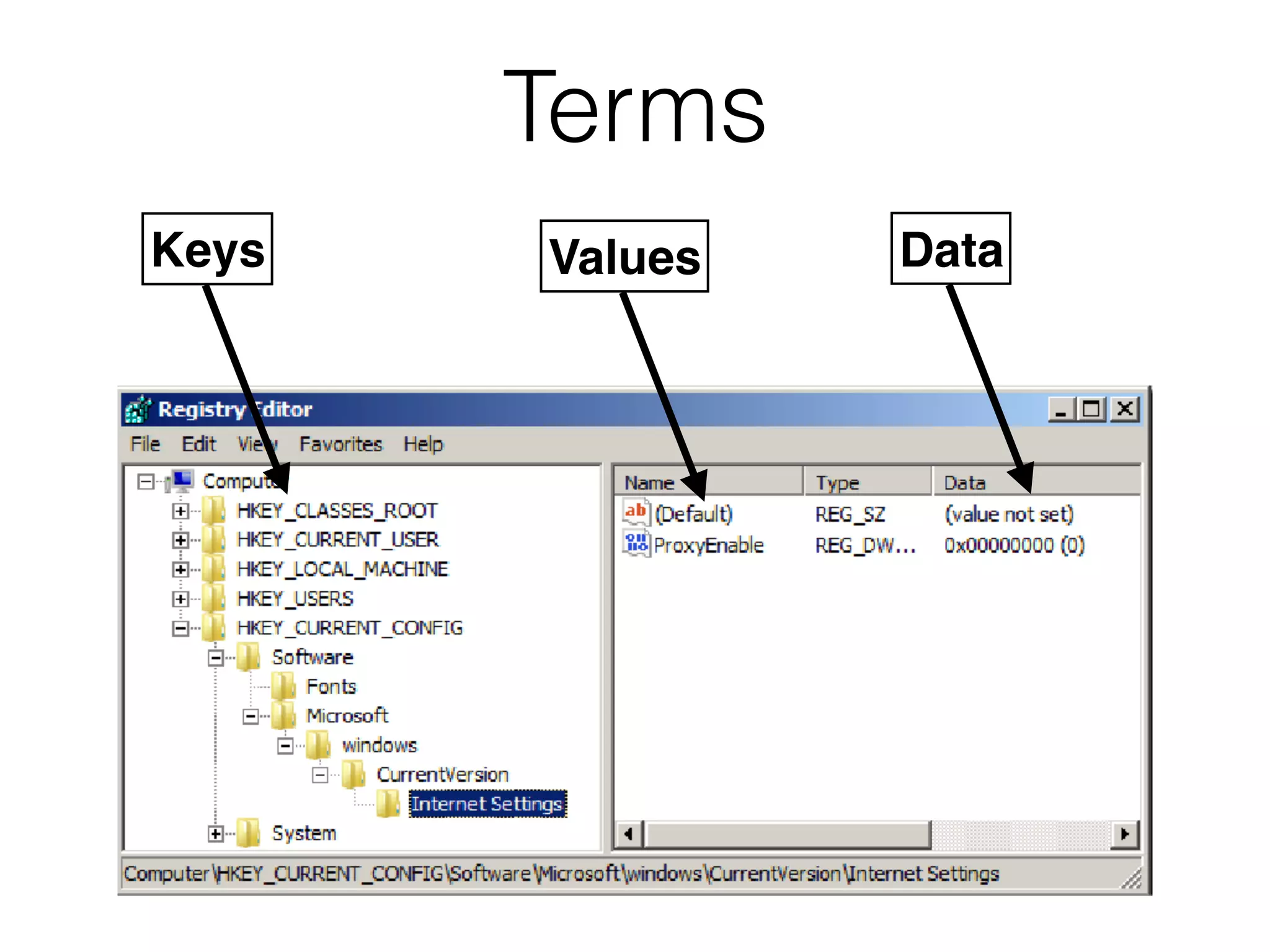
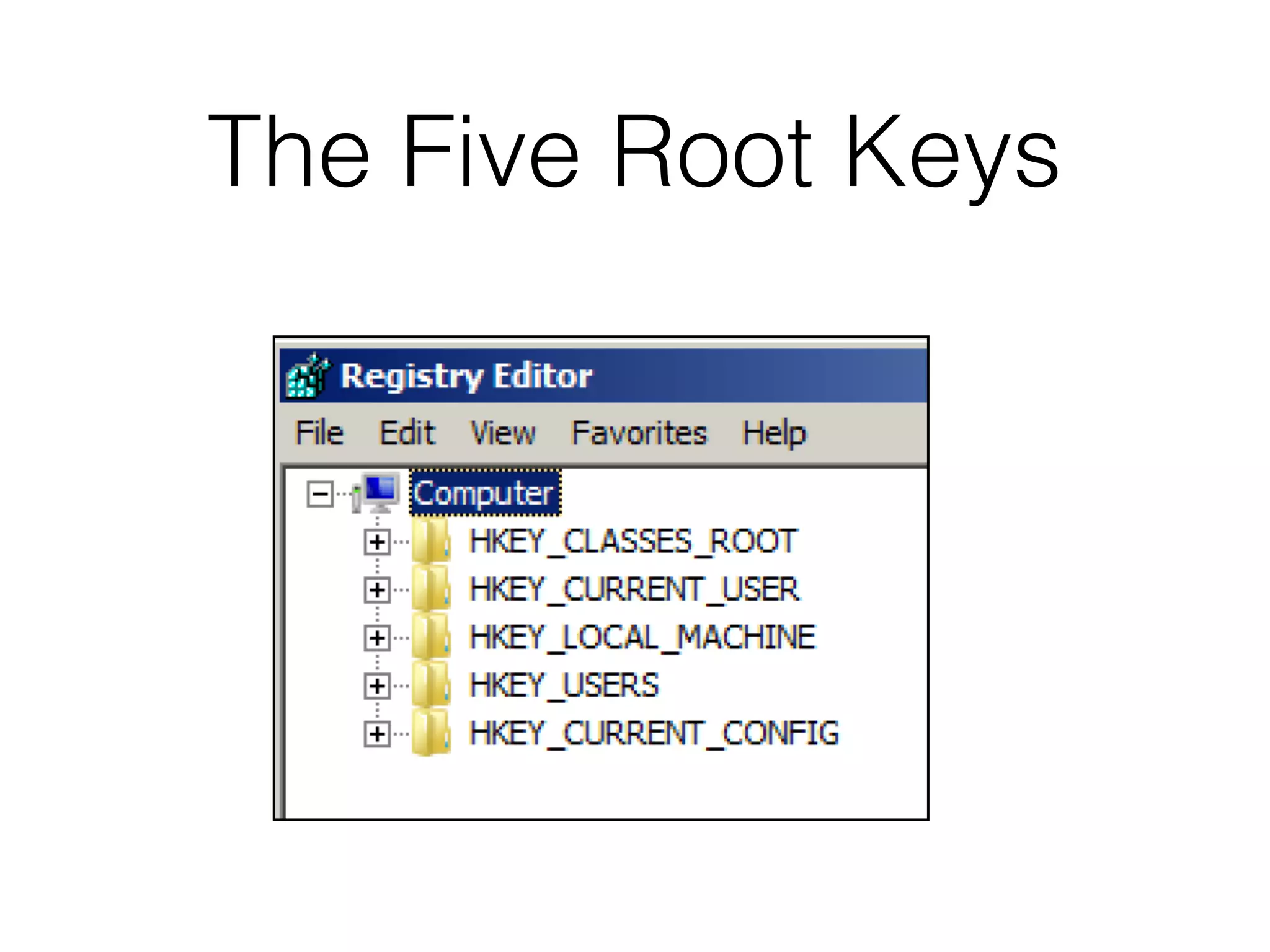
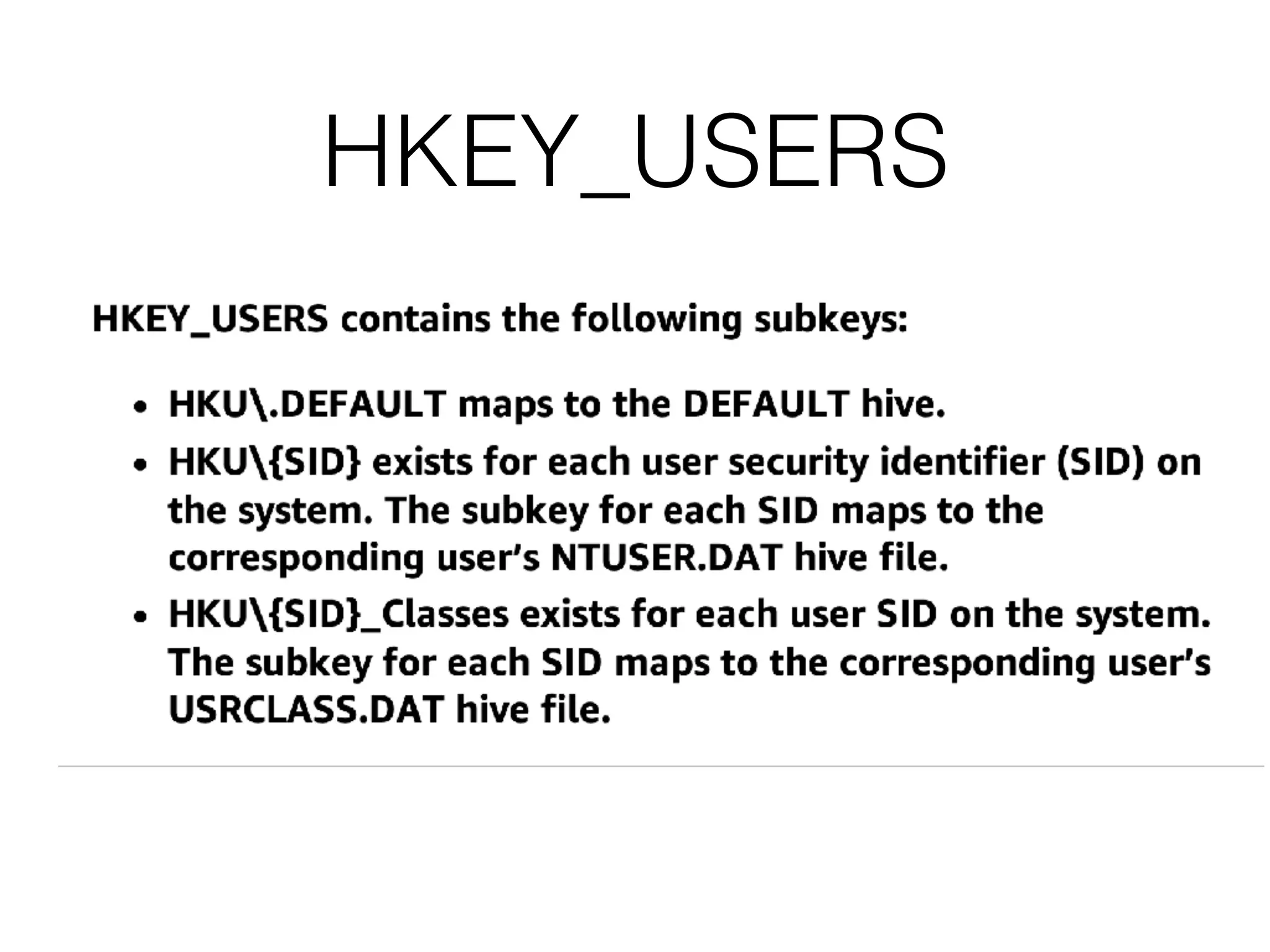
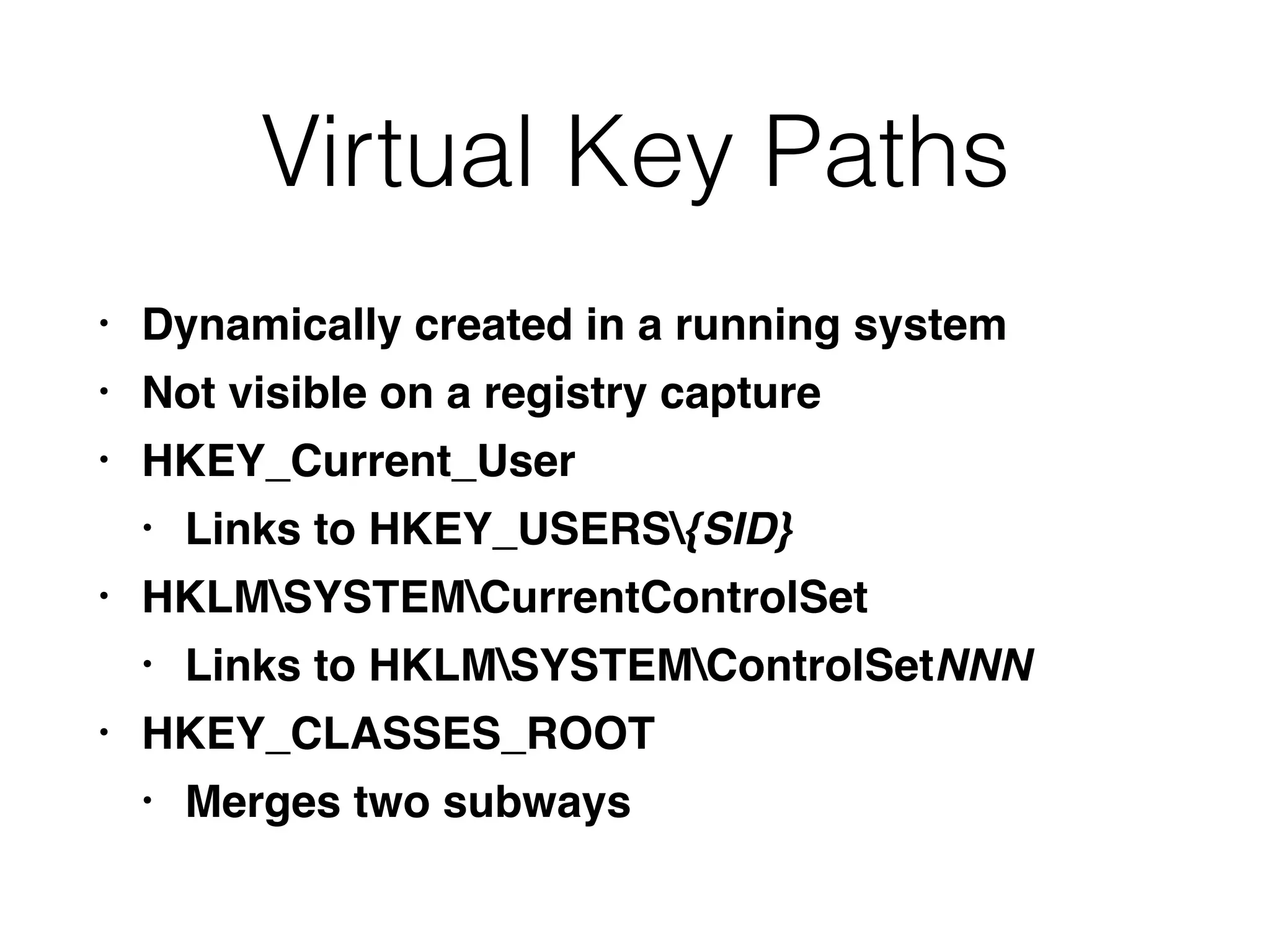
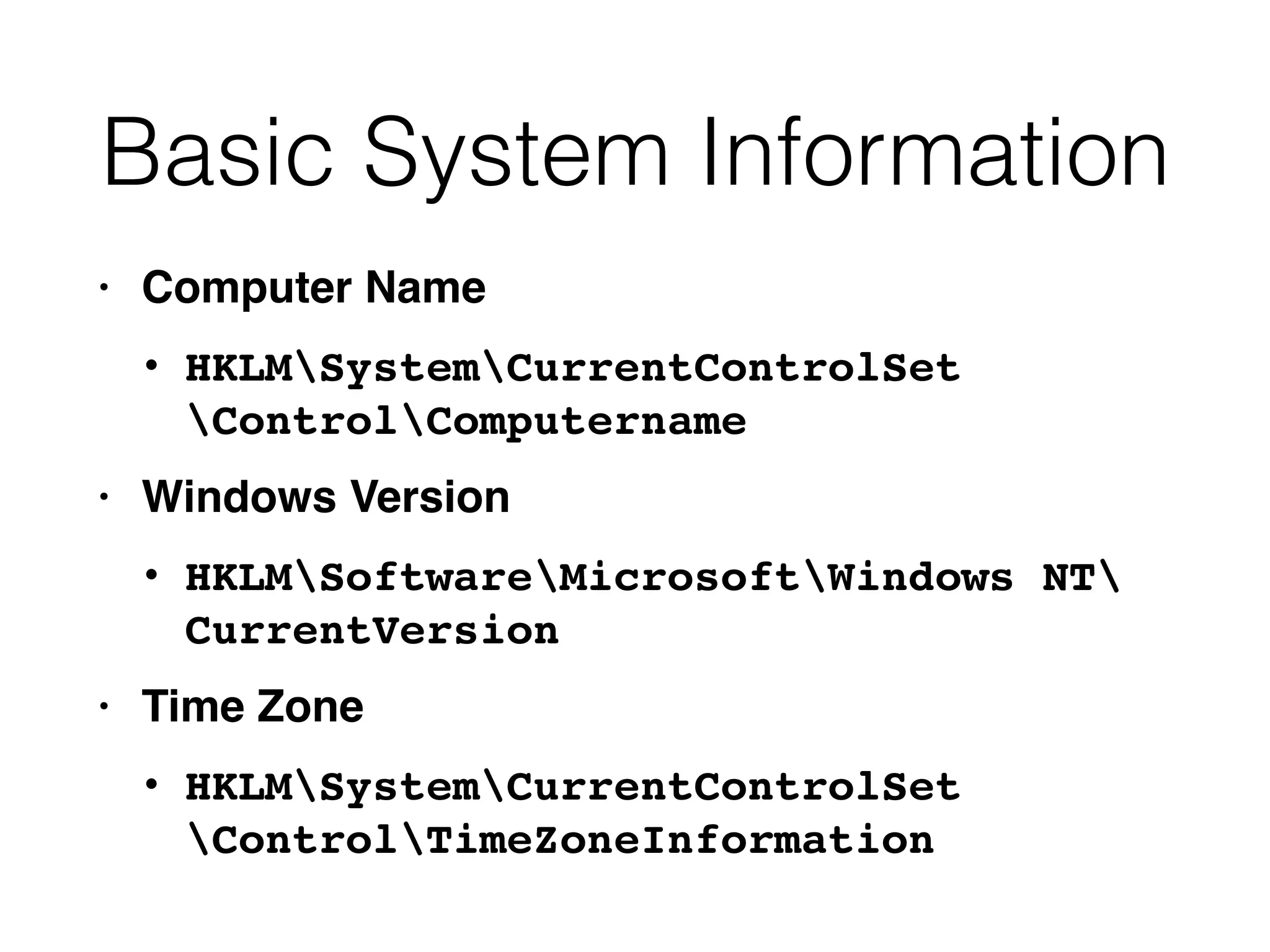
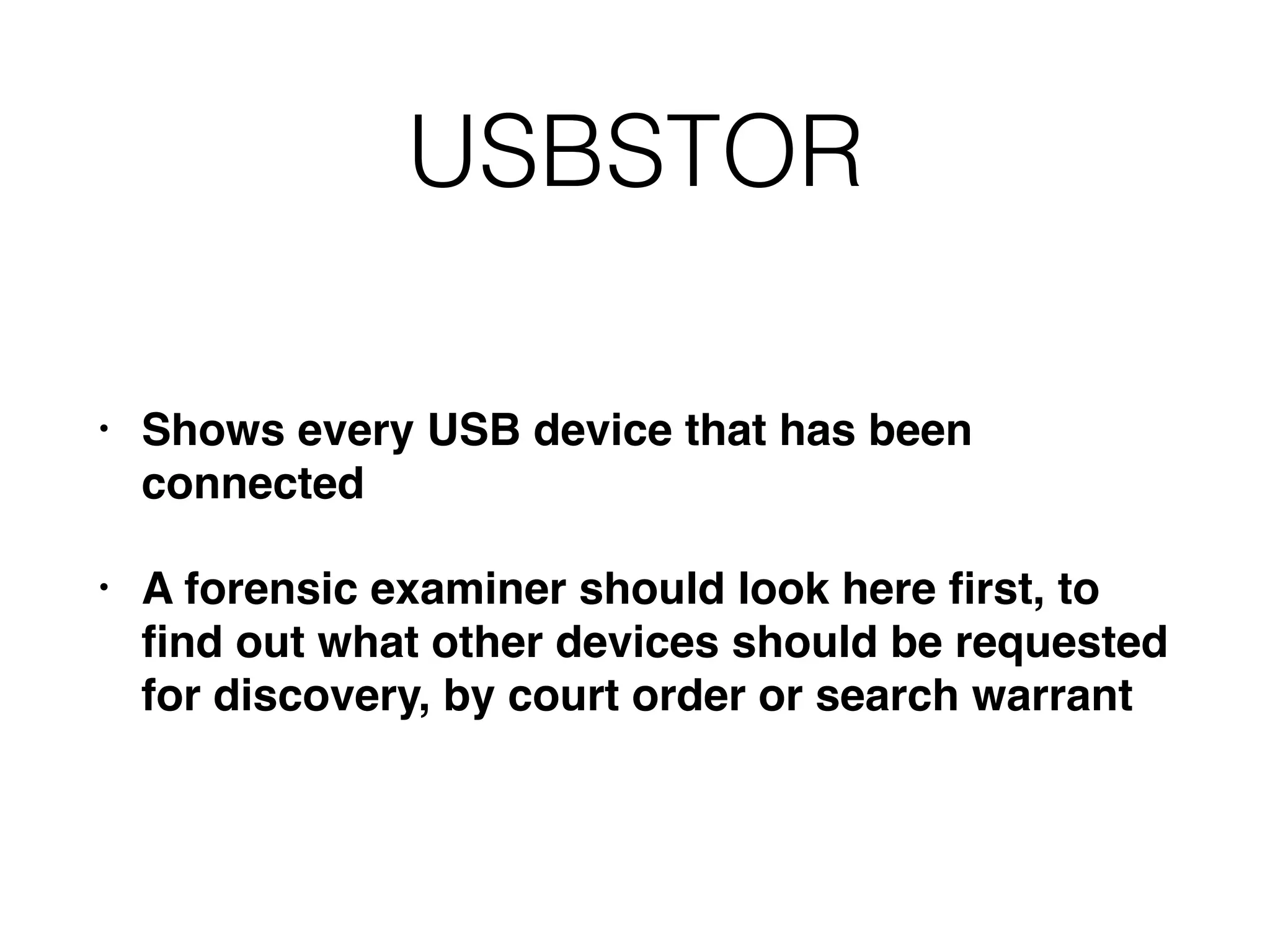
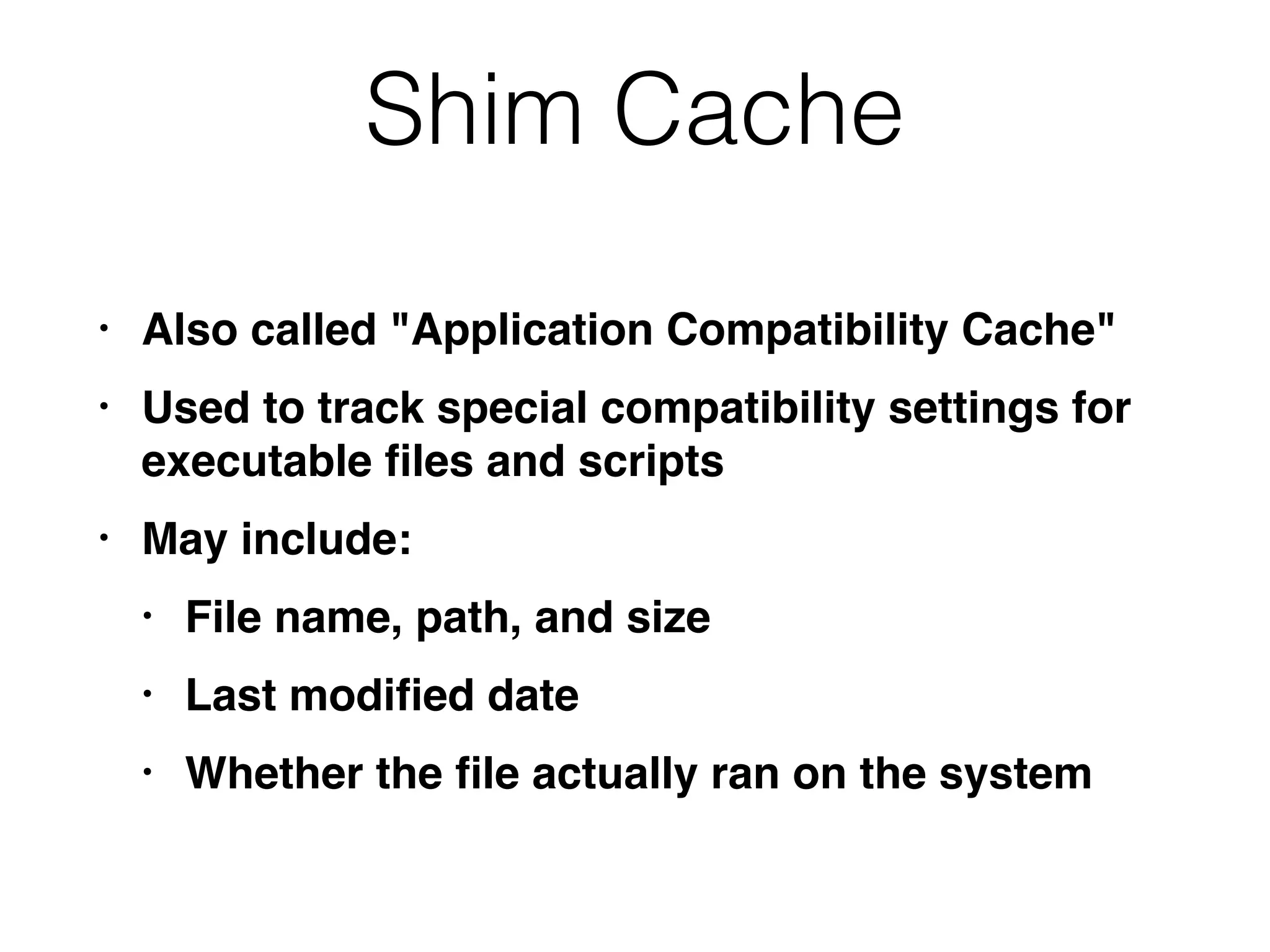
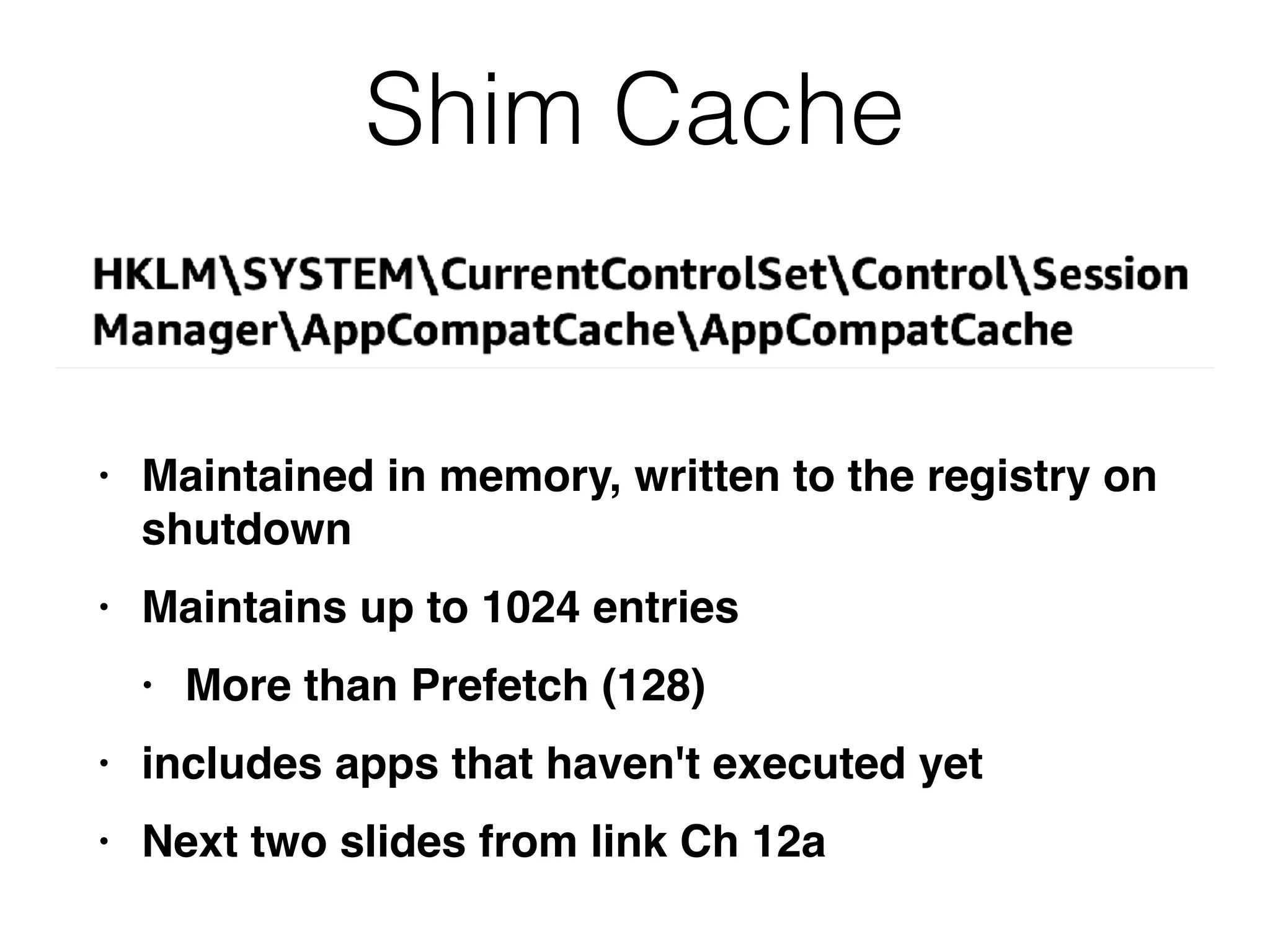
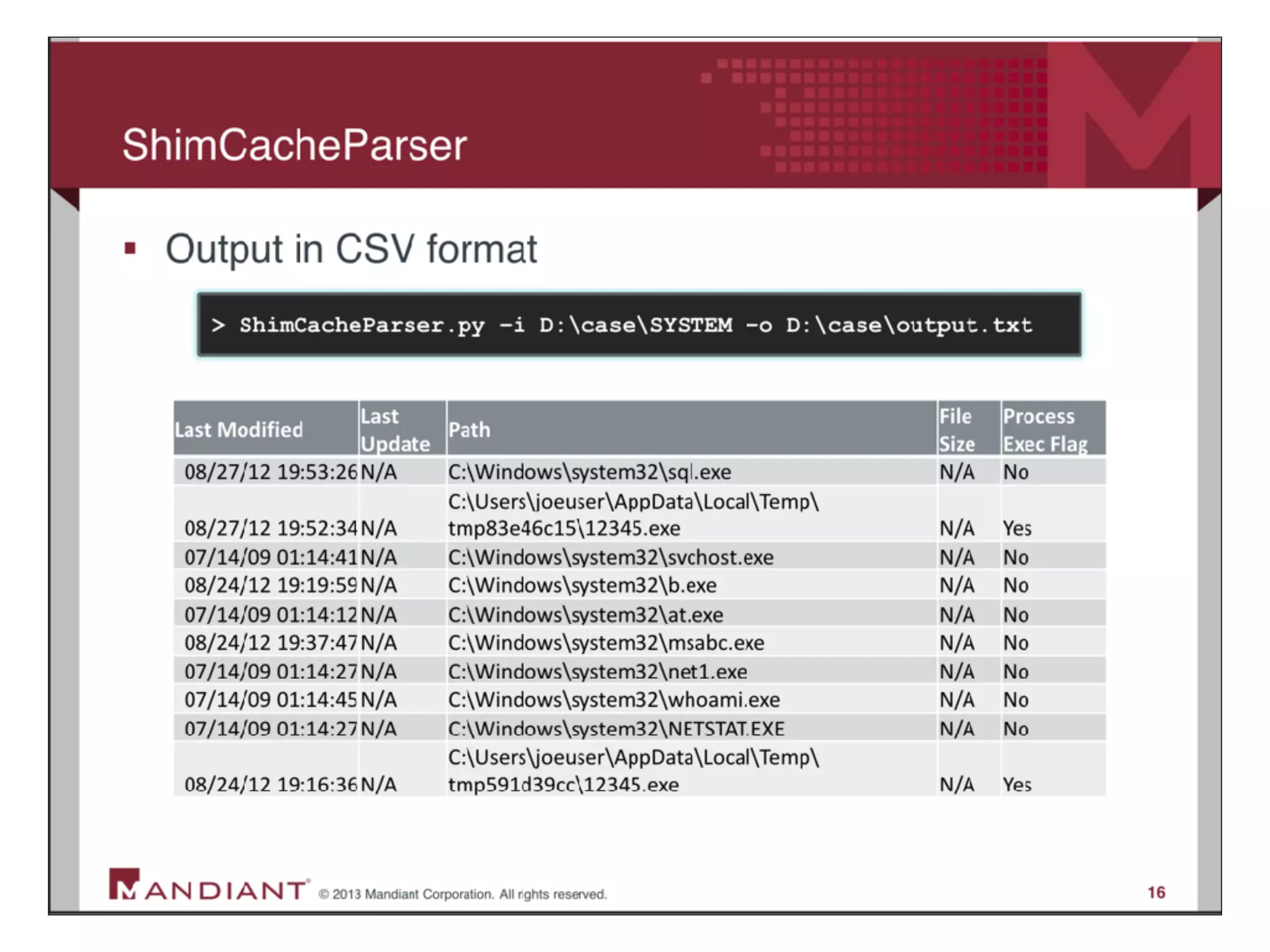
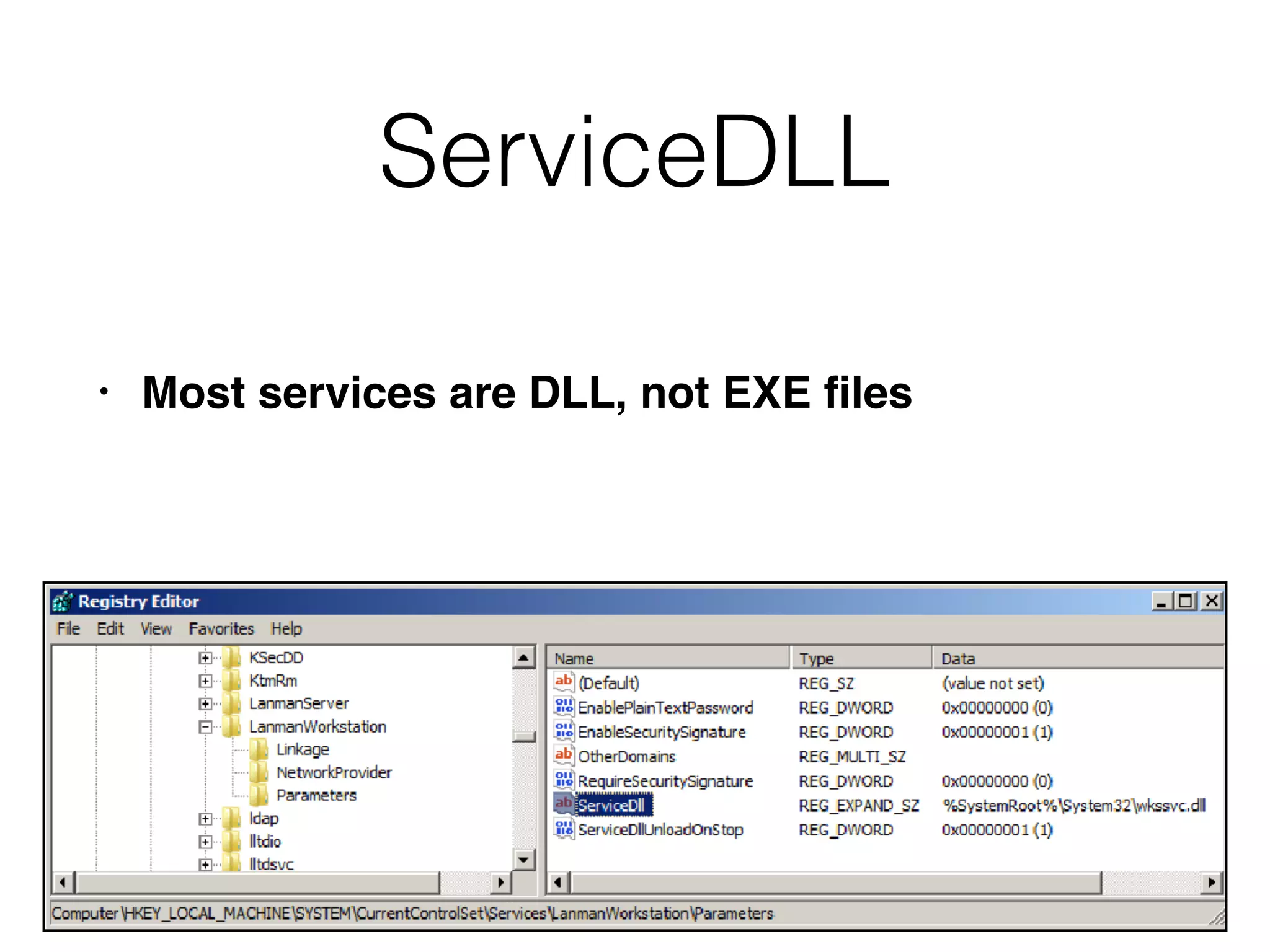
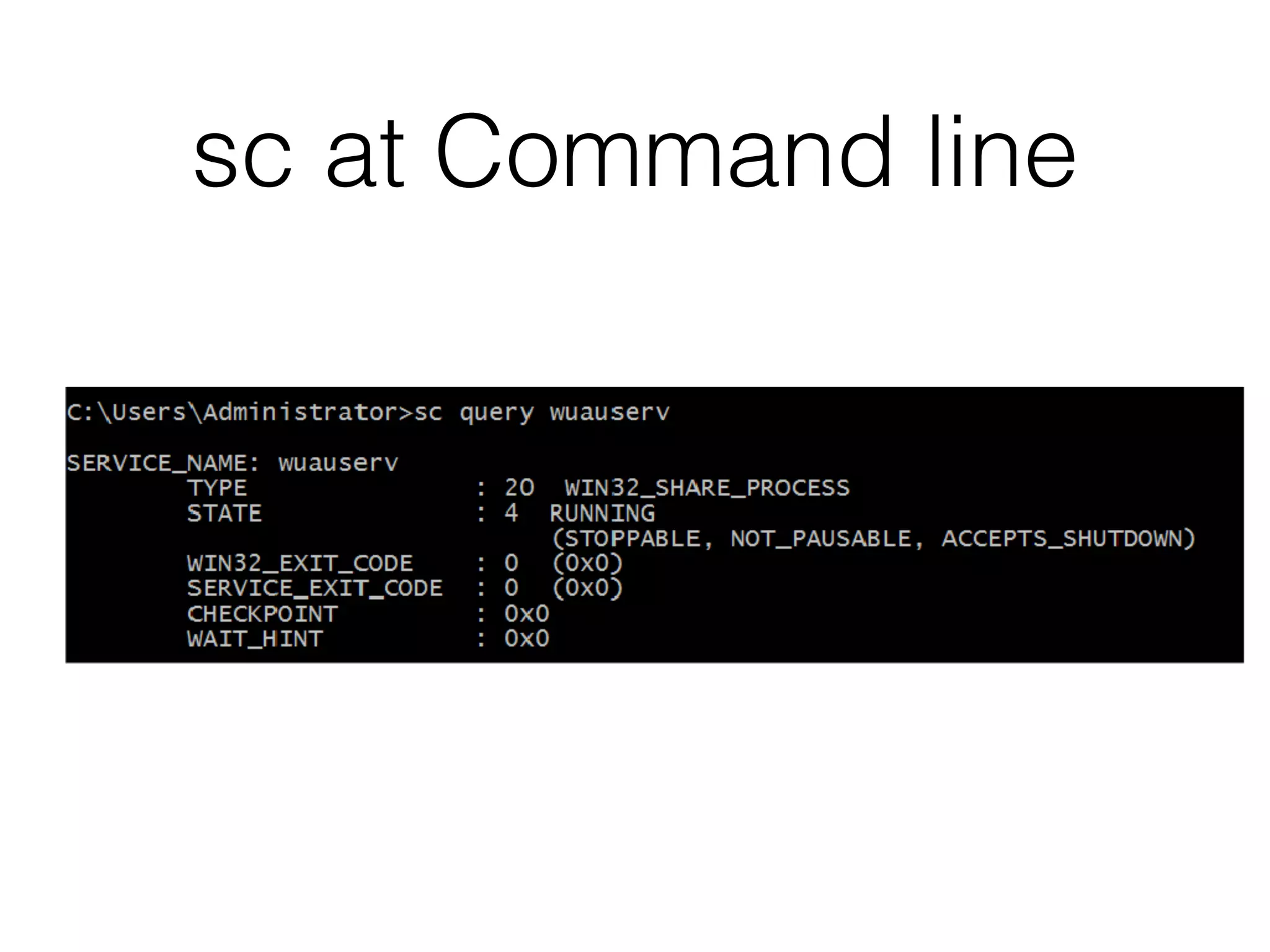
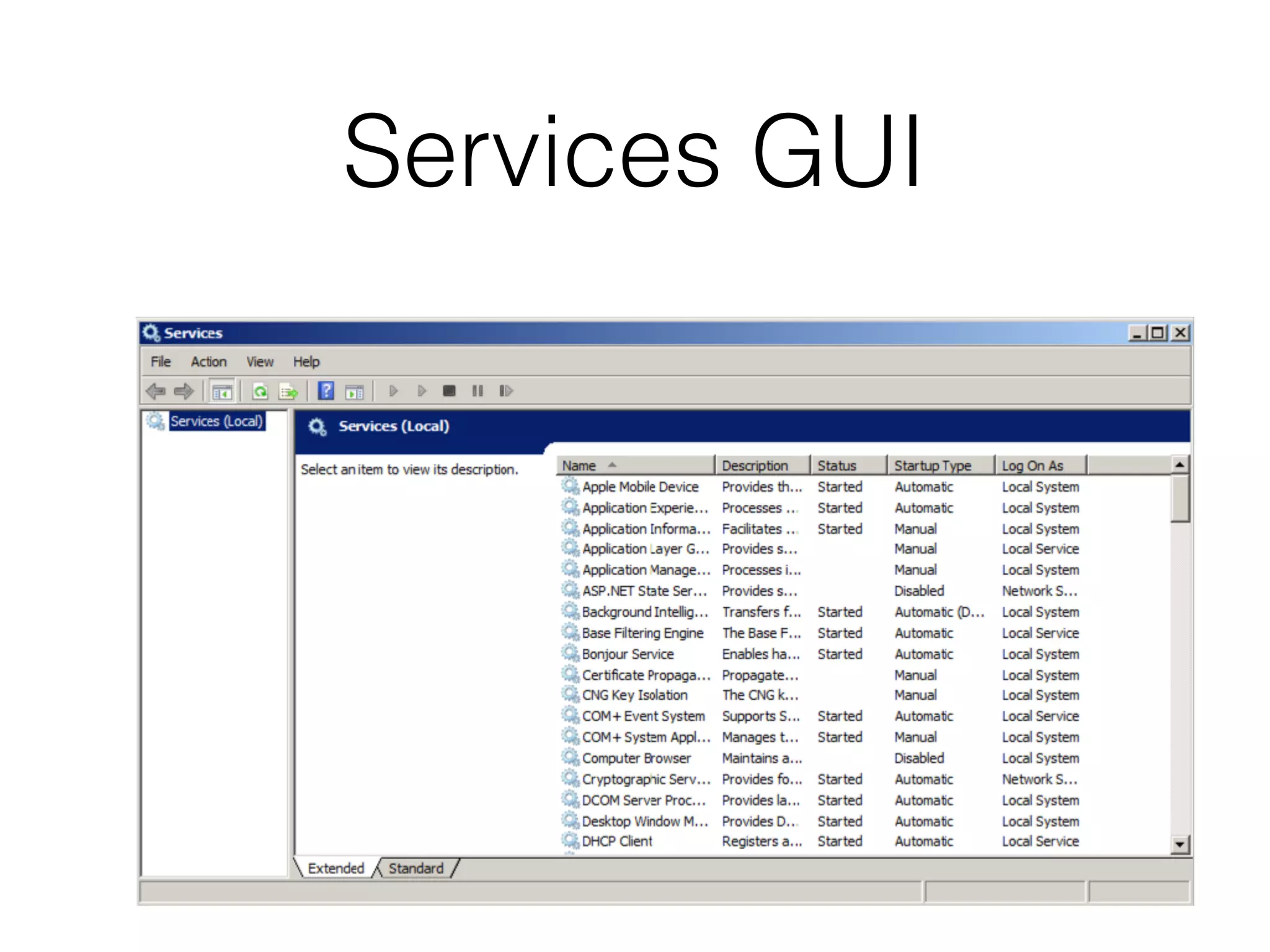
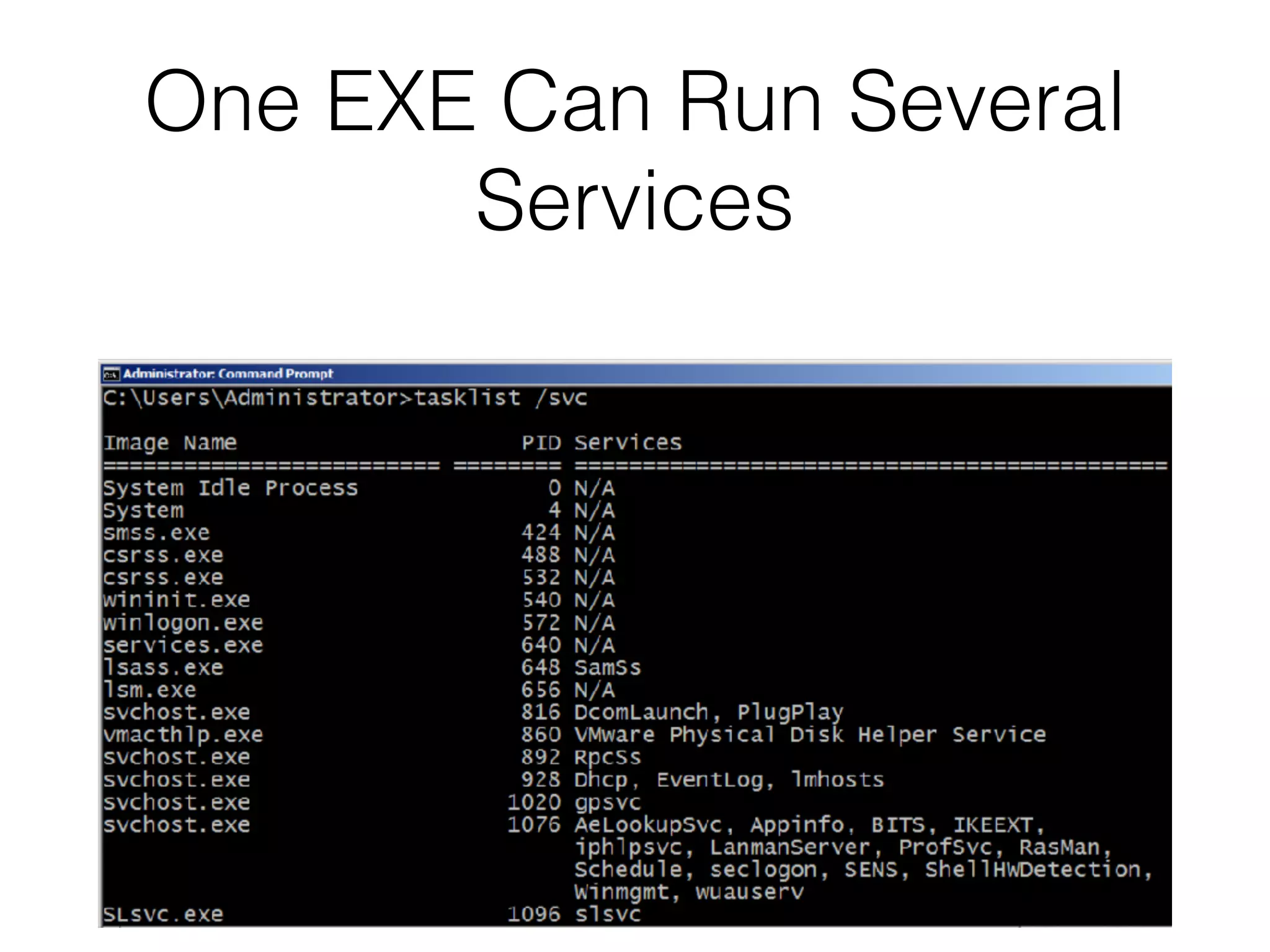
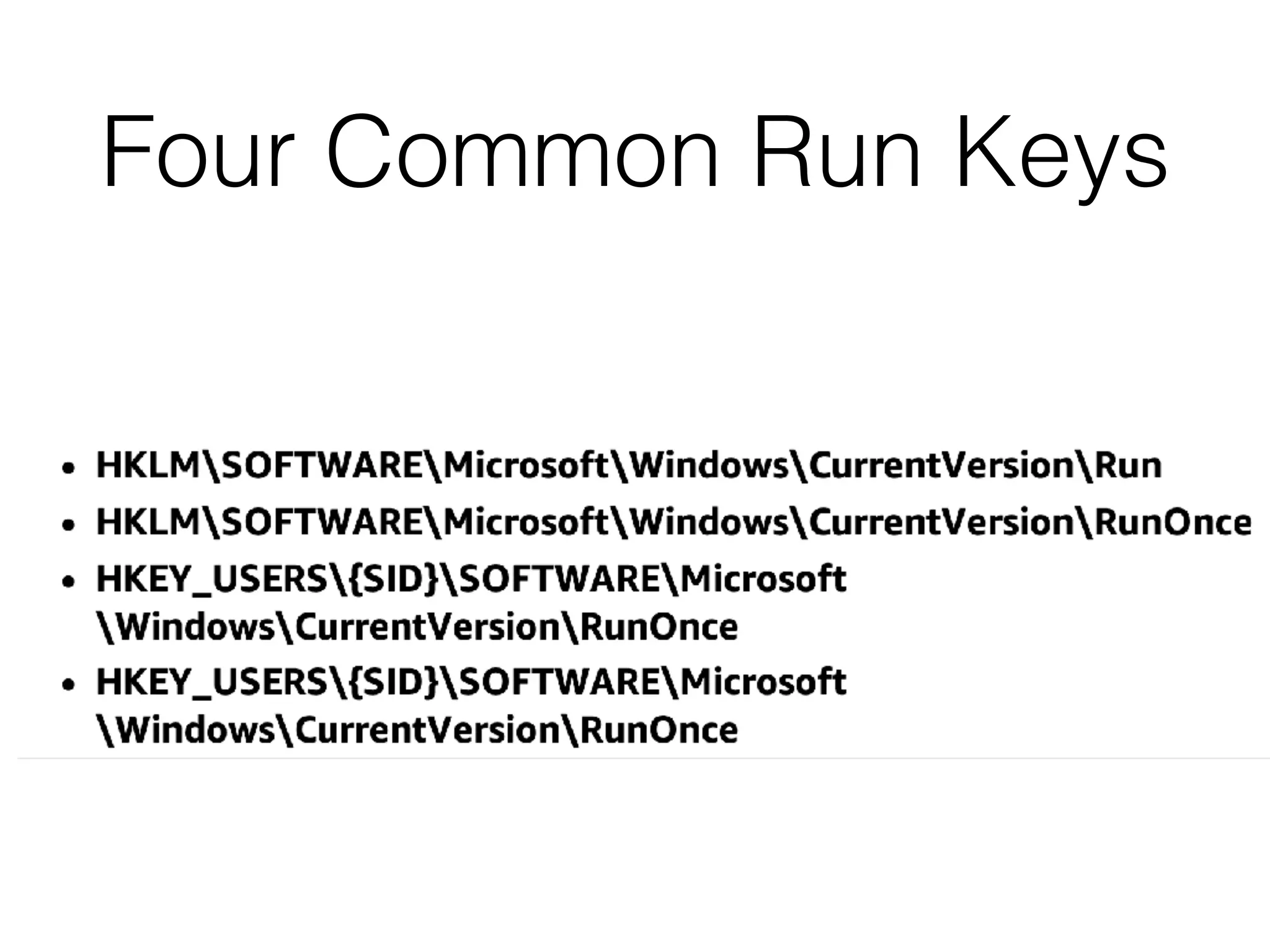
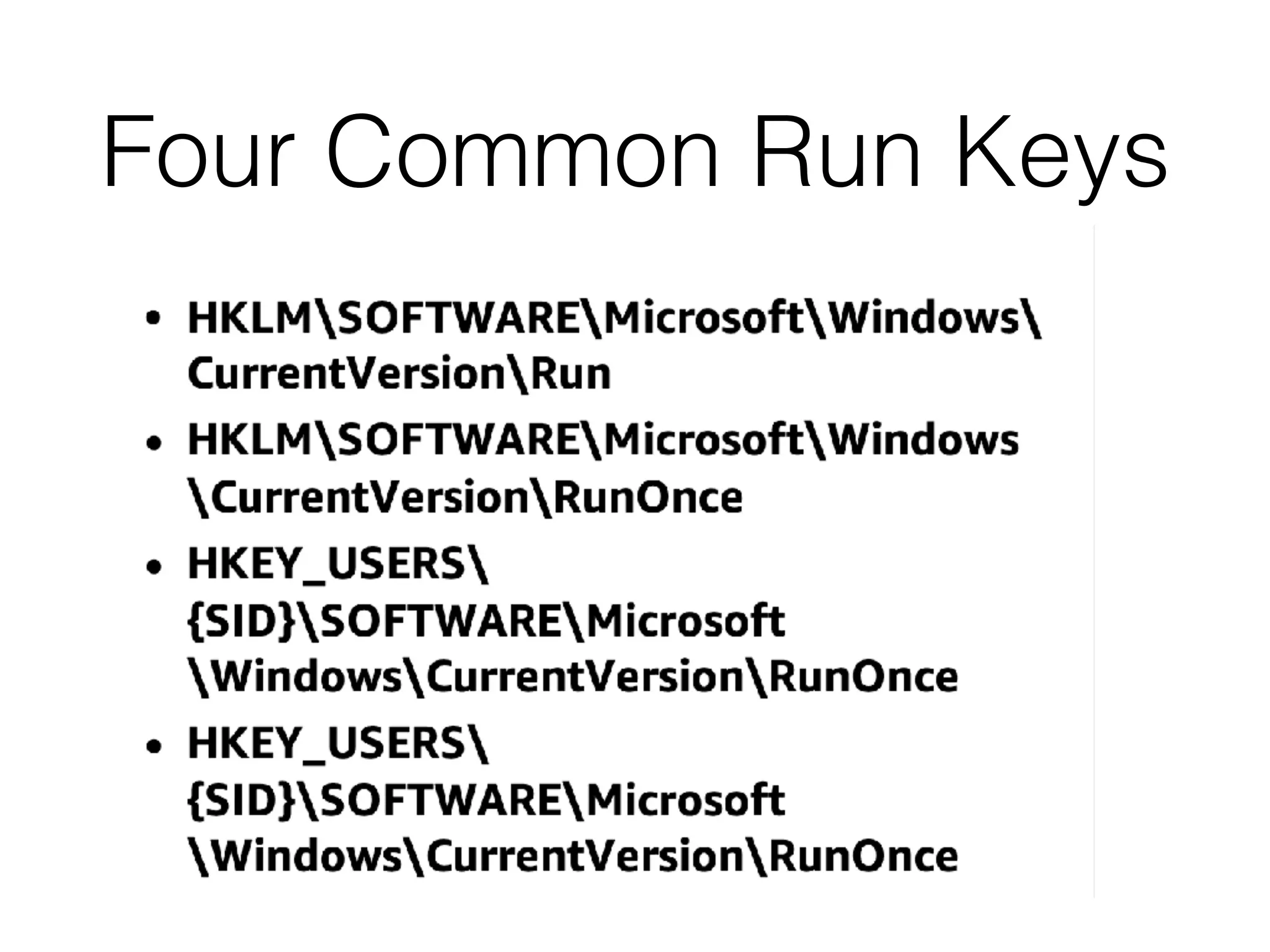
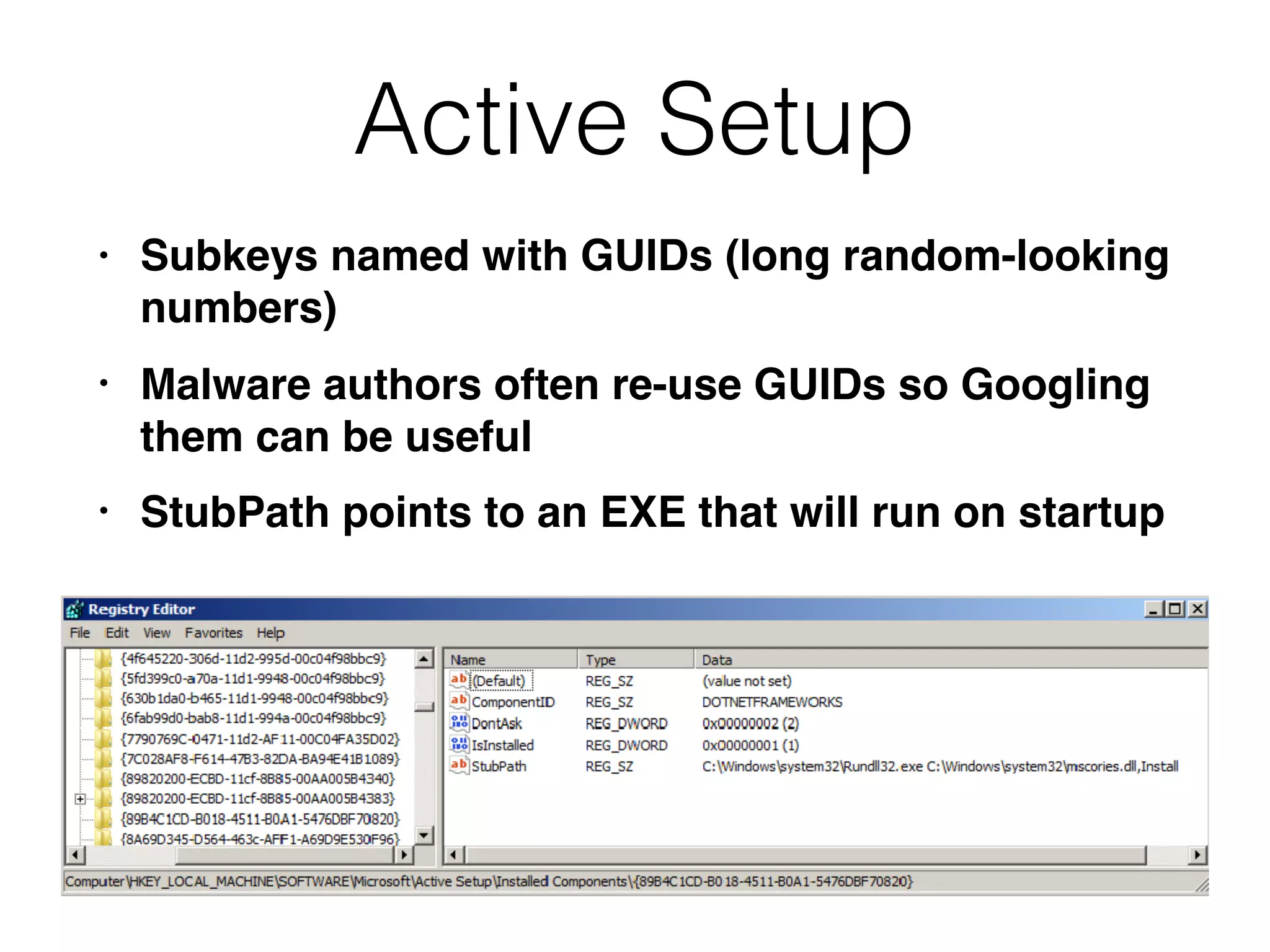
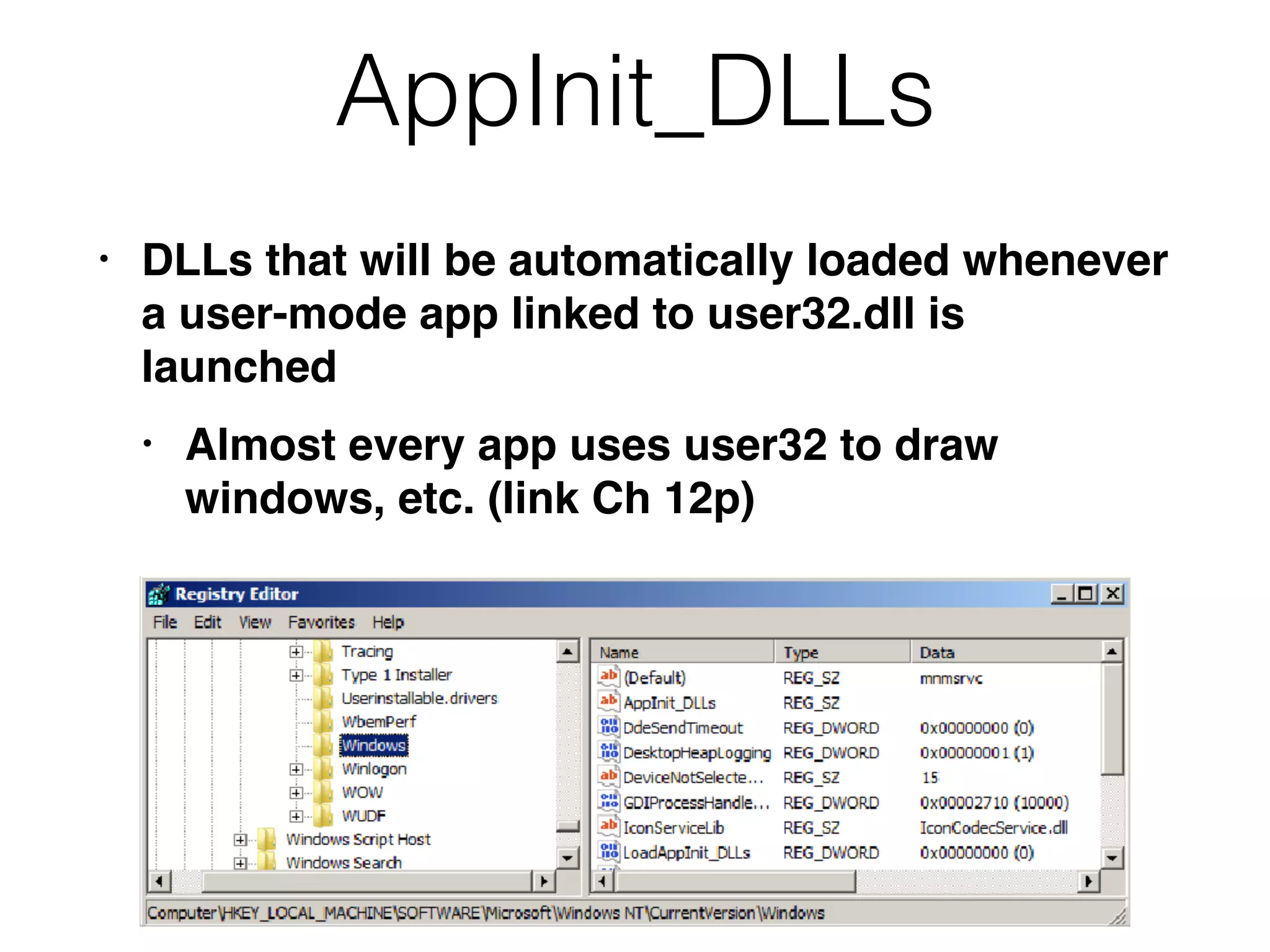
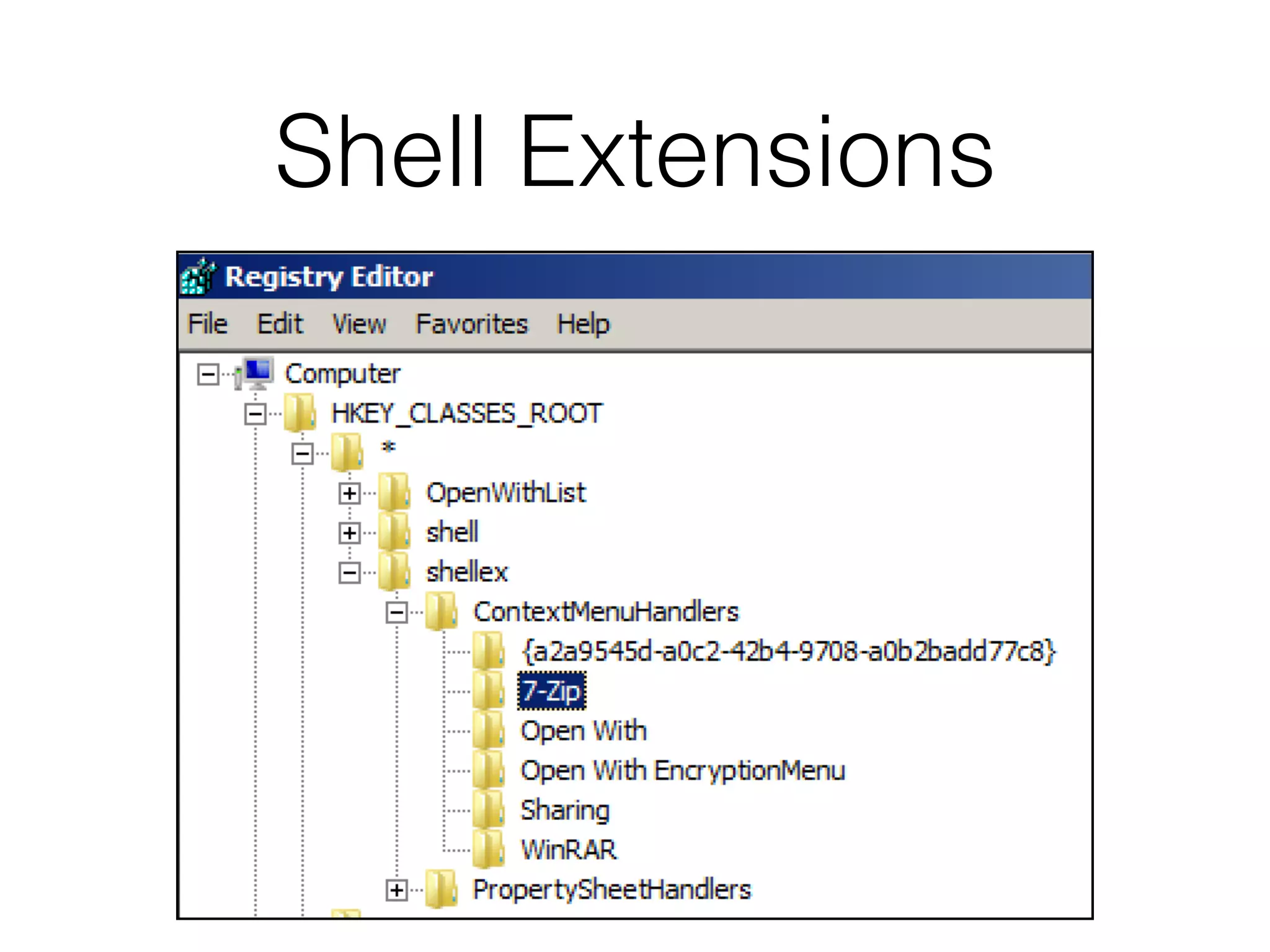
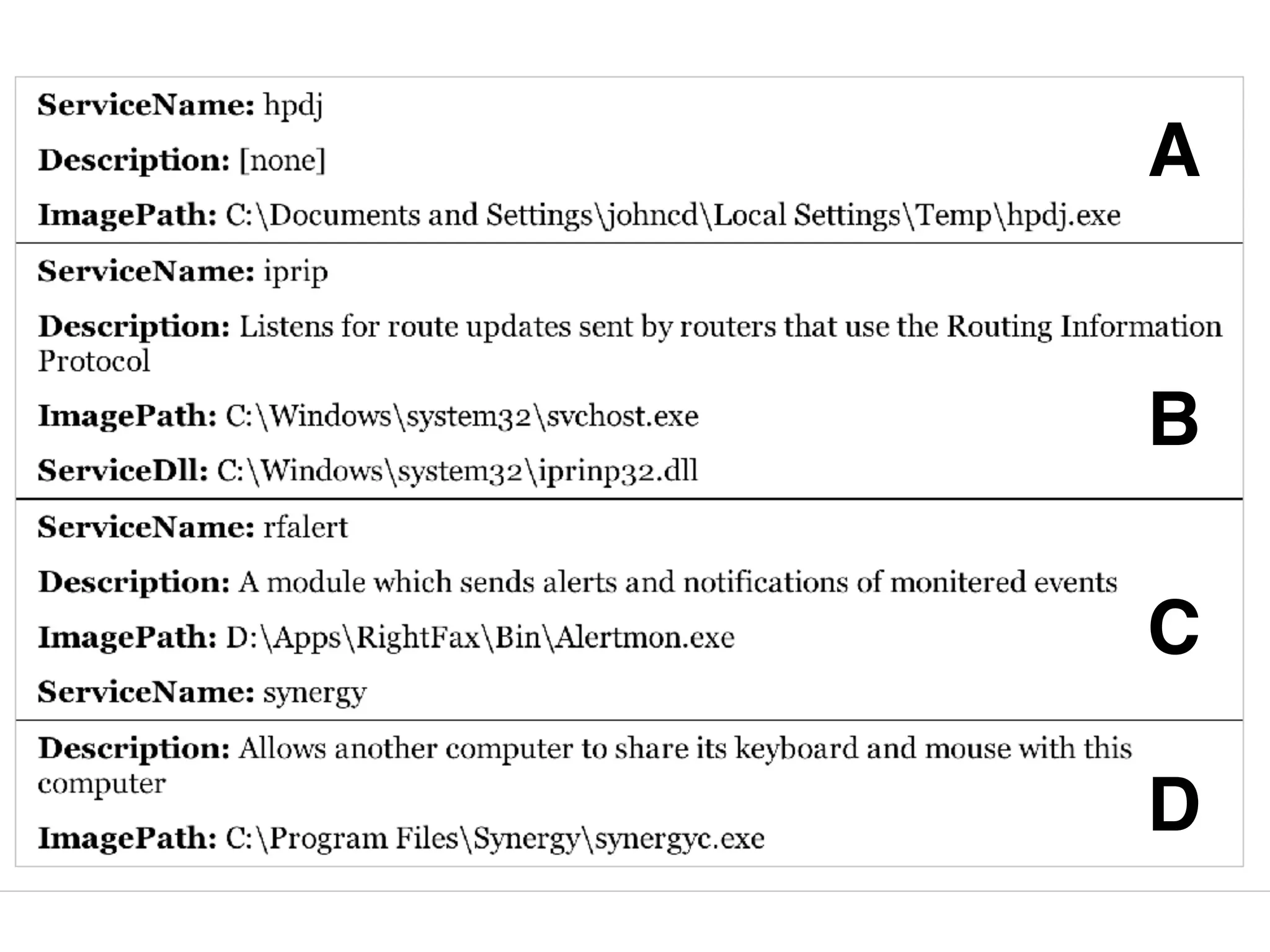
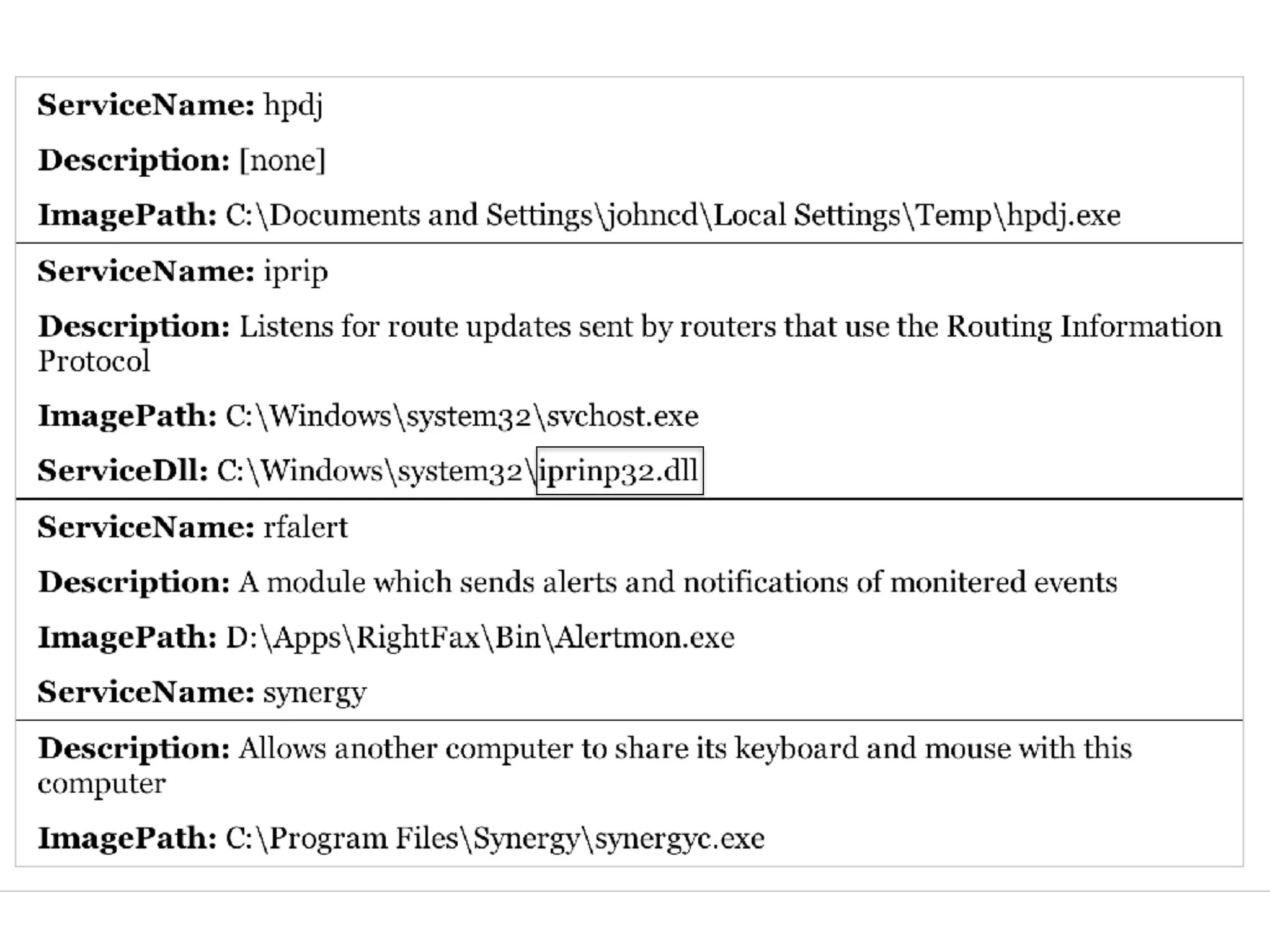
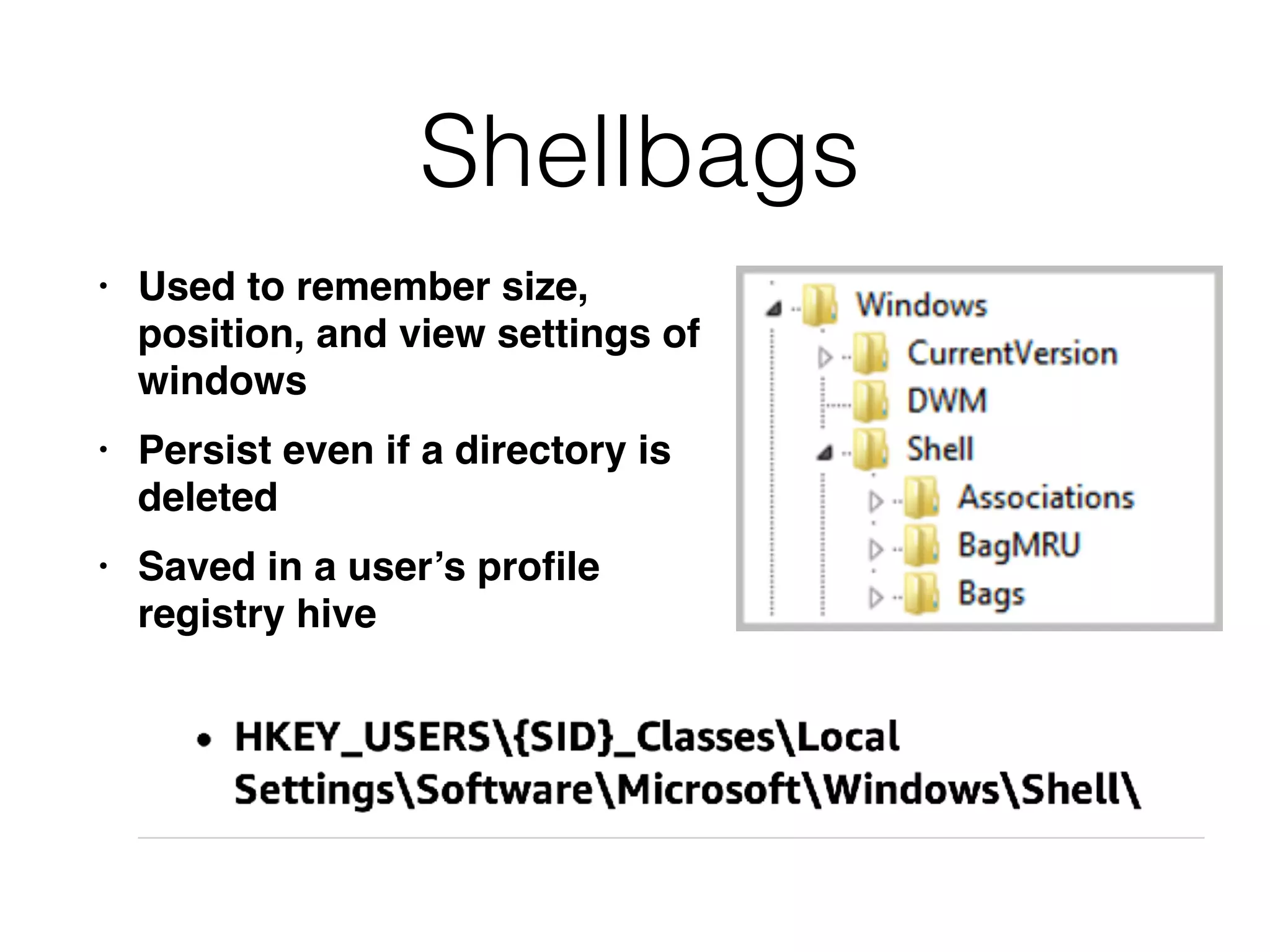
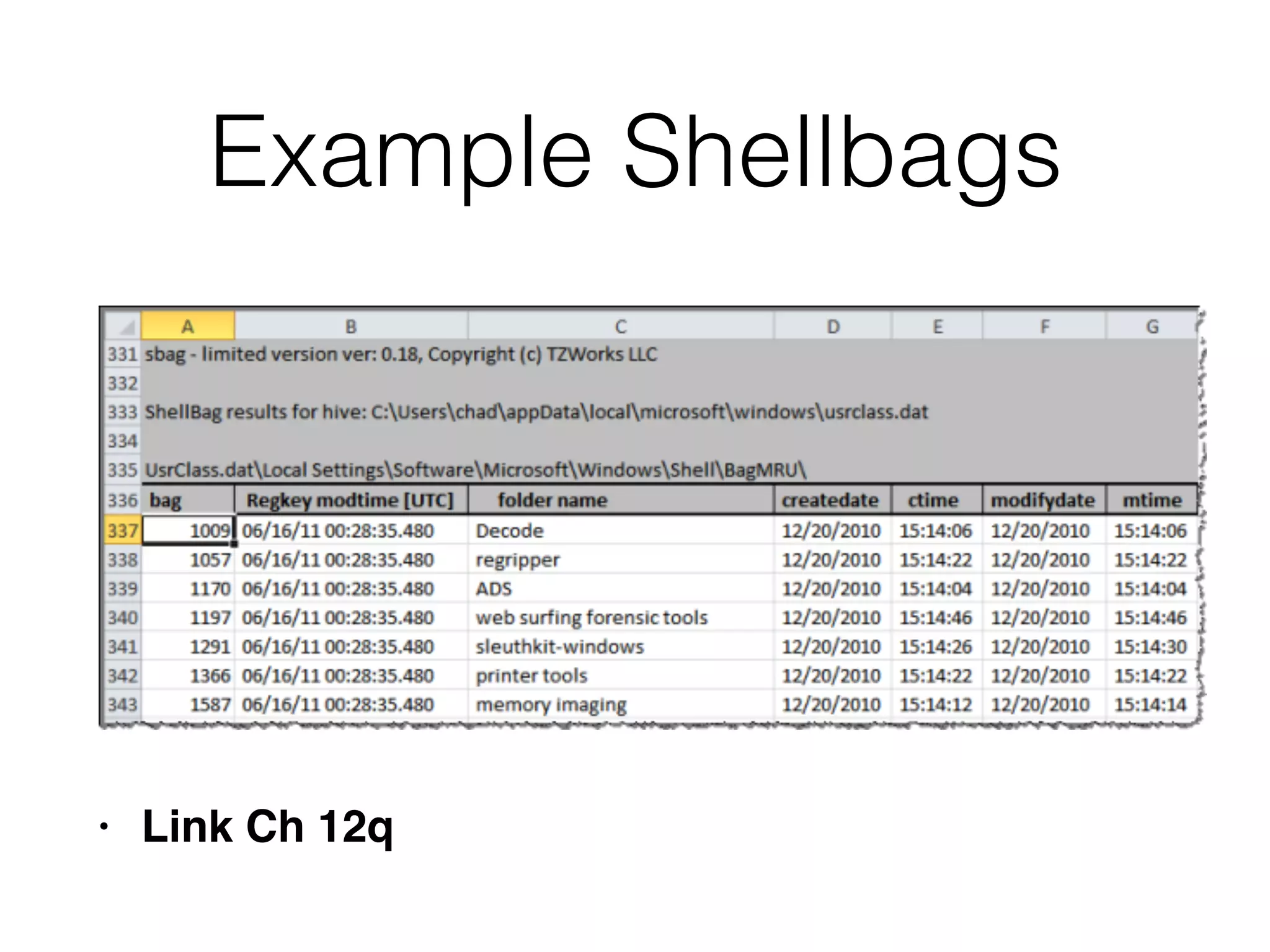
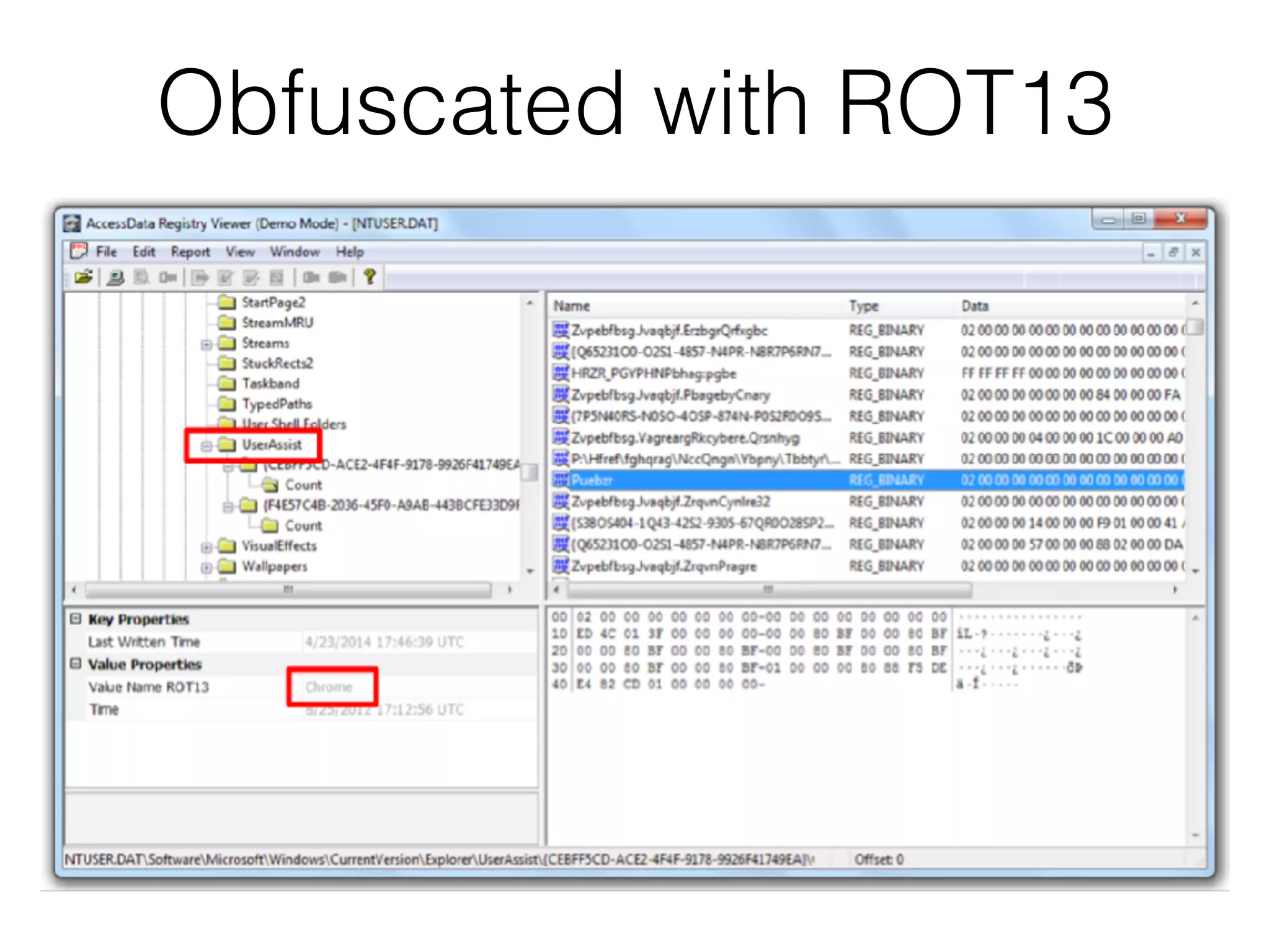
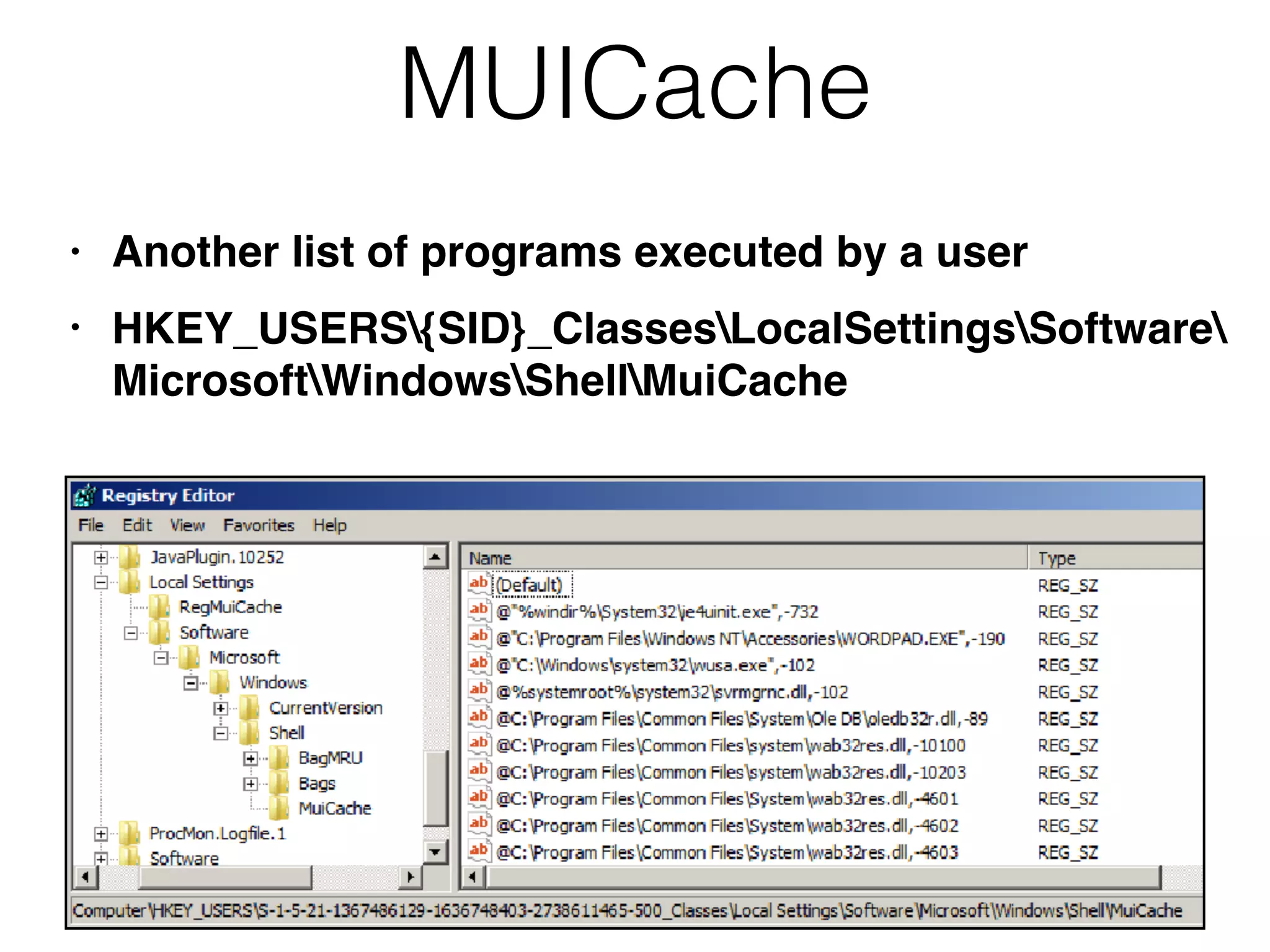
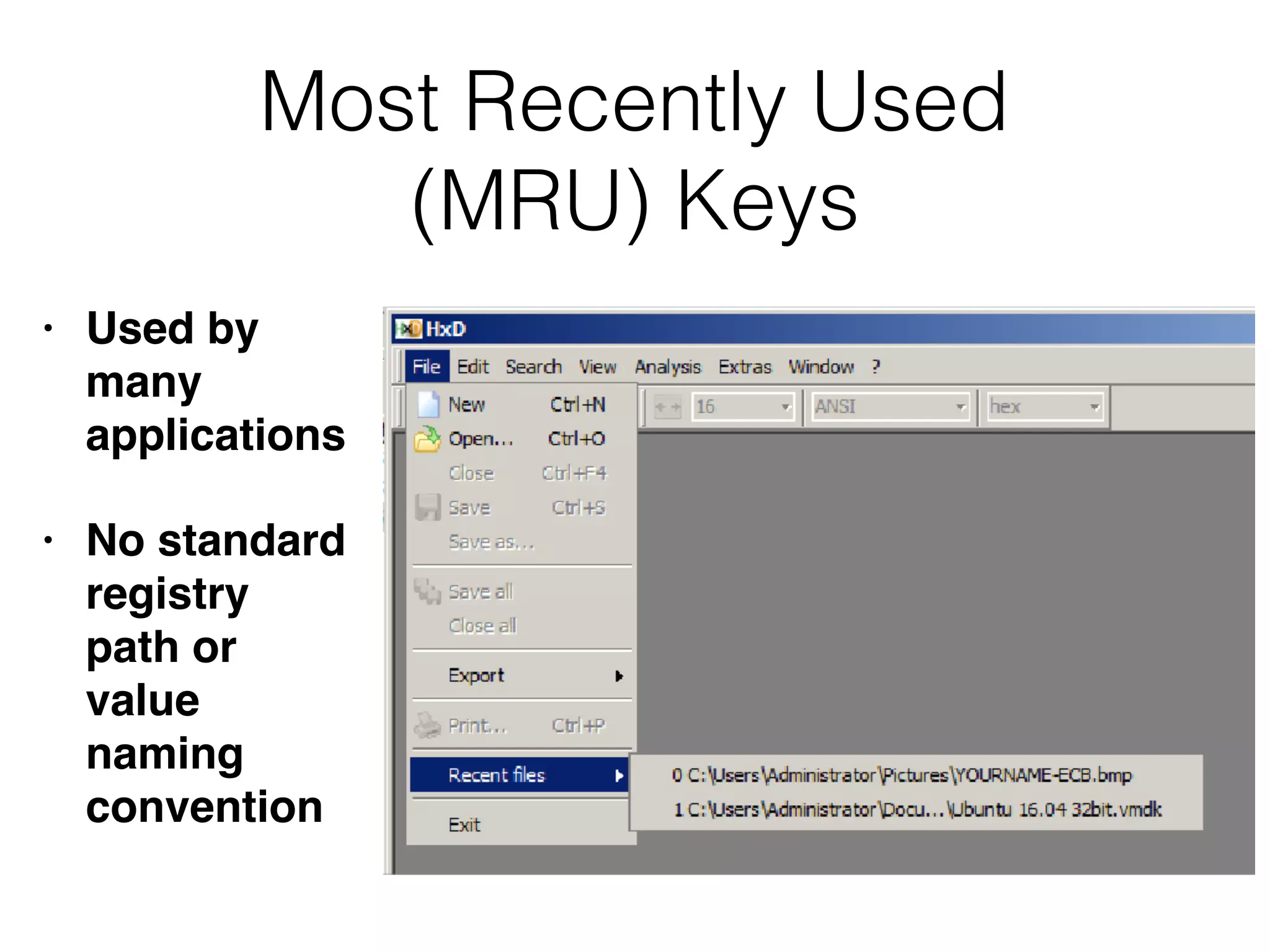
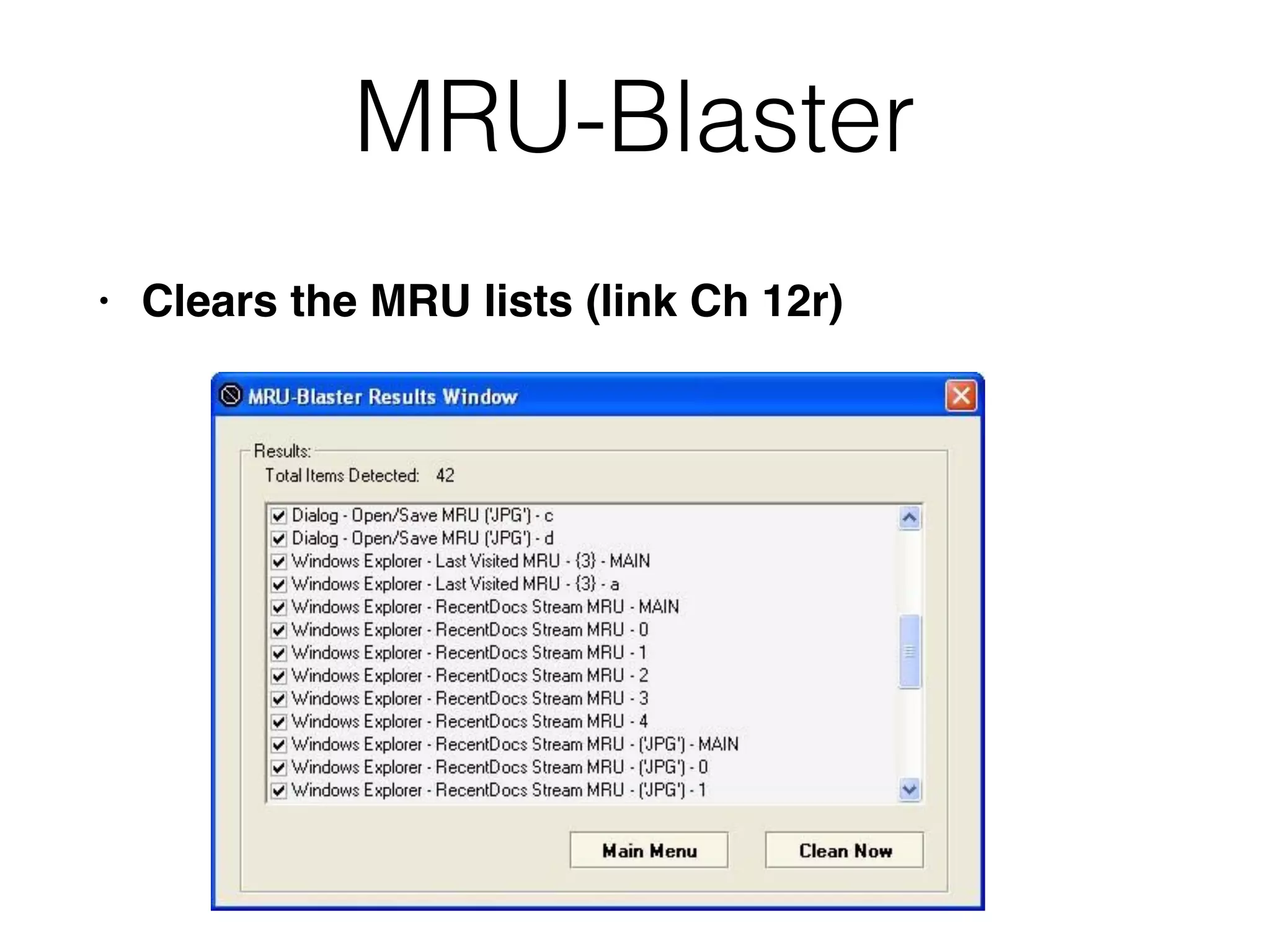
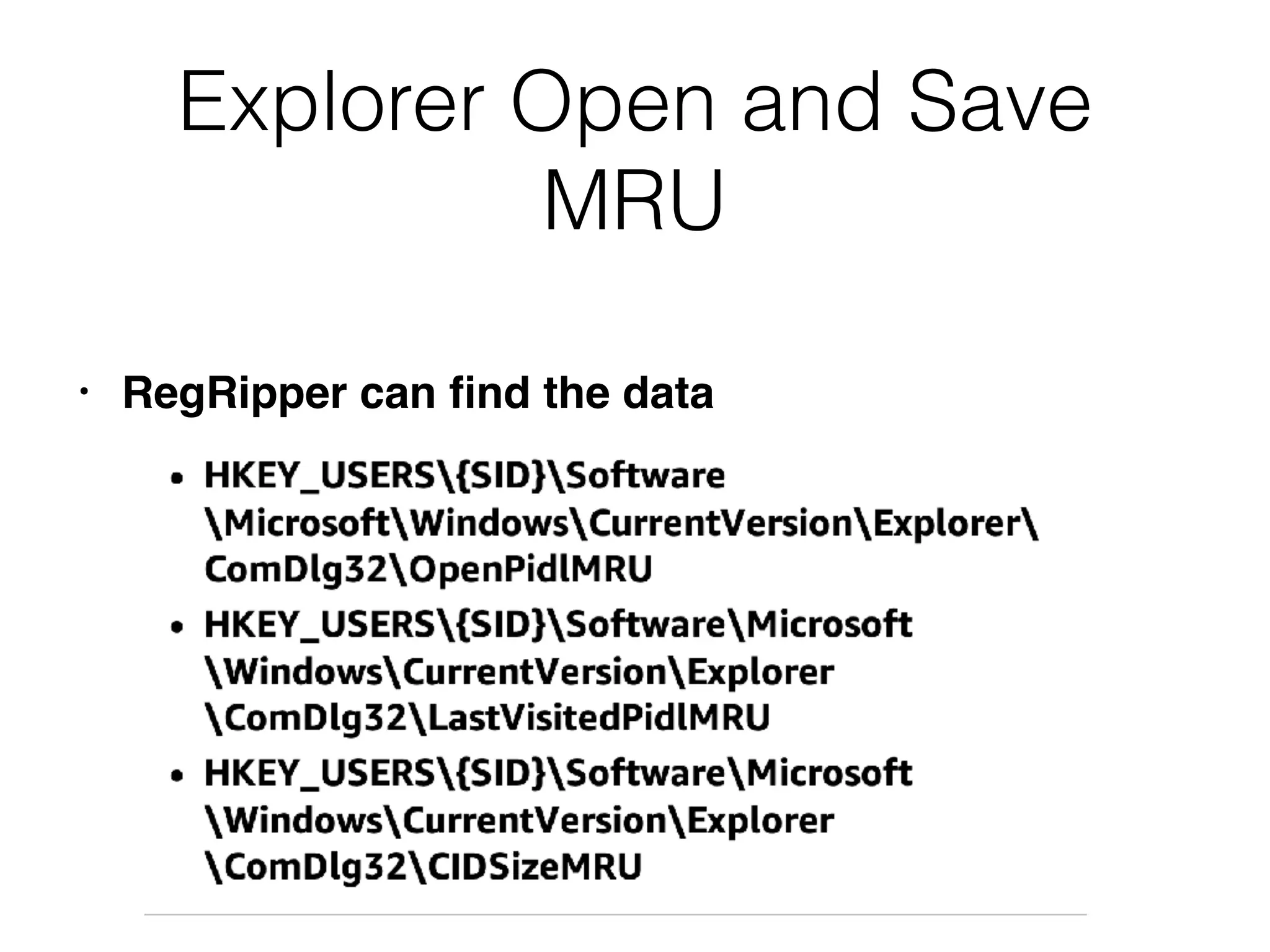
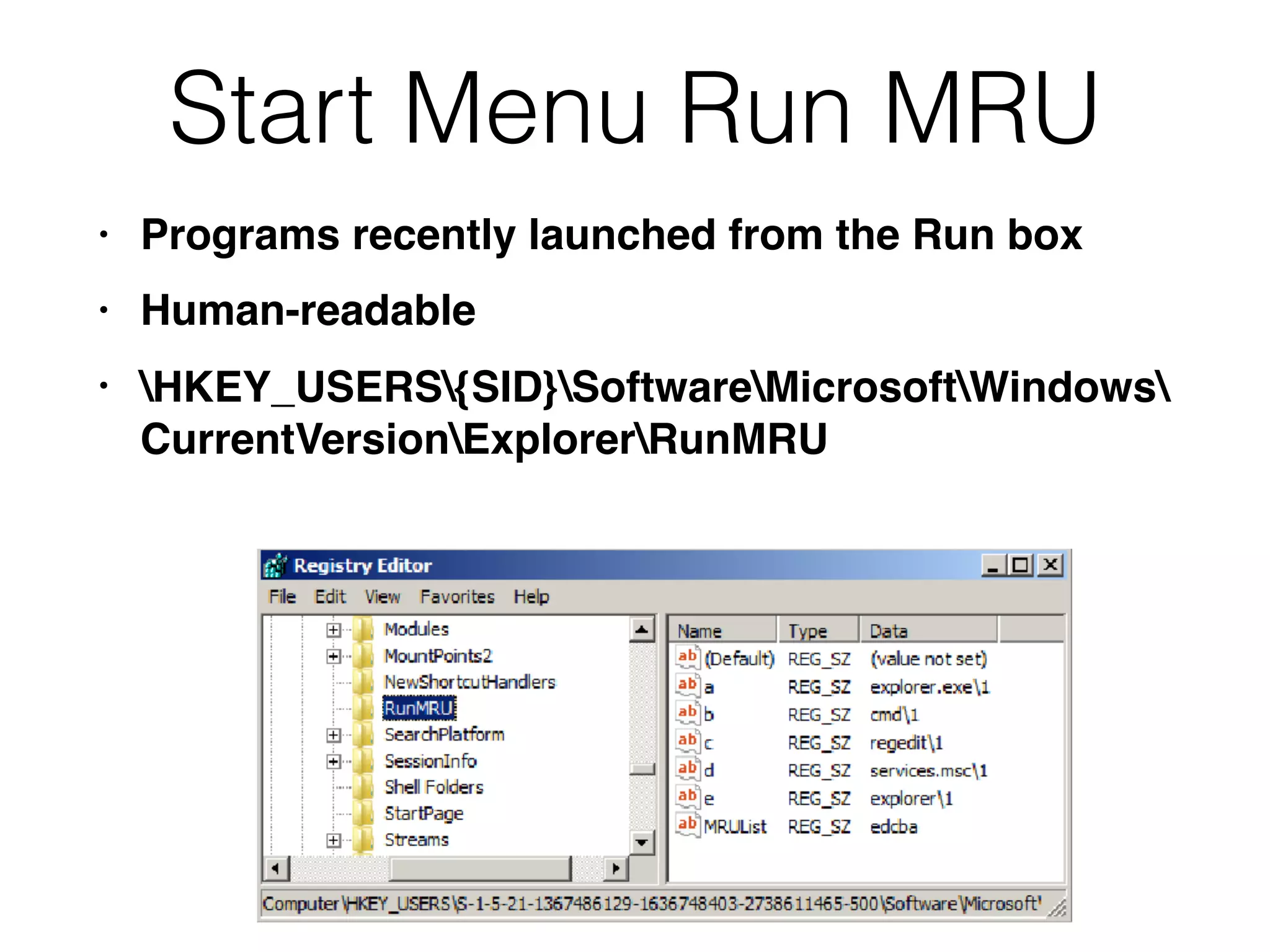
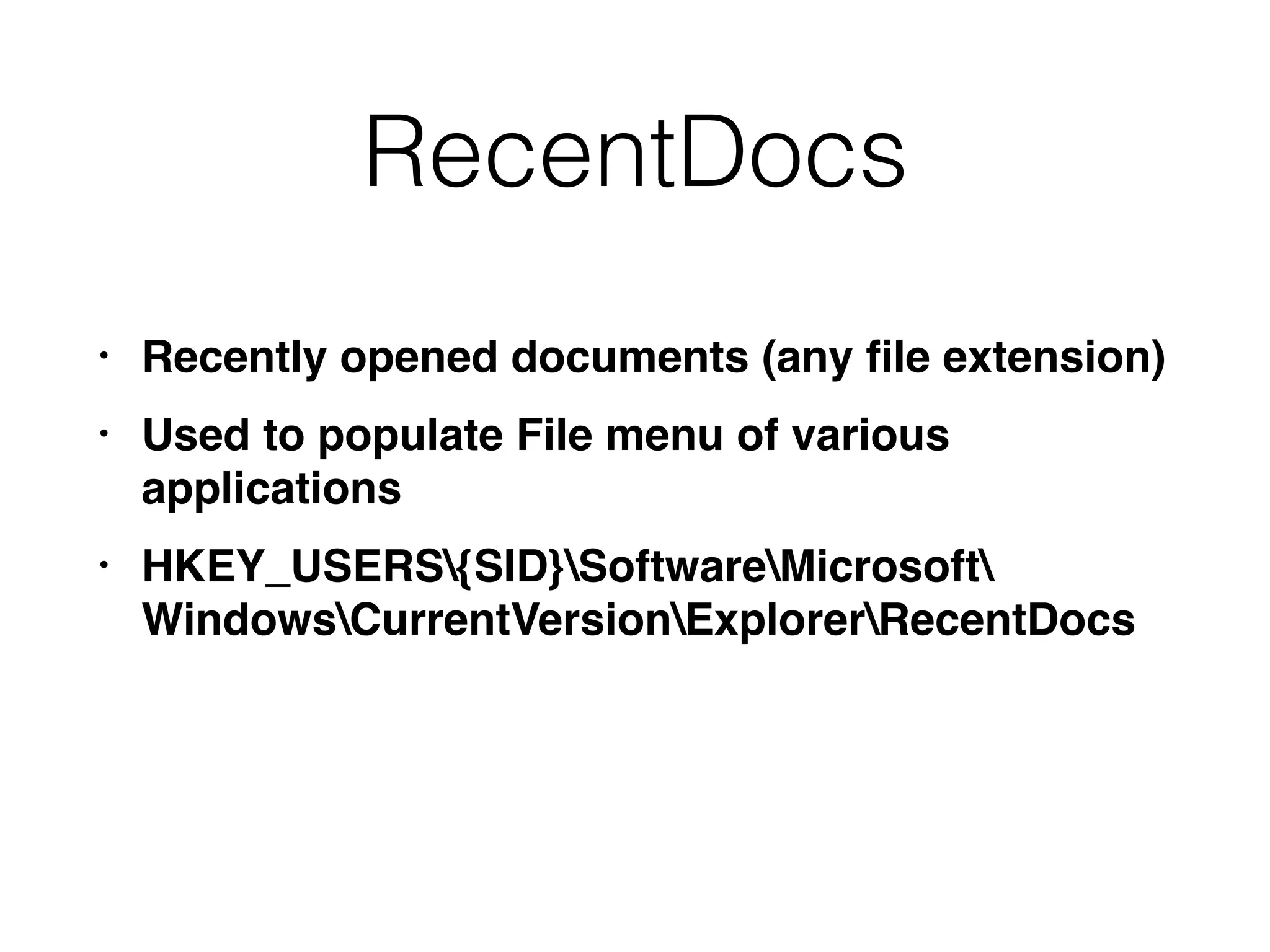
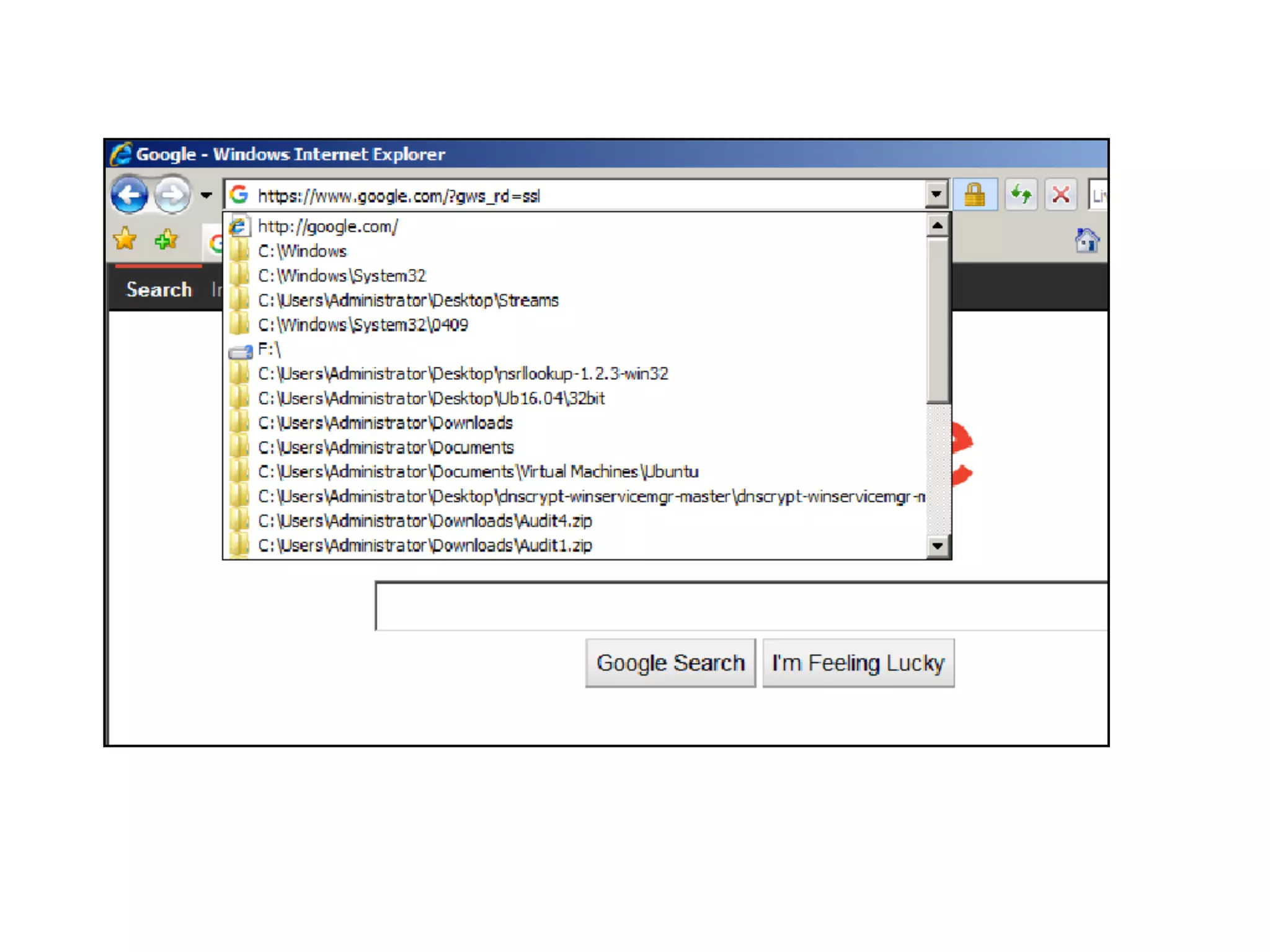
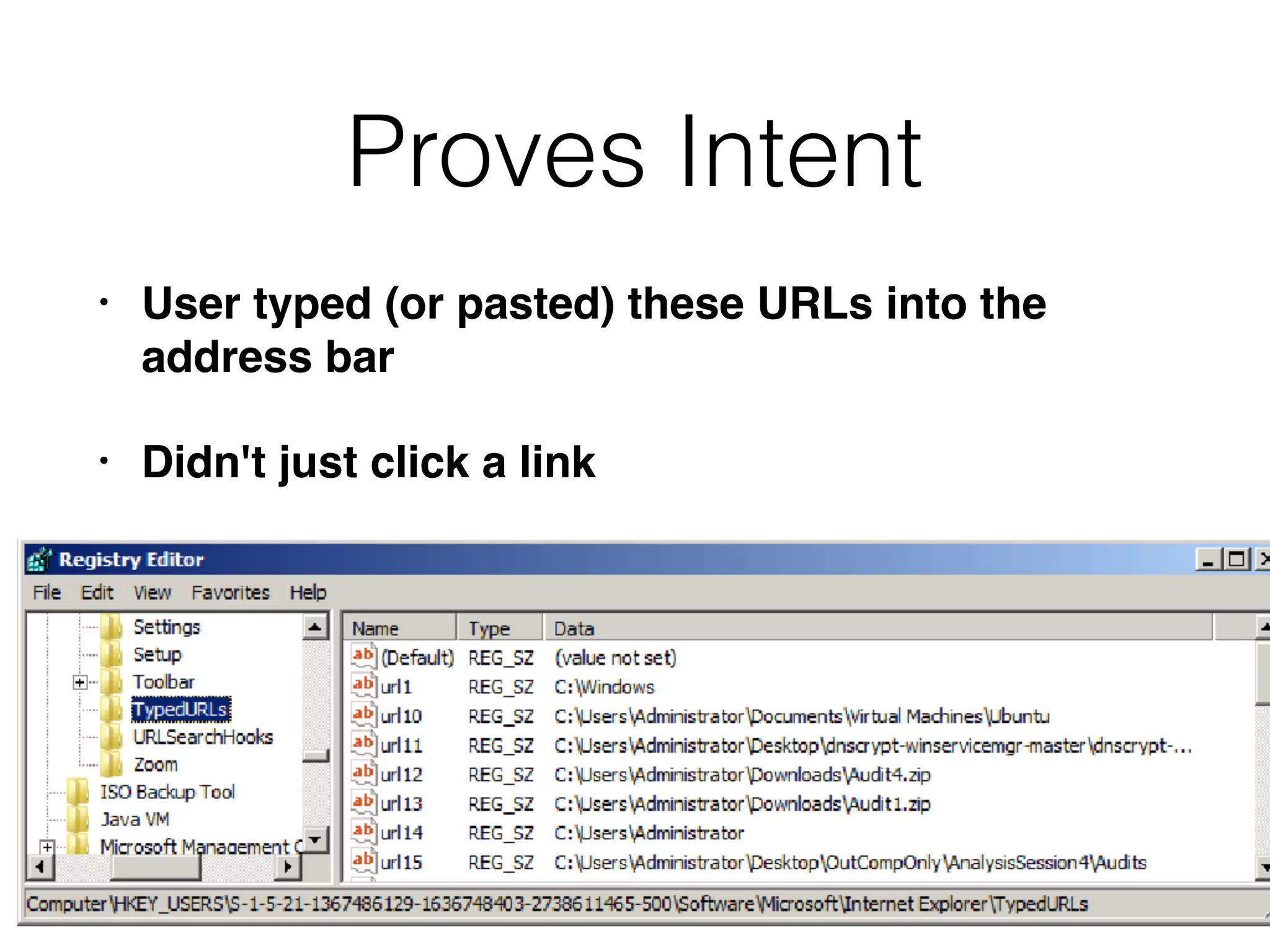
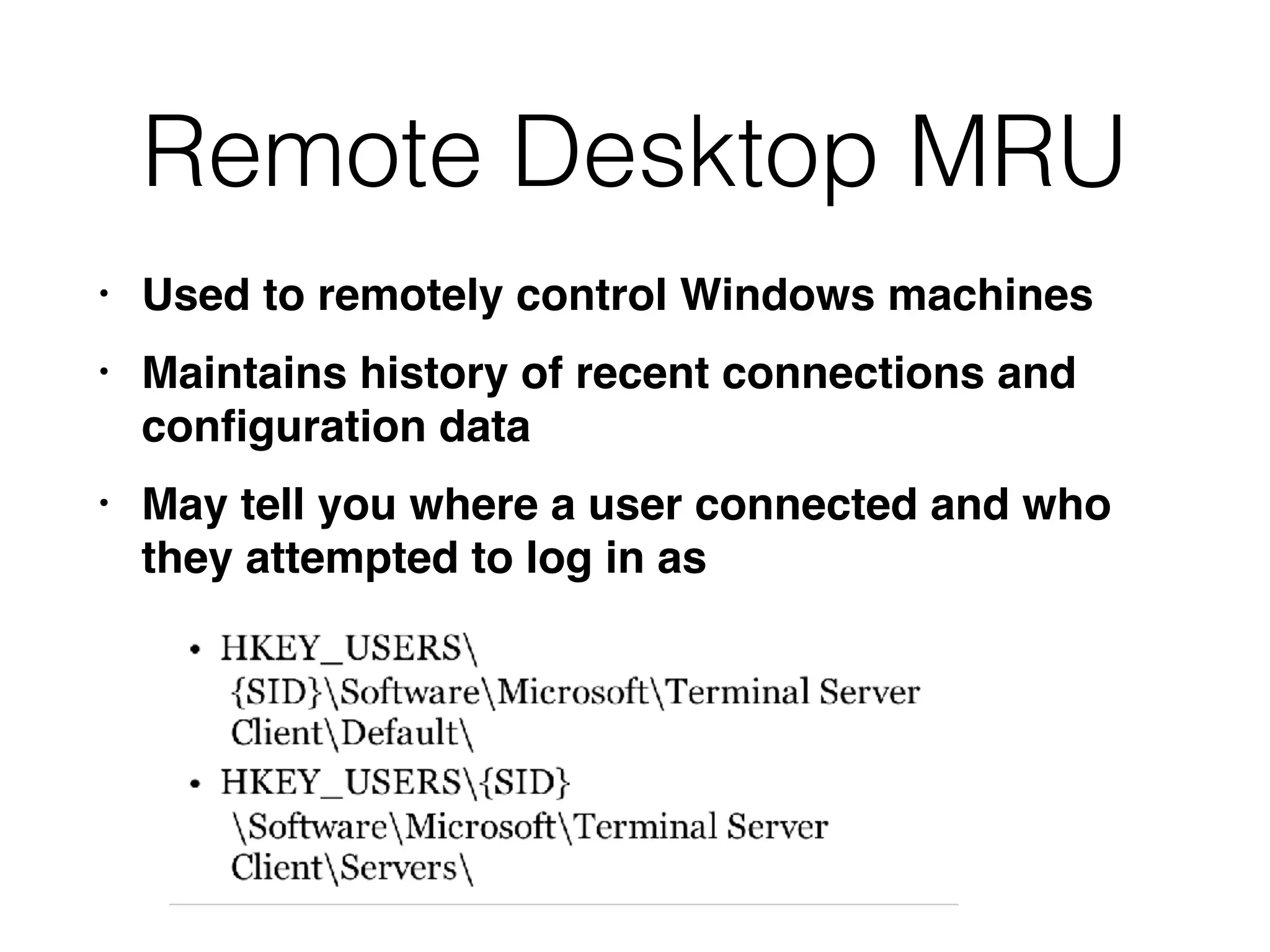
The document provides an overview of incident response for investigating Windows systems, focusing on the Windows registry, its purpose, and forensic value. It discusses various registry hives, important keys, and artifacts, including user profiles and registry timestamps that can be crucial in forensic analysis. Additionally, it outlines common auto-run registry keys utilized by malware, user-specific registry keys, and tools for registry analysis to identify malicious activity.