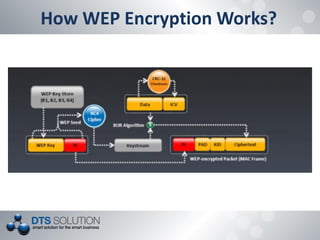
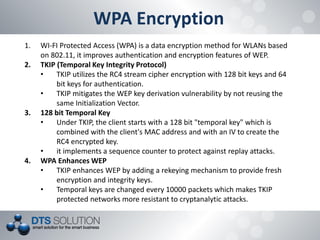
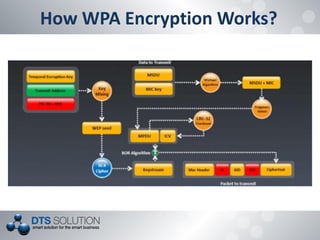
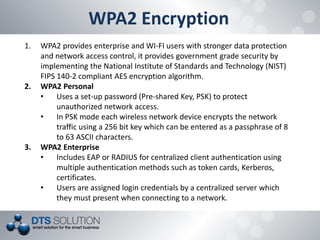
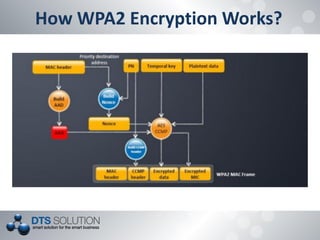
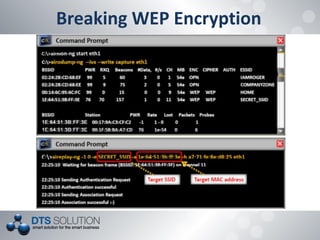
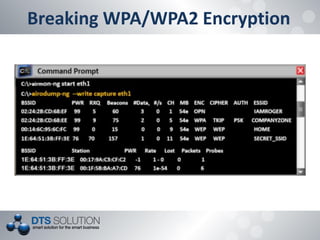
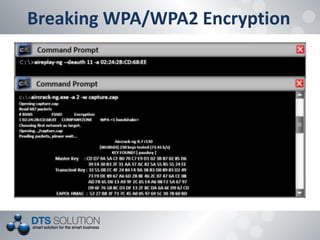
The document discusses the vulnerabilities and security protocols of wireless networks, focusing on Wi-Fi encryption methods such as WEP, WPA, and WPA2. It highlights the design flaws of WEP and the improvements made in WPA and WPA2, emphasizing the need for stronger encryption and better key management. The author provides insights into the security issues associated with these protocols and methods to crack them, stressing the importance of vigilant network security measures.