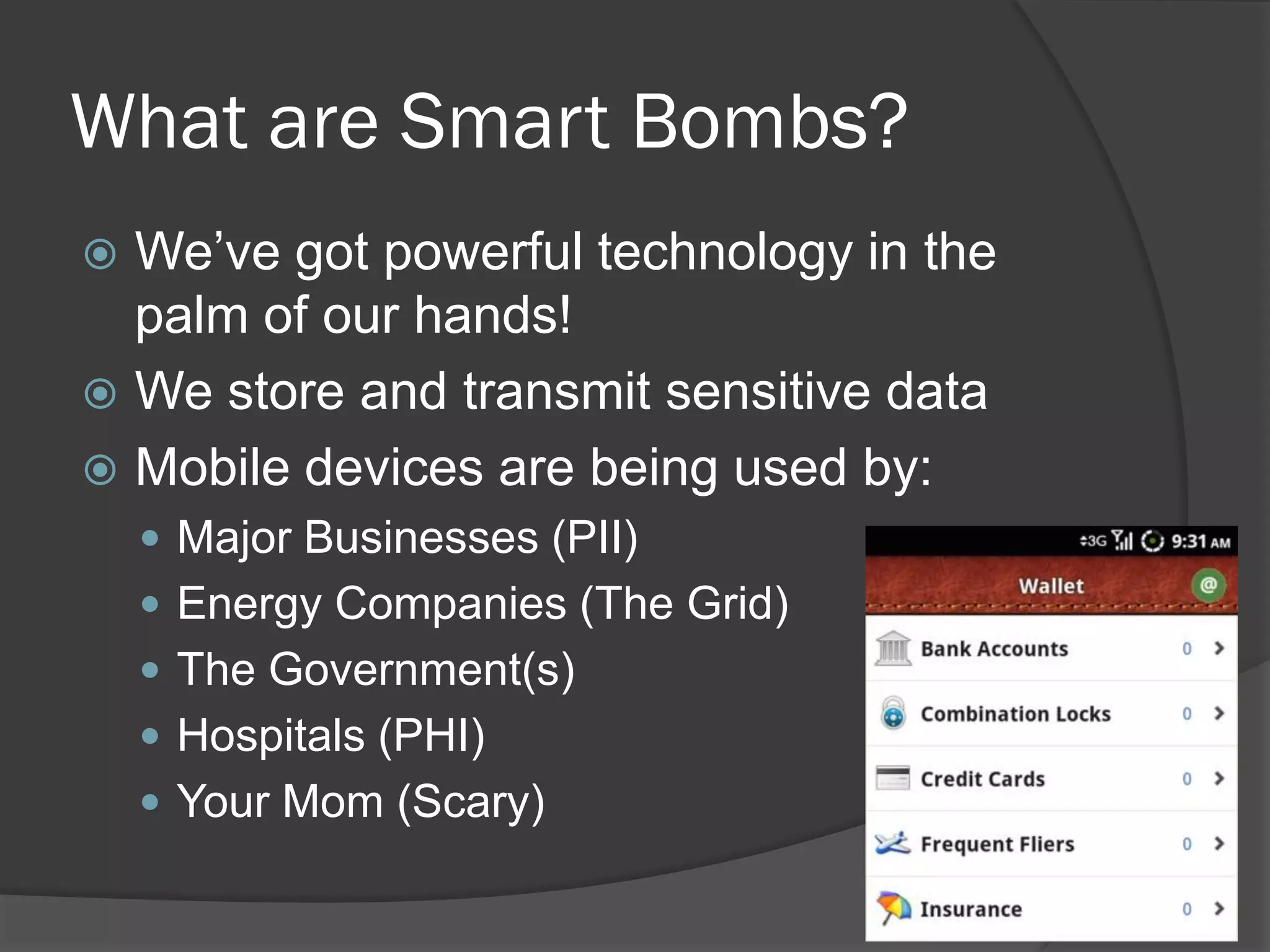
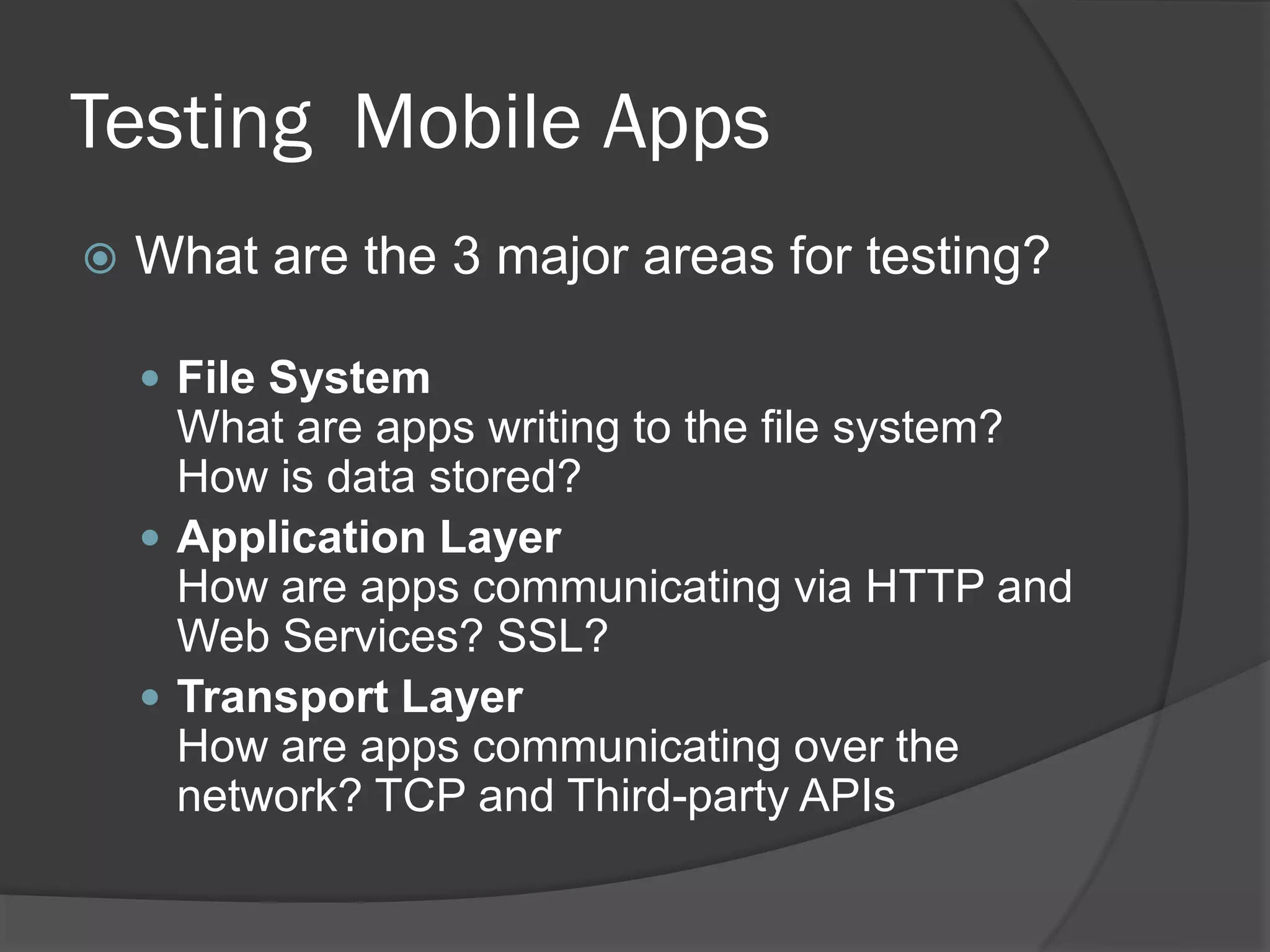
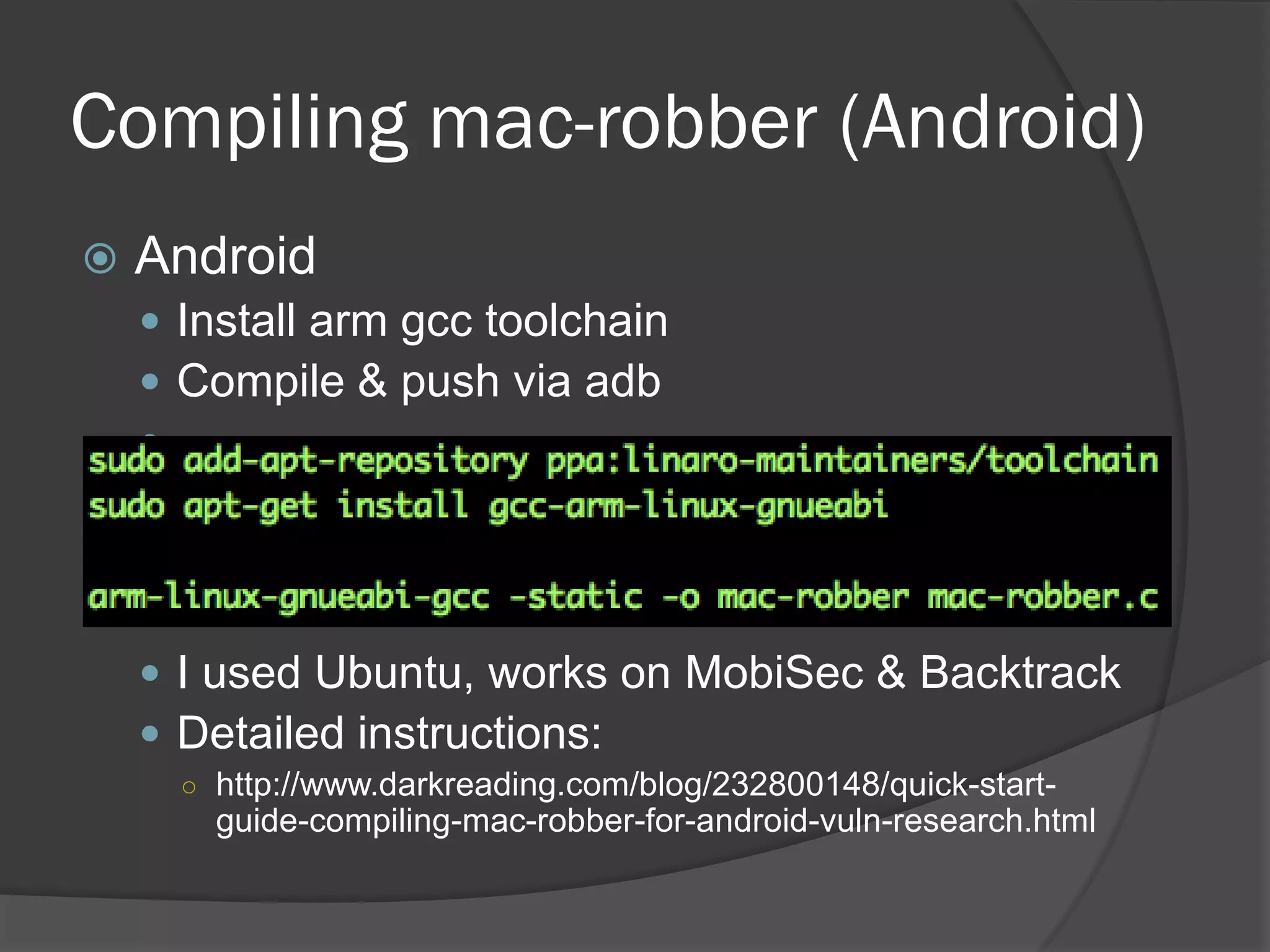
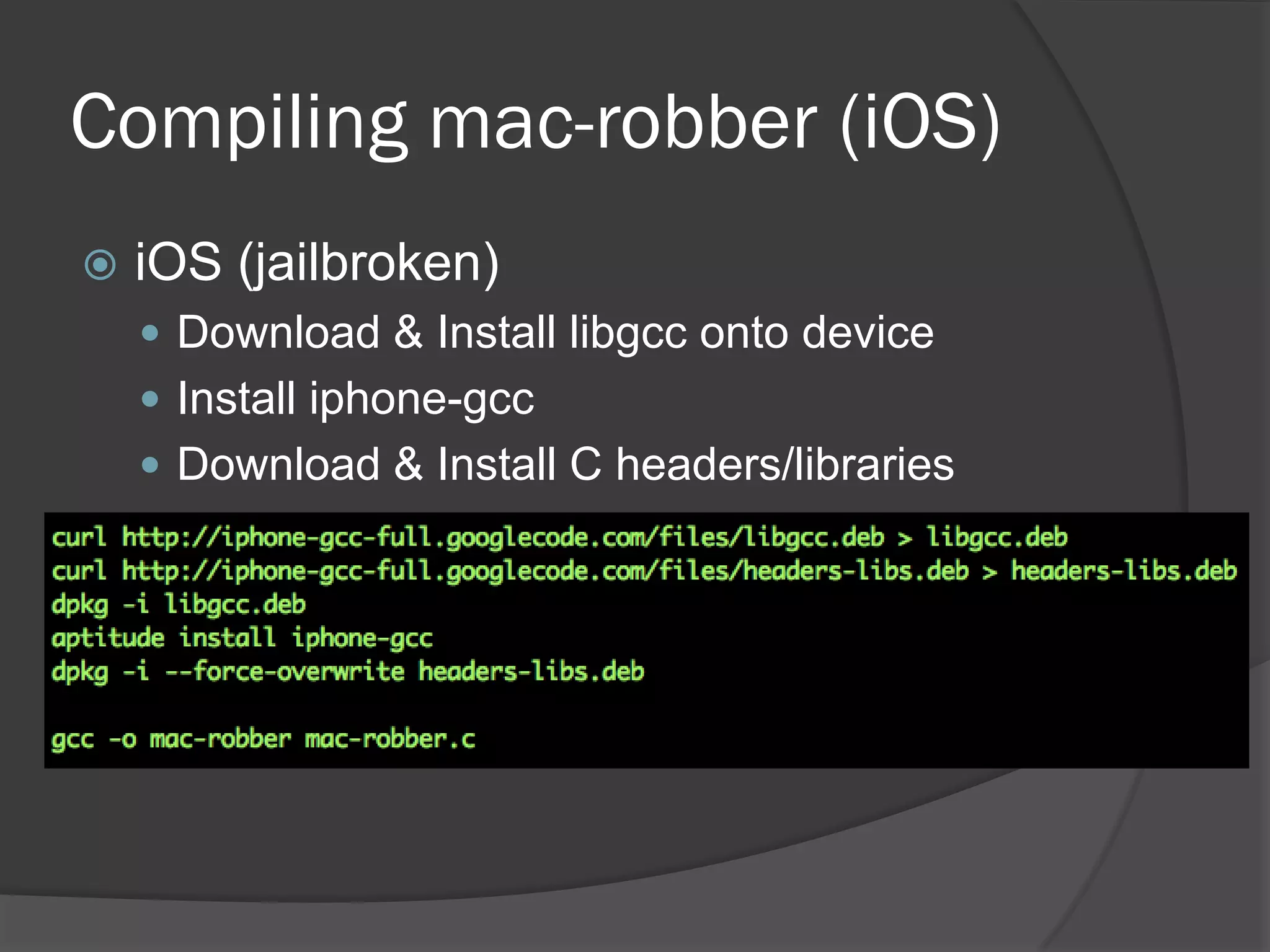
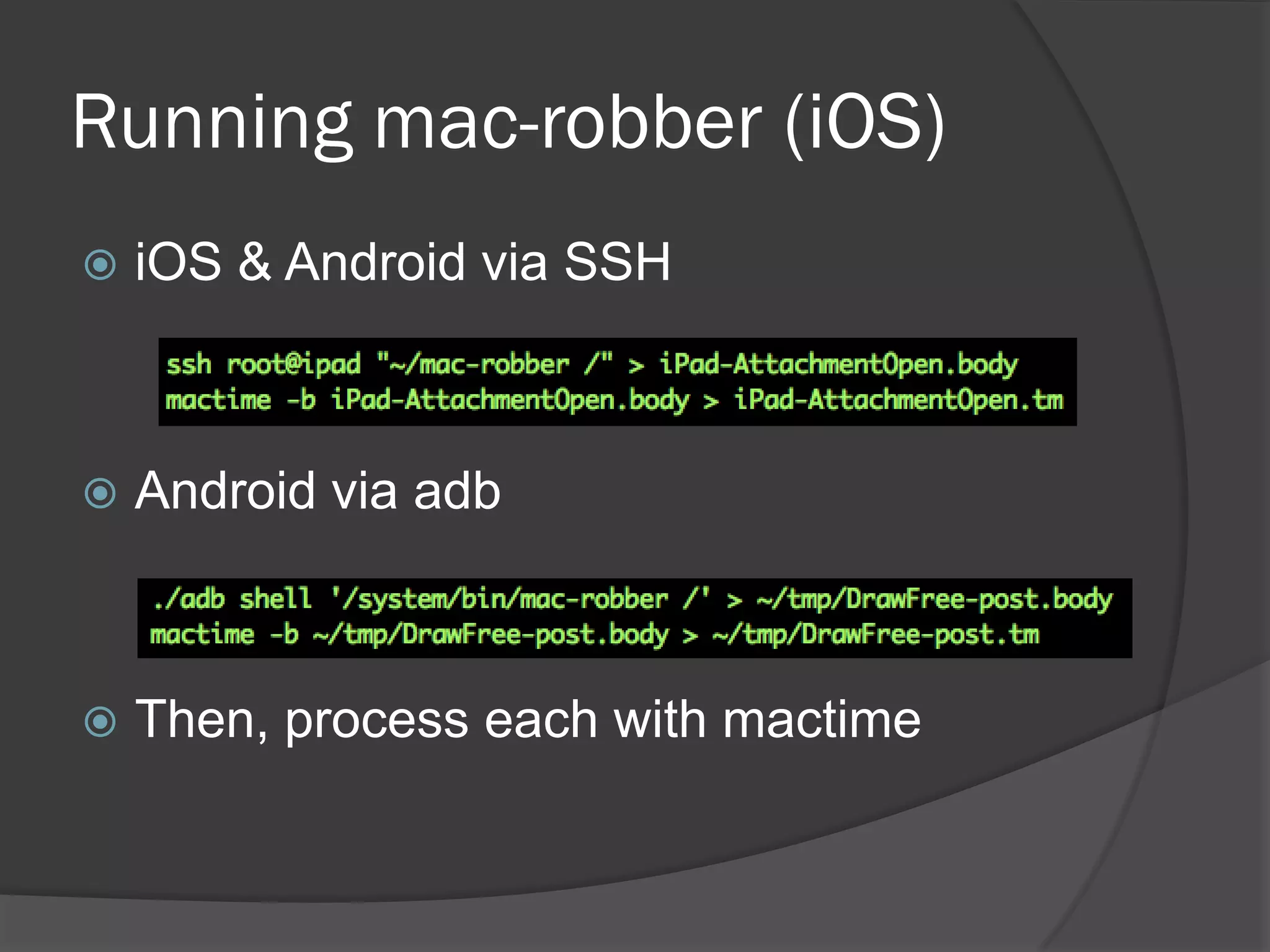
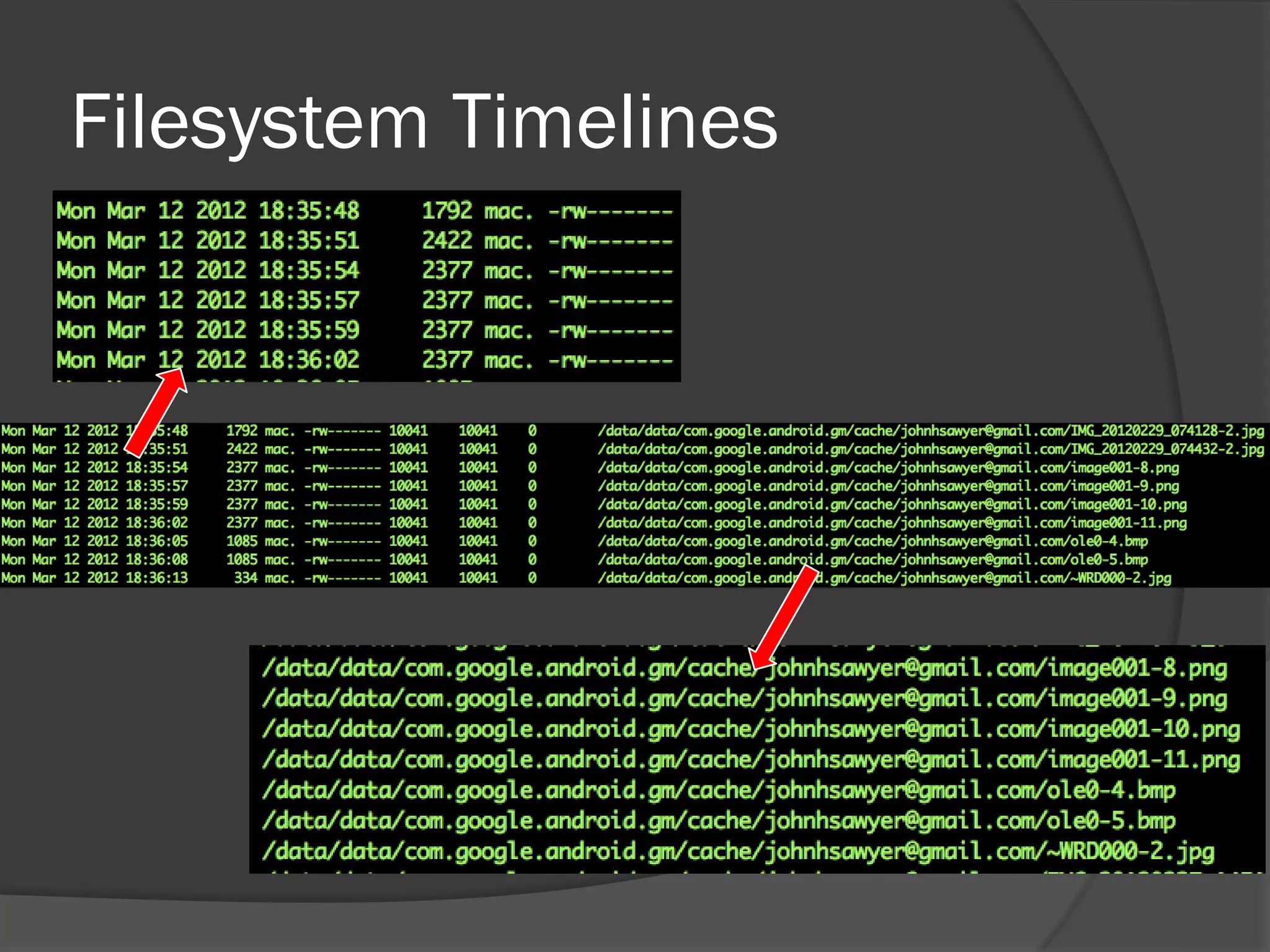
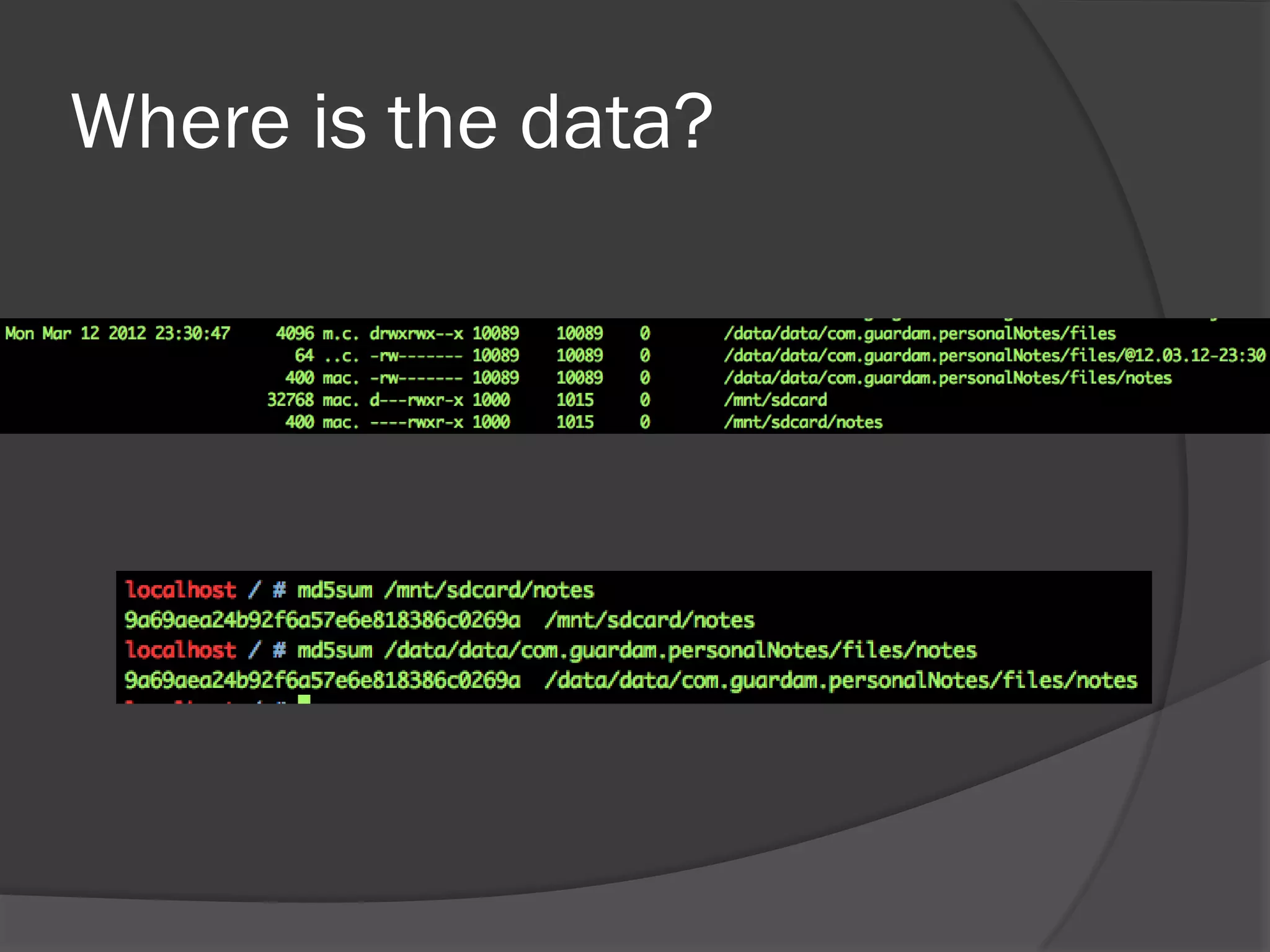
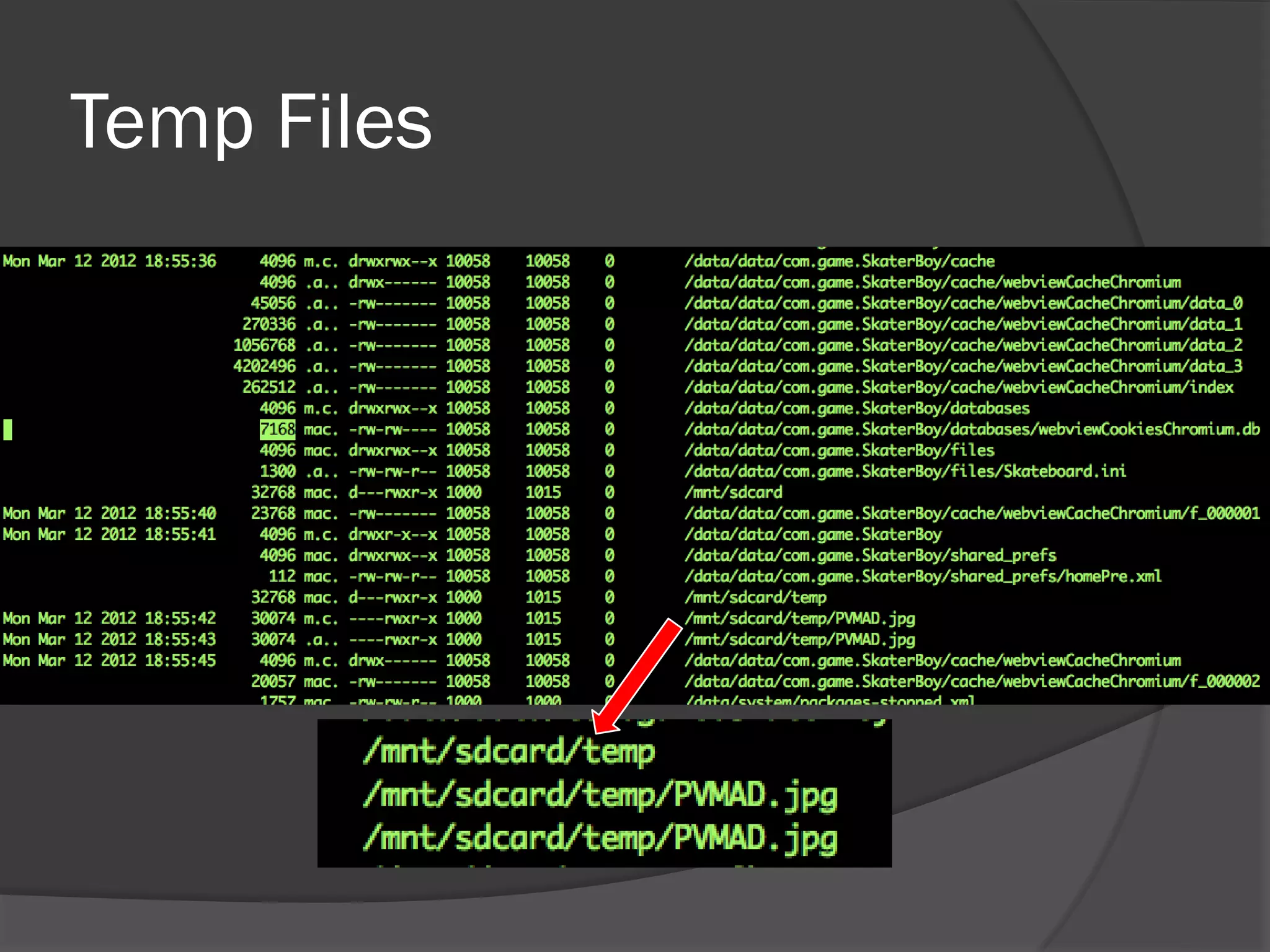
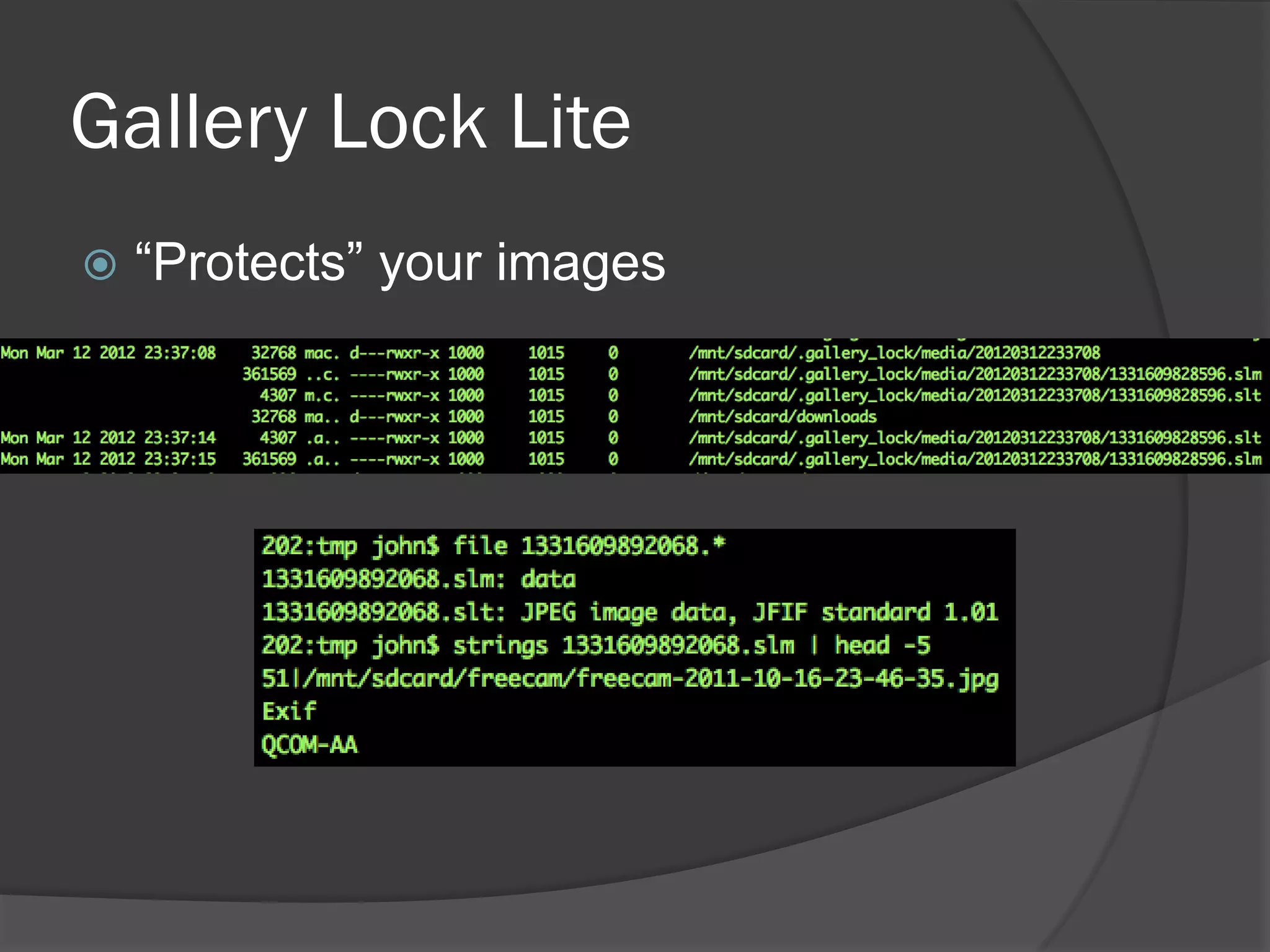
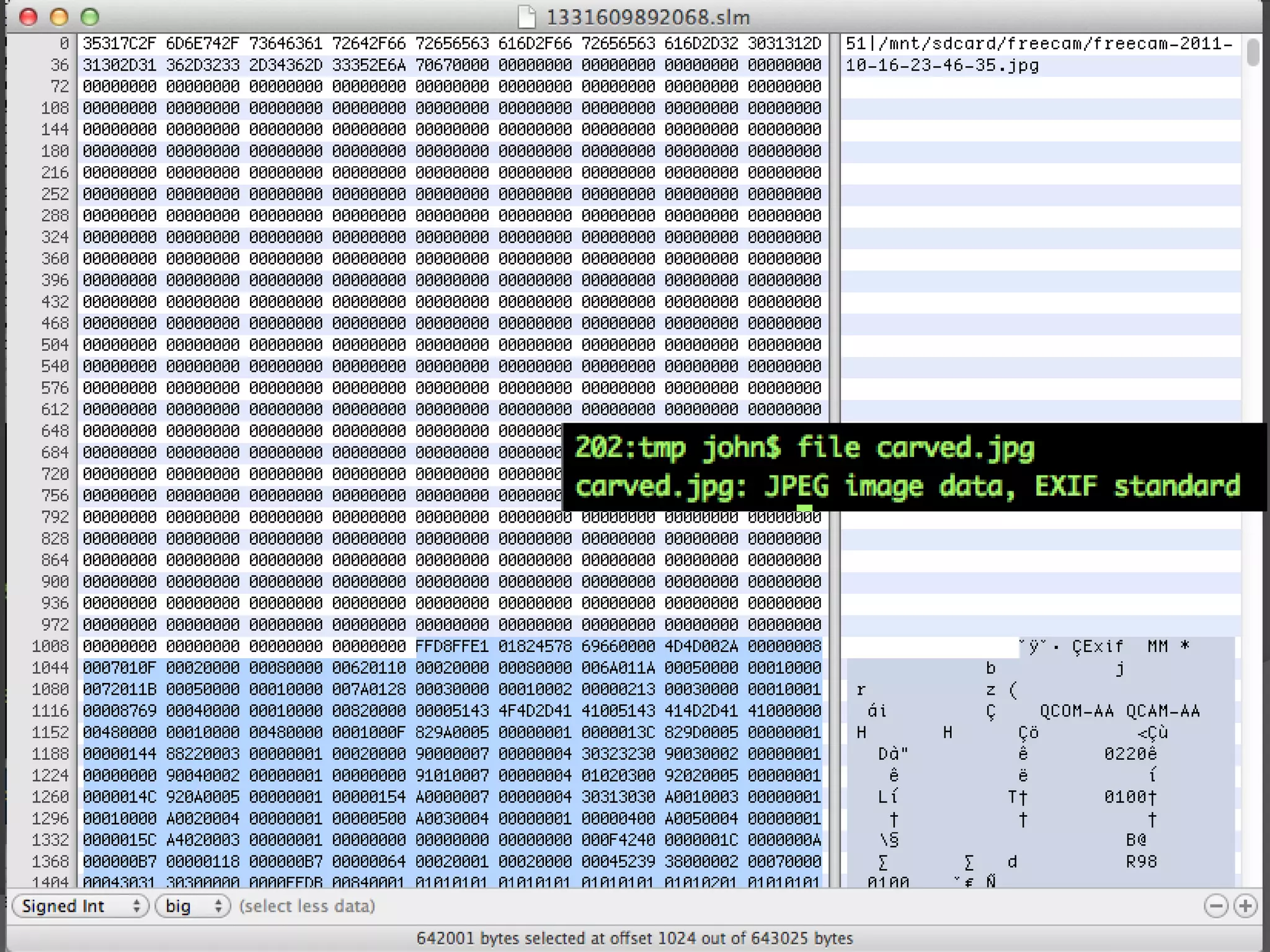
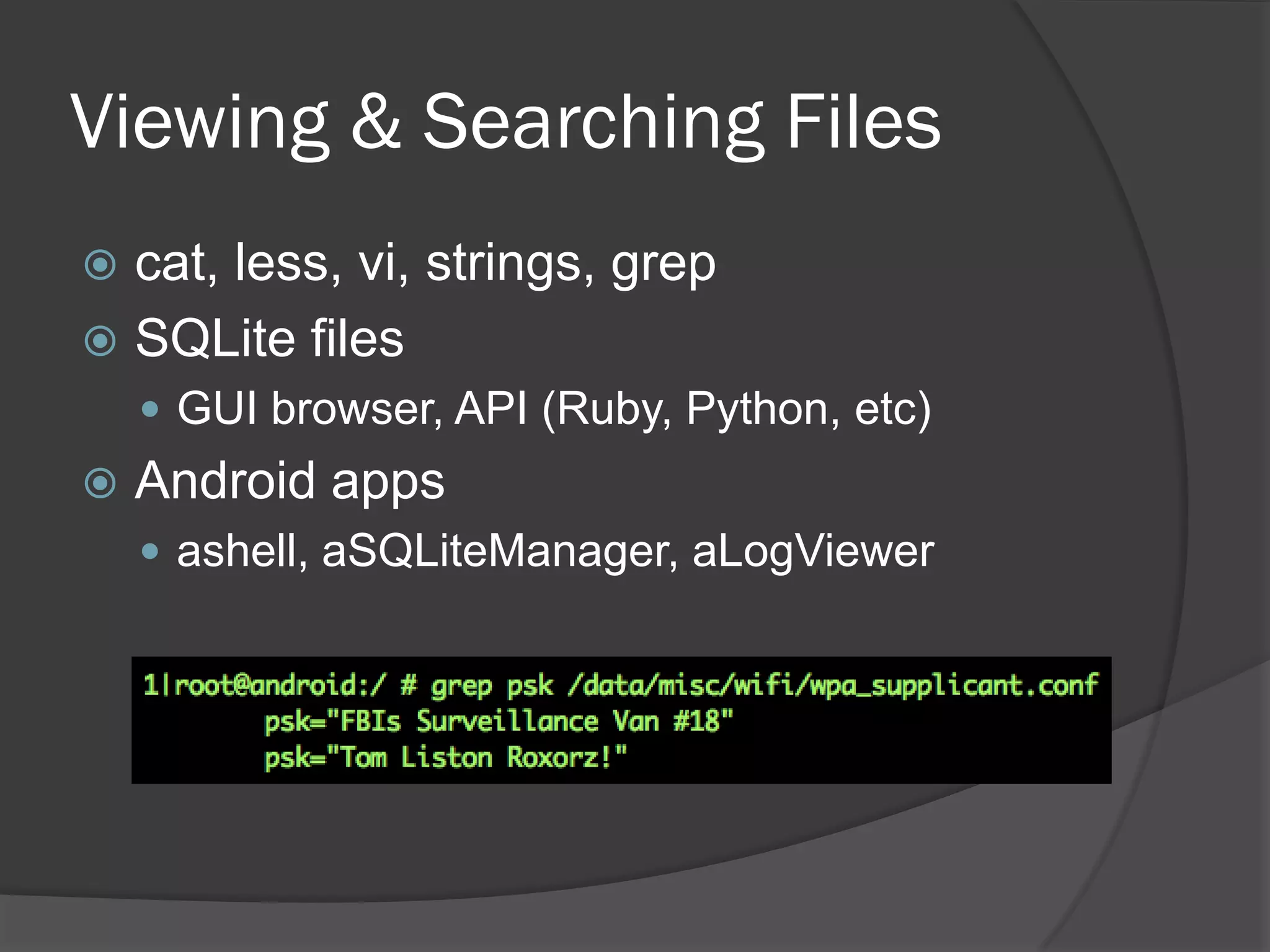
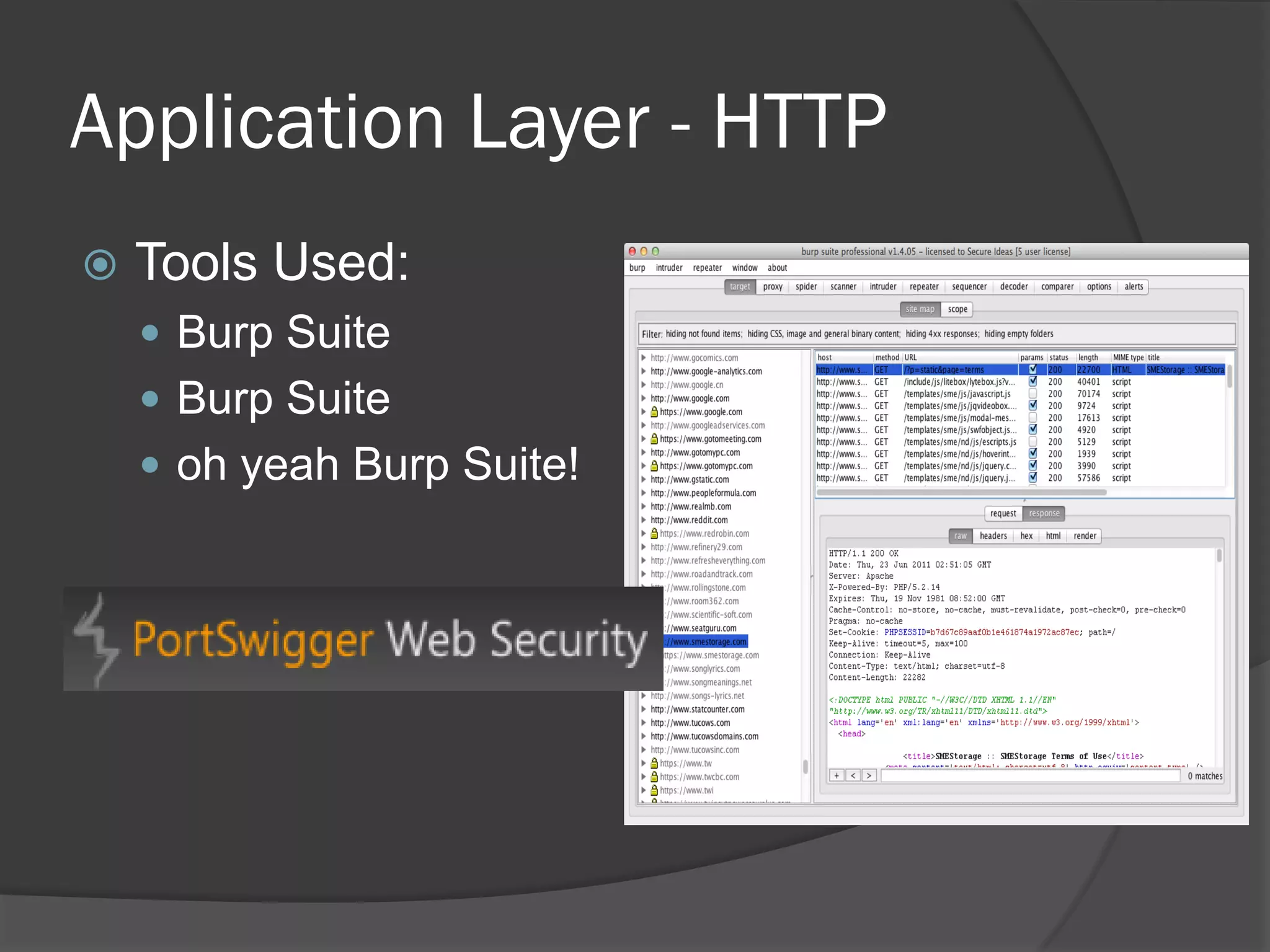
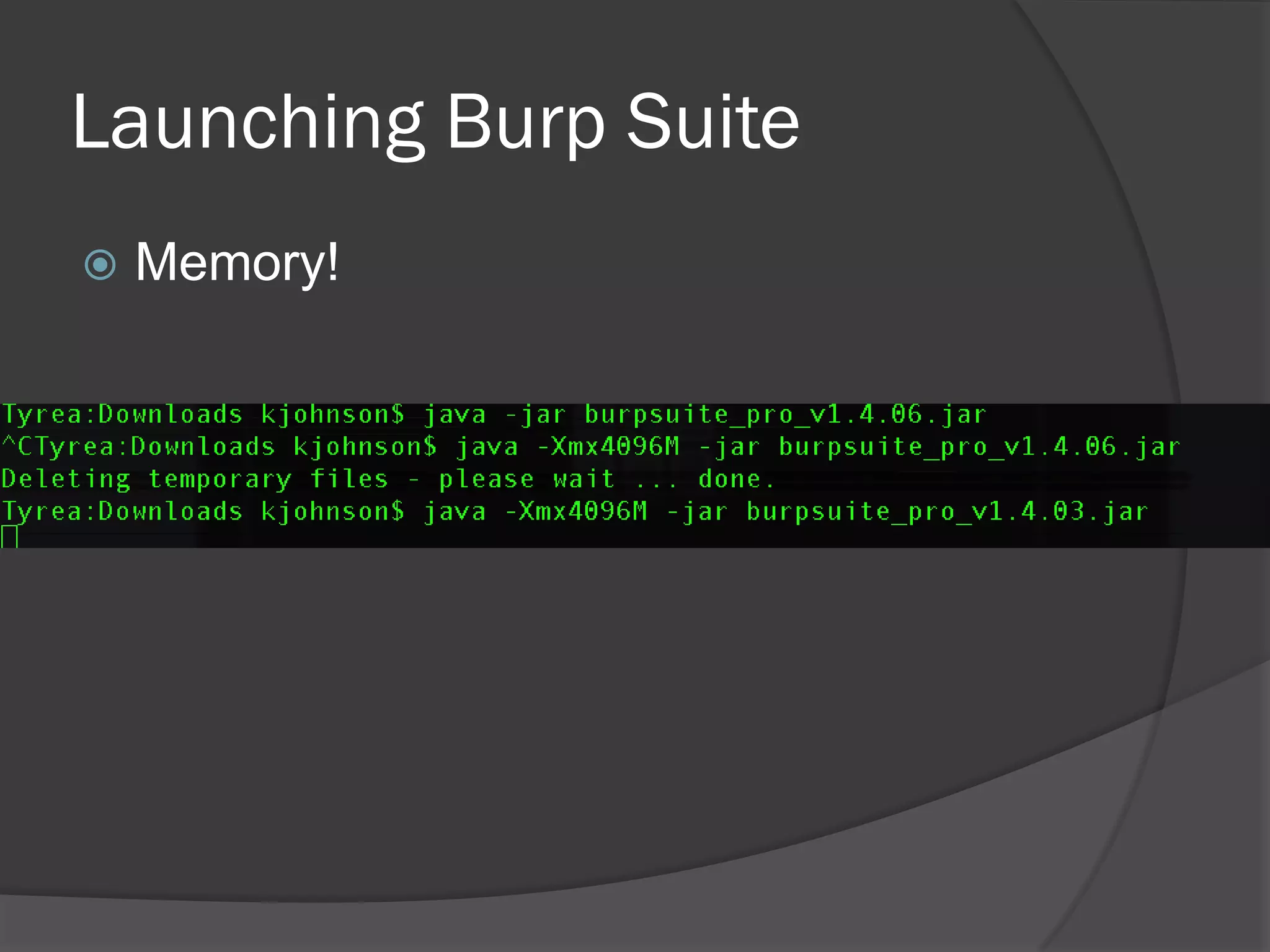
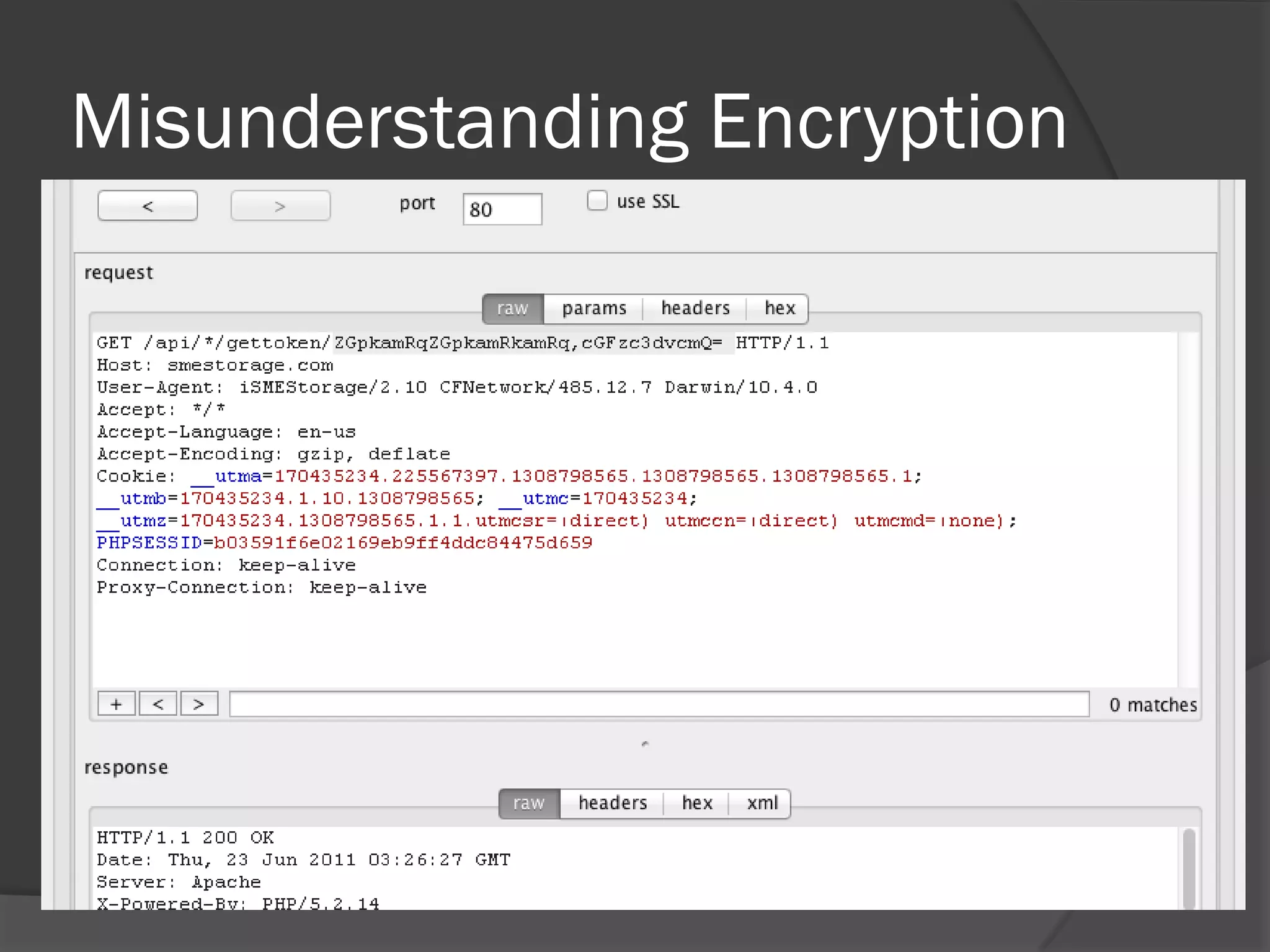
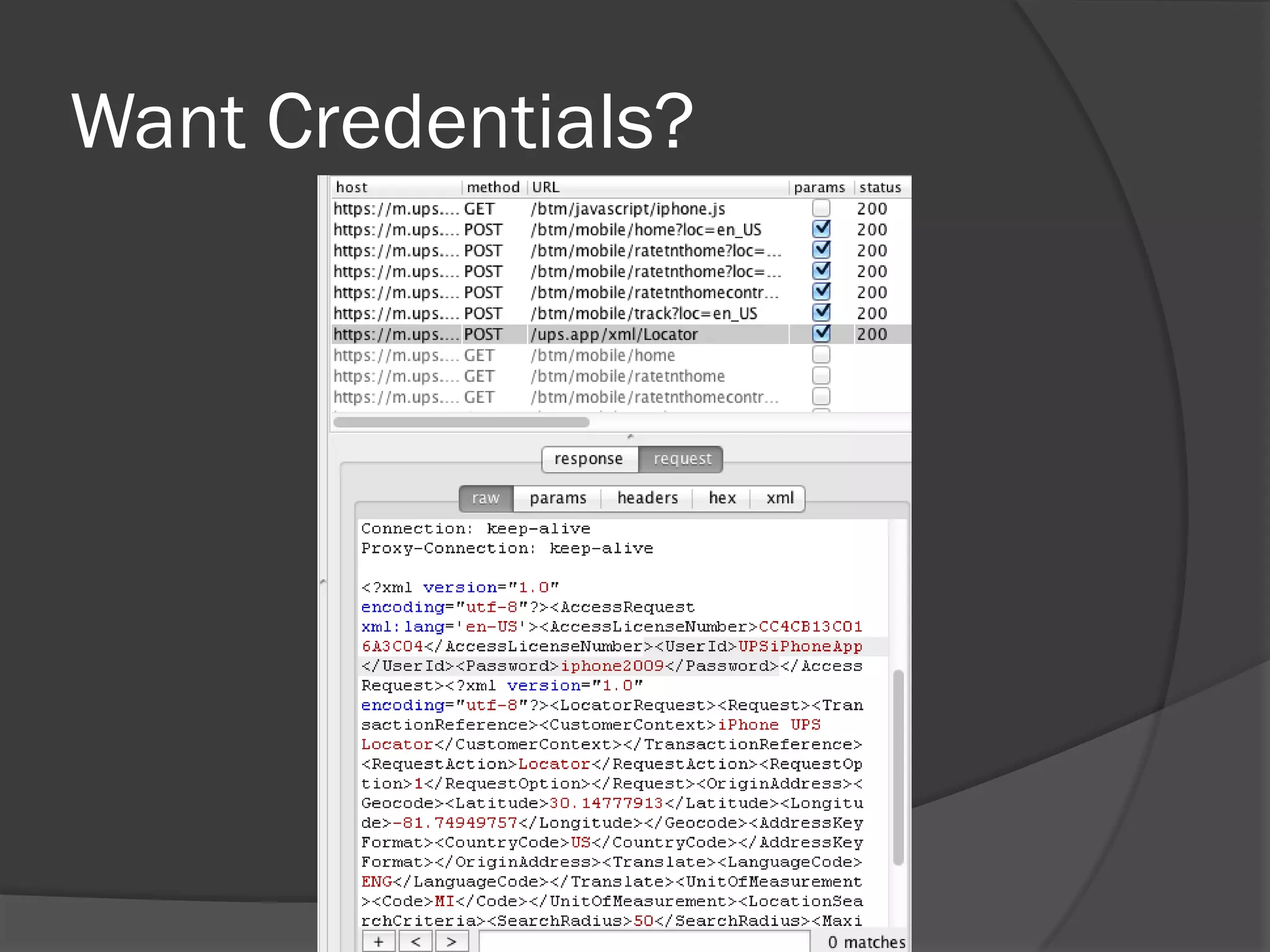
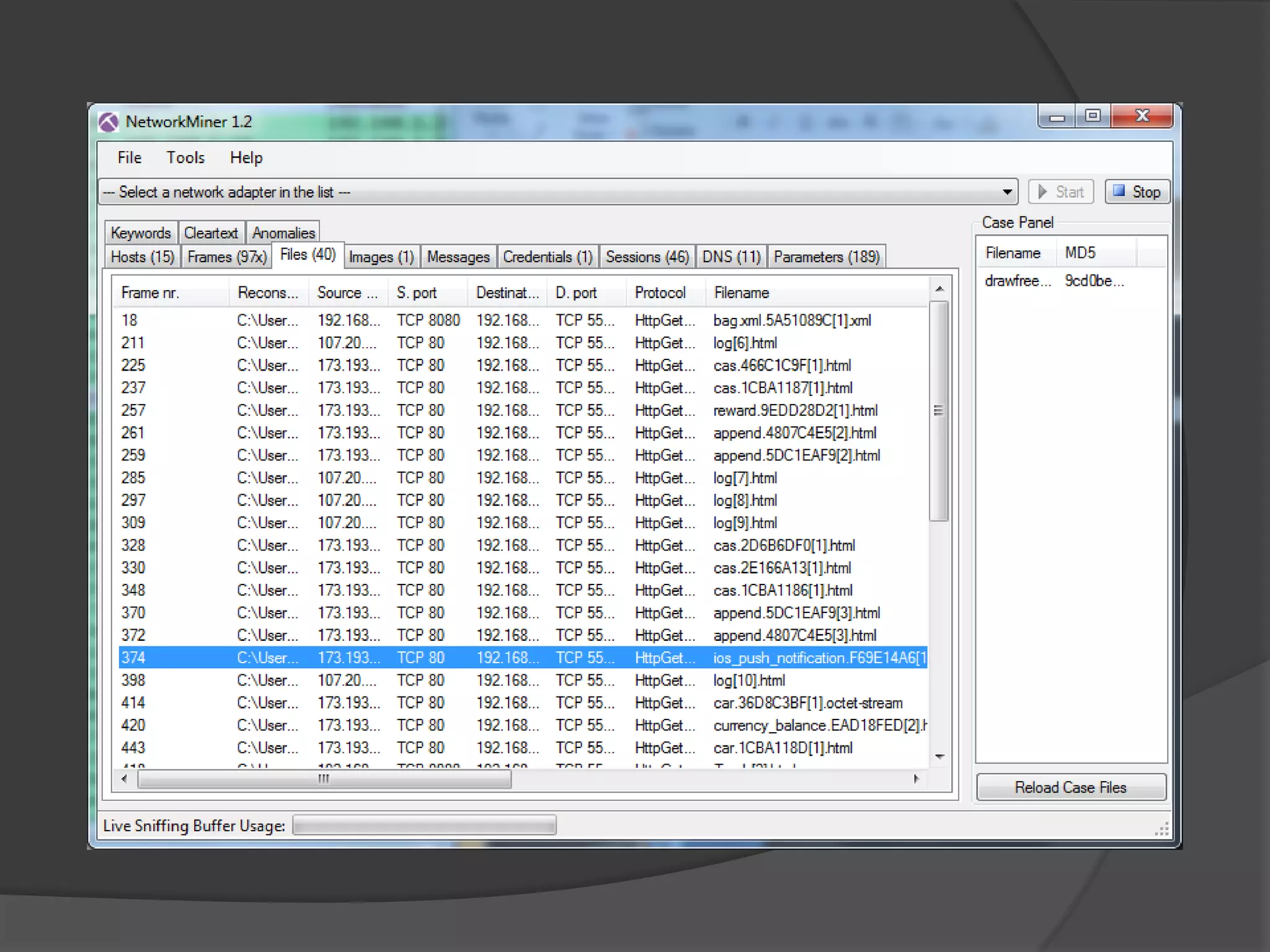
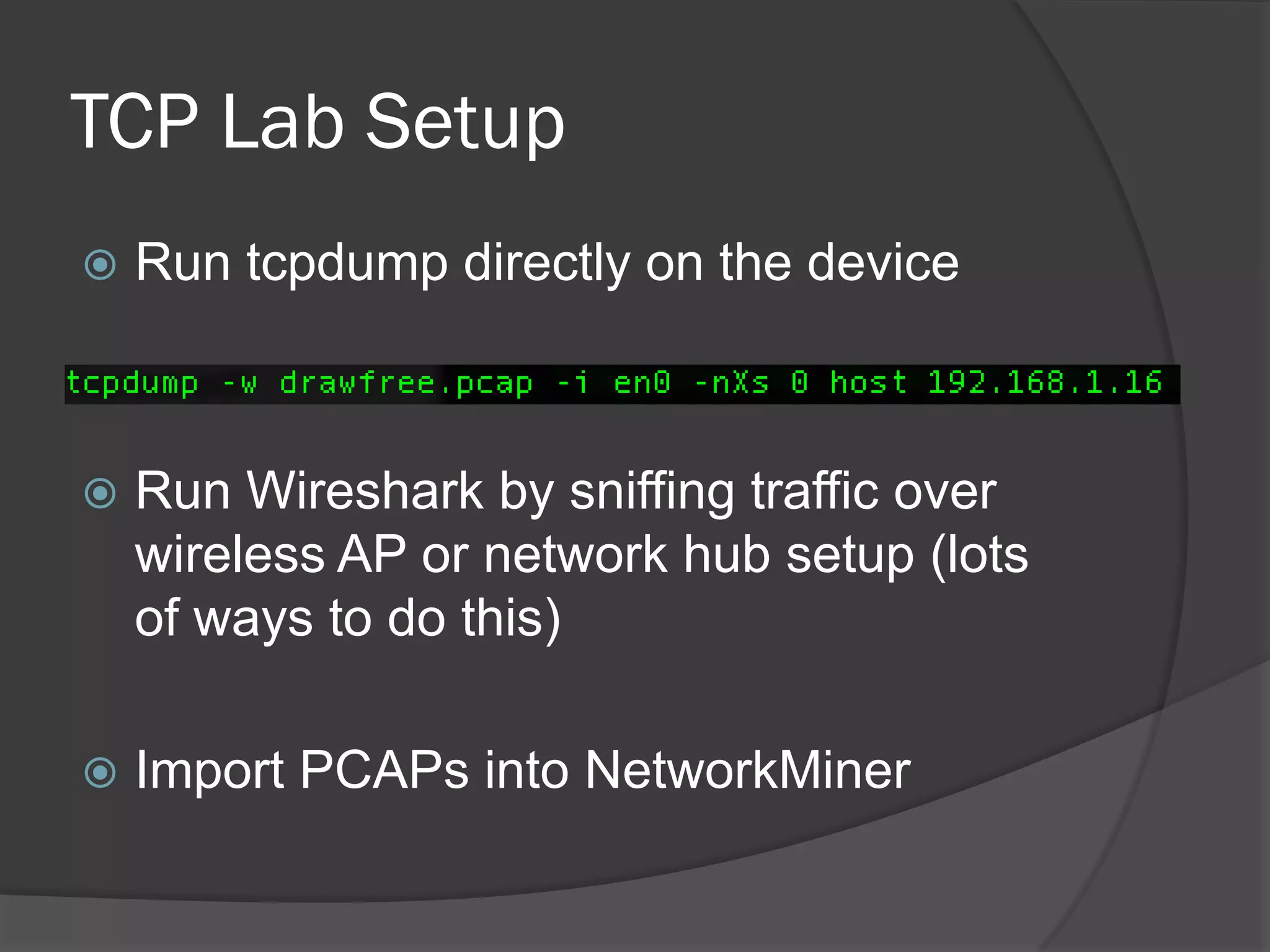
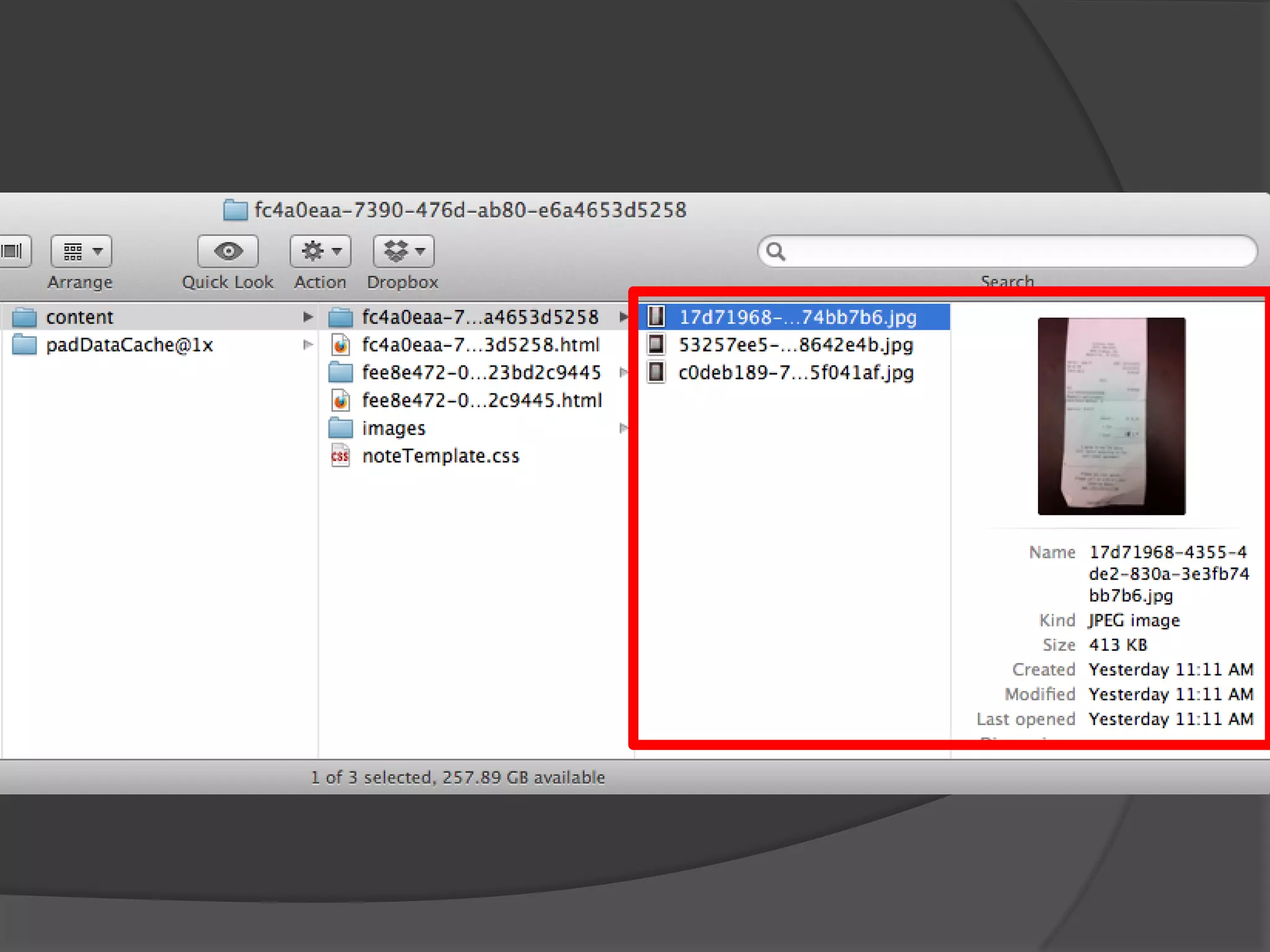
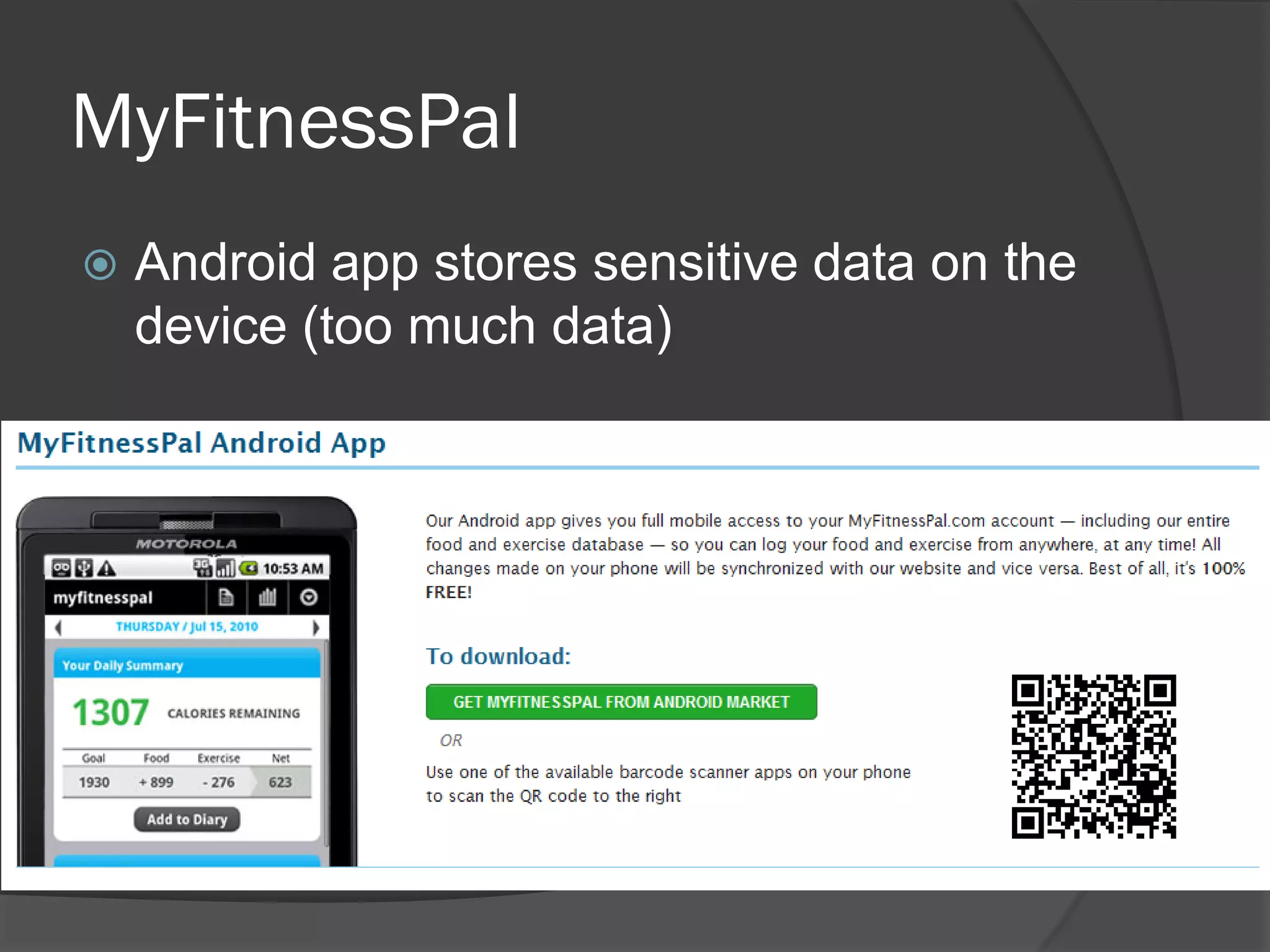
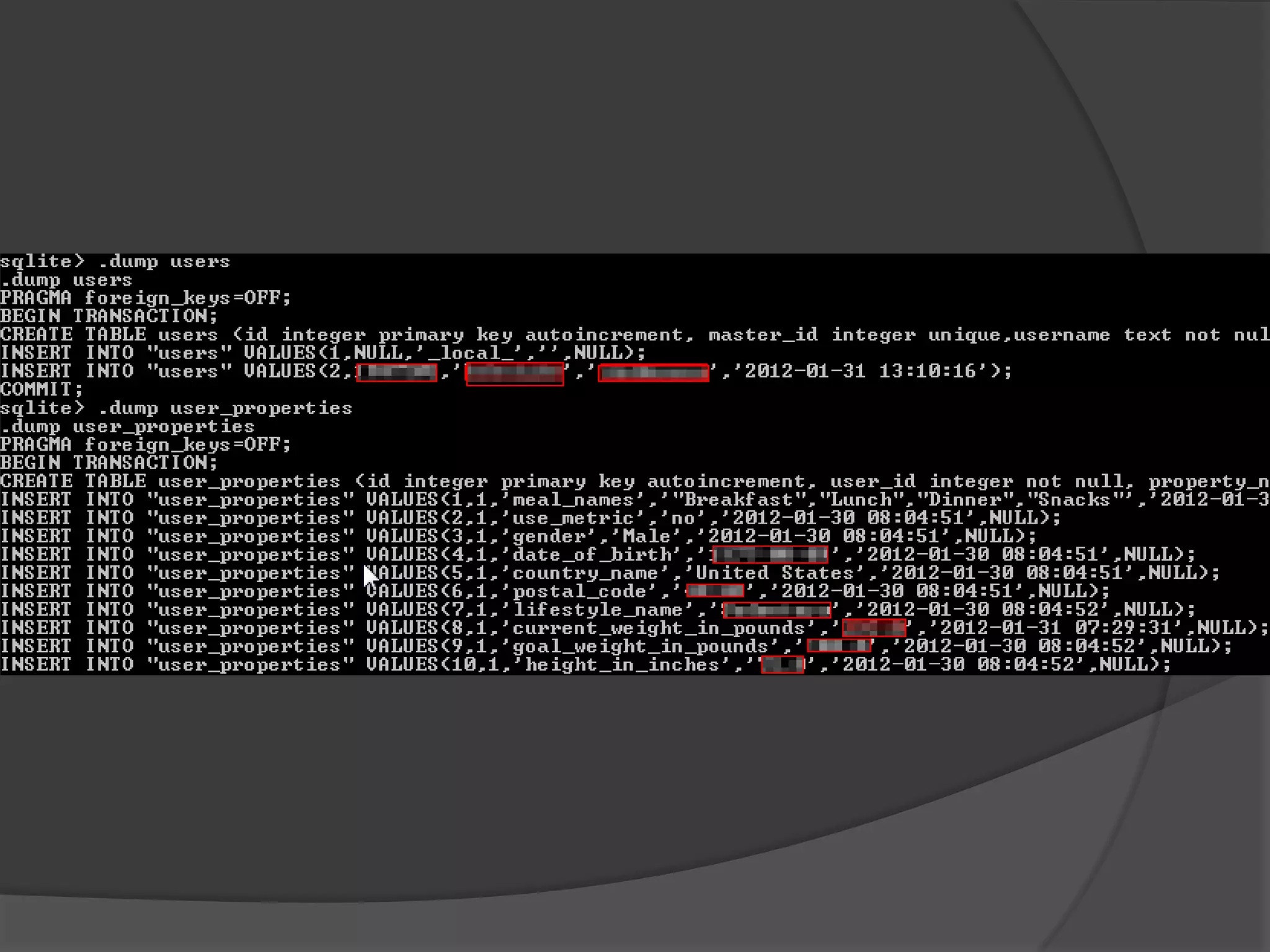
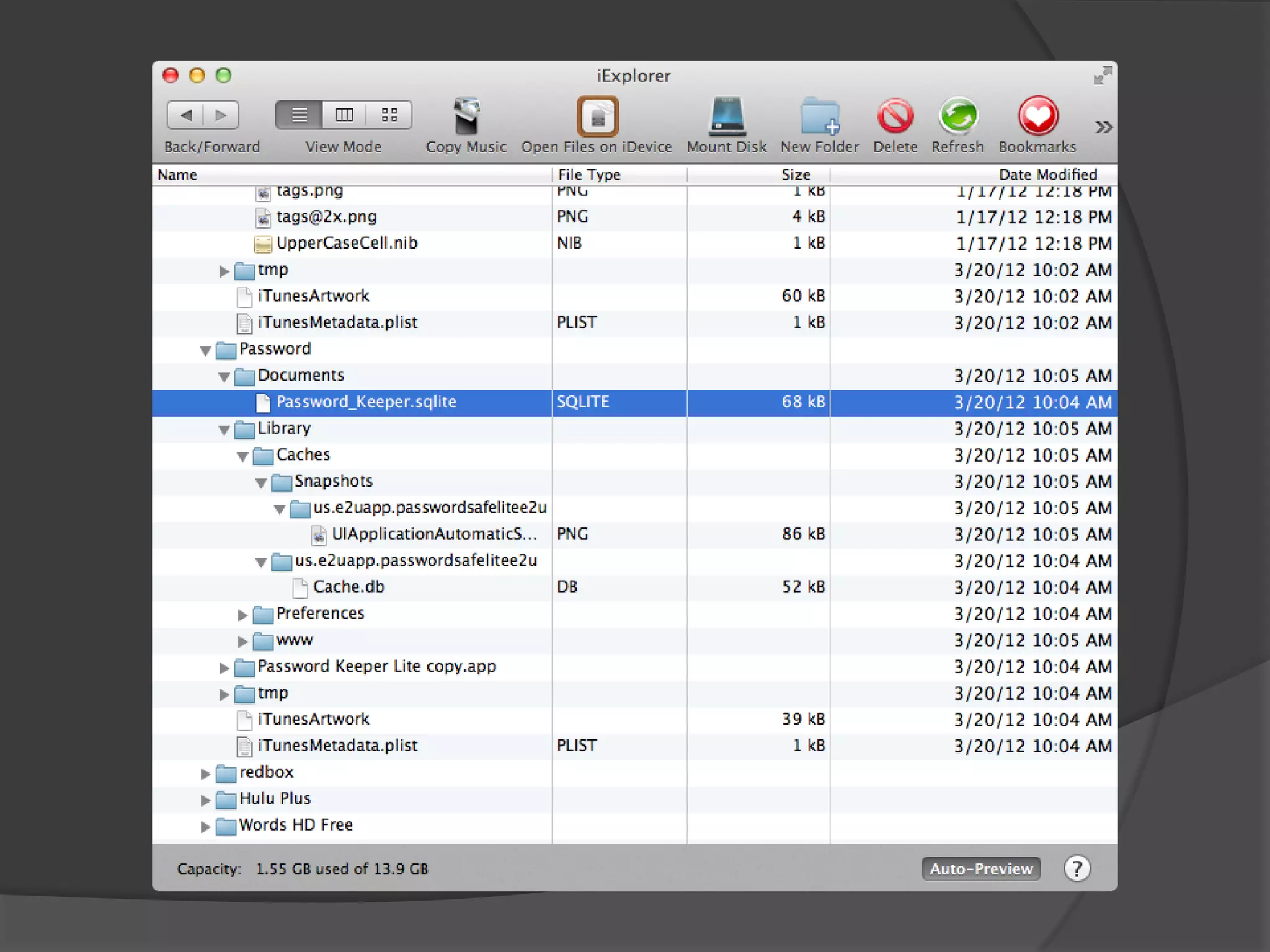
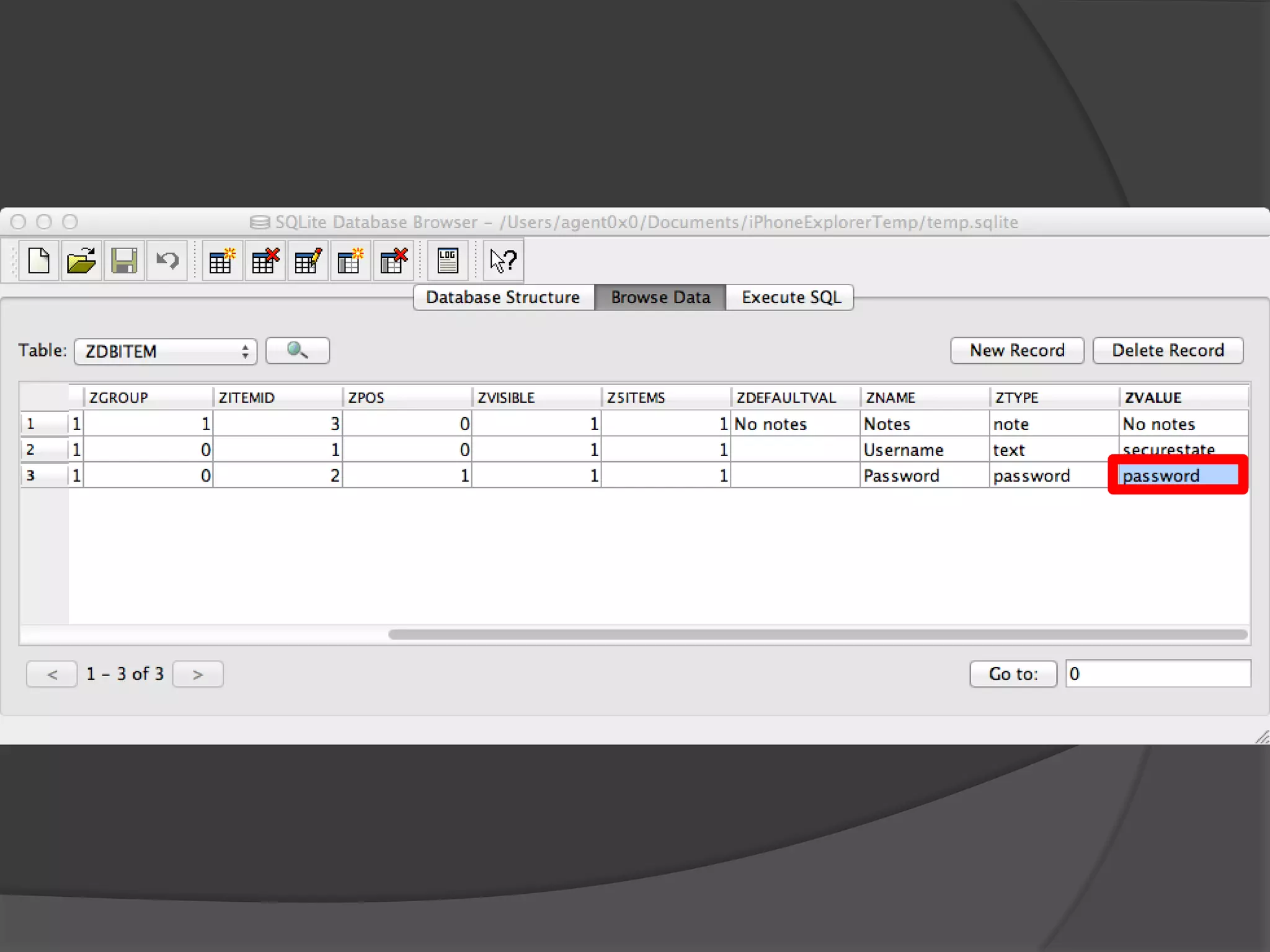
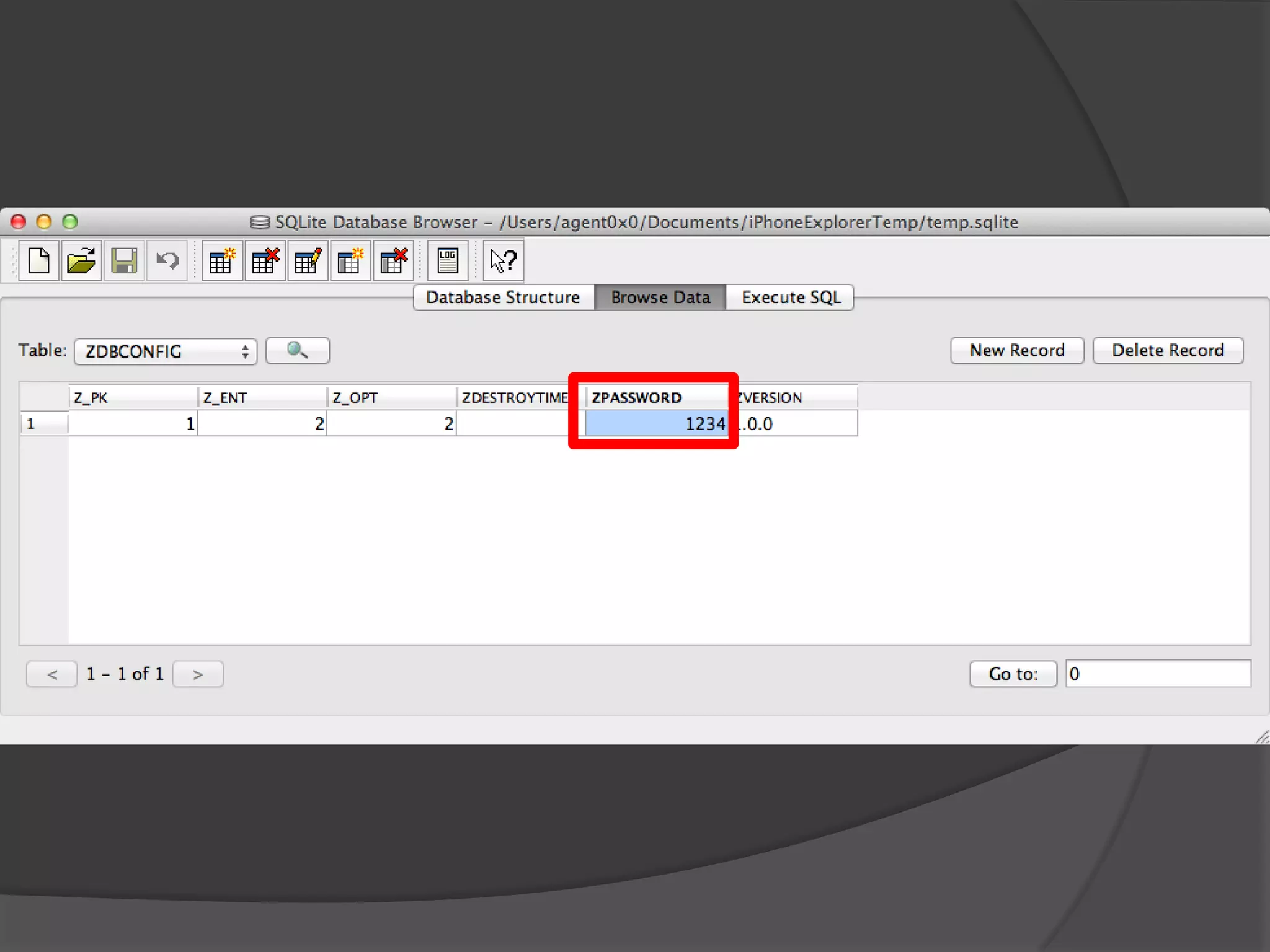
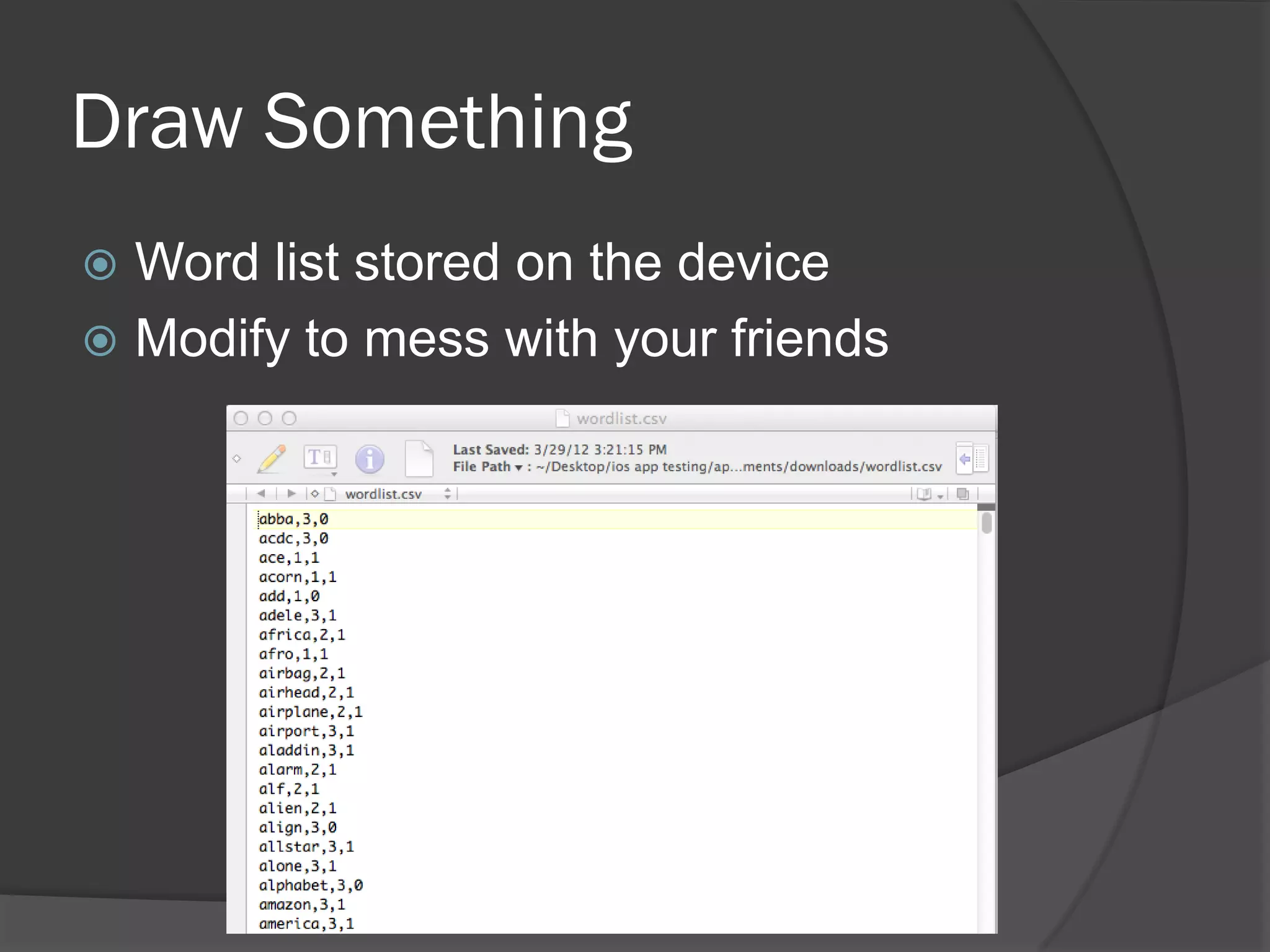
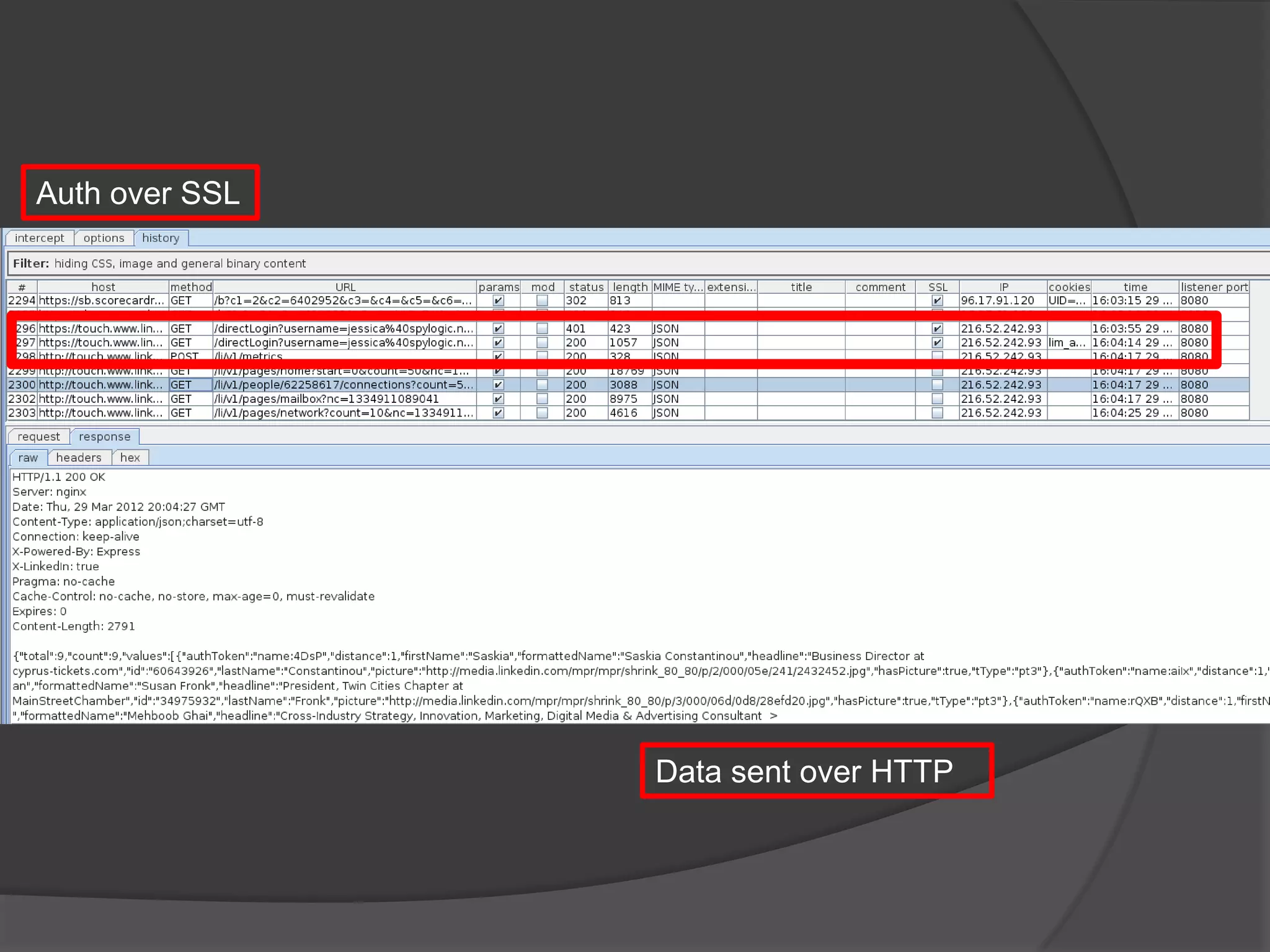
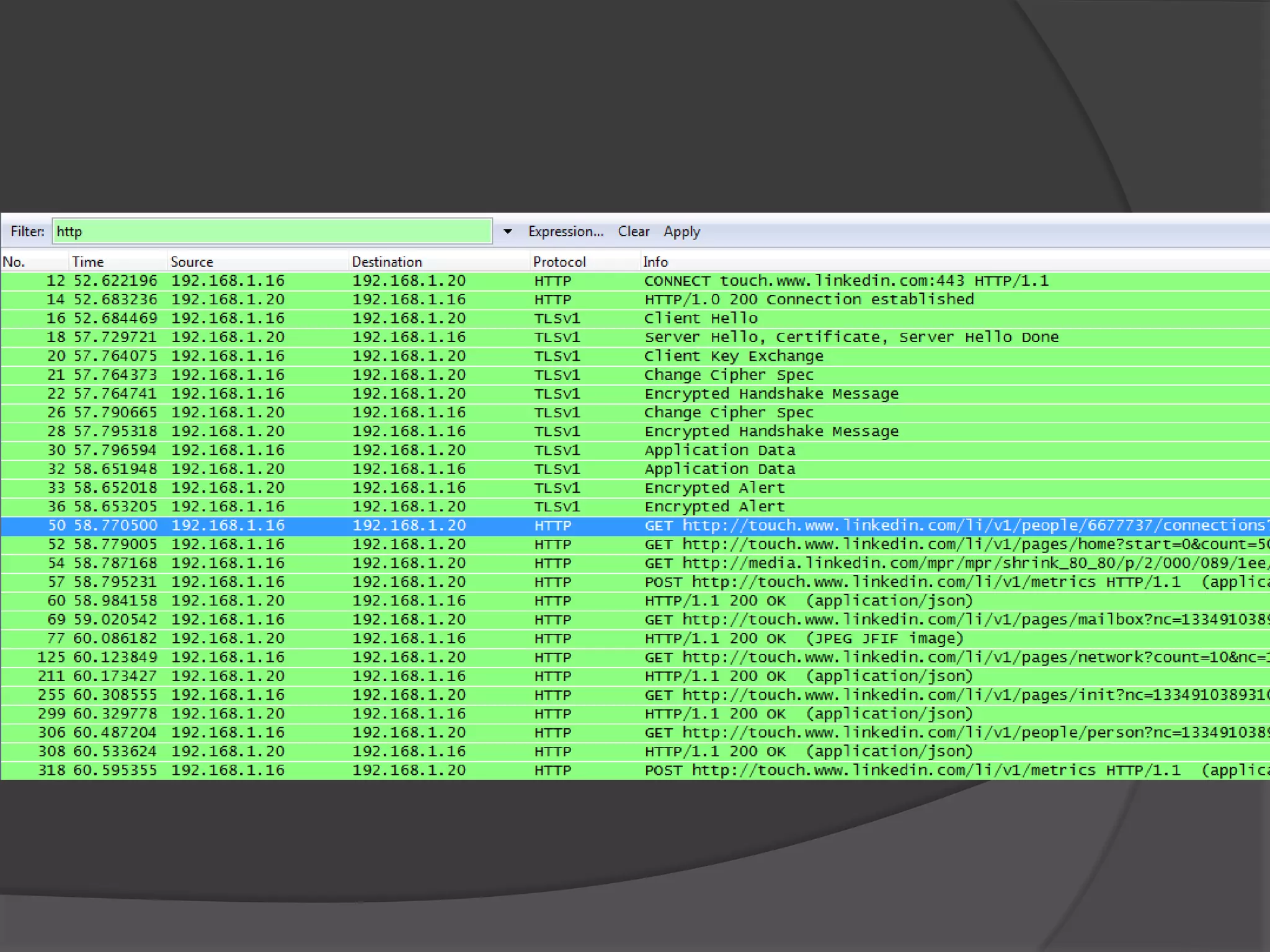
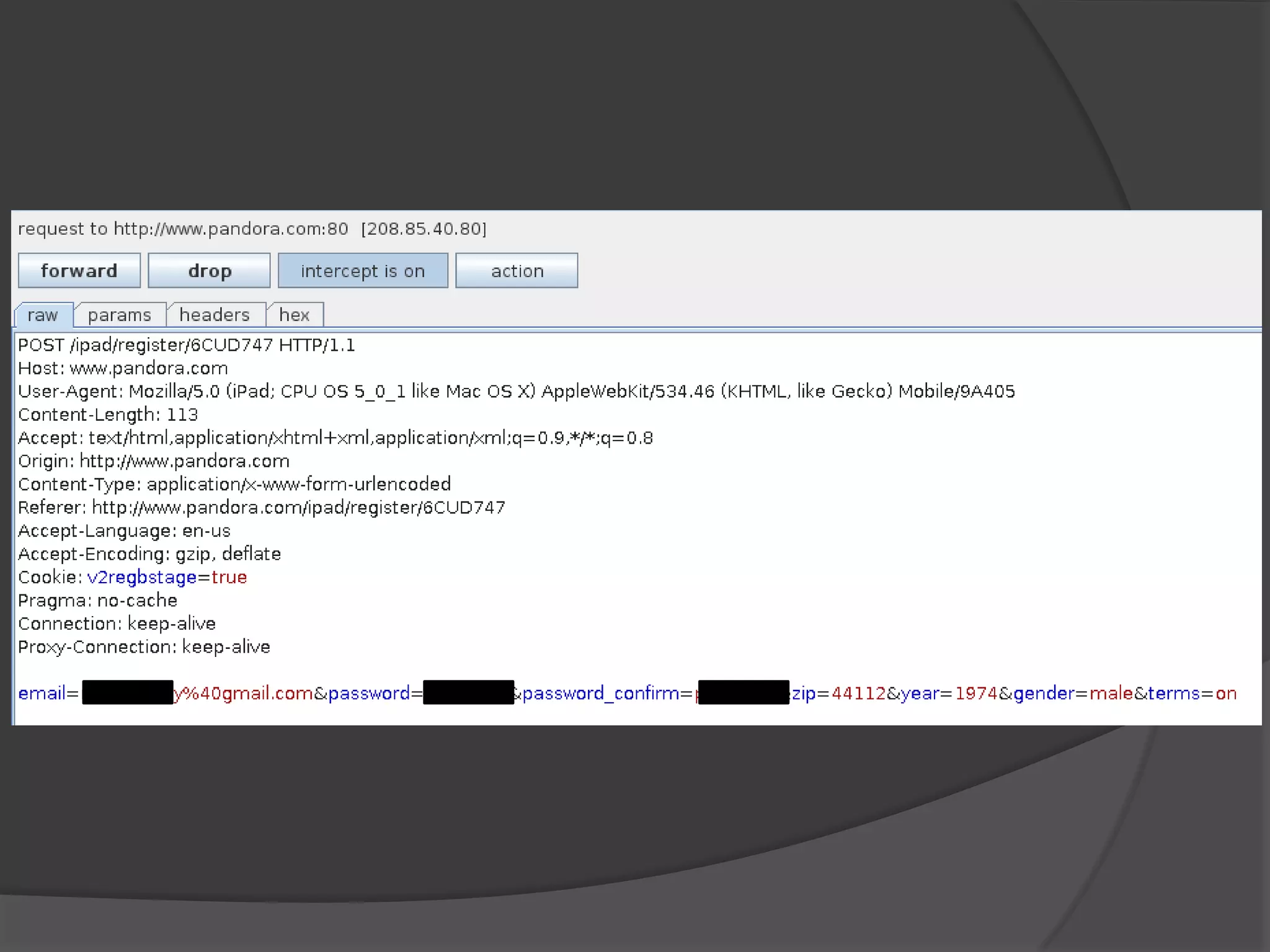
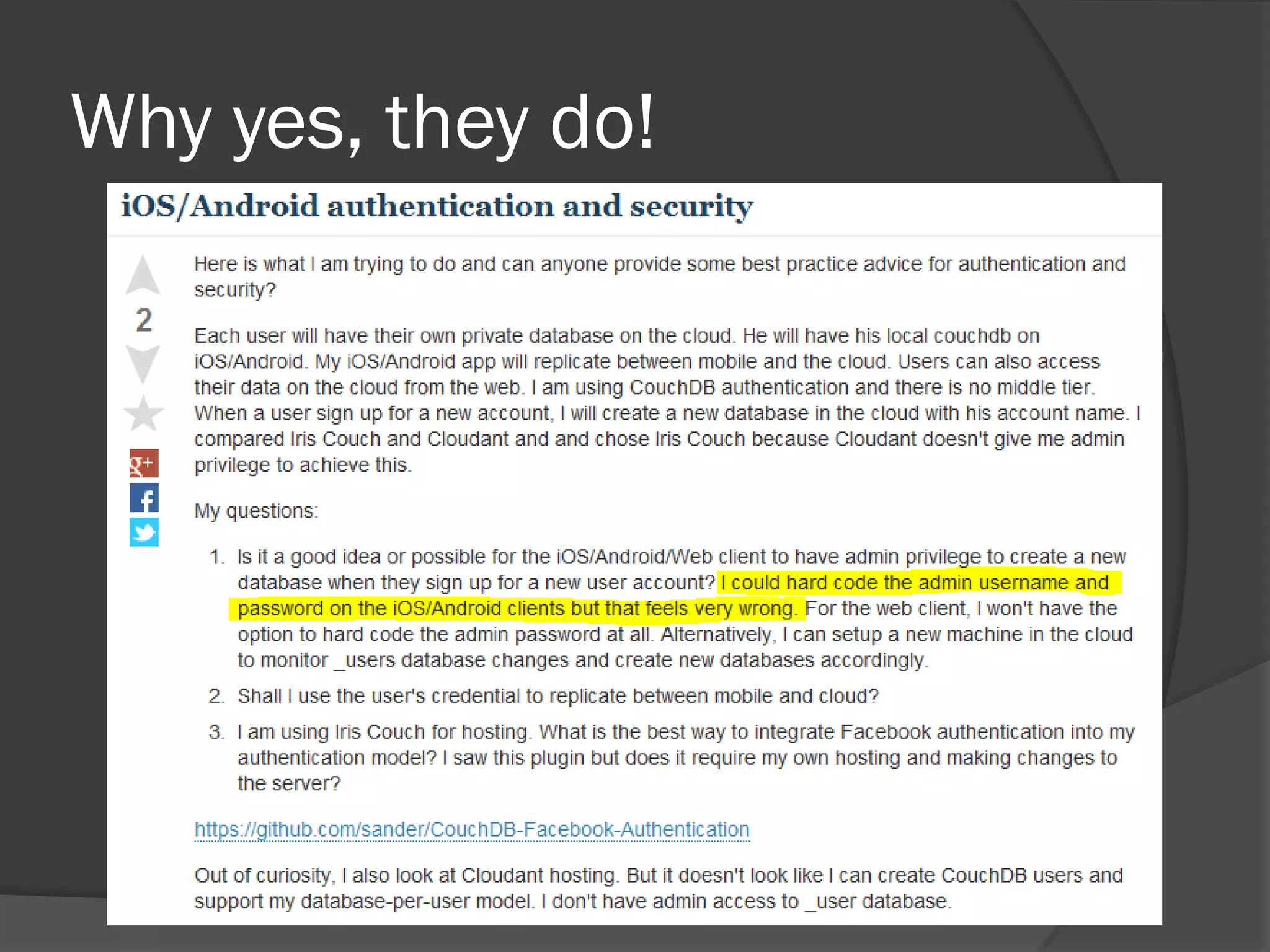
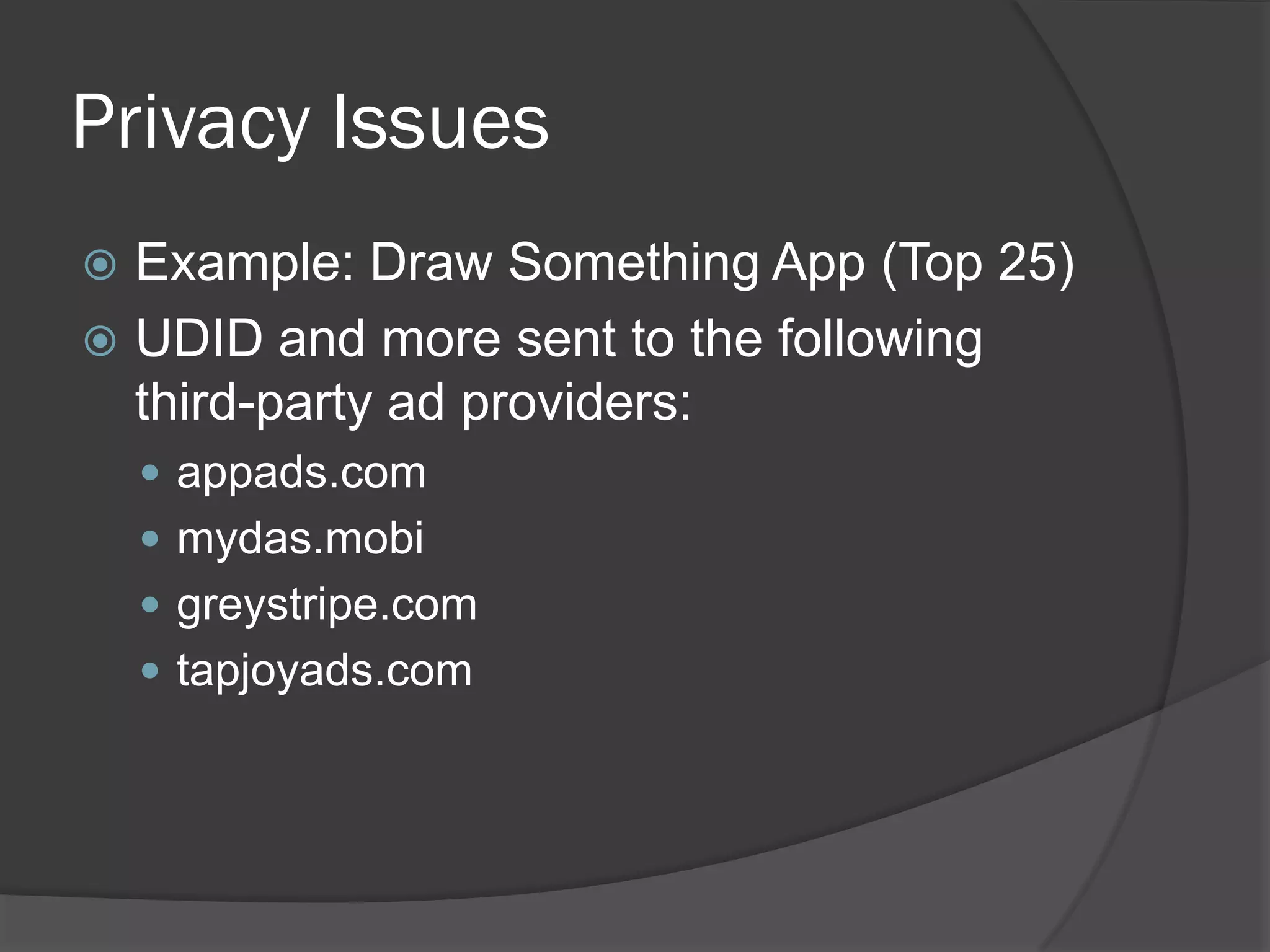
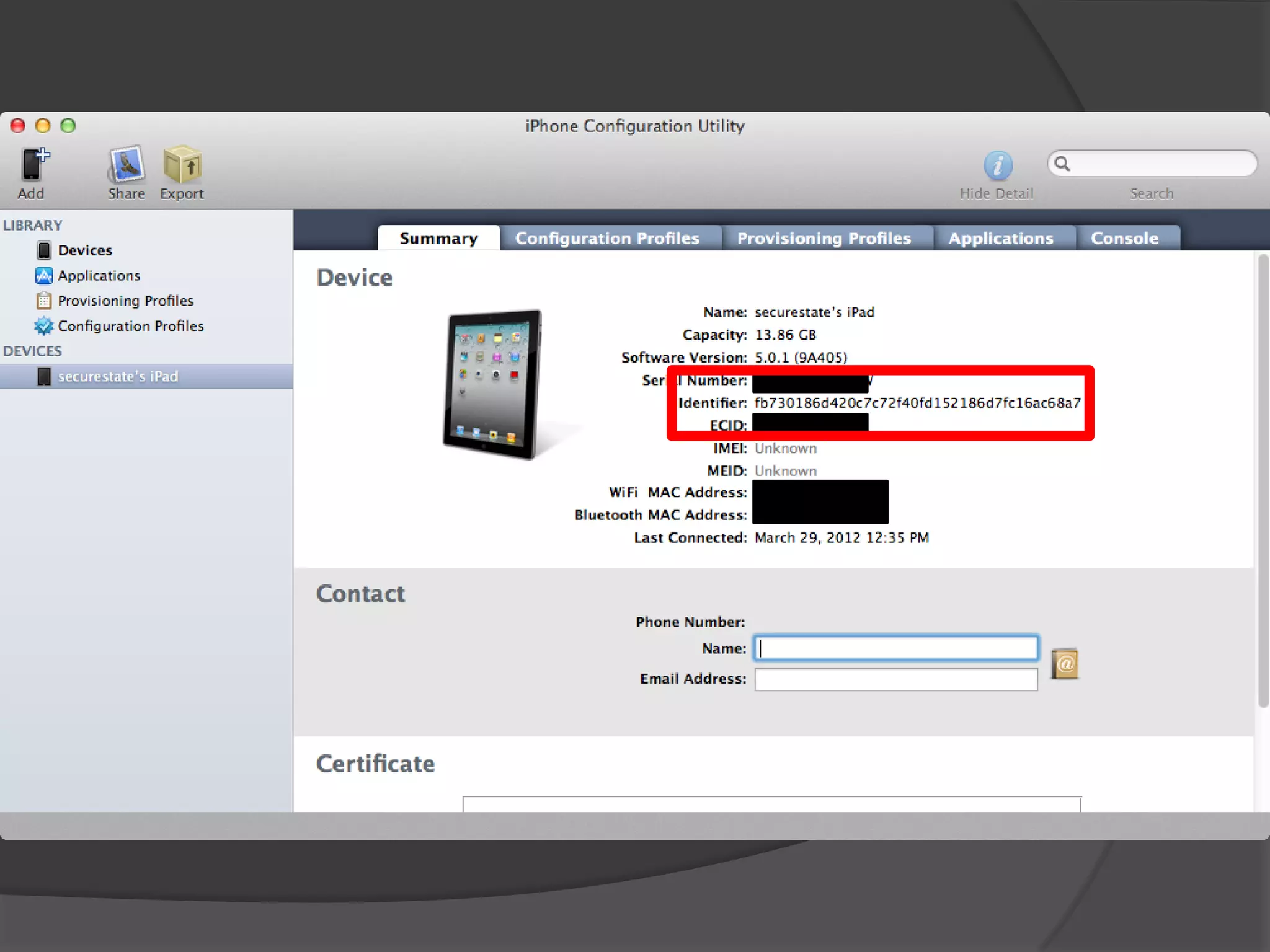
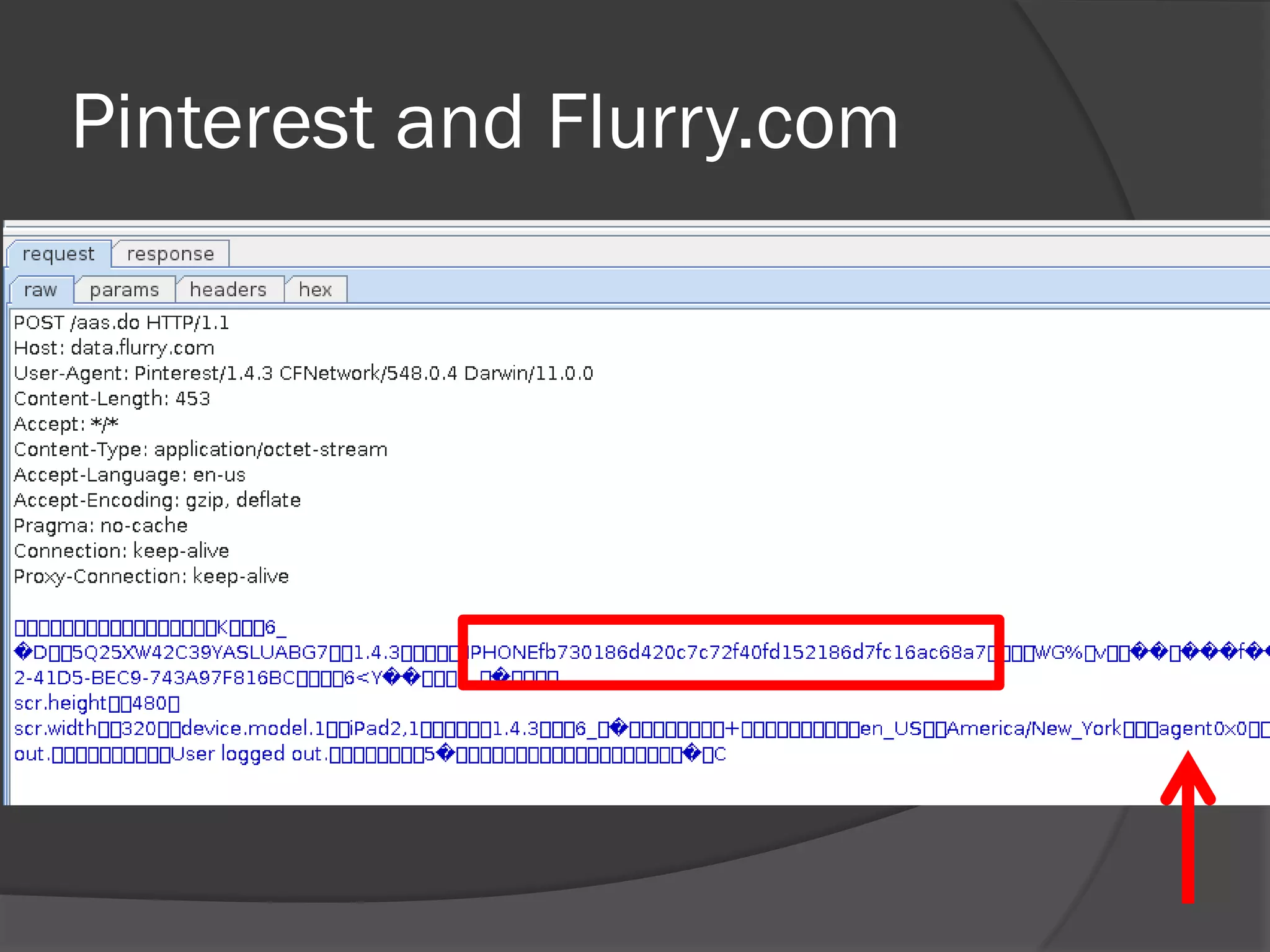
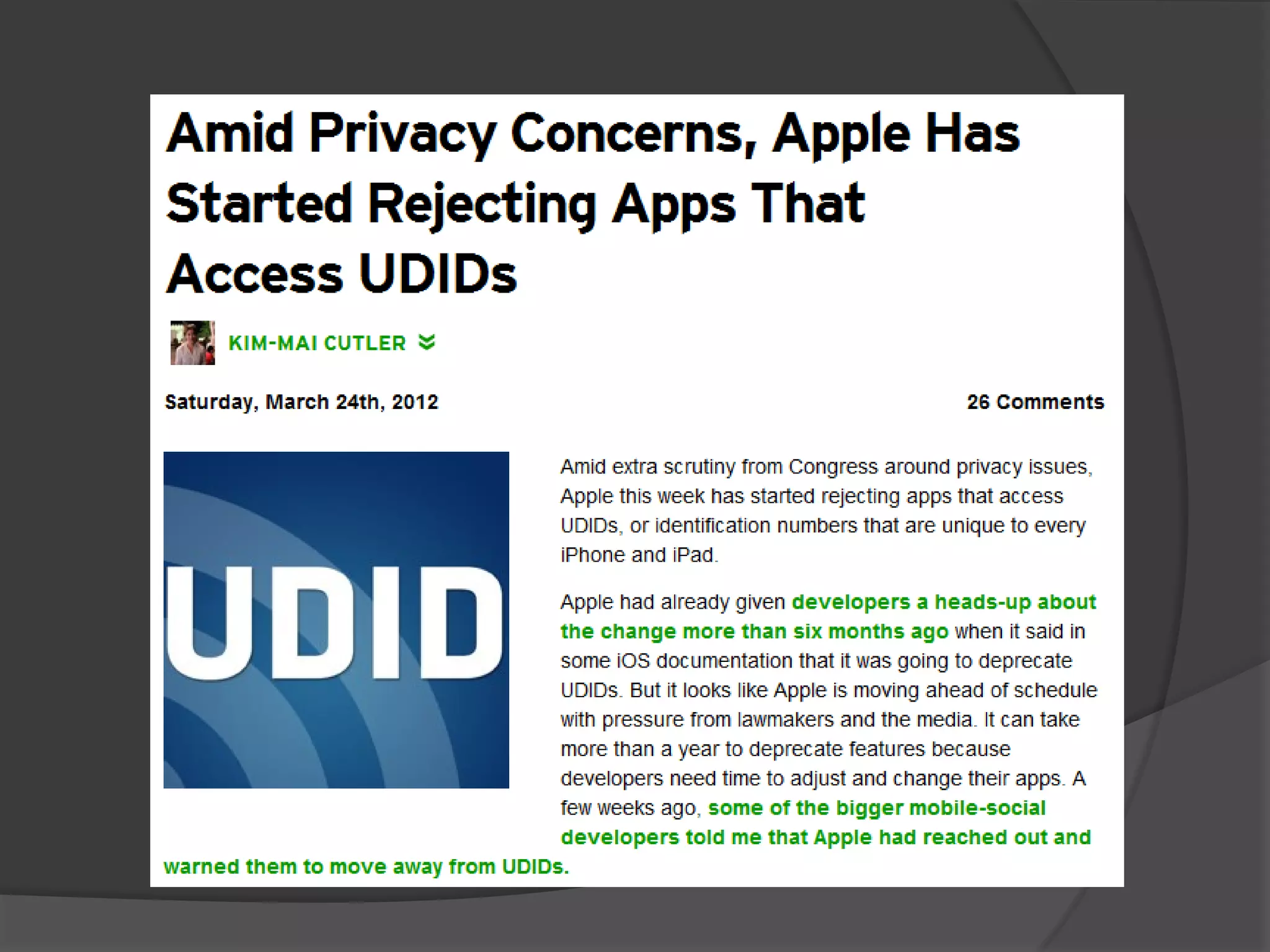
The document discusses mobile vulnerabilities and exploitation, highlighting common risks and areas for testing within mobile applications. It references the OWASP Top 10 mobile risks, including insecure data storage and insufficient transport layer protection, while outlining the importance of security in mobile device usage across various sectors. Additionally, it recommends tools for testing and forensics, and emphasizes the need for developers to prioritize security as mobile devices become increasingly prevalent.