Embed presentation
Downloaded 53 times


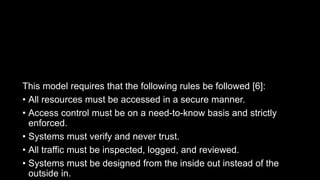
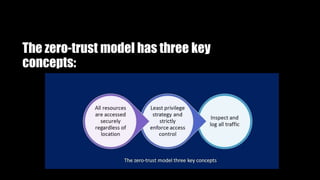
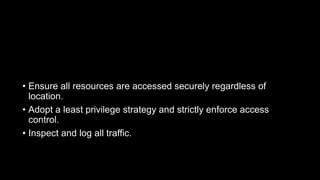
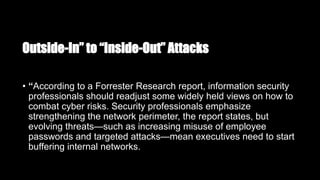









The Zero Trust Model (ZTM) of information security eliminates the concept of 'trusted' interfaces and mandates strict access control, requiring verification for all resources and ensuring traffic is logged and reviewed. It emphasizes a shift from an 'outside-in' to an 'inside-out' attack strategy, recognizing that internal users can also pose security risks. Recommendations for implementing ZTM include updating security infrastructure, analyzing employee access, and leveraging advanced technologies to monitor and control internal and external threats.















