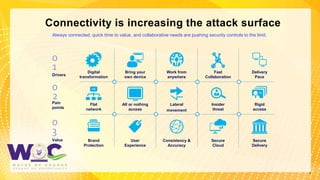
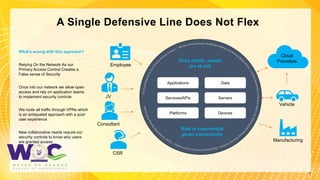
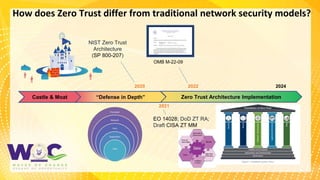
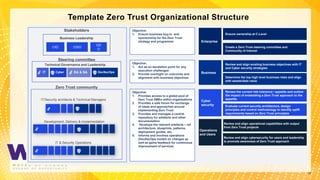
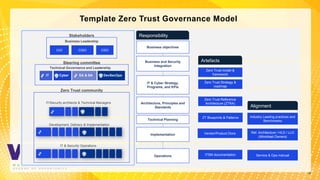
The document discusses the Zero Trust security framework, emphasizing its importance in today’s cybersecurity landscape as a means to prevent unauthorized access and enforce granular access control. It outlines the key principles of Zero Trust, including the necessity of assuming a hostile environment and validating user access continuously. Additionally, it highlights the need for an effective implementation strategy and community engagement to adapt to evolving security challenges.