Embed presentation
Downloaded 80 times

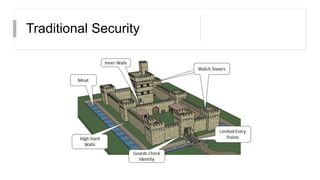
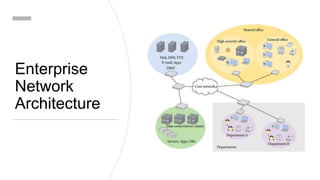
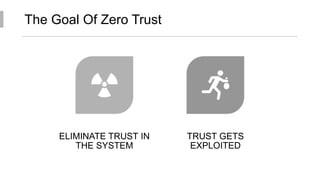
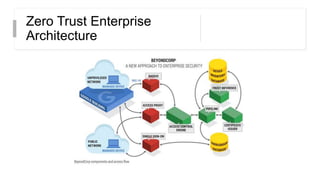
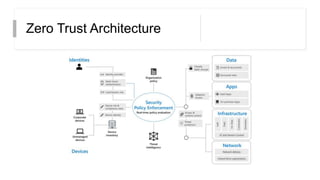
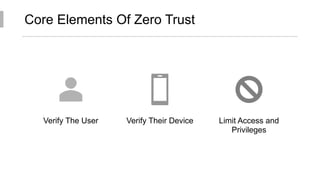
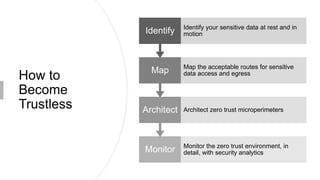


This document discusses the principles of zero trust architecture, which aims to eliminate trust from IT systems by verifying all users and devices before granting limited, least-privilege access. It outlines the core elements of zero trust, including verifying the user, verifying their device, and limiting access and privileges. The document also notes that implementing zero trust will require monitoring the environment closely, architecting microperimeters, mapping acceptable data routes, and identifying sensitive data. Organizations may face challenges from technical debt, legacy systems, and other issues requiring new technologies or wrappers.










