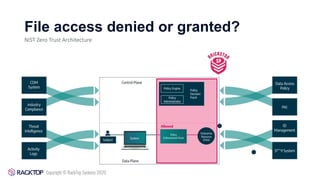
The document explains the concept of Zero Trust, emphasizing the need to eliminate implicit trust and focus on protecting individual resources, particularly in distributed environments. It discusses a dynamic security model that evaluates trust based on each transaction, and highlights the importance of monitoring data access while addressing vulnerabilities in legacy systems. The BrickStor SP solution is presented as an effective measure to enhance data security by integrating safety without compromising performance.