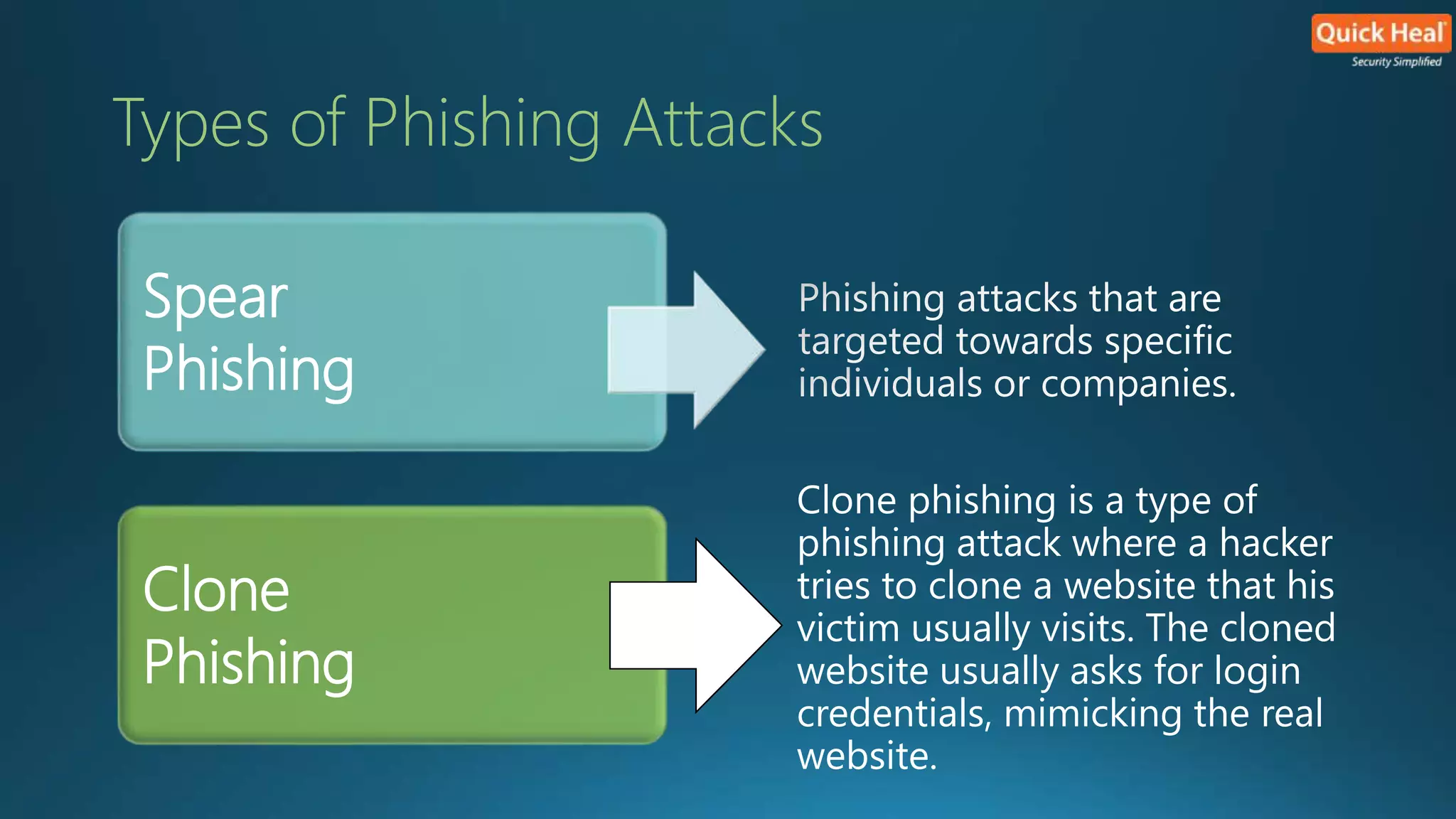
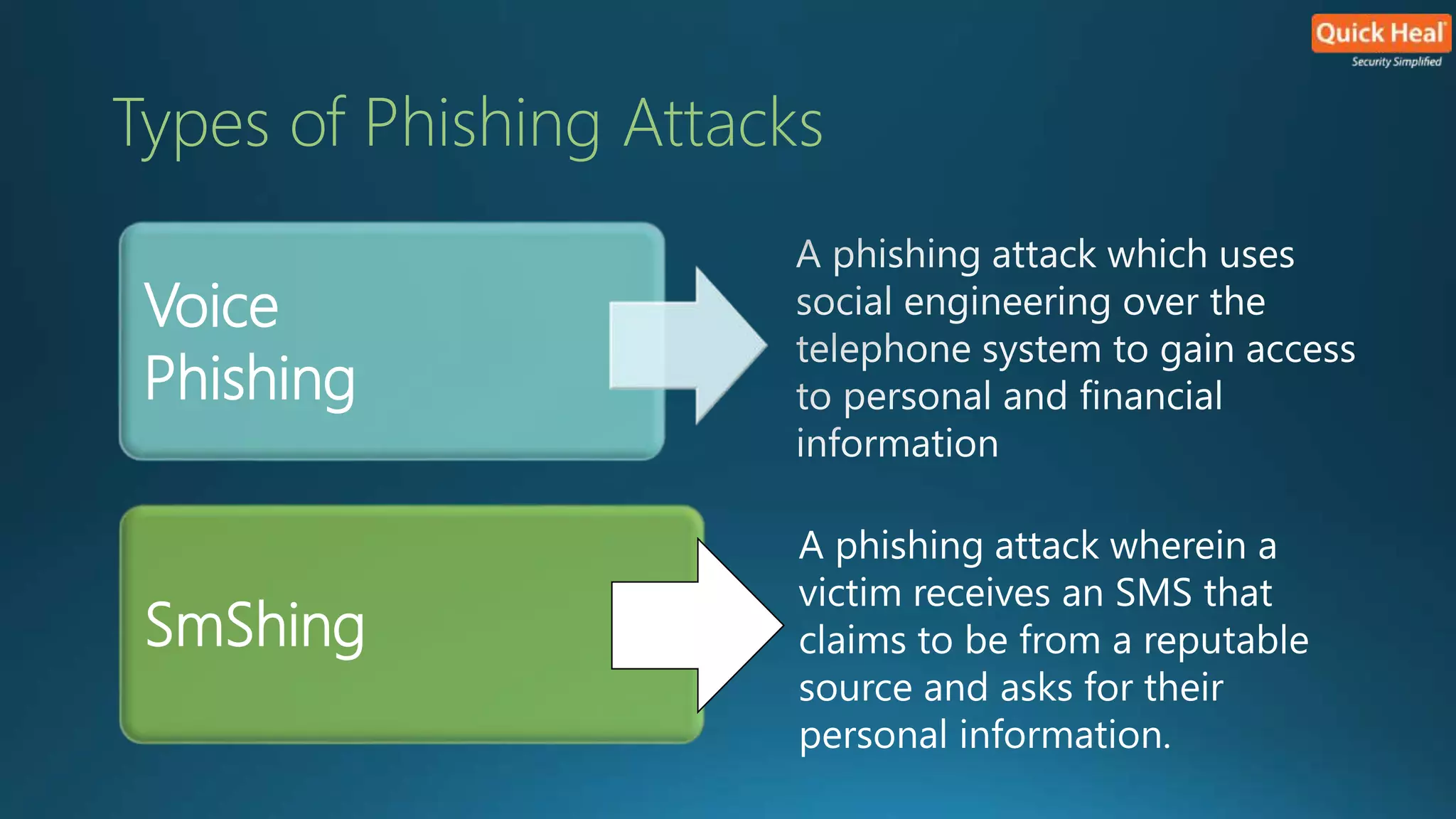
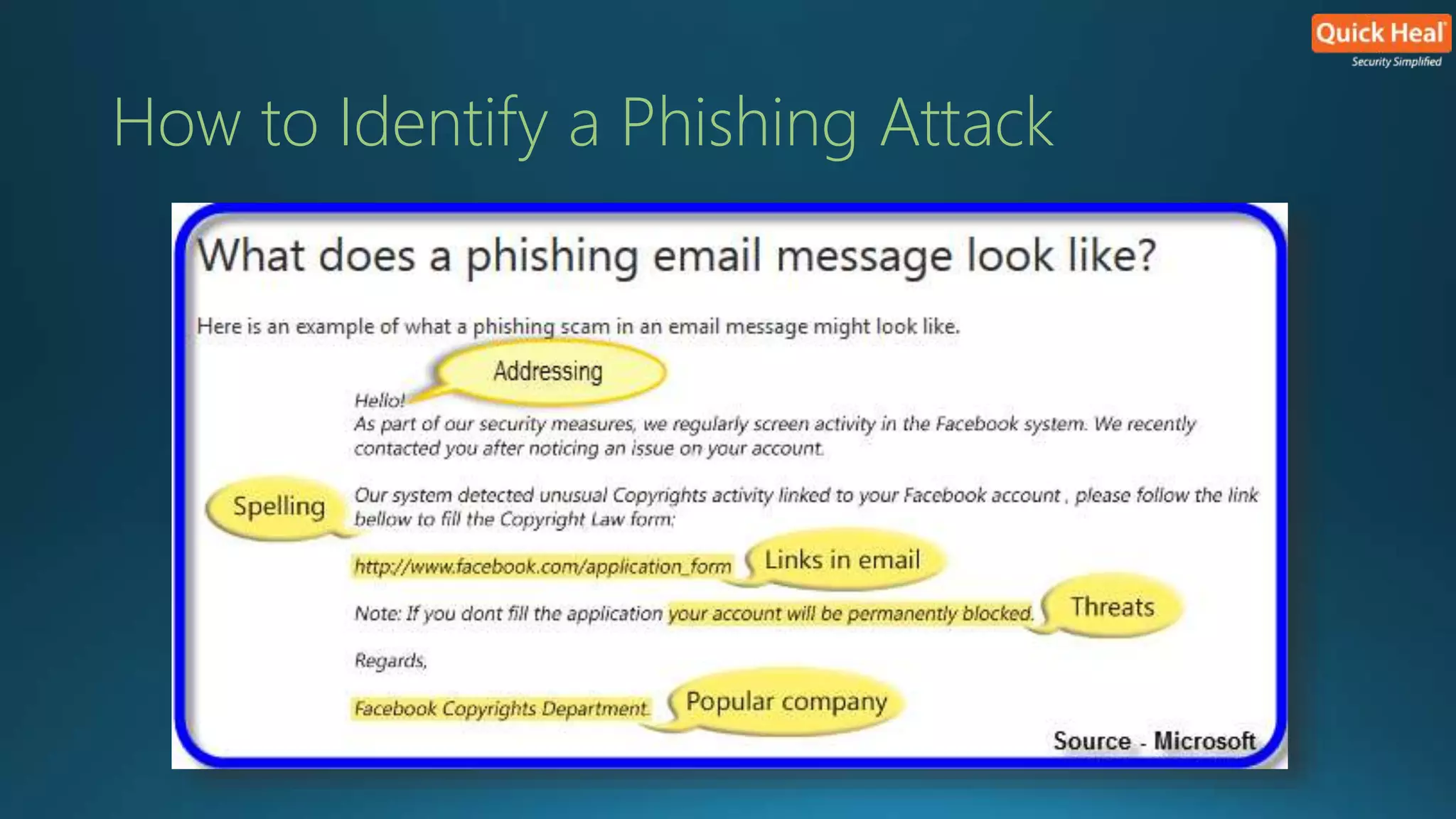
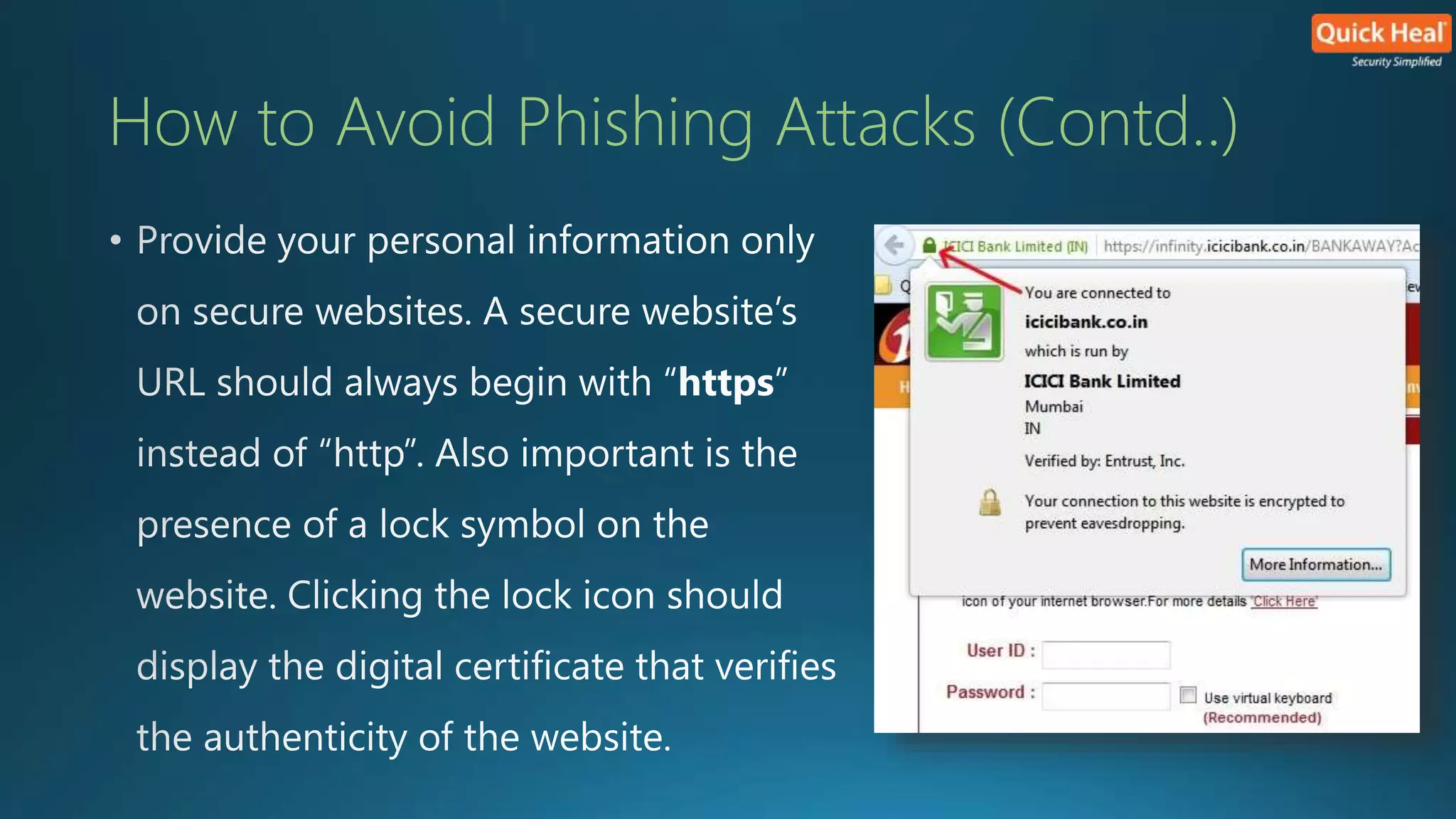
This webinar provides an overview of phishing, emphasizing that security is a collective responsibility and highlighting various phishing techniques such as spear phishing, clone phishing, and smshing. It outlines characteristics of phishing attacks and offers identification tips, warning against generic greetings and unusual URLs. While no single solution exists for preventing phishing, implementing the right precautions and security measures can enhance protection against these threats.