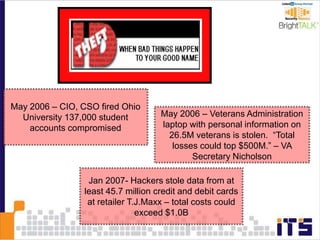
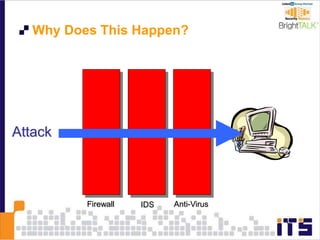
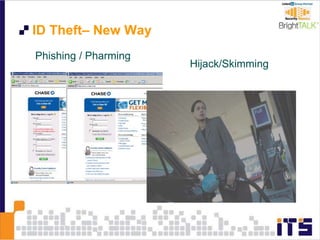
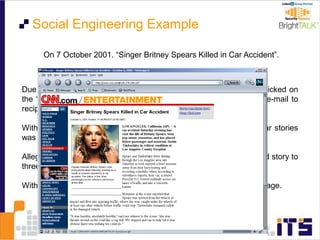
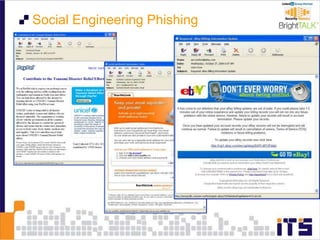
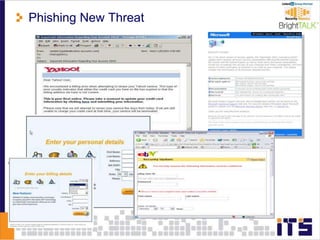
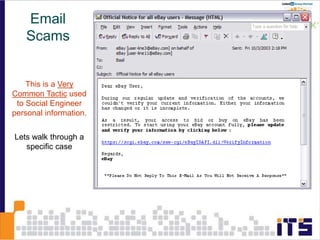
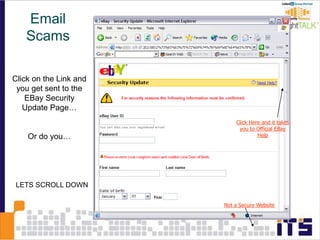
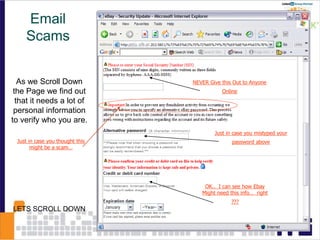
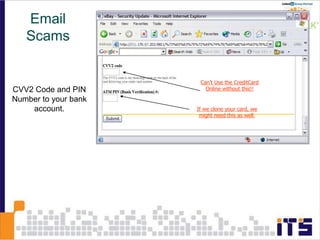
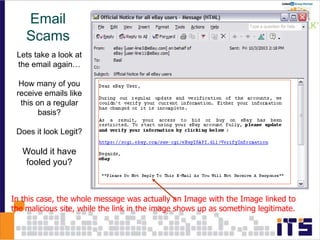
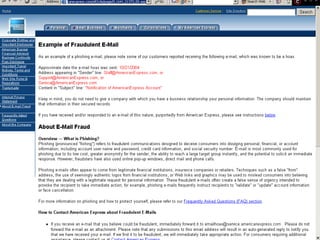
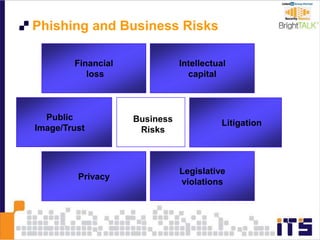
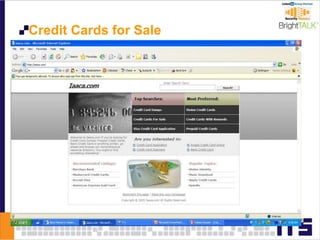
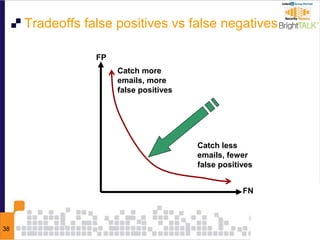
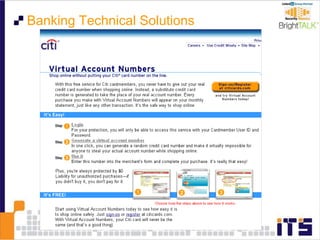
This document discusses email phishing and countermeasures. It provides examples of data breaches and losses from stolen personal information. Phishing works through social engineering techniques like spoofing emails and websites to steal passwords, credit card numbers, and other details. Users may unwittingly provide such information in response to phishing attacks. Defenses against phishing include educating users, technical filters and monitoring, and legislation against identity theft. Ongoing challenges include the sophistication of attacks versus defenses.