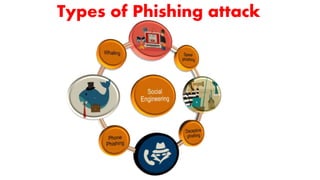
The document discusses phishing as a fraudulent method to obtain sensitive personal information, detailing various types such as deceptive phishing, spear phishing, whaling, vishing, and smishing. It emphasizes recognizing and avoiding phishing scams through careful inspection of emails and URLs, as well as implementing best practices like security awareness training and using protective software. The document advocates for proactive measures, including multi-factor authentication and maintaining up-to-date antivirus protection.