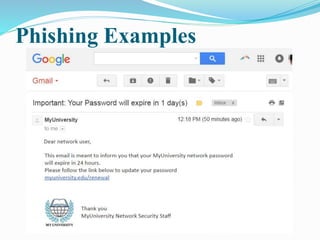
The document outlines Prajakta Shinde's seminar on phishing attacks. It defines phishing as attempting to acquire personal information through electronic communication by posing as a trustworthy entity. It discusses common phishing techniques like link manipulation and phone phishing. It also covers types of phishing like deceptive and man-in-the-middle phishing, causes of phishing like user awareness and website vulnerabilities, methods to defend against attacks, and concludes that a combination of user education and security improvements can help reduce phishing.