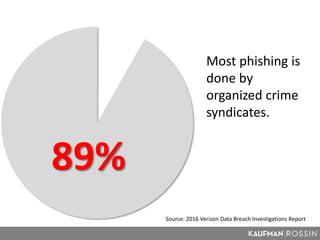
This document provides information about phishing attacks and how to identify and avoid them. It defines phishing as fake emails sent to trick users into clicking links or downloading attachments. Many phishing emails are opened and clicked within an hour, showing they can be effective. However, human detection of phishing attacks is more effective than technology. The document outlines common traits of phishing emails like generic greetings and requests for urgent action. It advises users to be suspicious of unsolicited attachments and links, and to contact senders through verified methods rather than responding directly. Users should report any suspected phishing to IT and not click, respond or download anything from suspicious emails.