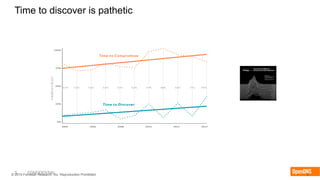
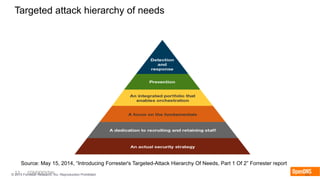
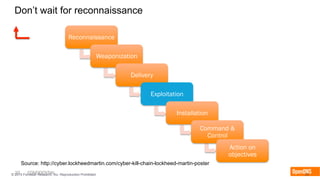
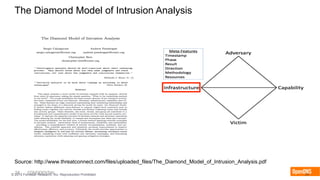
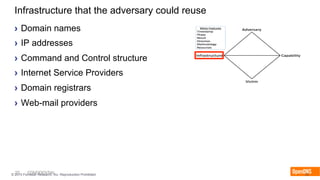
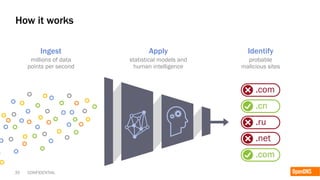
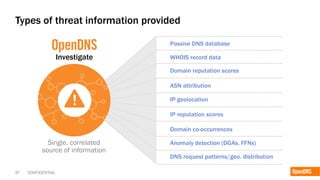
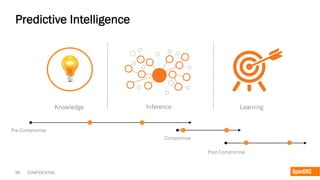
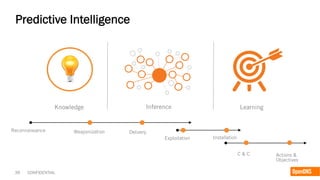
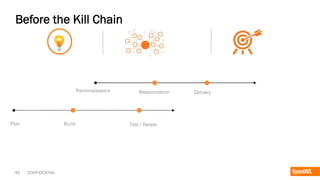
The document discusses the importance of the cyber kill chain and the need for prevention in cybersecurity rather than solely relying on detection and response. It emphasizes the urgency of improving incident discovery times and leveraging predictive analytics to anticipate adversary tactics. Additionally, it highlights the necessity of blocking adversary infrastructure to enhance overall security efficacy.