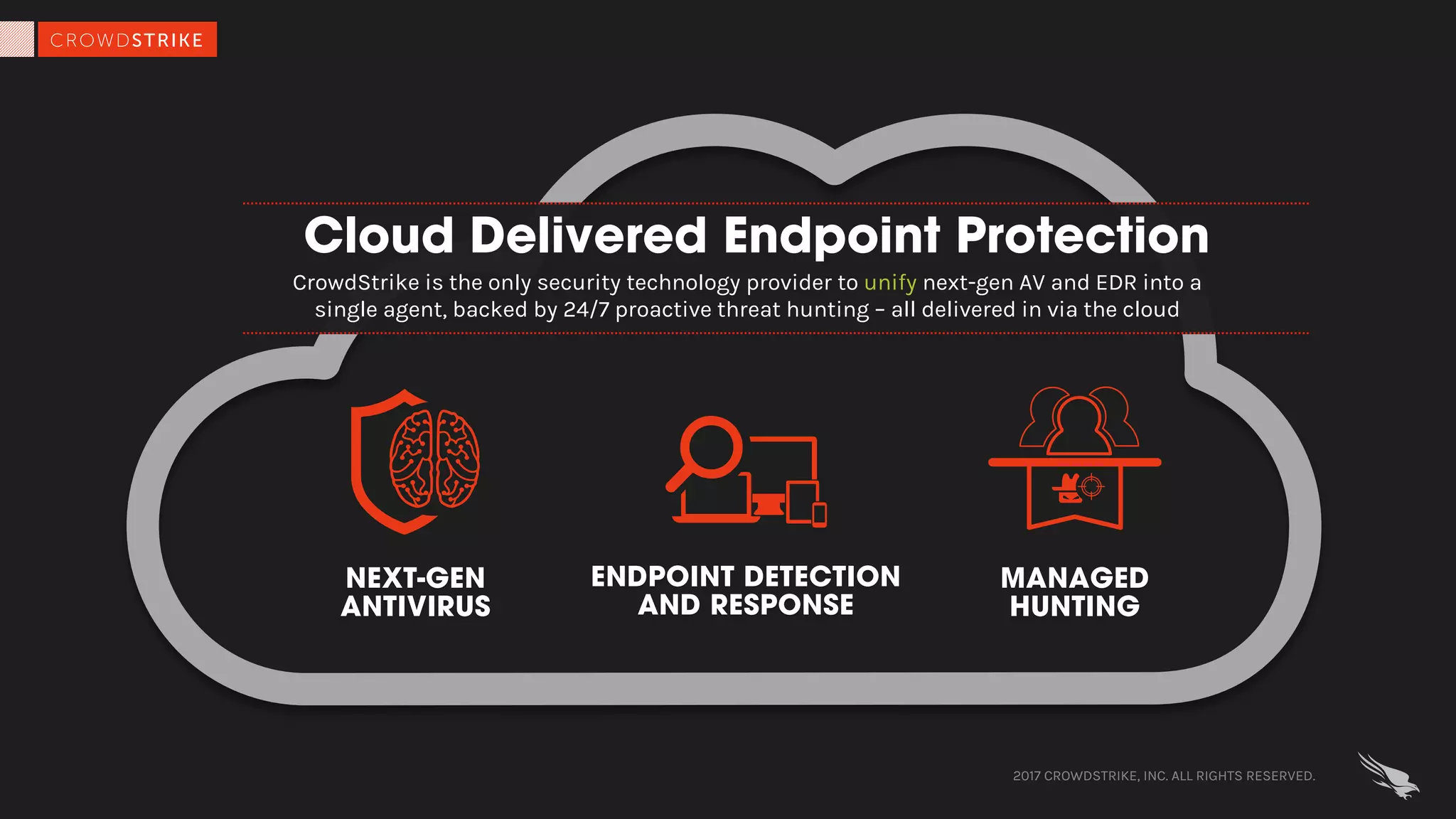
CrowdStrike's document outlines the advantages of cloud-enabled endpoint security, highlighting improved performance, easier deployment, and enhanced protection through real-time intelligence sharing. It addresses common concerns regarding data security in the cloud and explains how CrowdStrike's solutions mitigate these risks while maintaining strict data privacy controls. The document emphasizes the effectiveness of their technology in detecting and responding to threats, leveraging cloud capabilities for better operational efficiency and threat hunting.