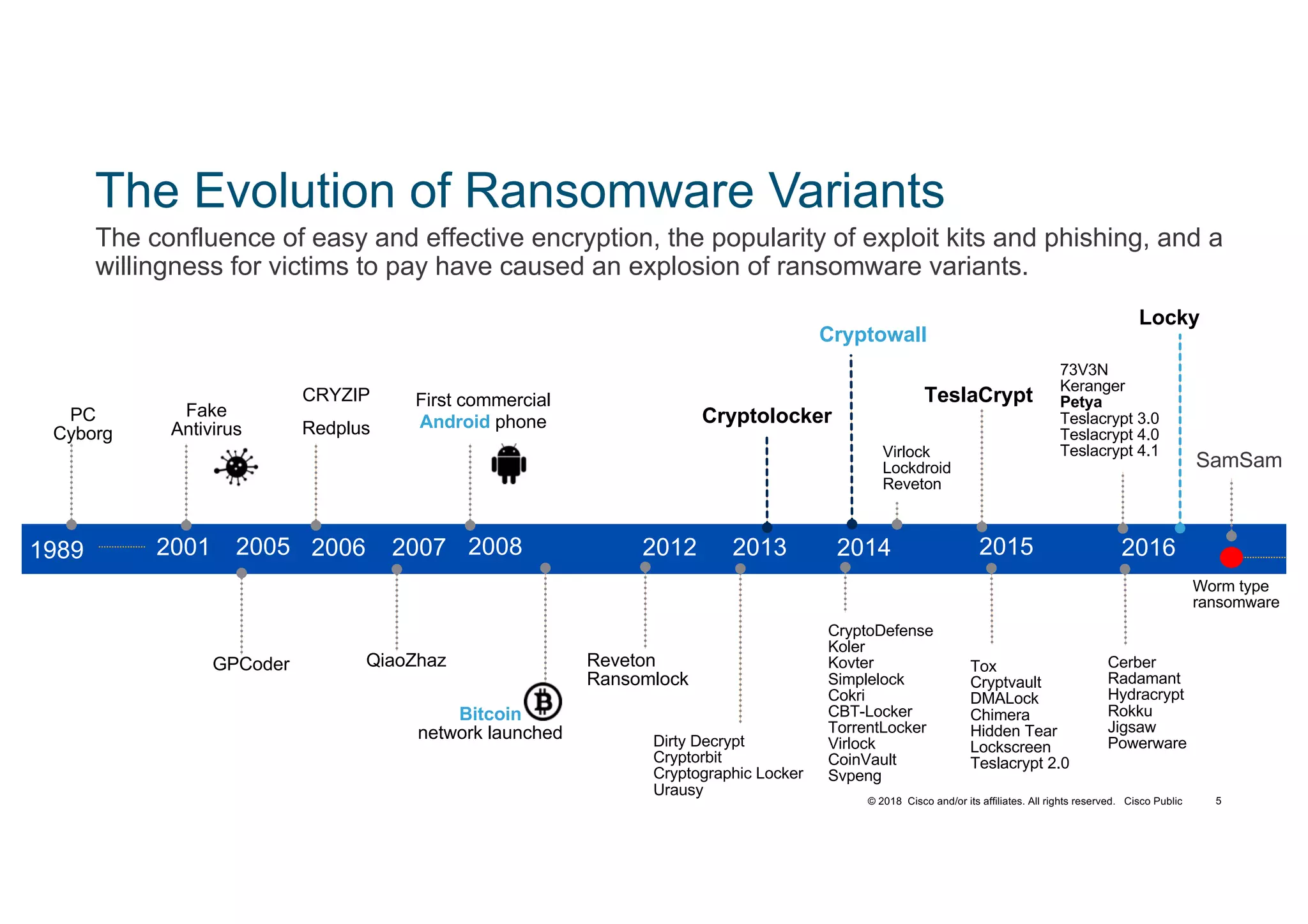
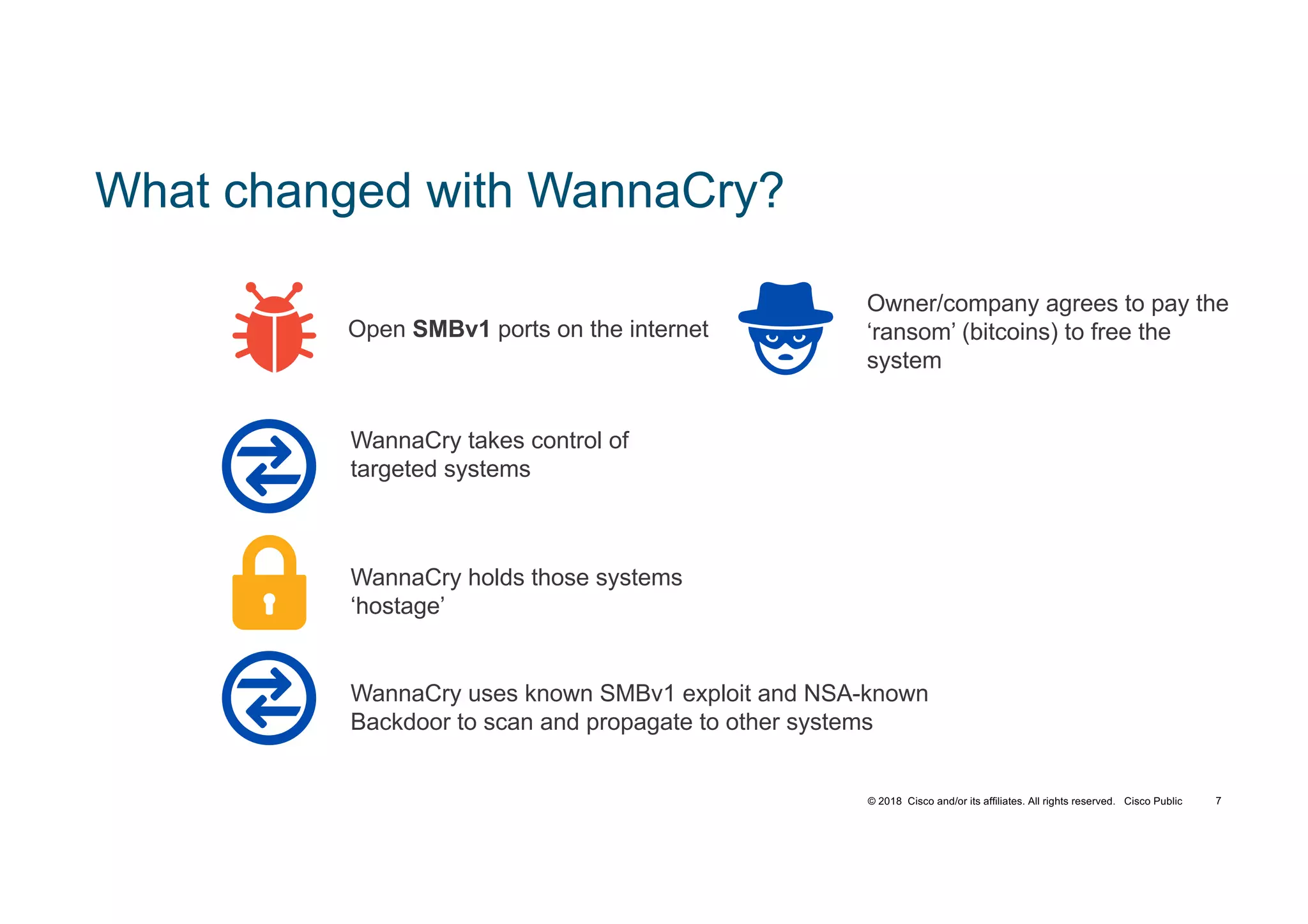
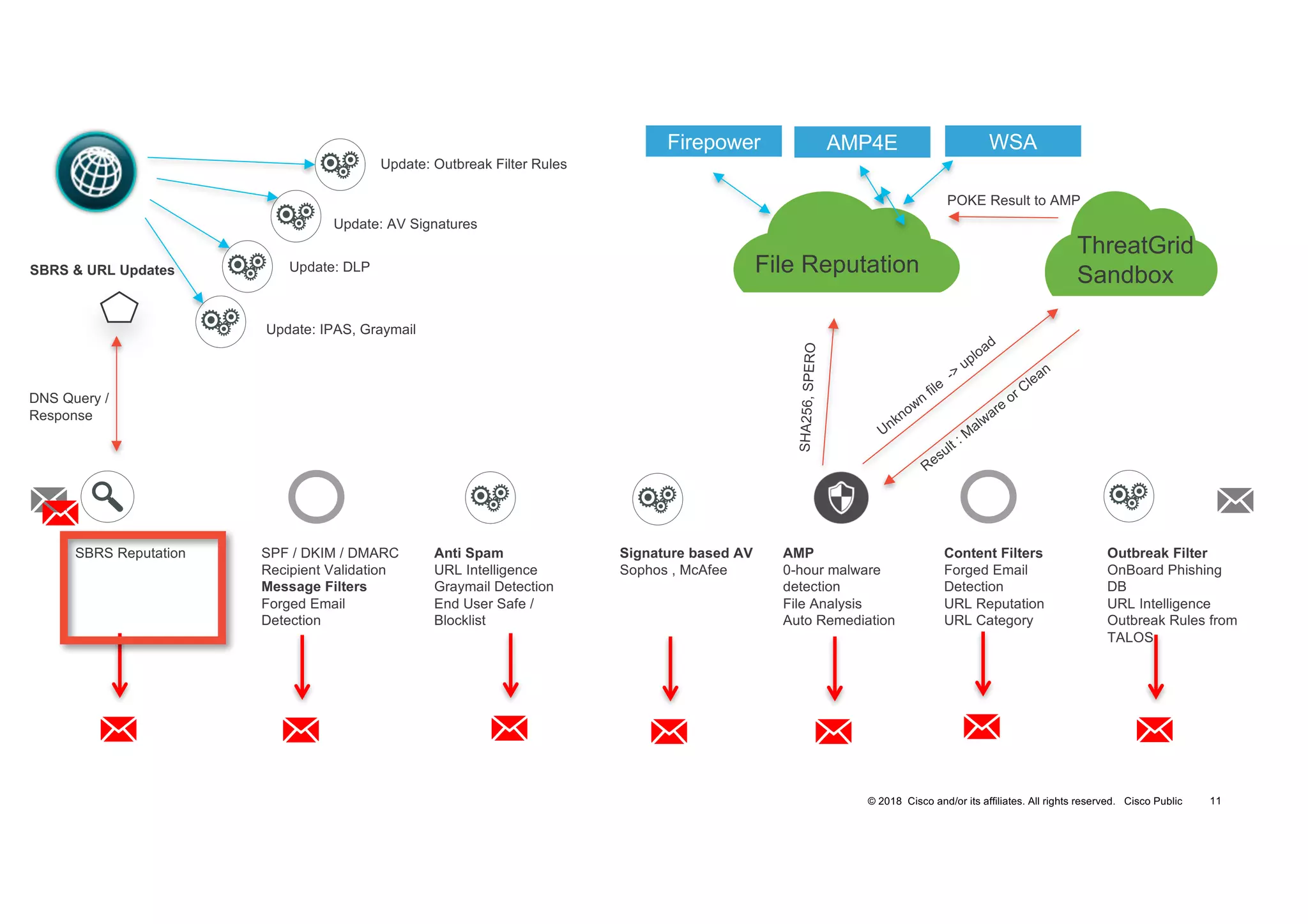
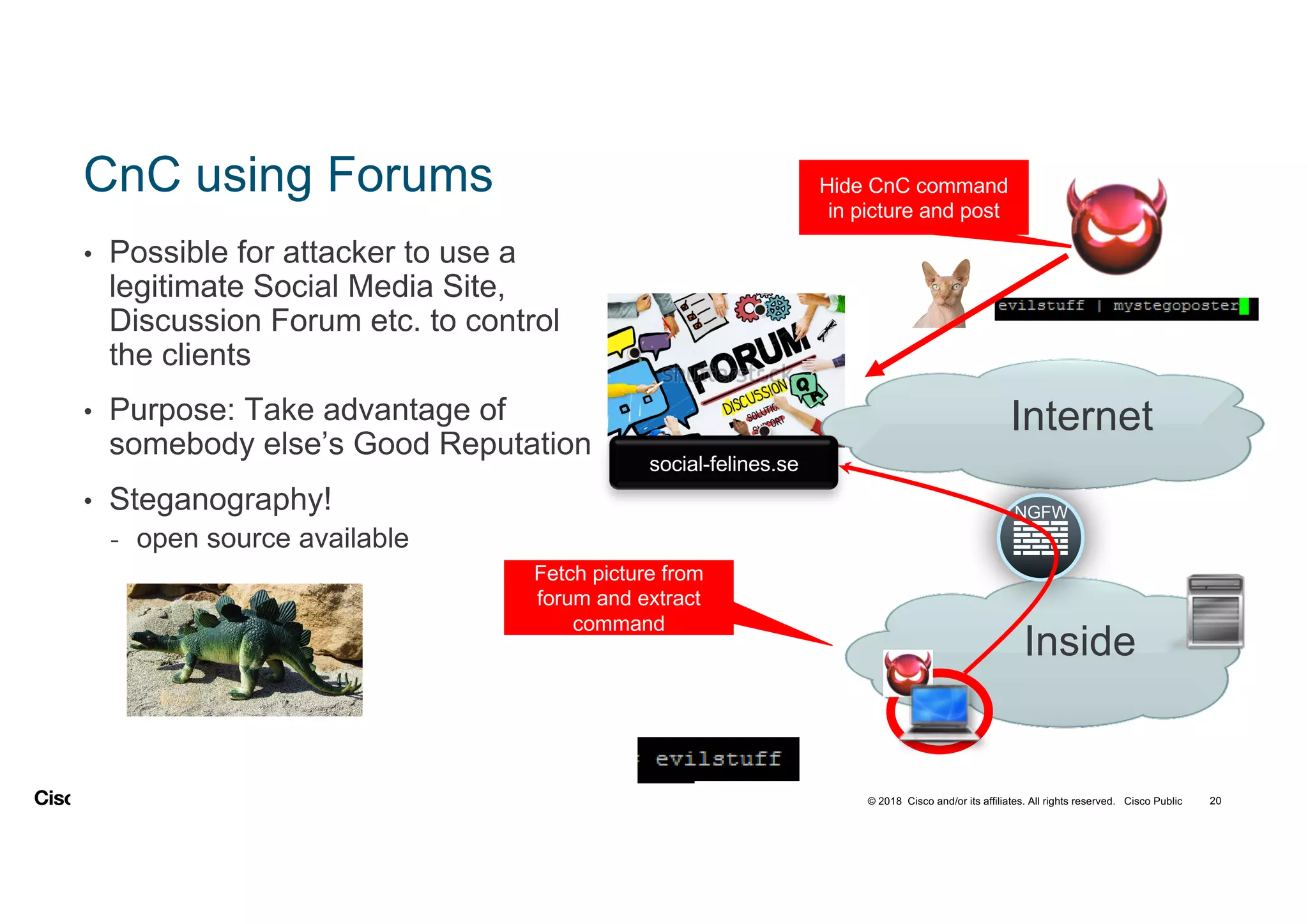
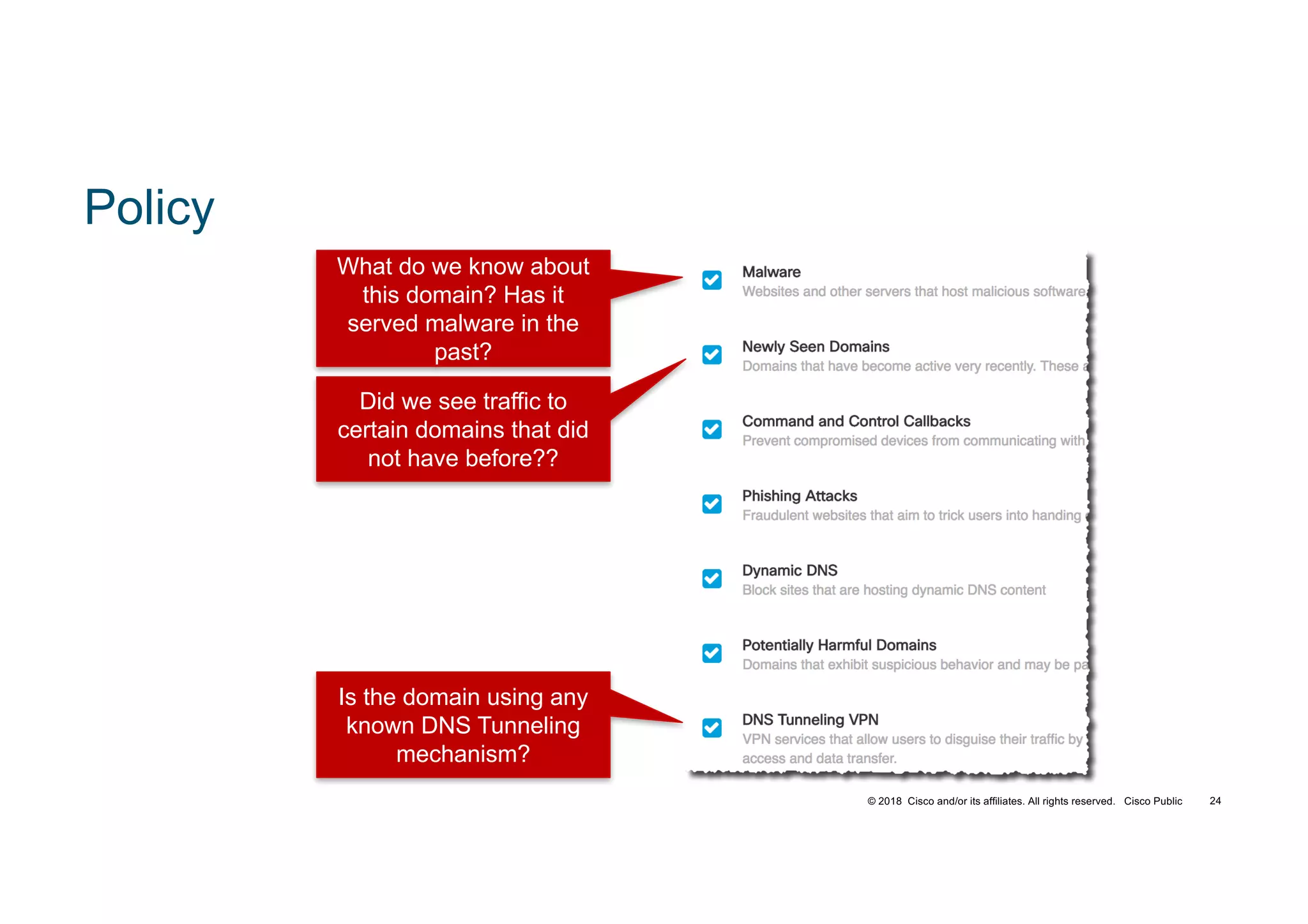
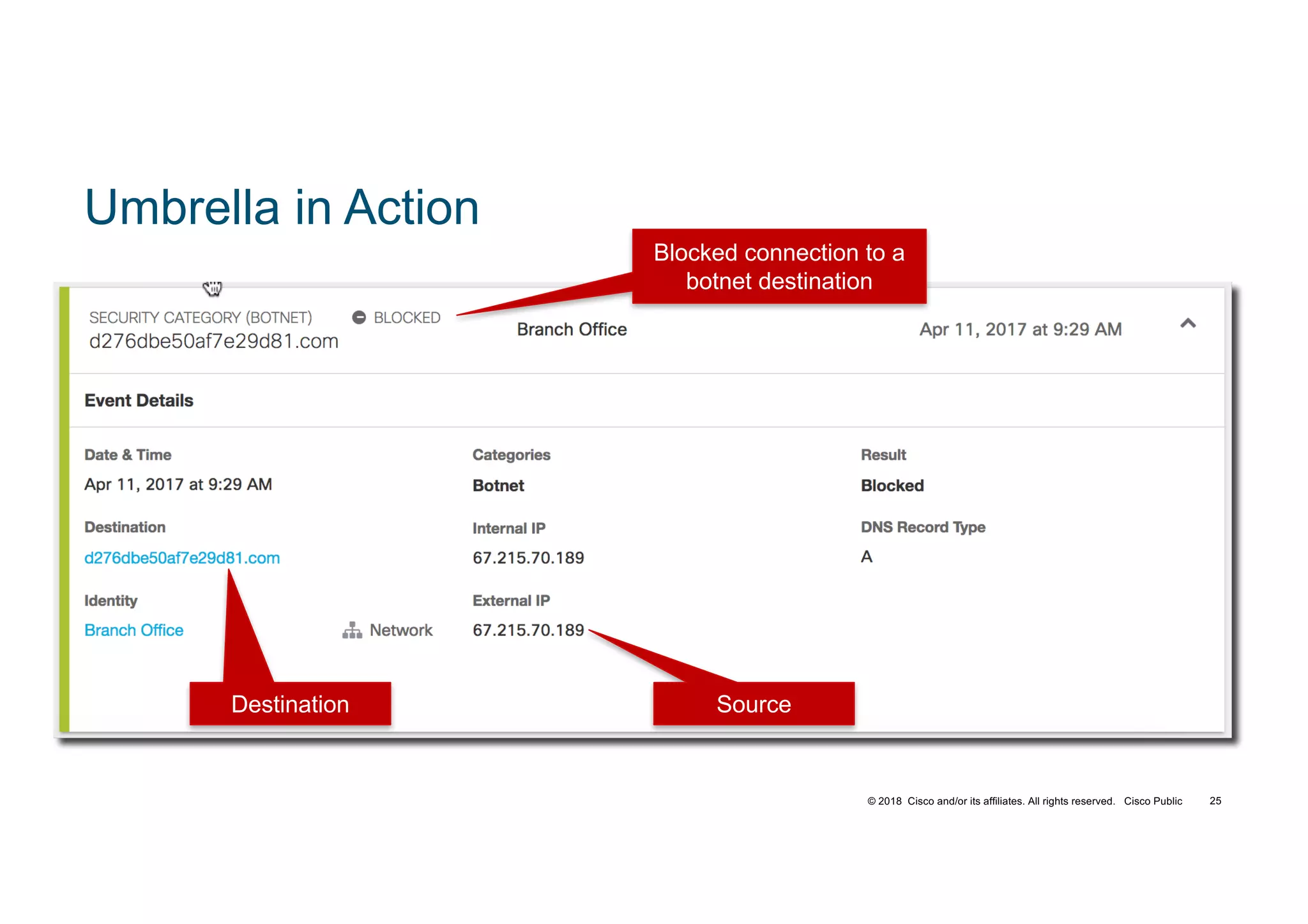
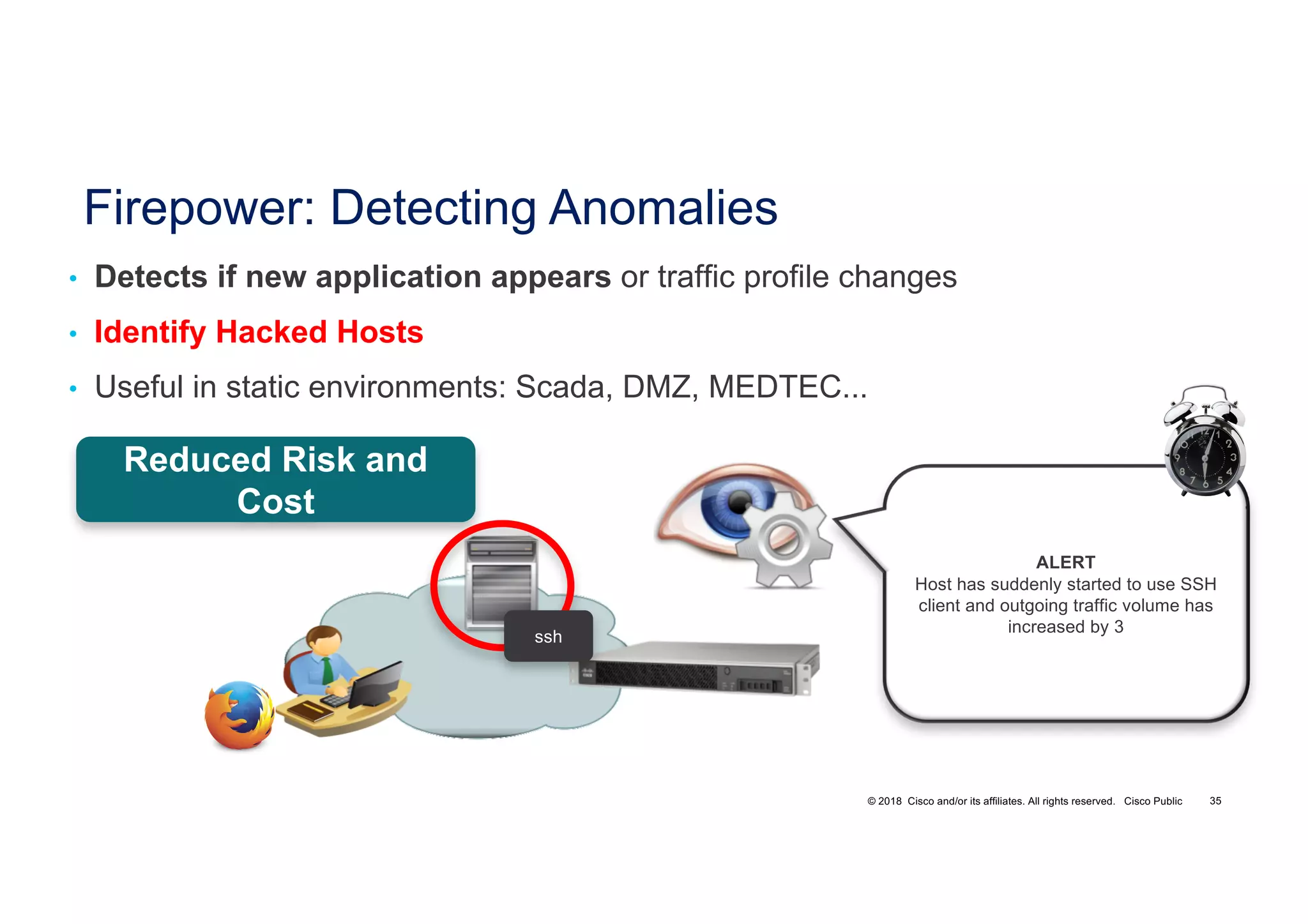
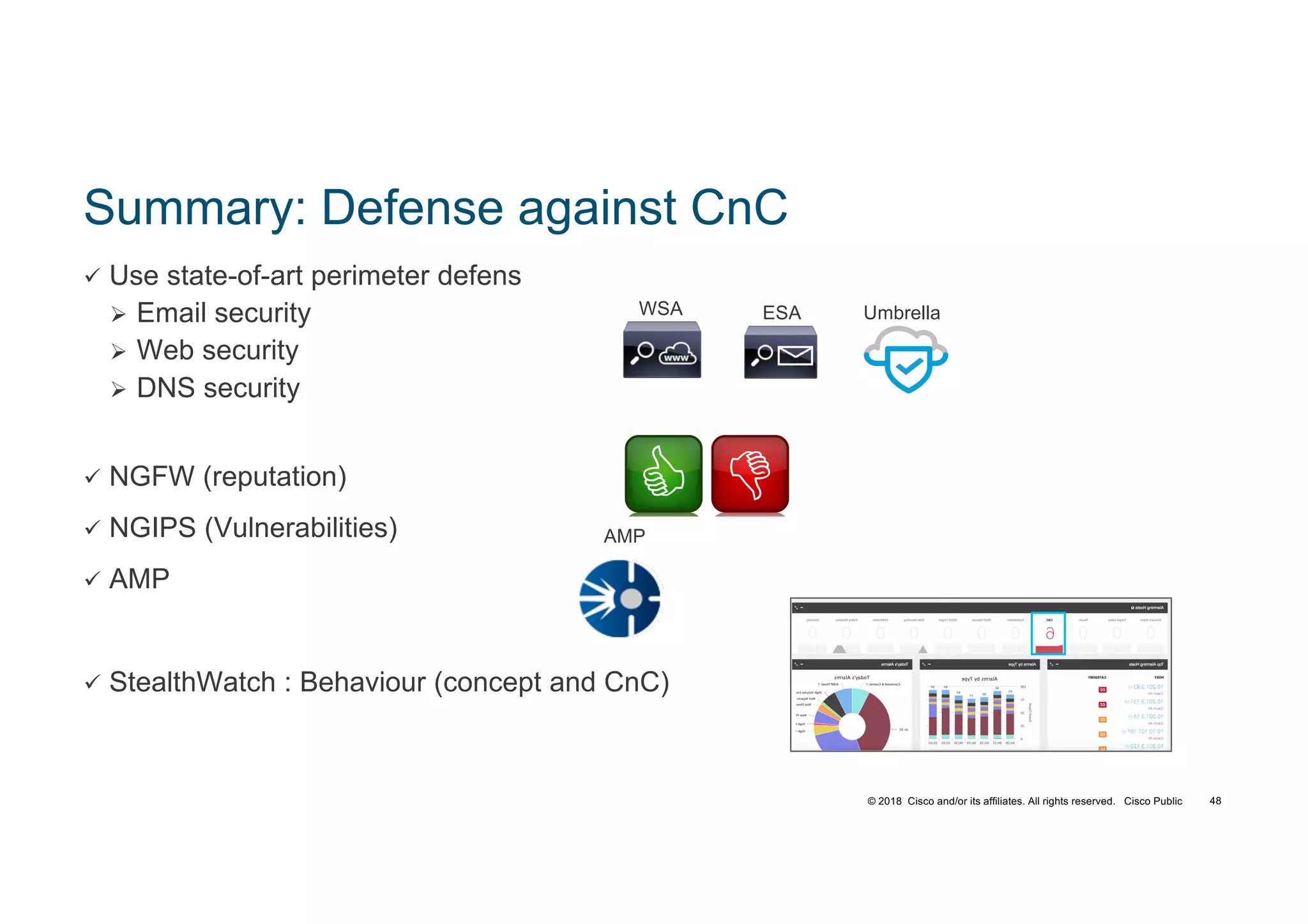
The document discusses various techniques used in ransomware attacks and defenses against them. It covers topics like email security appliances, command and control (CnC) detection using DNS, the evolution of ransomware variants, and tools like Umbrella that can be used to block malicious domains. It also discusses how the Next Generation IPS/NGFW from Cisco called Firepower can help discover vulnerabilities, detect malware, and tune signatures based on network context.