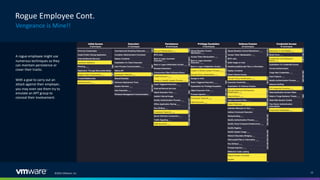
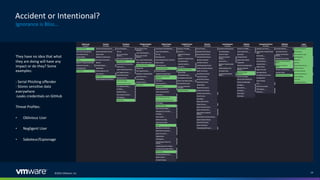
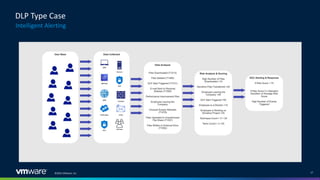
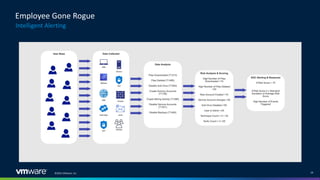
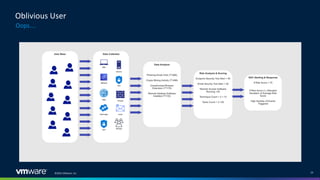
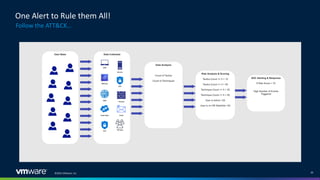
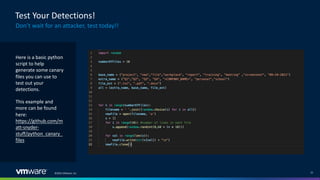
The document discusses insider threats in organizations and how to utilize the MITRE ATT&CK framework to identify and mitigate them. It categorizes insider threats into types such as oblivious users, negligent users, and malicious insiders, highlighting the importance of understanding each profile to build intelligent detections. The document emphasizes the necessity of creating tailored insider threat programs, collaborating with legal and HR departments, and continuously testing detection methods.