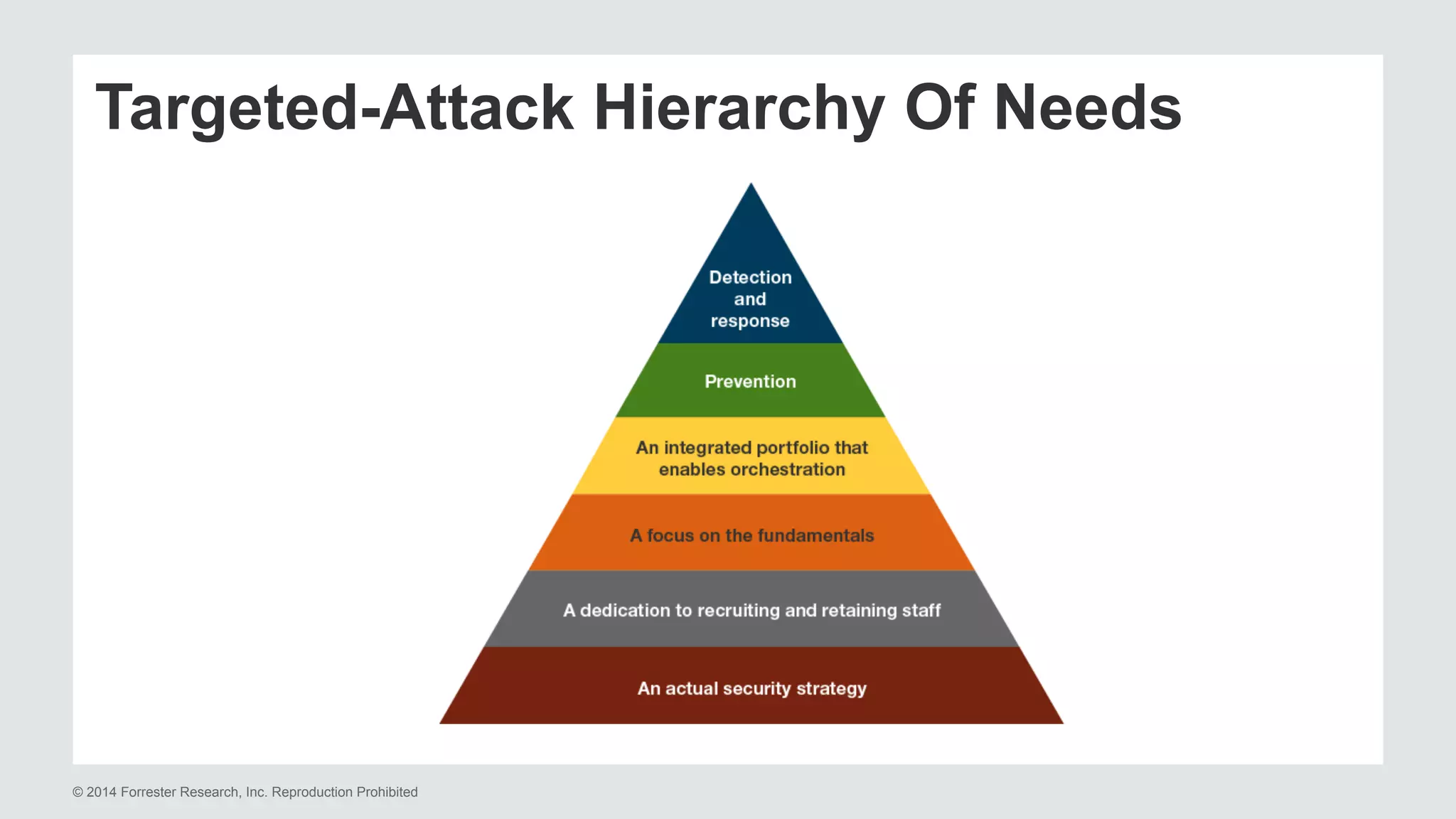
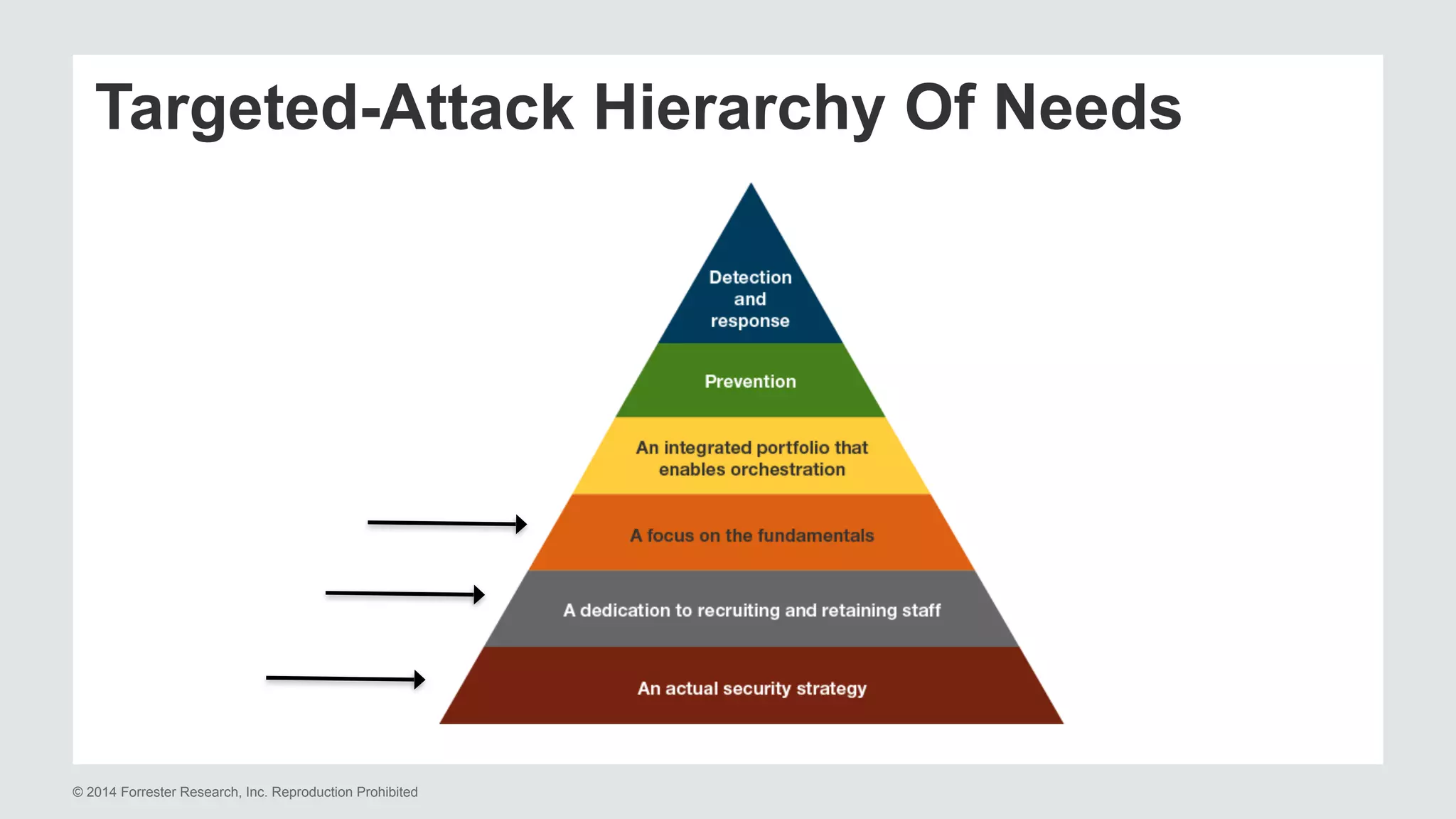
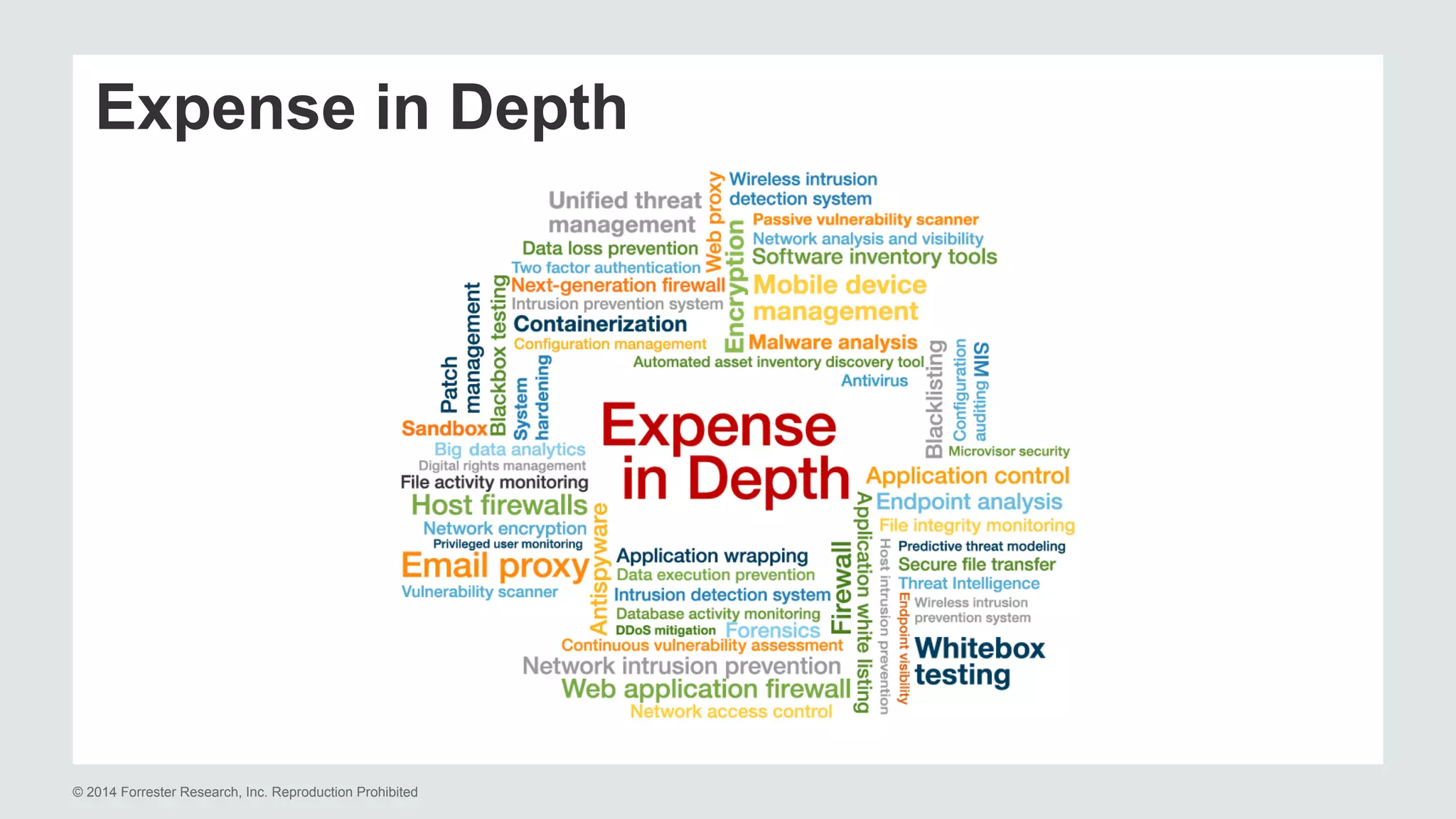
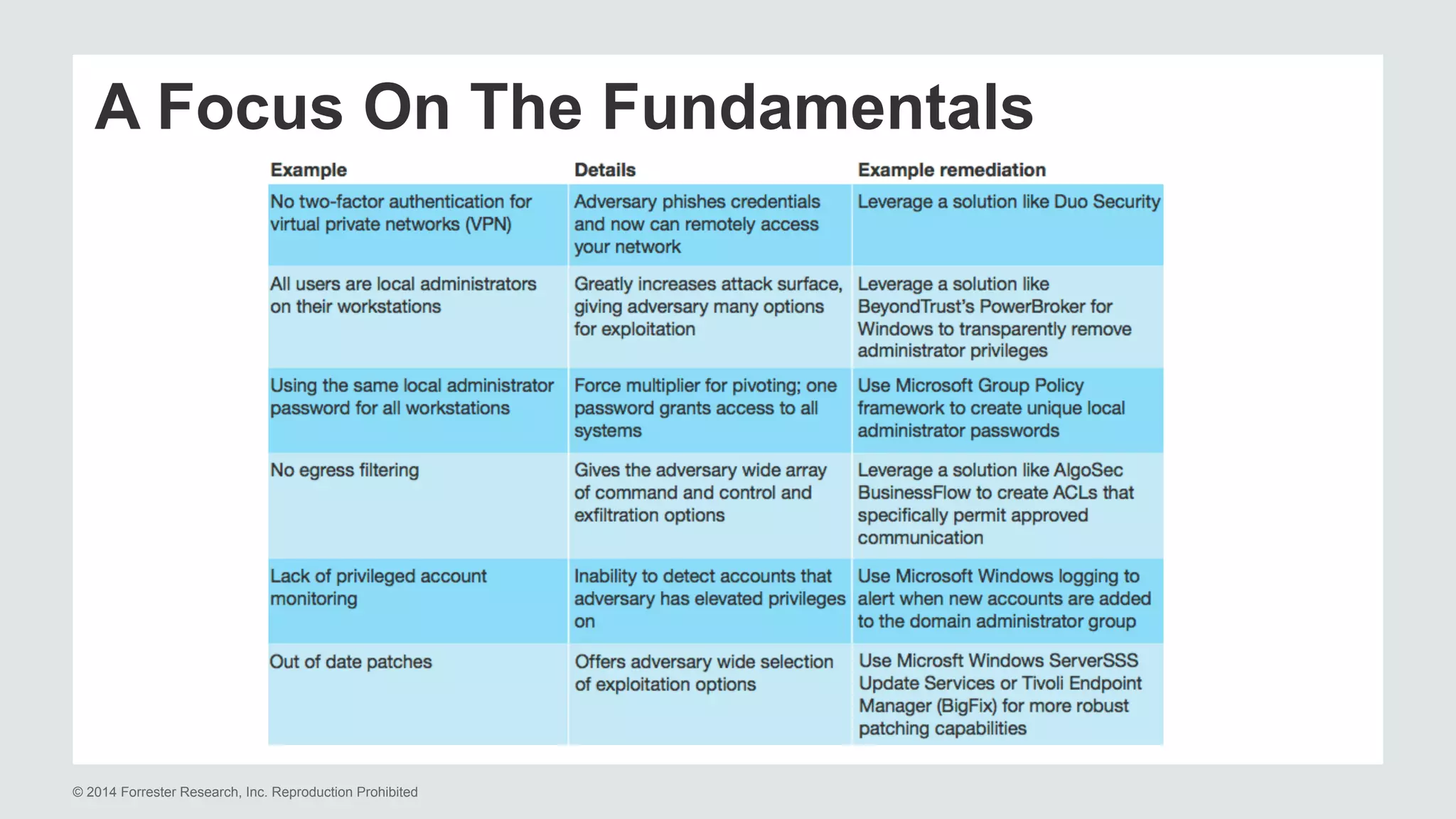
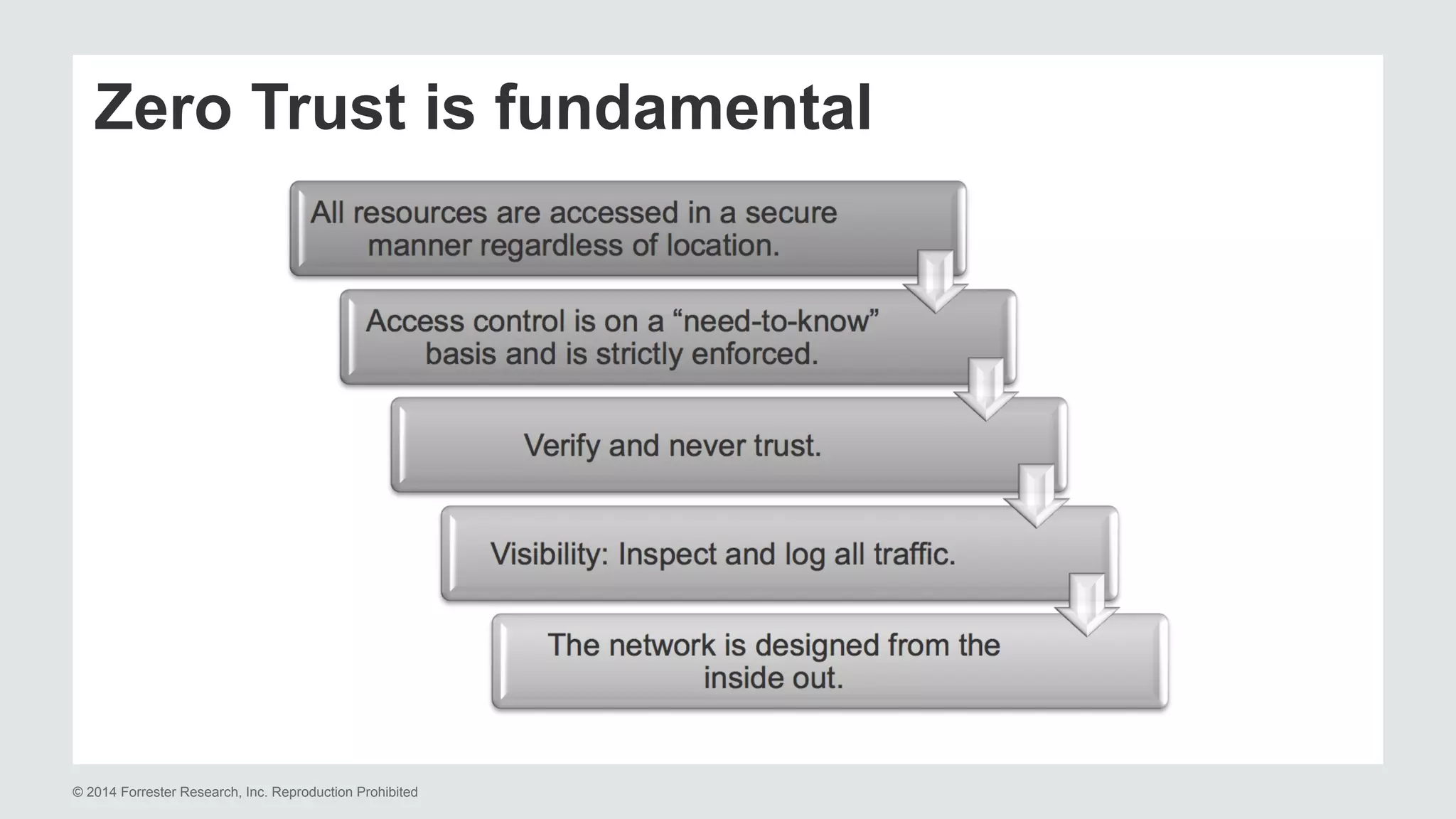
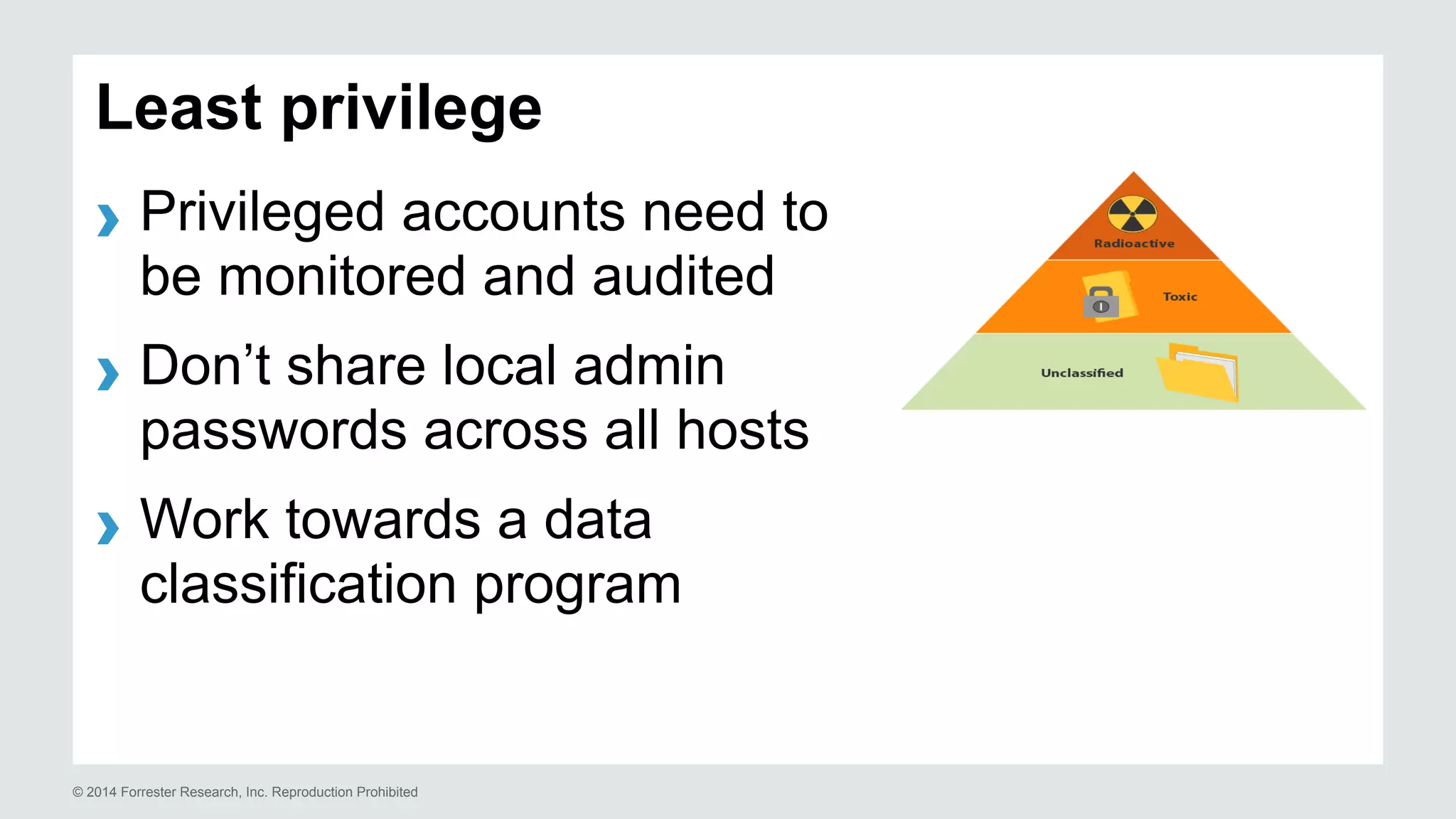
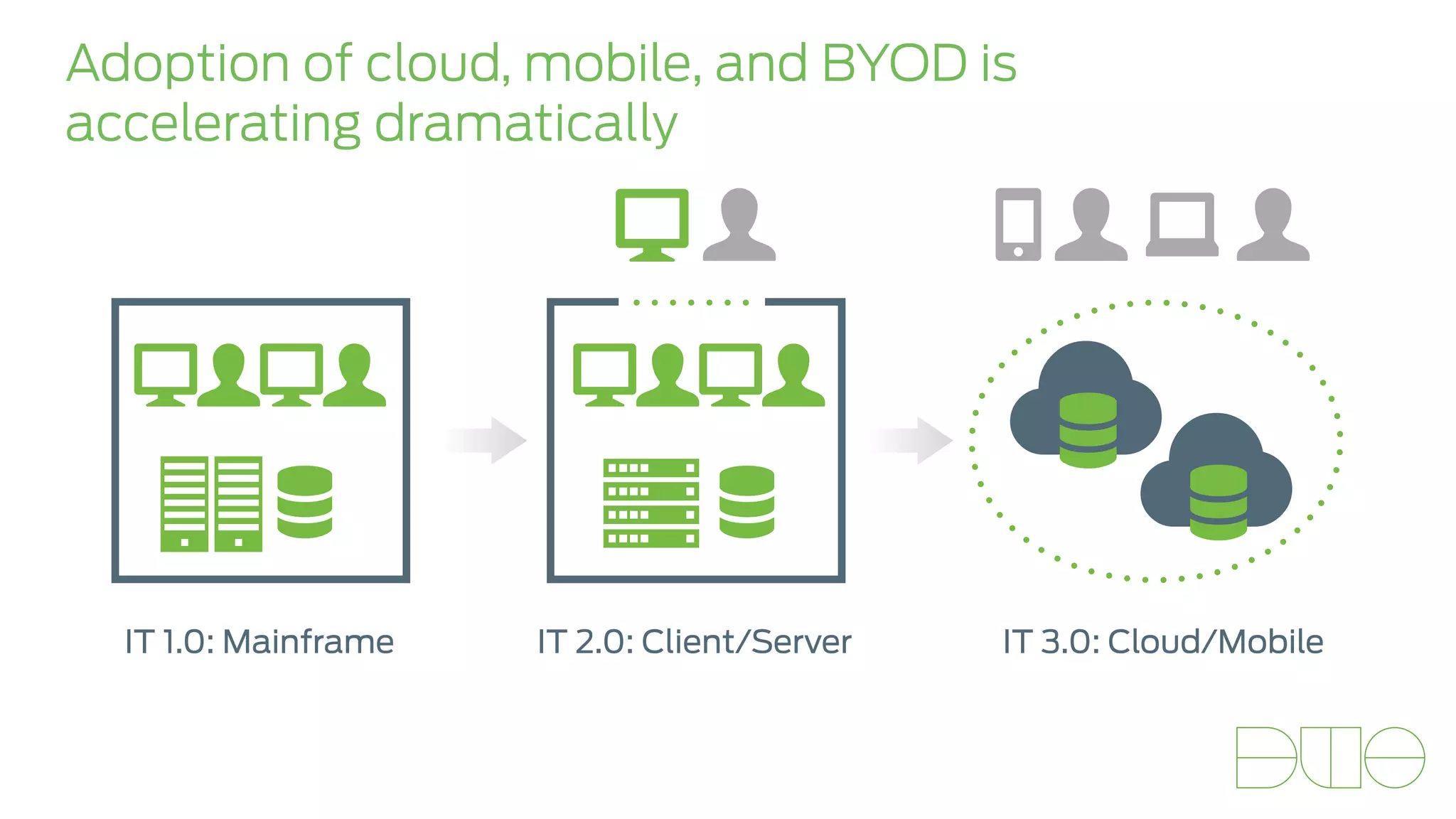
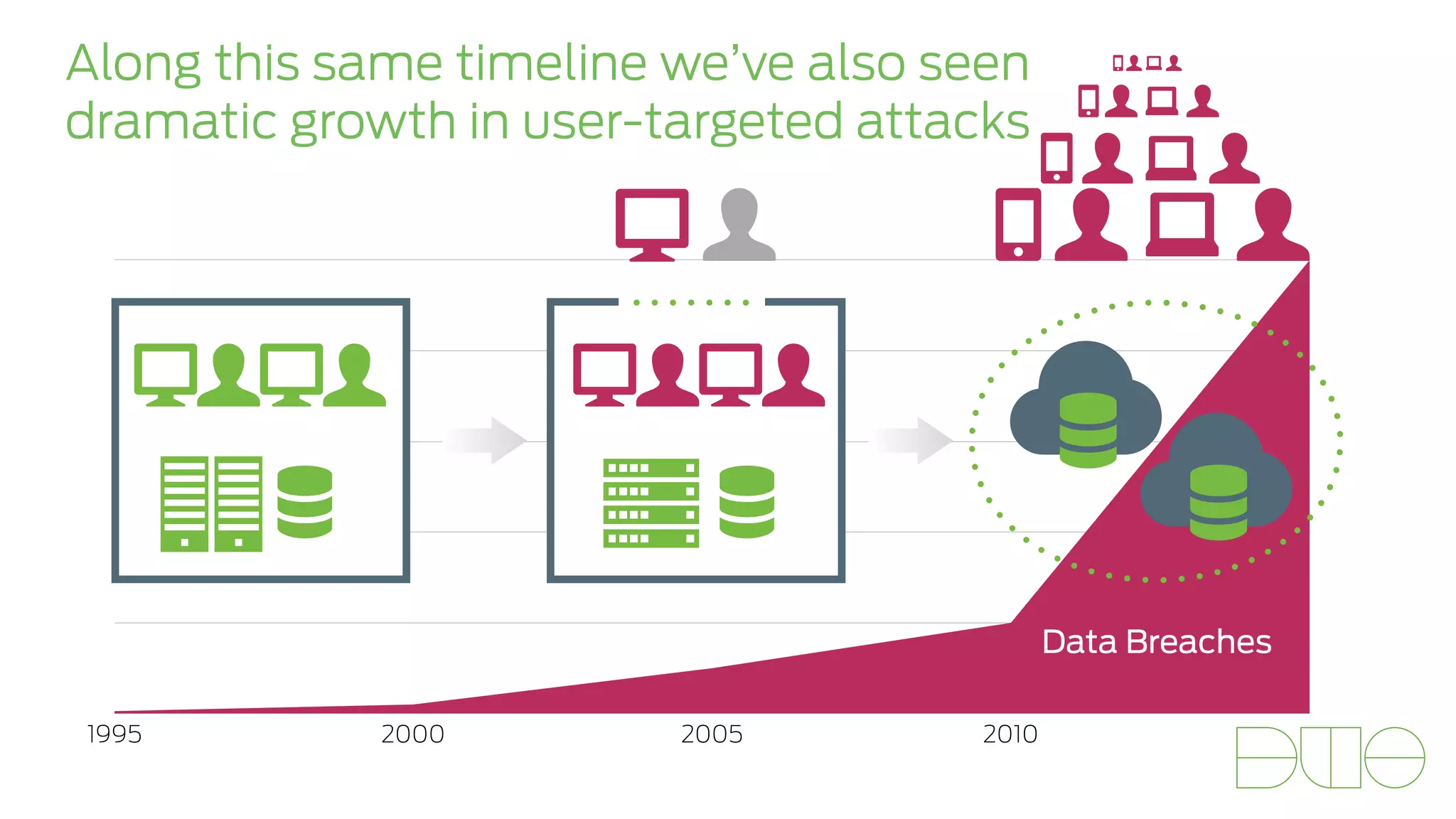
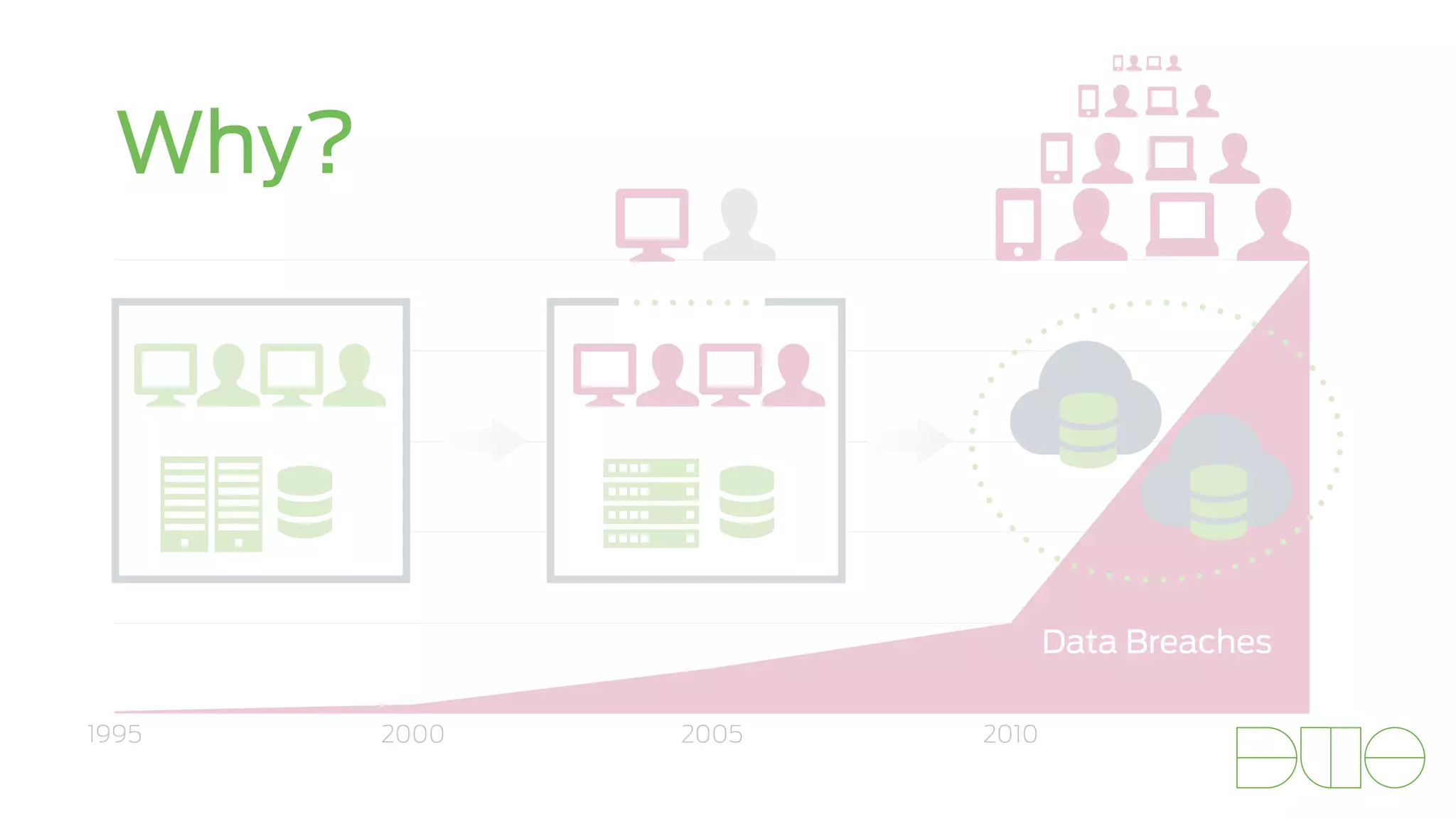
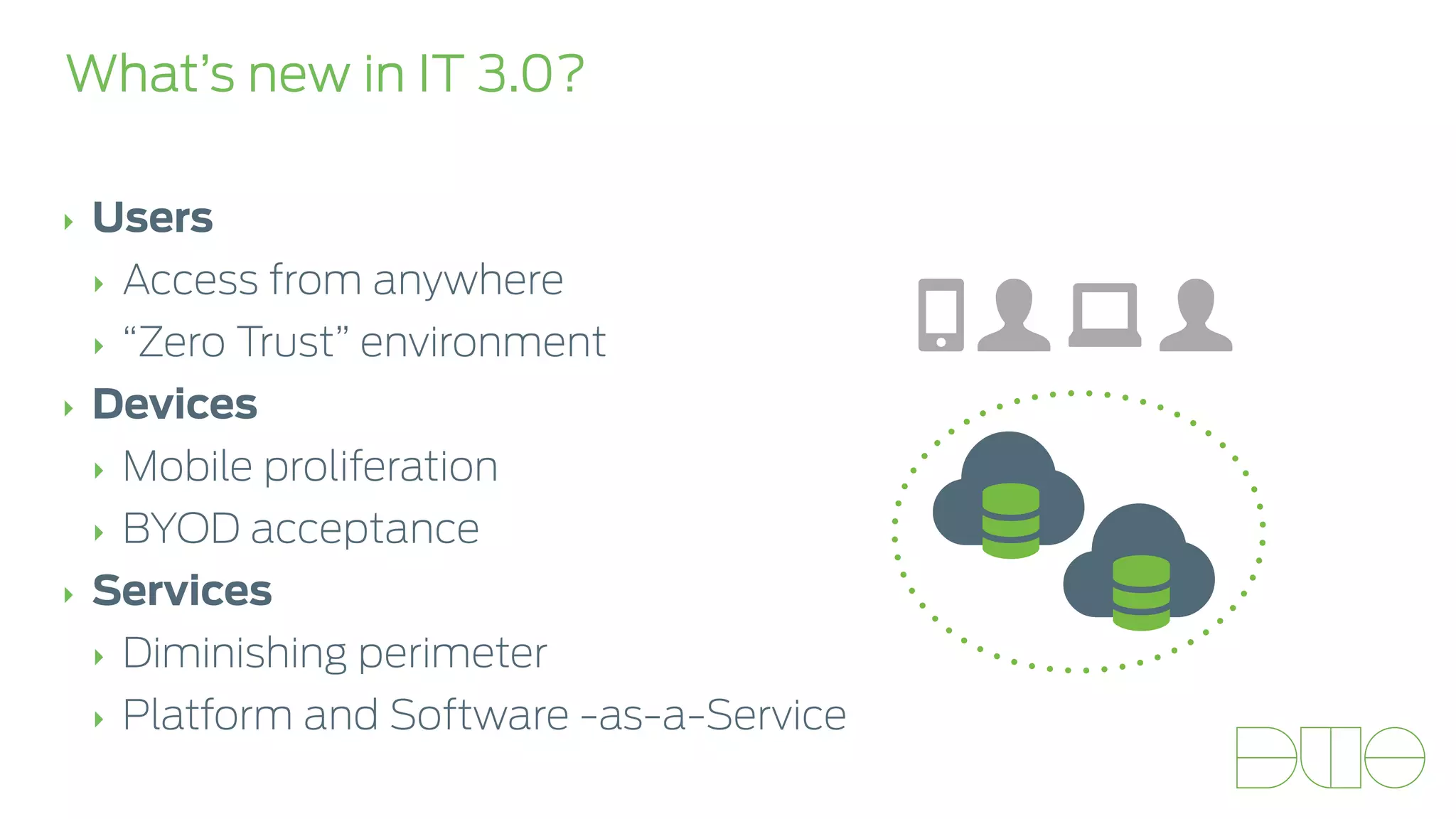
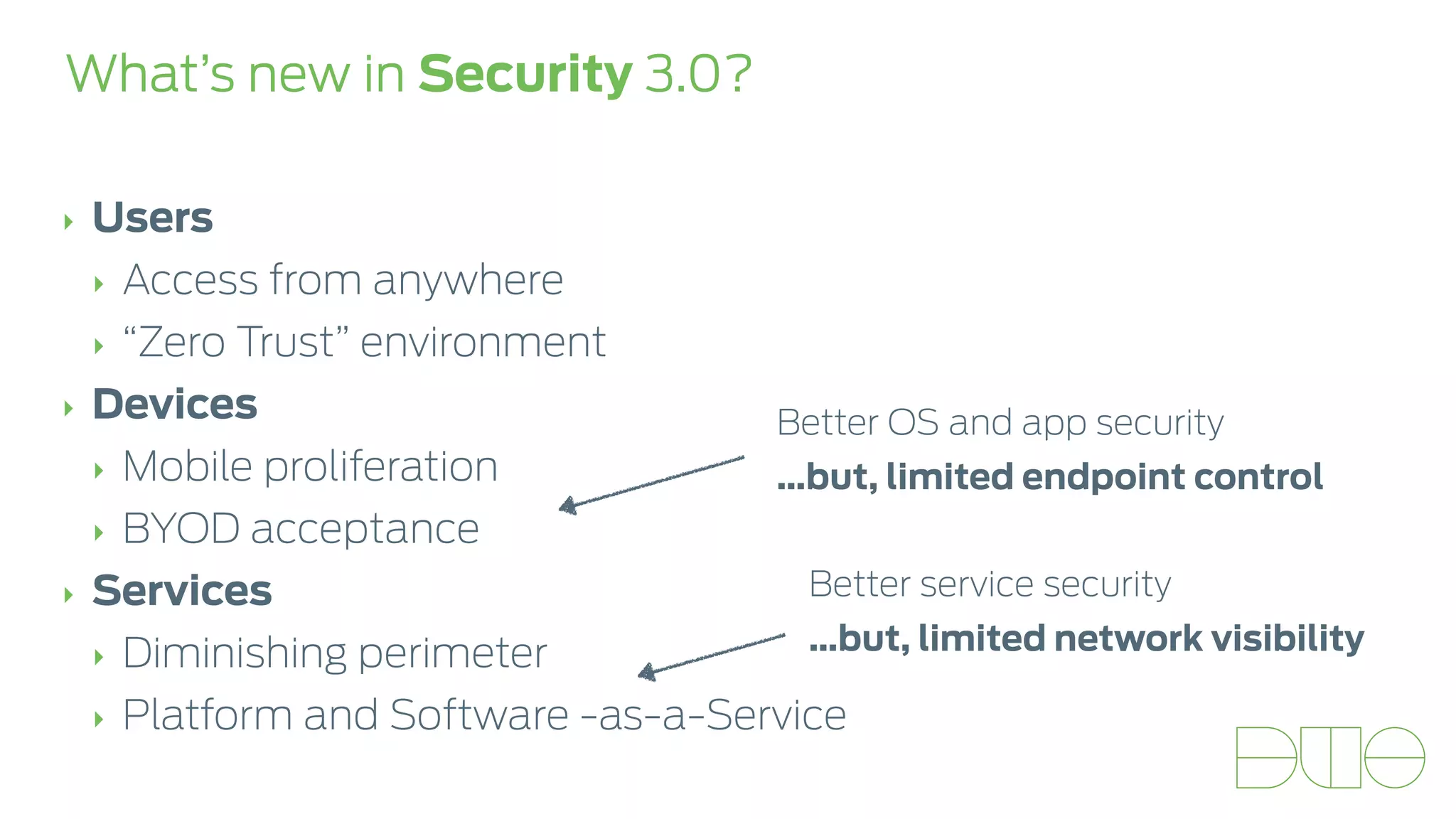
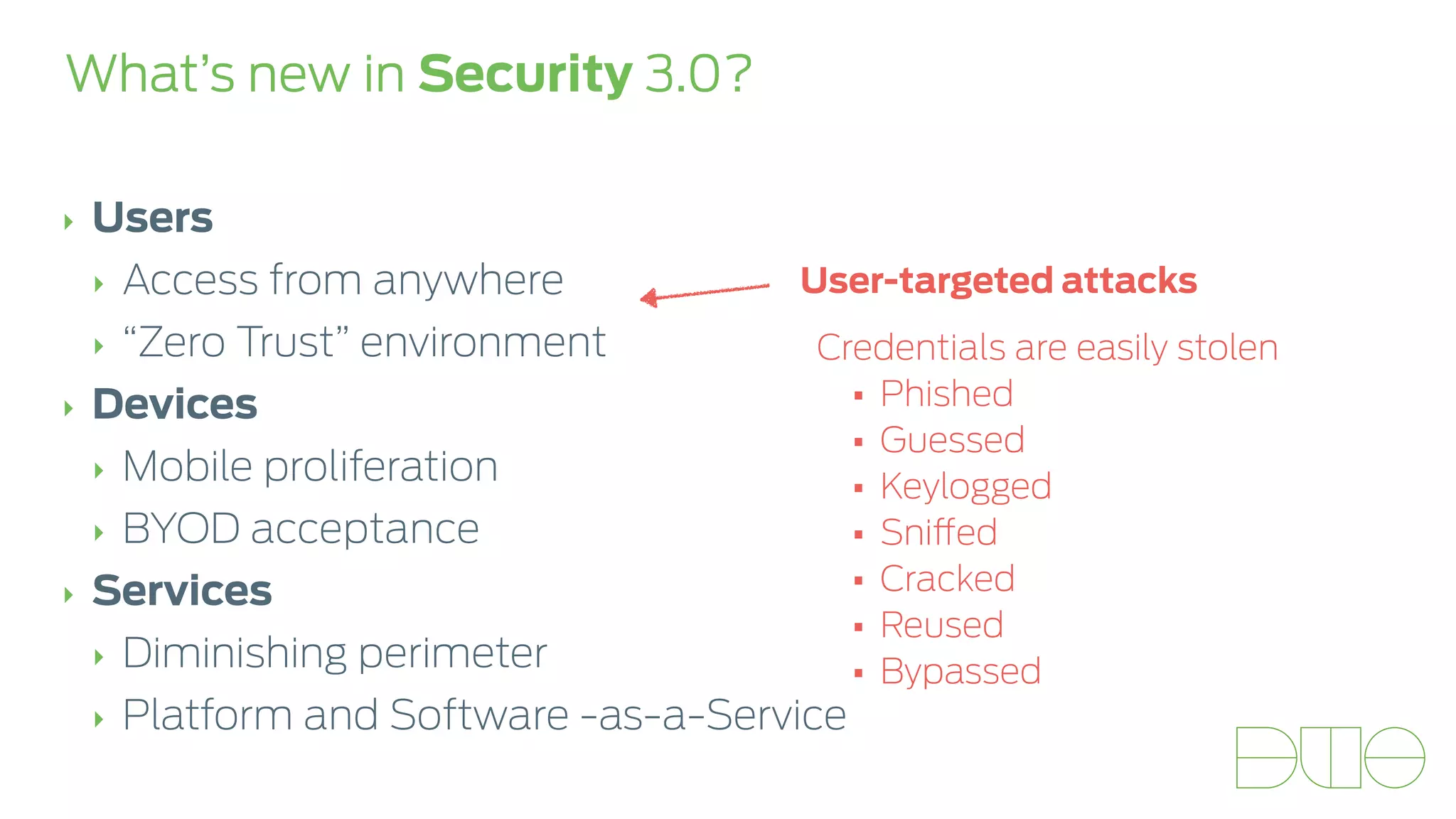
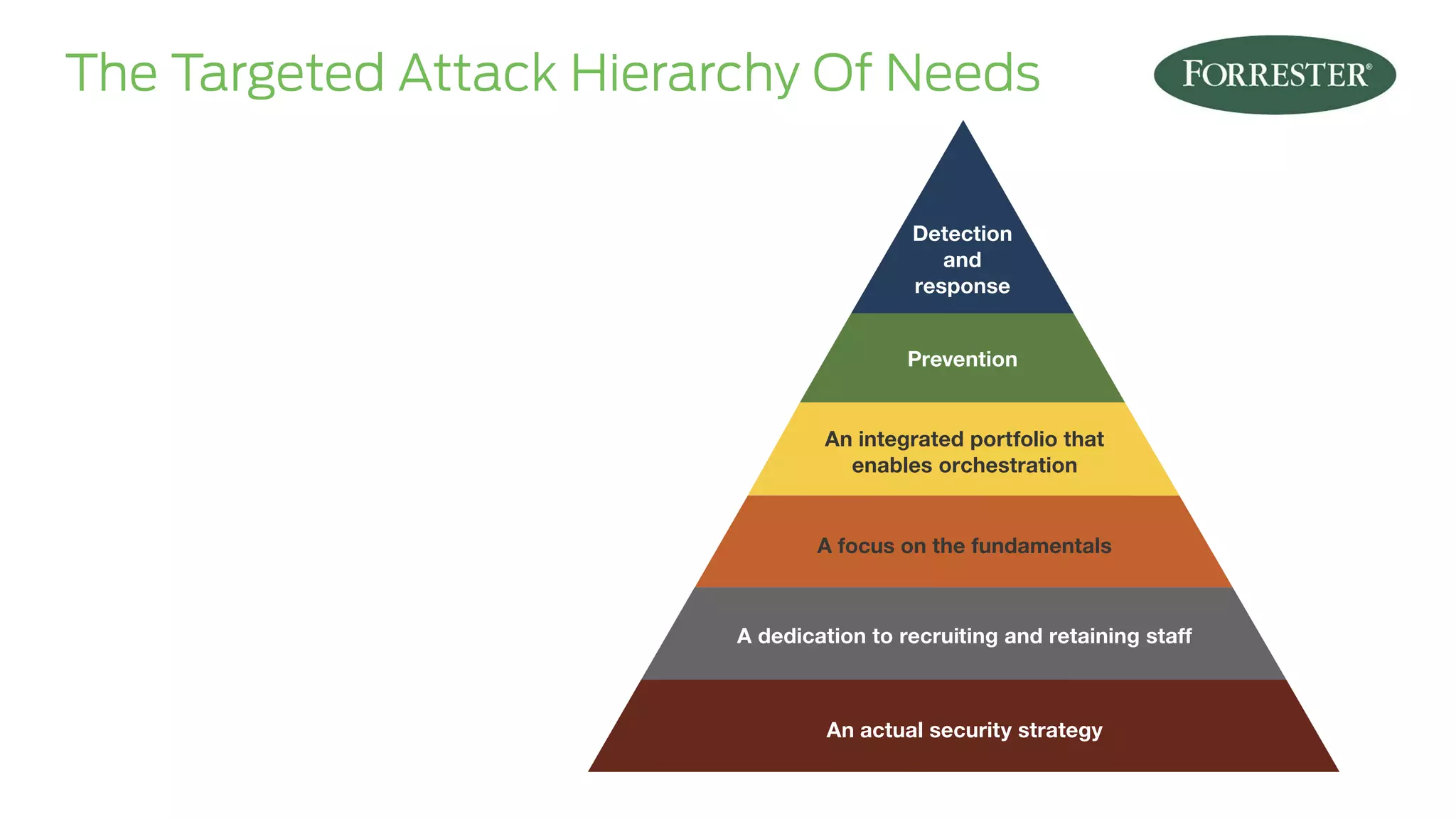
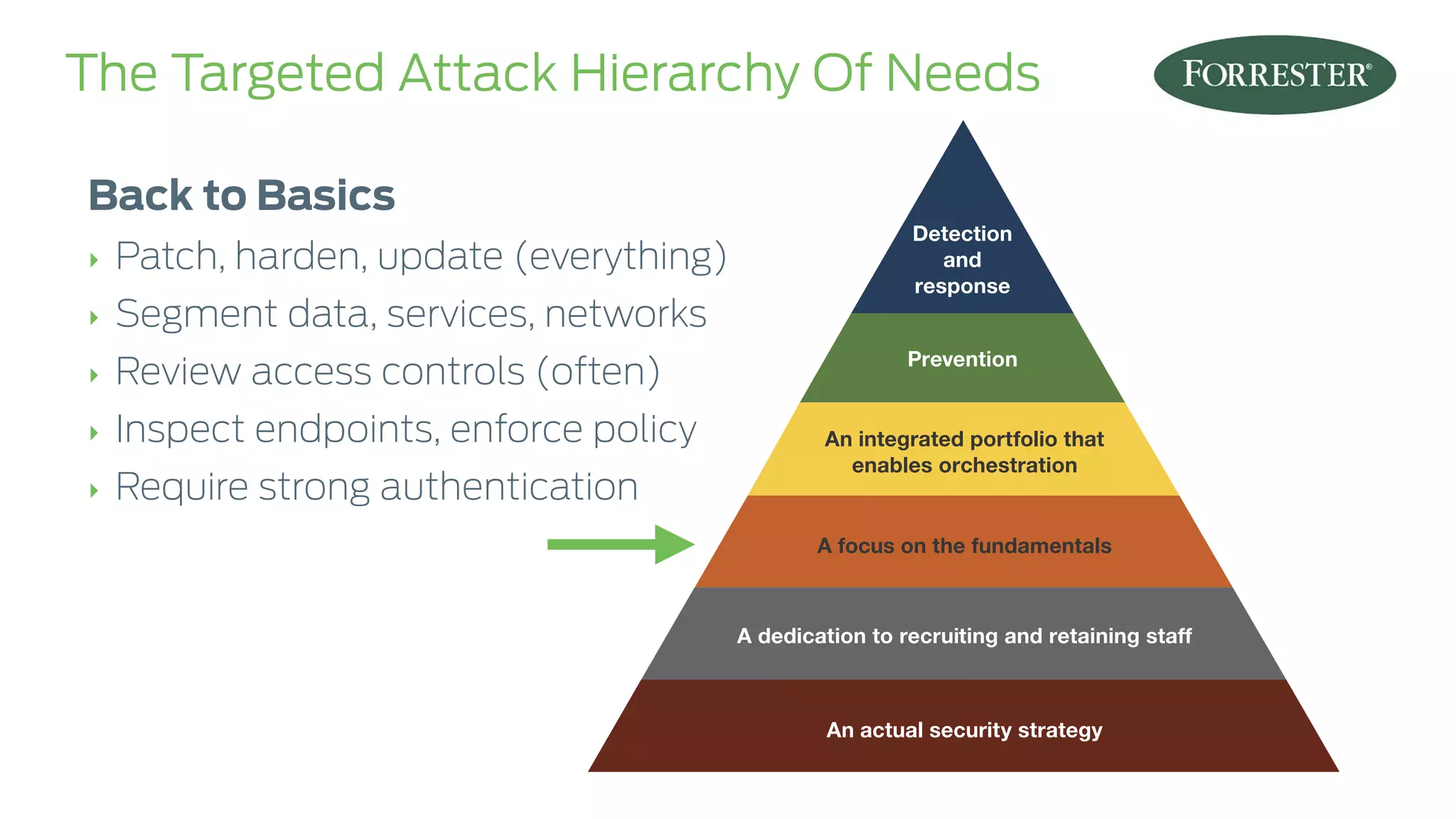
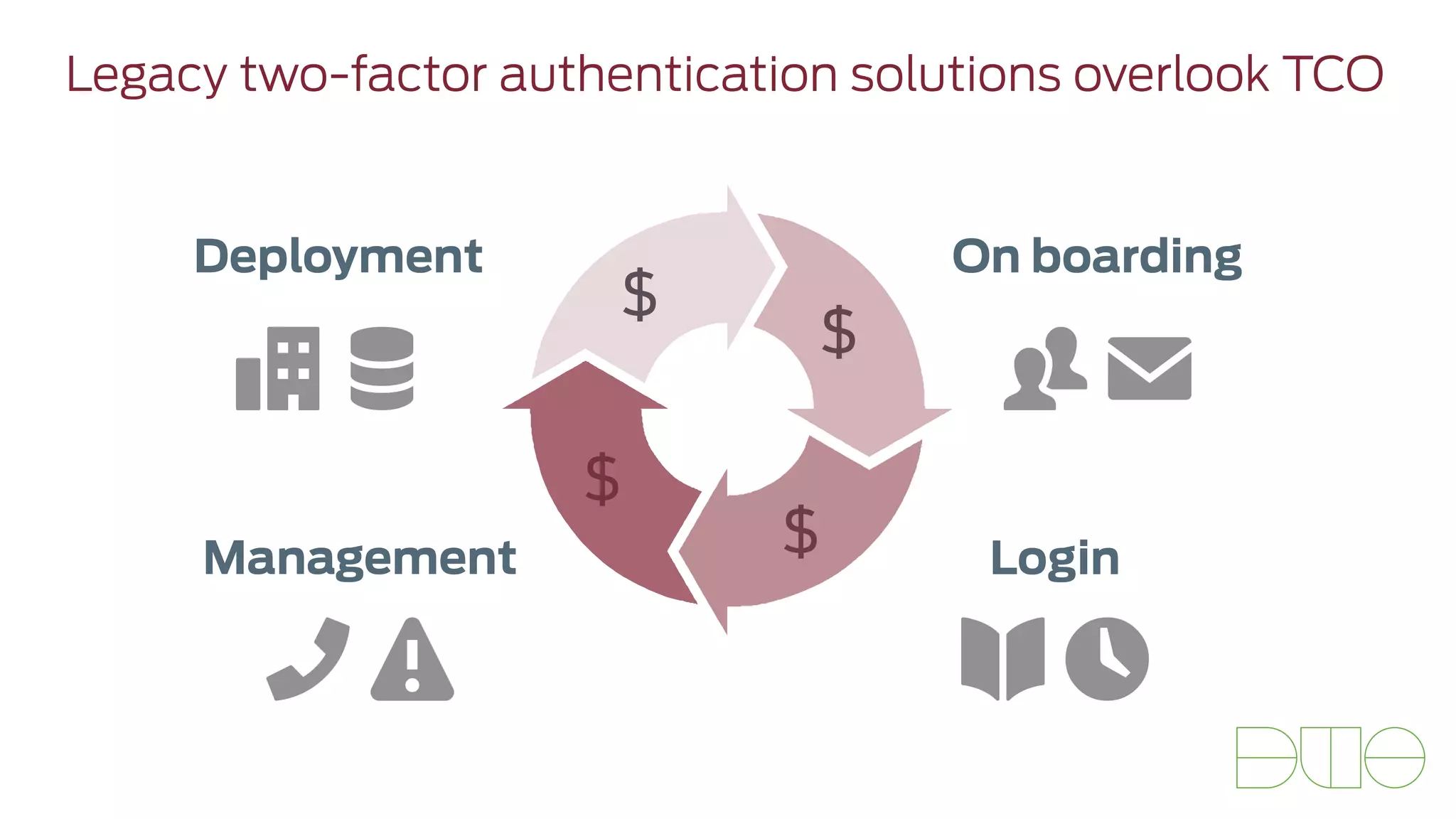
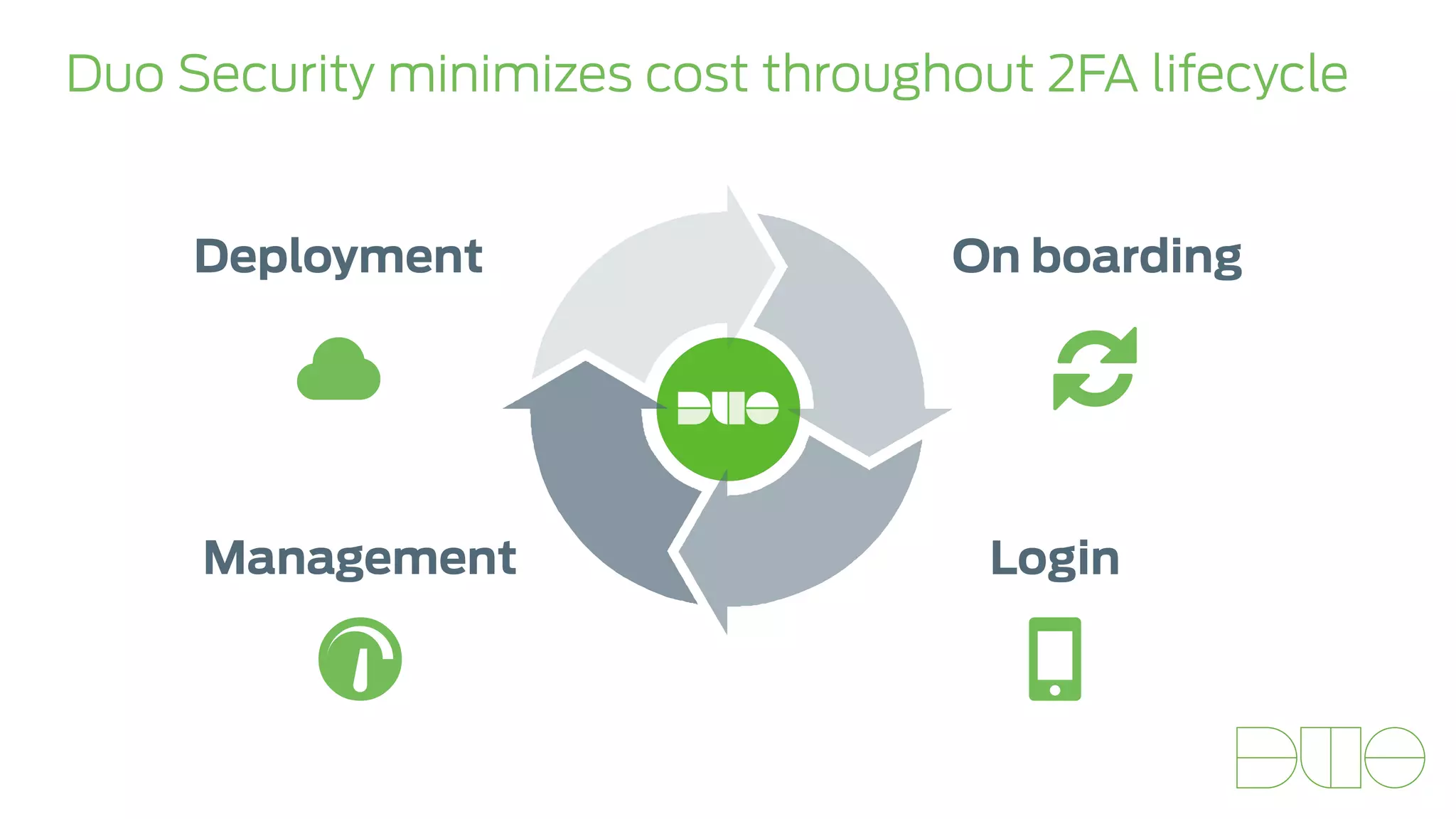
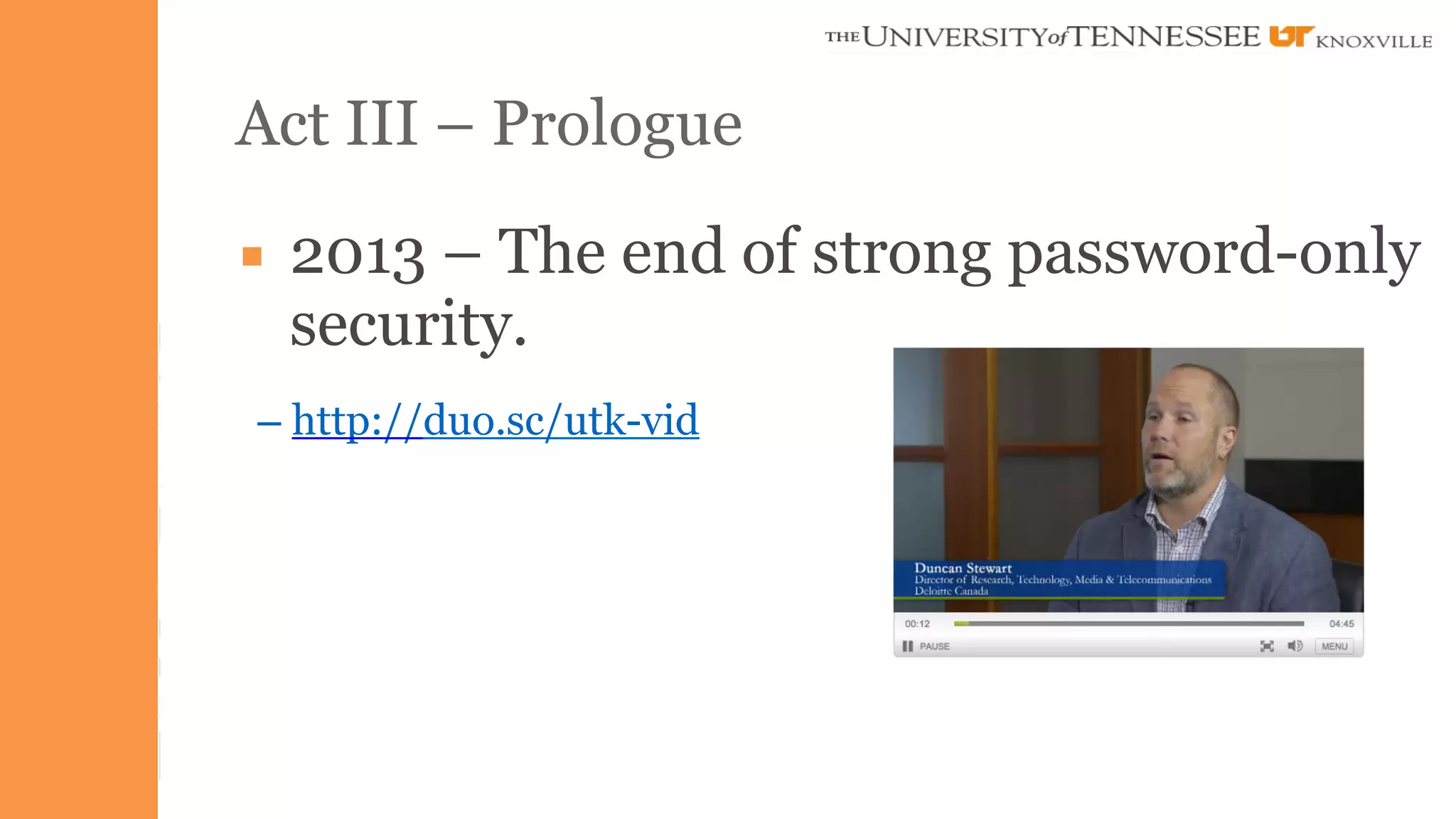
The document presents insights on stopping targeted attacks and avoiding 'expense in depth' through strong authentication, featuring speakers from Forrester Research, Duo Security, and the University of Tennessee. Key topics include the necessity of a robust security strategy, the importance of strong authentication, and the implementation of multi-factor authentication strategies. The discussion highlights the evolution of security in response to rising user-targeted attacks and emphasizes a zero trust environment as crucial for effective defense.