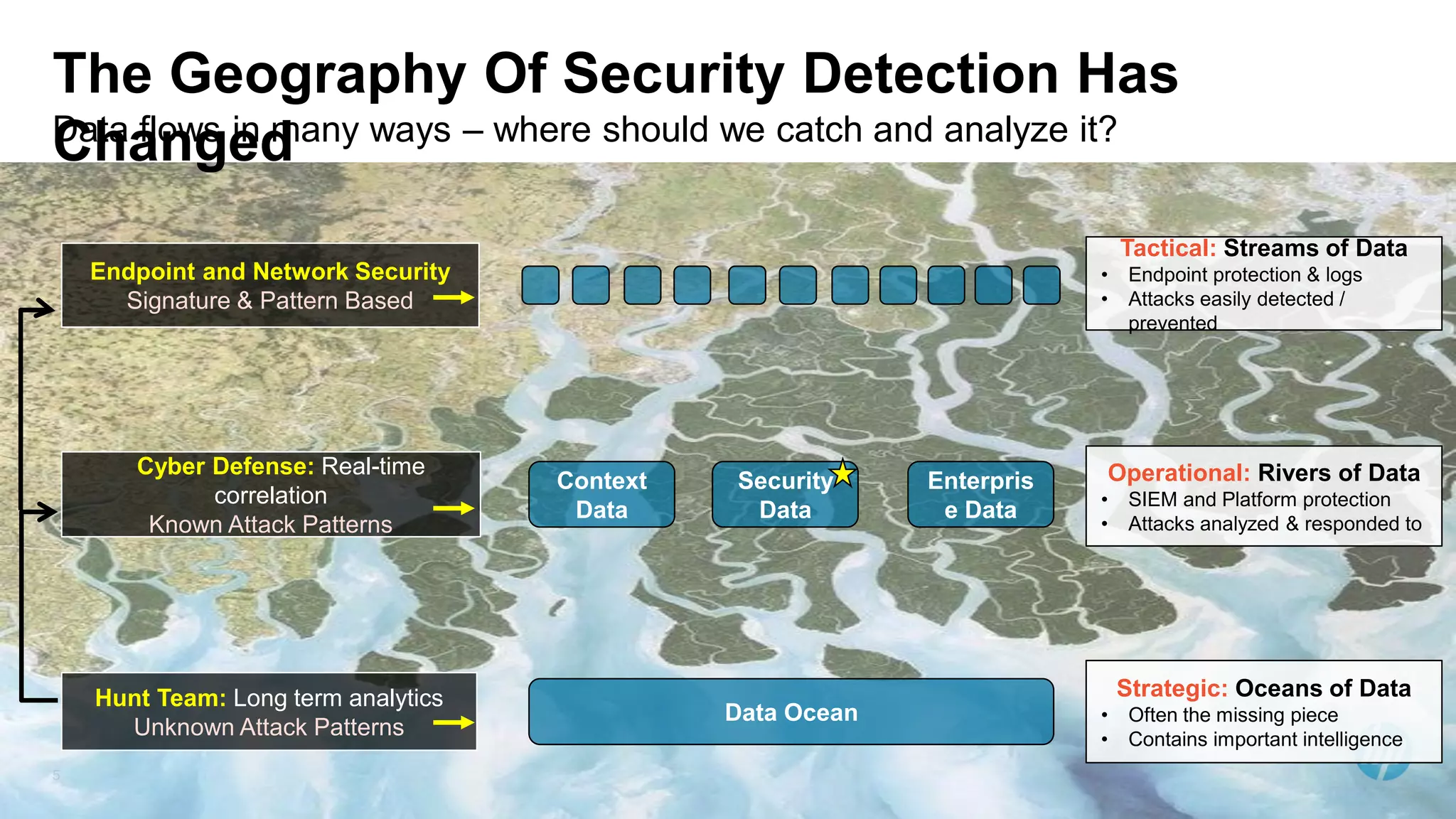
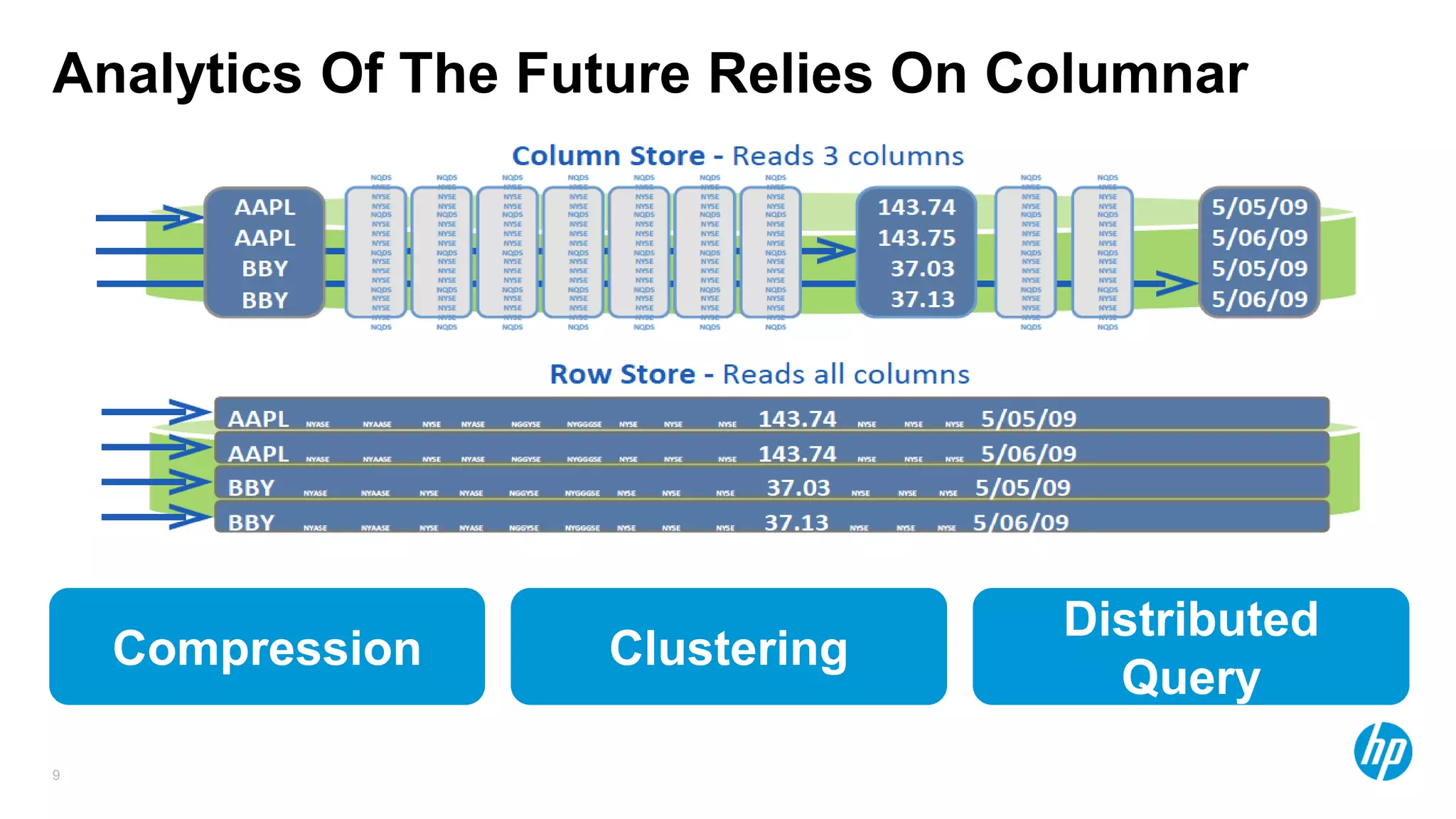
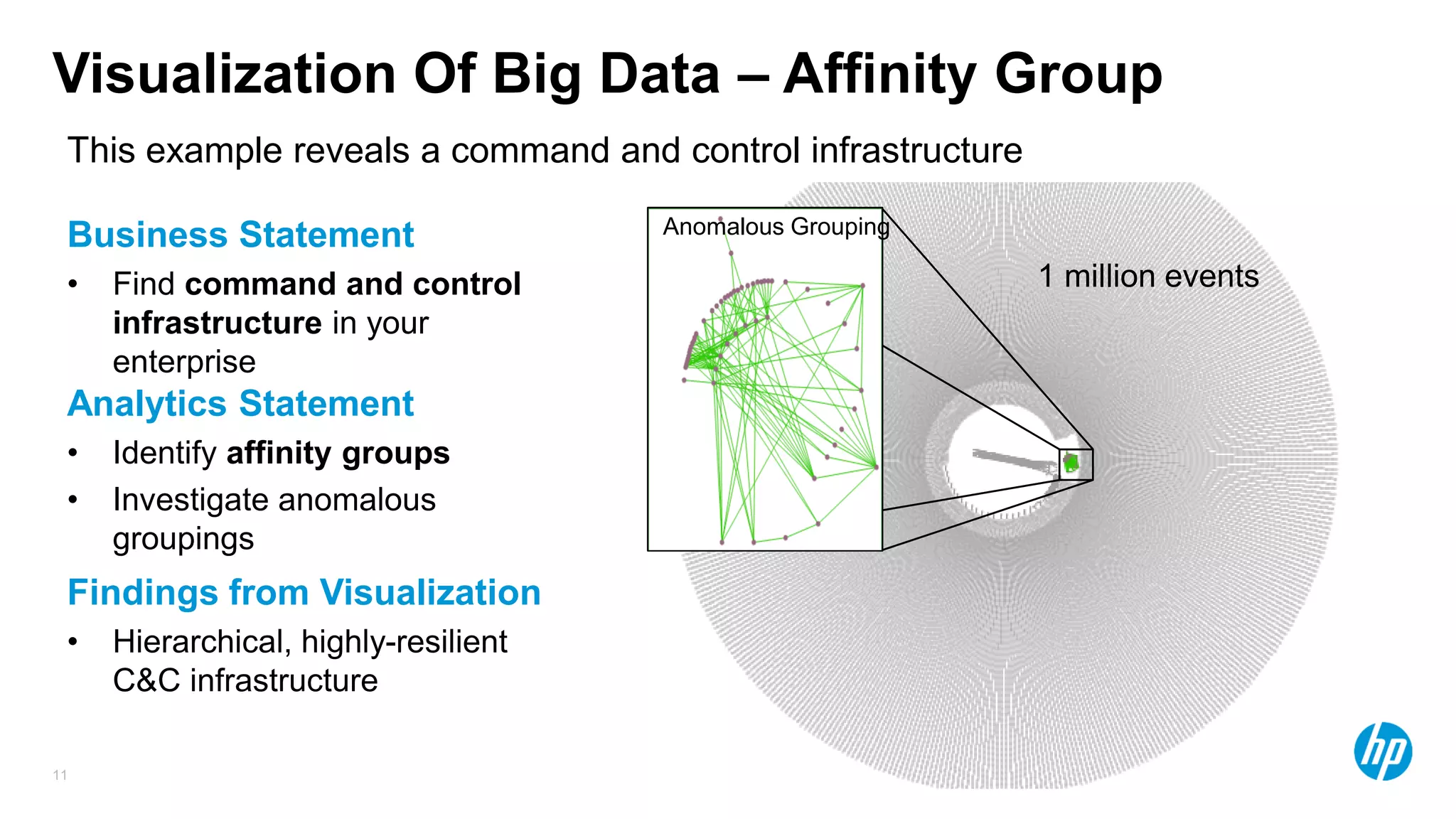
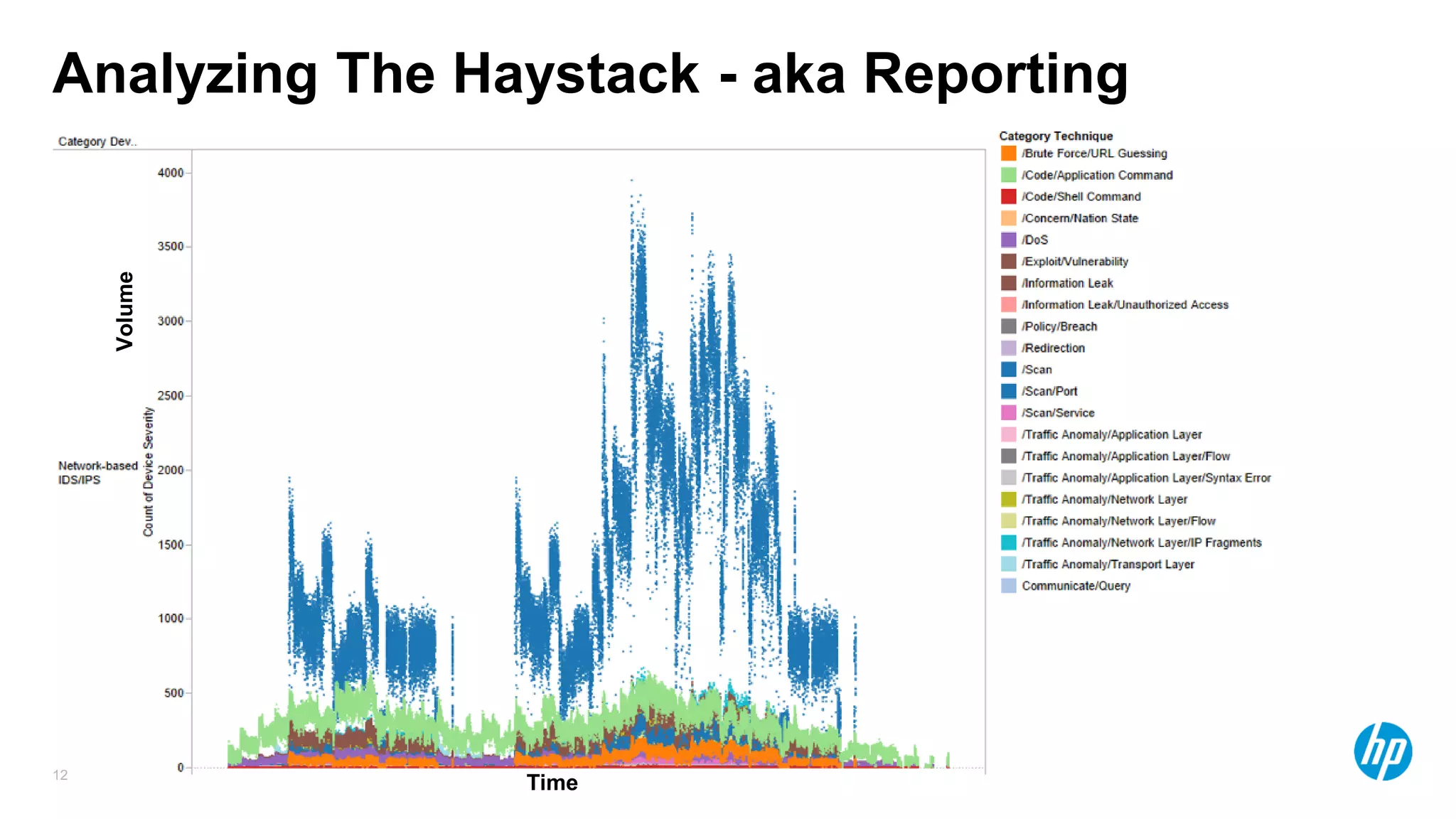
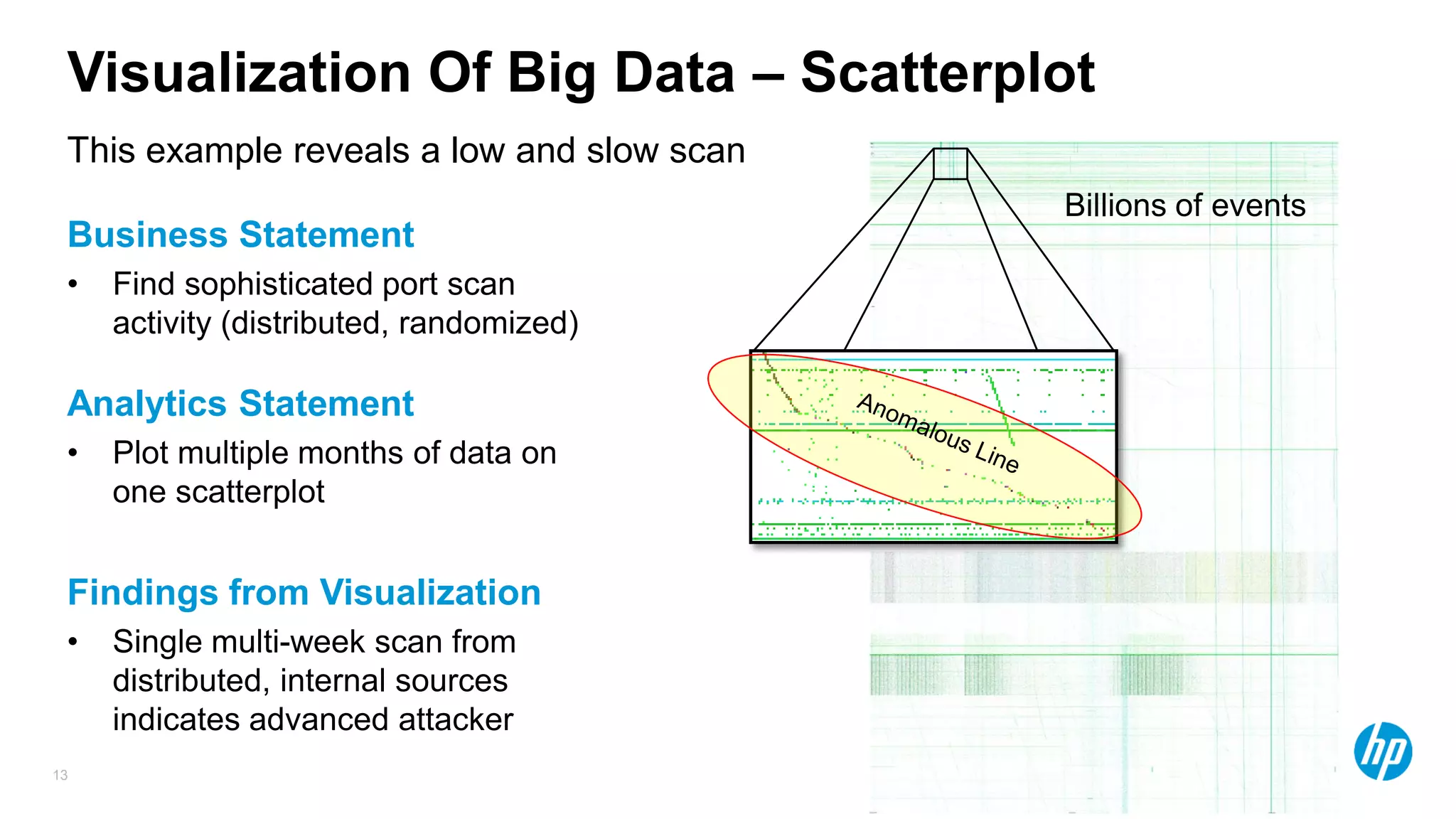
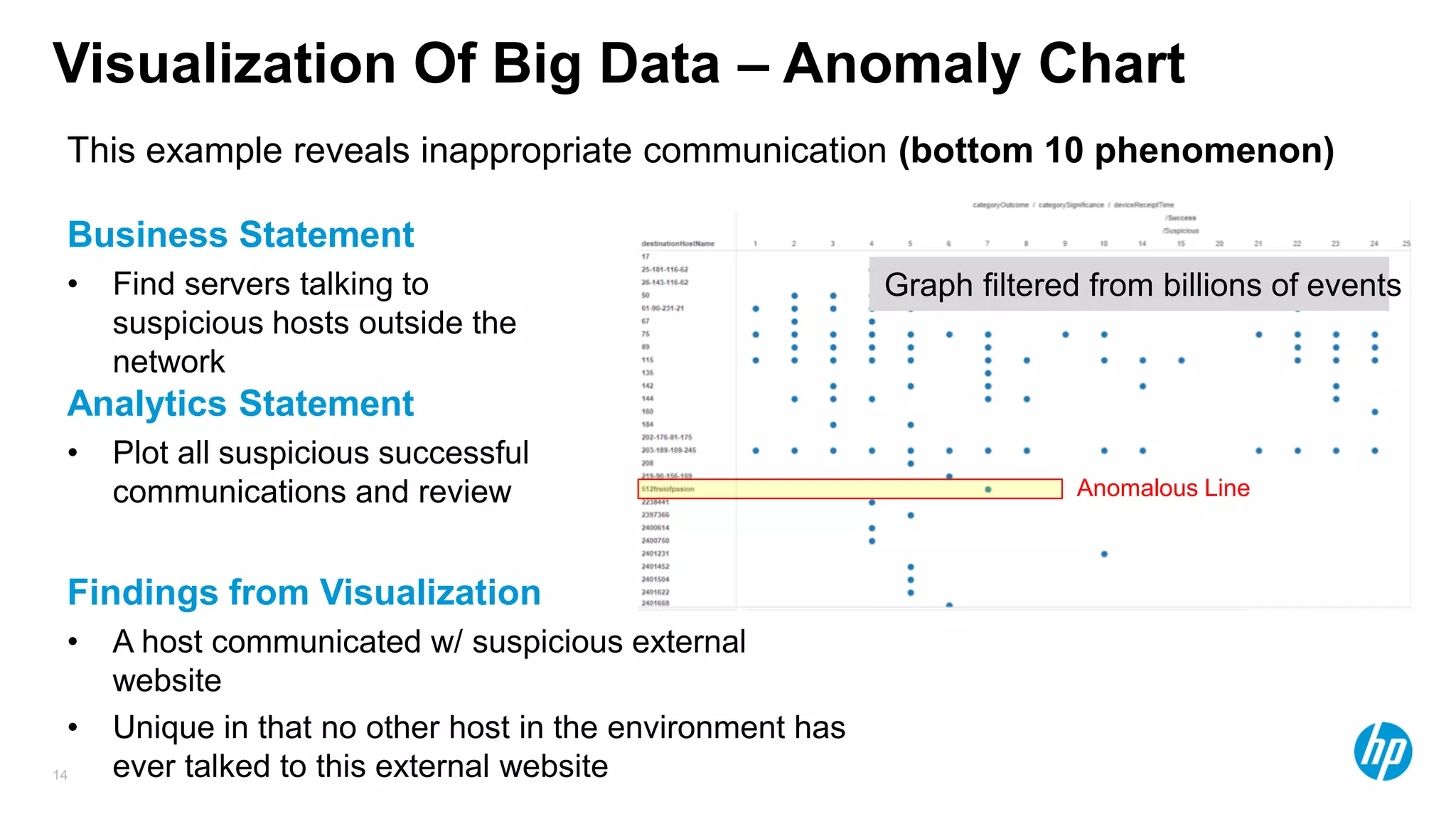
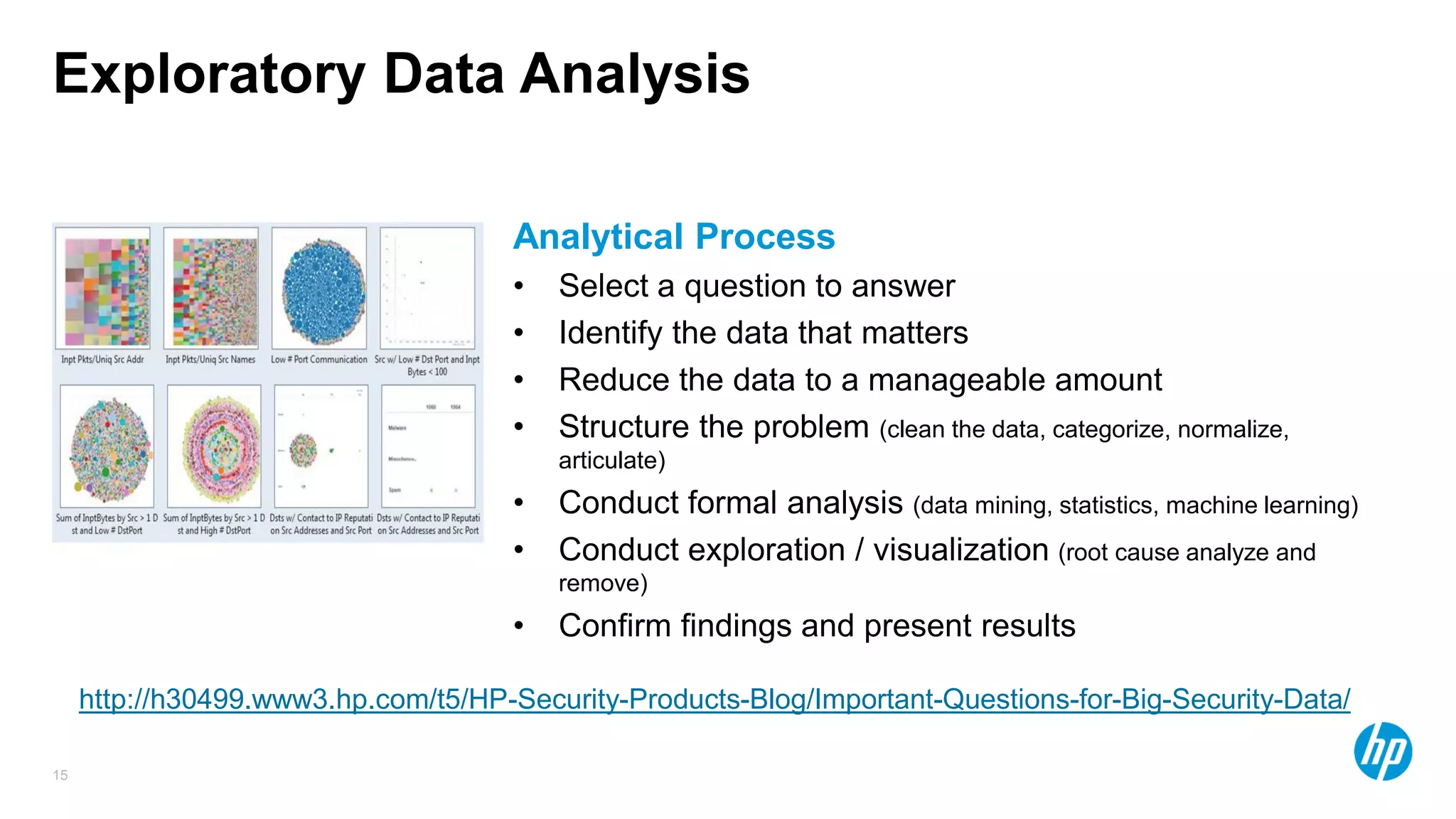
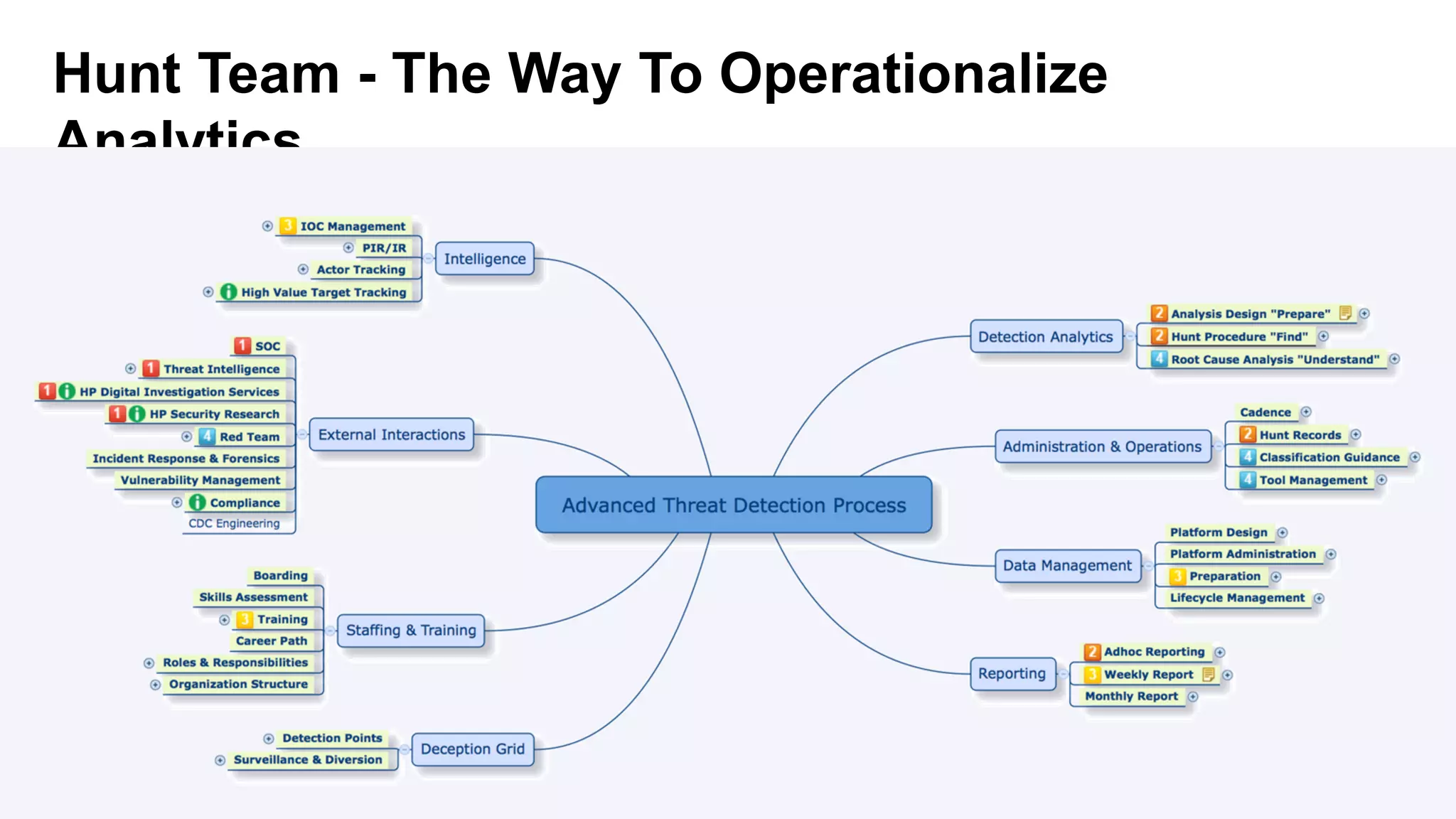
The document discusses using advanced analytics and visualization techniques to more effectively detect security threats within large amounts of data. It describes how traditional detection methods are unable to catch threats that behave in novel or subtle ways. The document advocates applying techniques like correlation, clustering, affinity grouping, and statistical analysis to organize and extract useful intelligence from security data oceans. This can help identify more sophisticated threats that avoid easy detection. Visualization is also presented as a way to explore anomalies and reveal hidden patterns within big security data.