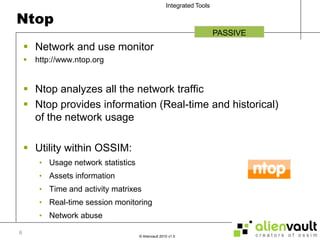
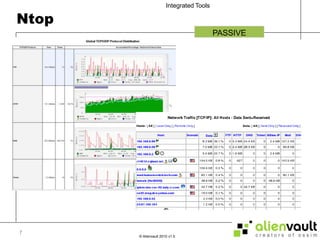
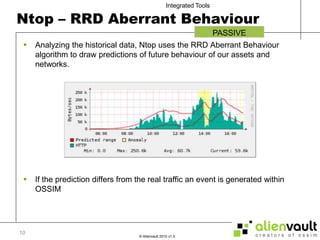
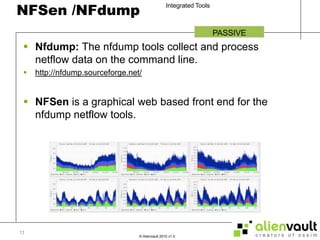
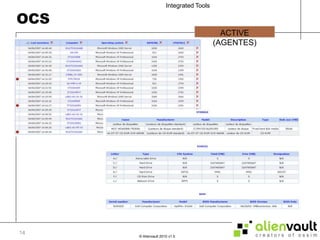
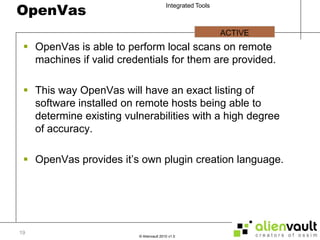
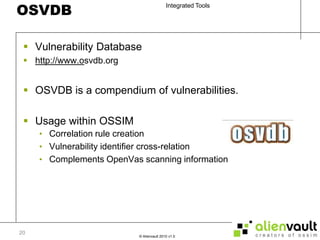
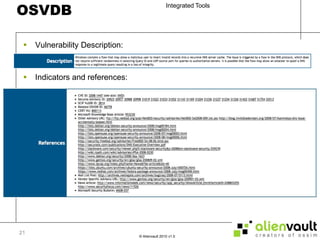
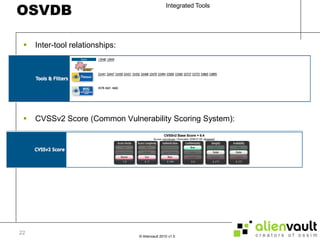
The document discusses various tools that can be integrated within the AlienVault USM platform. It categorizes the tools as either active or passive. Active tools generate their own network traffic while passive tools analyze existing network traffic without generating any themselves. It then provides details on the purpose and functionality of each tool, including Snort for intrusion detection, Ntop for network monitoring, Nagios for availability monitoring, OpenVas for vulnerability scanning, and others. It explains how each tool can be used within the AlienVault platform.

![SnortPASSIVEPolicy violationsalert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:"ET POLICY Megaupload file download service access"; flow:to_server,established; content:"GET "; depth: 4; uricontent:"/?d="; content:"|0d 0a|Host\: "; content:"megaupload.com"; within:25; nocase; classtype:policy-violation; reference:url,doc.emergingthreats.net/2009301; reference:url,www.emergingthreats.net/cgi-bin/cvsweb.cgi/sigs/POLICY/POLICY_Download_Services; sid:2009301; rev:2;)alert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:"ET POLICY Porn-Sports-Gambling site designed to bypass restrictions"; flow:to_server,established; content:"Host\:"; nocase; pcre:"/Host\:[^\n]+\.(bodog|bodogbeat|bodognation|bodogmusic|bodogconference|bodogpokerchampionships)\.com/i"; reference:url,www.bodog.com; classtype:policy-violation; reference:url,doc.emergingthreats.net/2003100; reference:url,www.emergingthreats.net/cgi-bin/cvsweb.cgi/sigs/POLICY/POLICY_bodog.com; sid:2003100; rev:4;)Malwarealert tcp $HOME_NET any -> $EXTERNAL_NET $HTTP_PORTS (msg:"ET CURRENT_EVENTS MALWARE Potential Malware Download, rogue antivirus (IAInstall.exe)"; flow:established,to_server; uricontent:"/download/IAInstall.exe"; nocase; classtype:bad-unknown; reference:url,malwareurl.com; reference:url,www.emergingthreats.net/cgi-bin/cvsweb.cgi/sigs/CURRENT_EVENTS/CURRENT_Malwareurl_top_downloads; reference:url,doc.emergingthreats.net/2010447; sid:2010447; rev:2;)alert tcp $EXTERNAL_NET $HTTP_PORTS -> $HOME_NET 1024: (msg:"ET MALWARE 404 Response with an EXE Attached - Likely Malware Drop"; flow:established,from_server; content:"HTTP/1.1 404 Not Found|0d 0a|"; depth:24; content:"|0d 0a 0d 0a|MZ"; distance:0; classtype:attempted-admin; reference:url,doc.emergingthreats.net/bin/view/Main/2009028; reference:url,www.emergingthreats.net/cgi-bin/cvsweb.cgi/sigs/POLICY/POLICY_404_EXE; sid:2009028; rev:2;)4](https://image.slidesharecdn.com/integratedtools-100212031329-phpapp02/85/Integrated-Tools-in-OSSIM-4-320.jpg)