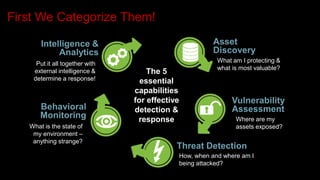
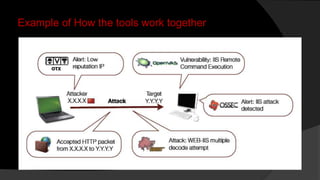
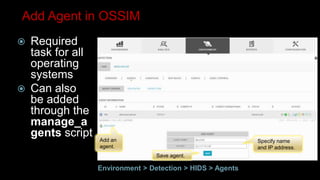
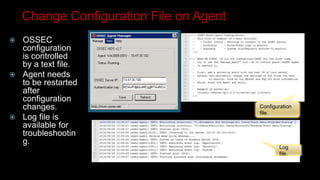
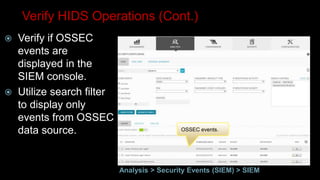
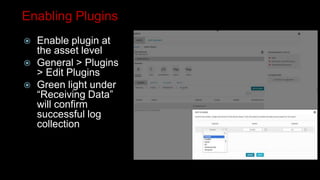
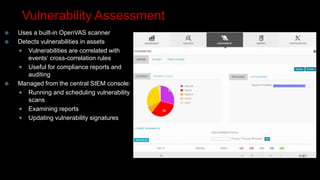
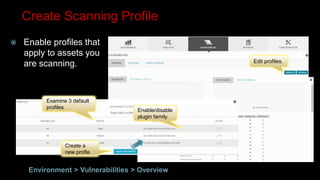
This document provides an overview of deploying and configuring the open source security information and event management (SIEM) solution OSSIM. It discusses setting up OSSEC host-based intrusion detection system agents, configuring syslog forwarding and enabling plugins, performing vulnerability scans of network assets, and demonstrates OSSIM's integrated capabilities. The document emphasizes that prevention alone is not sufficient and that detective controls are also needed to effectively detect and respond to security incidents across the network.