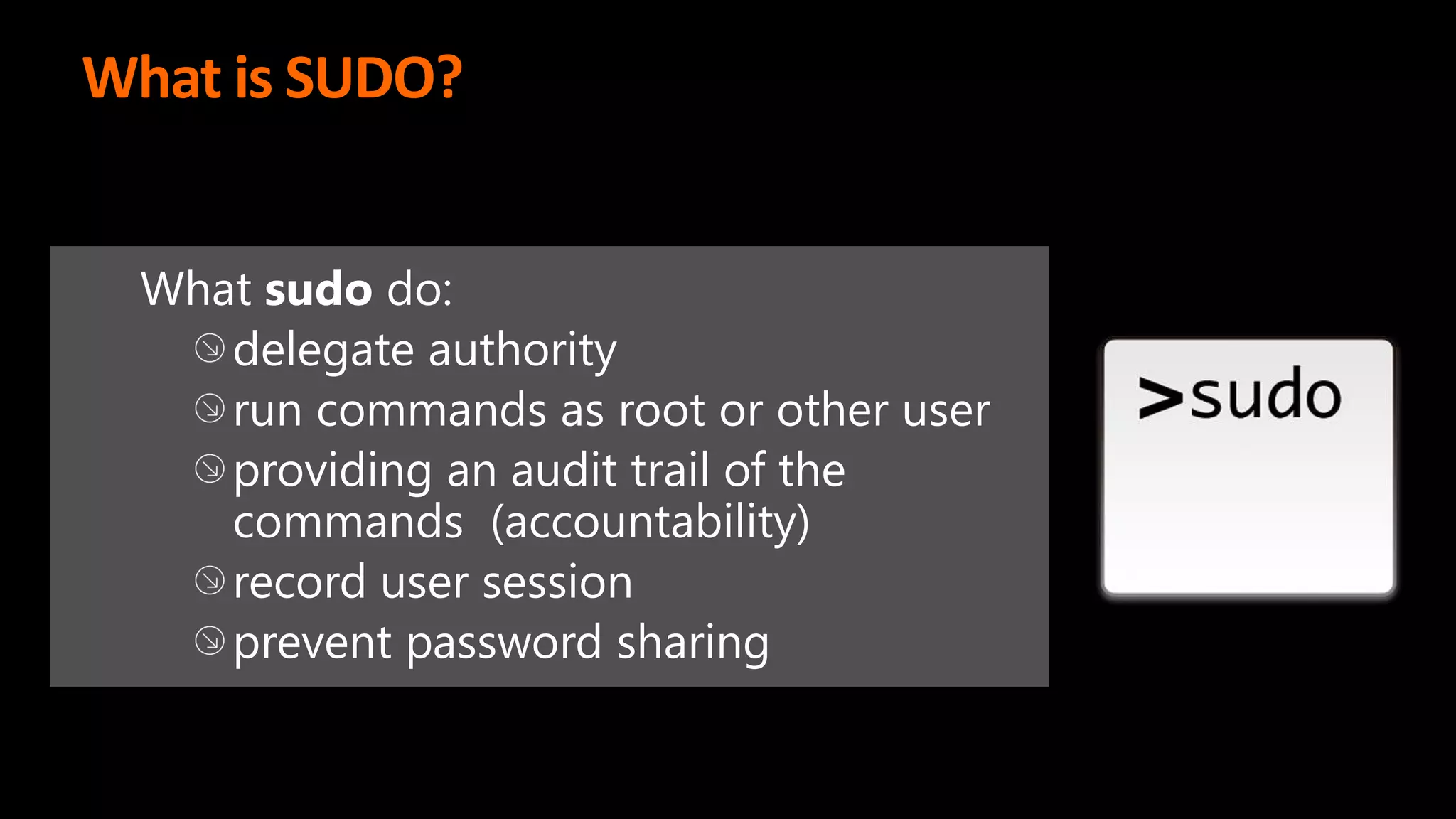
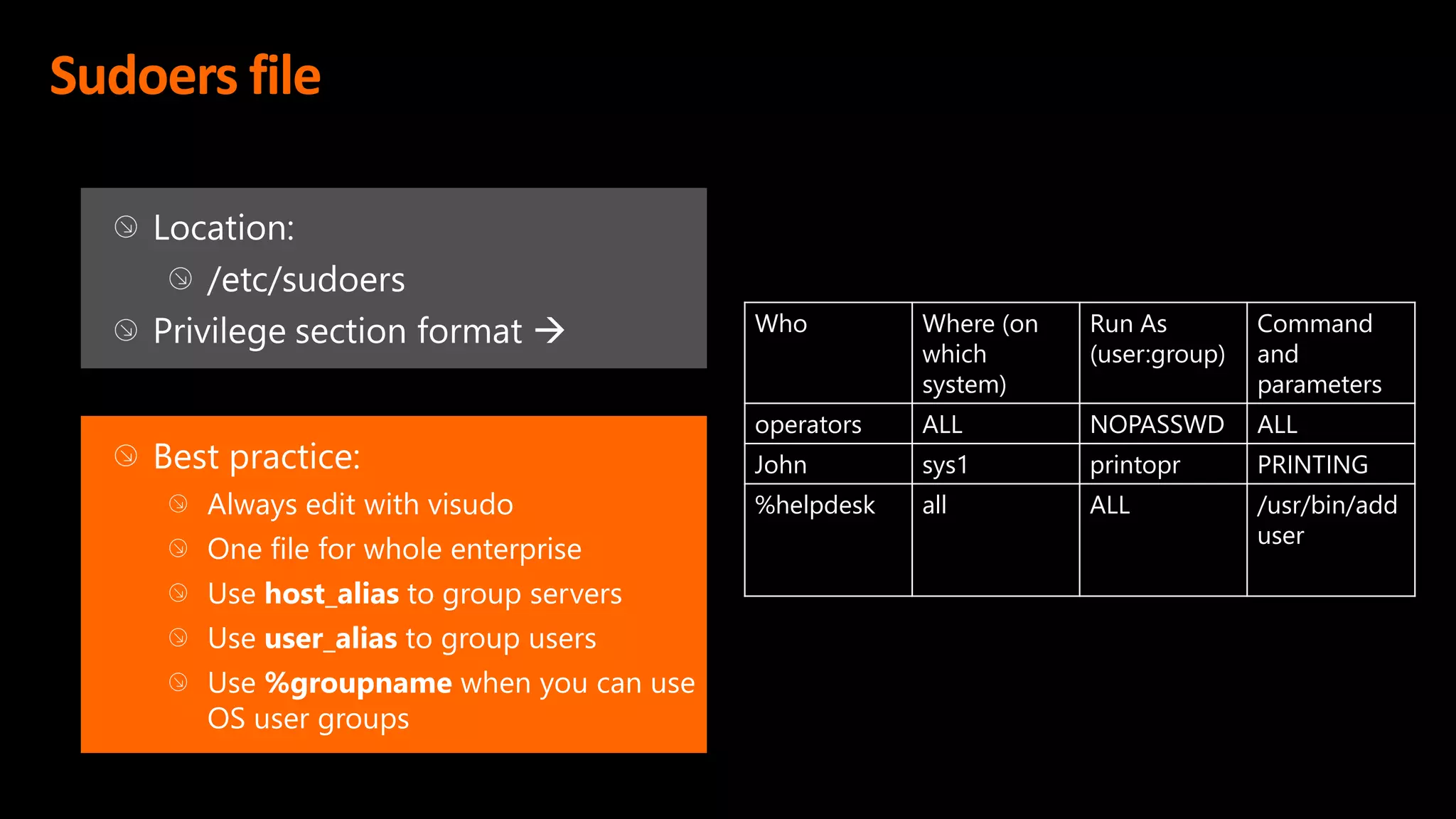
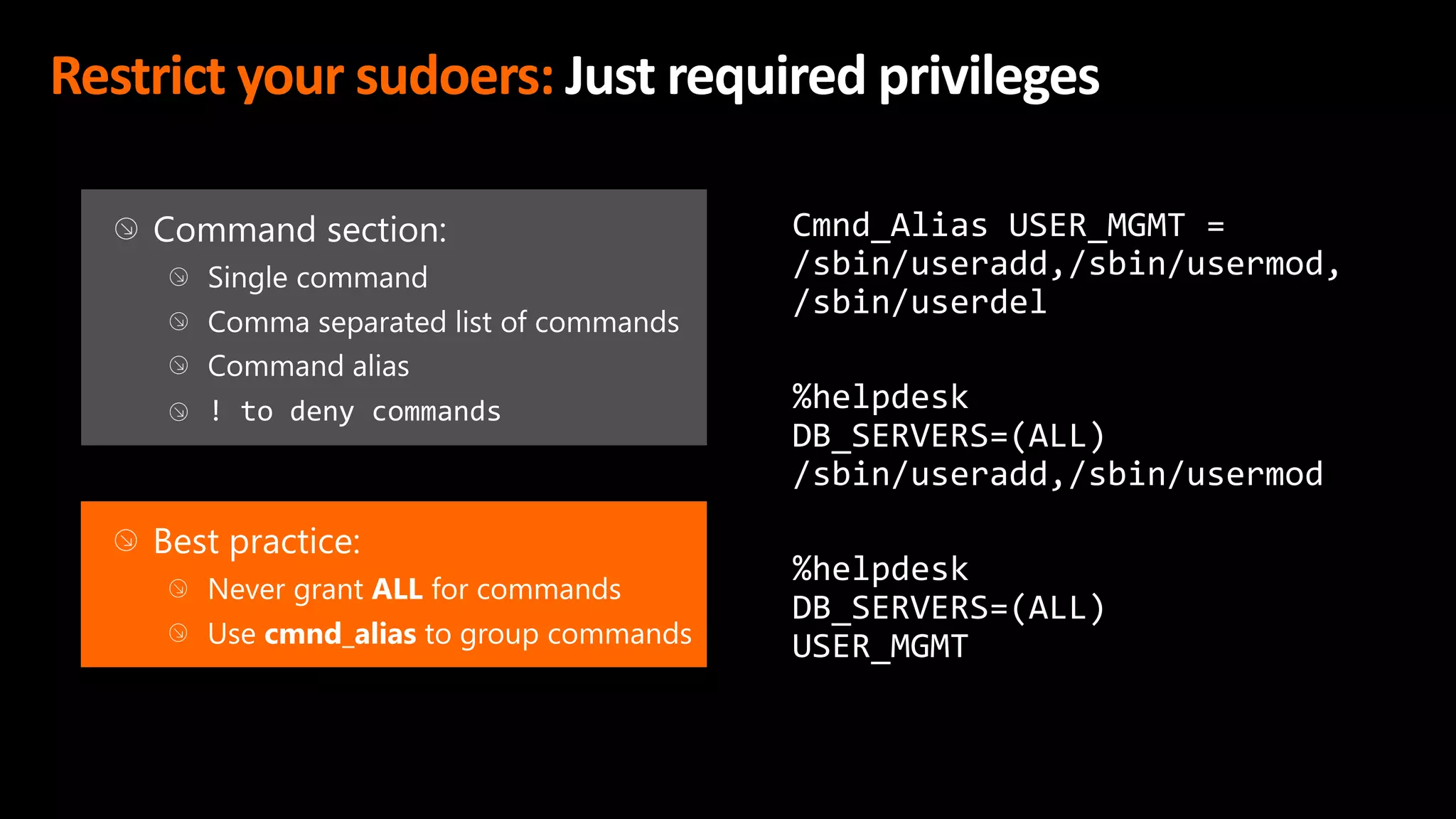
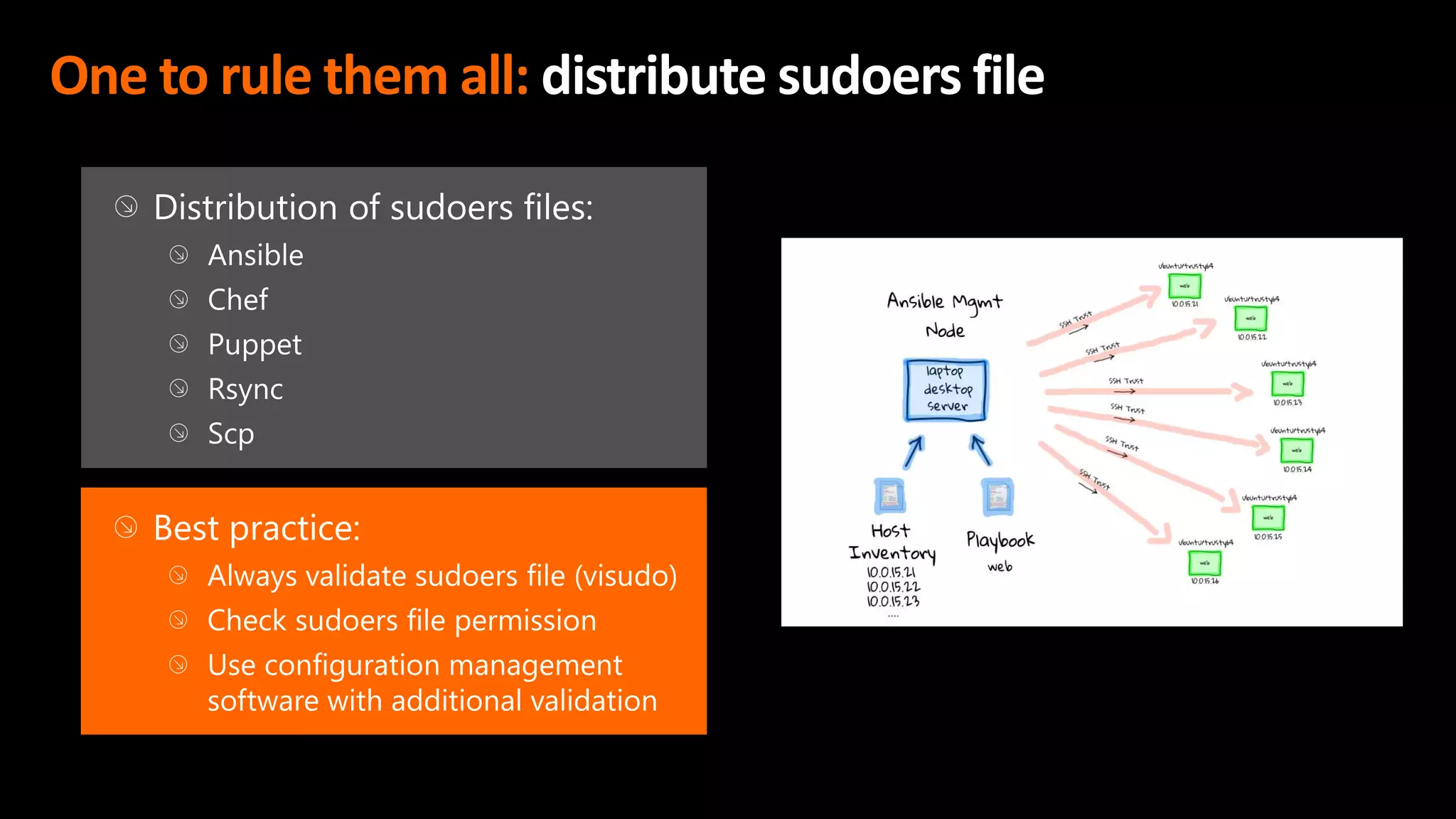
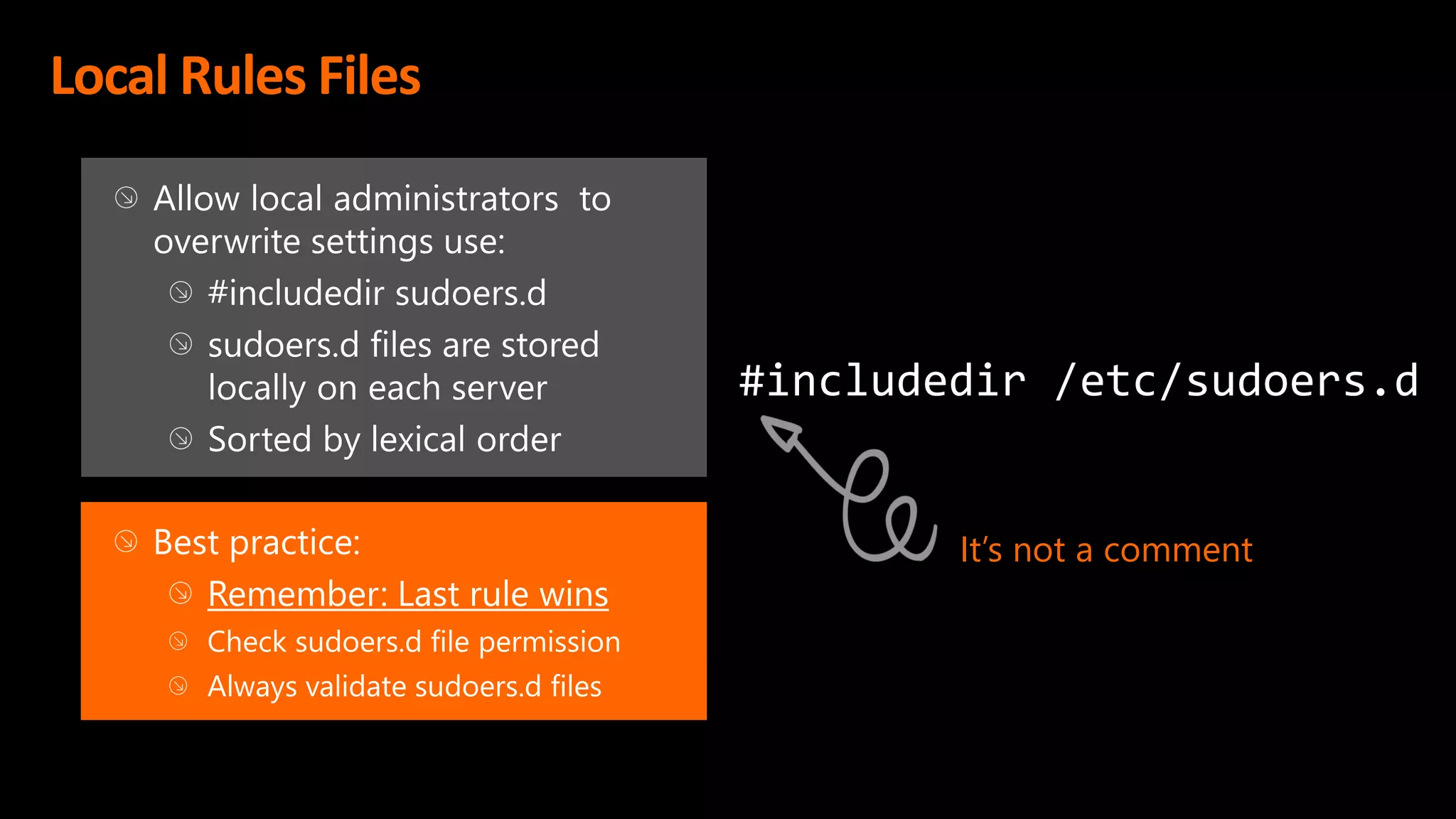
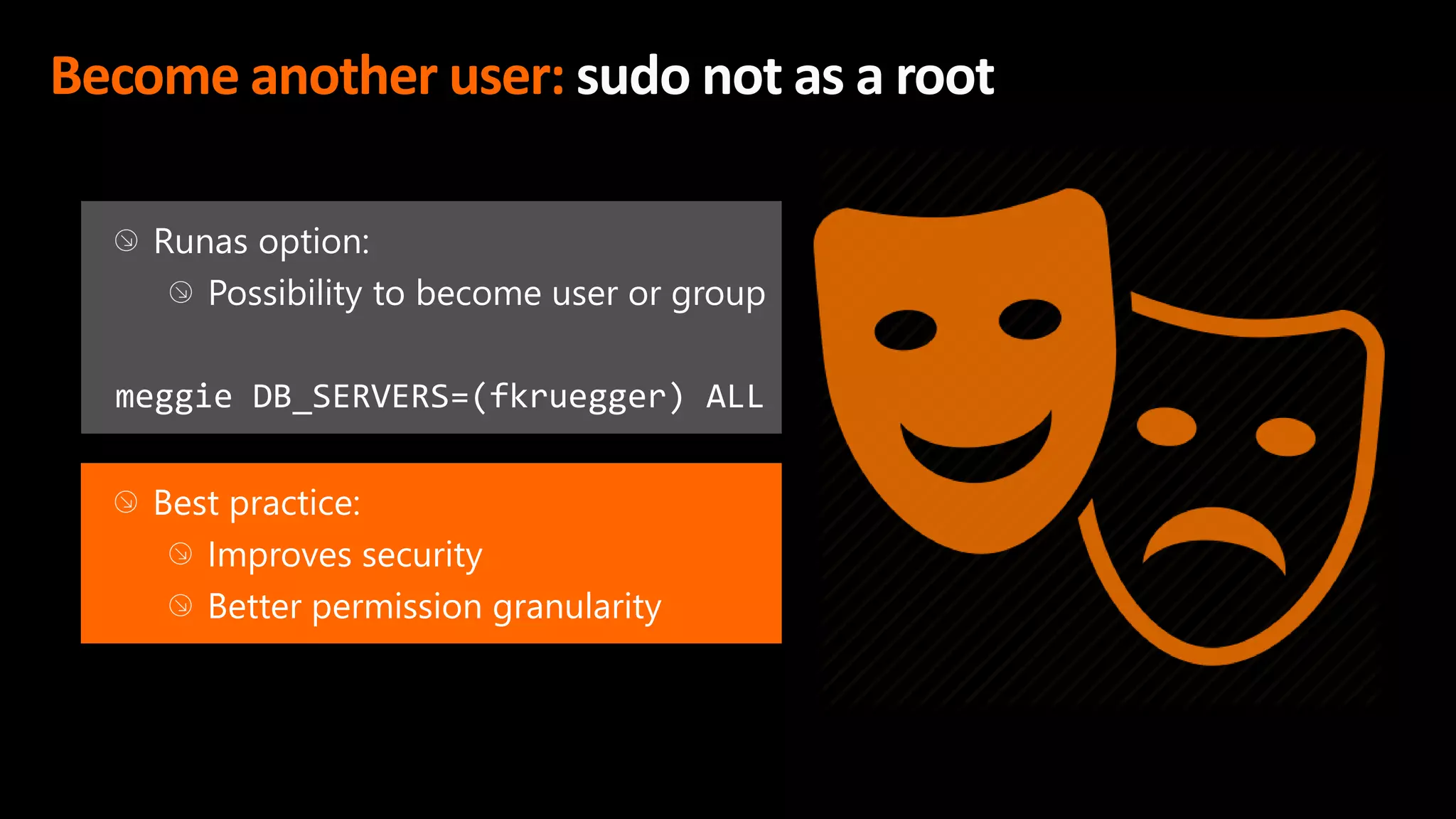
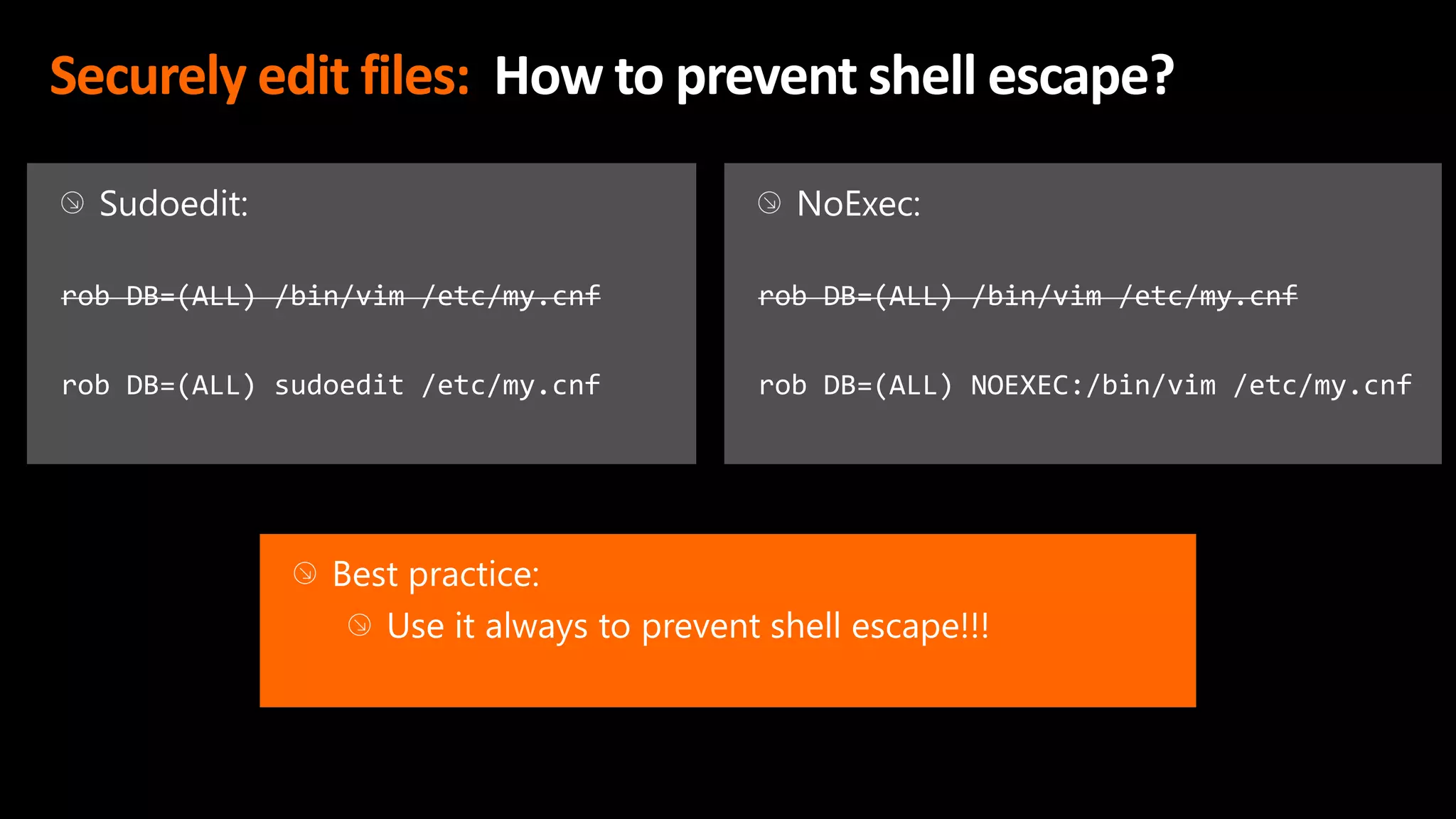
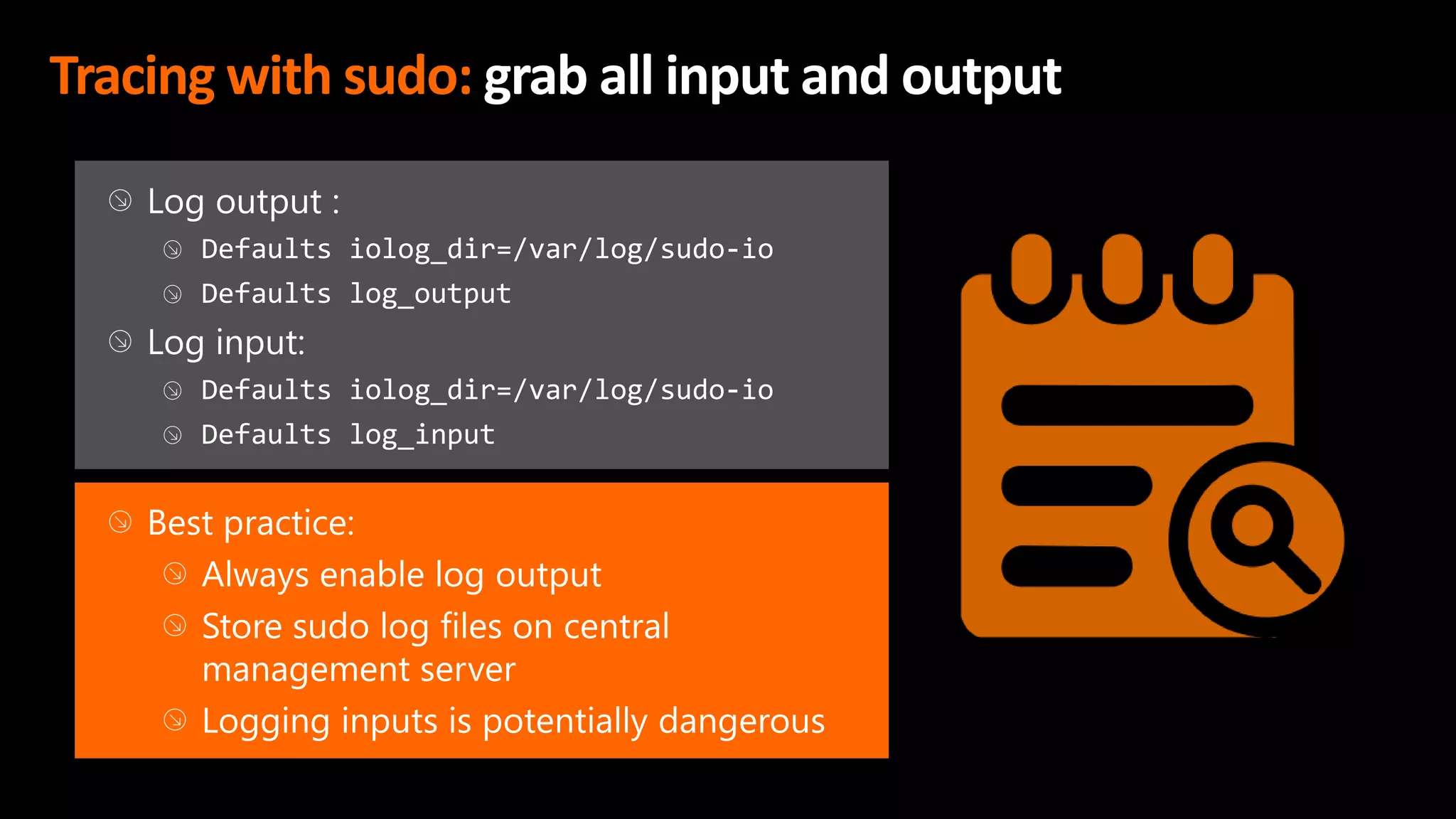
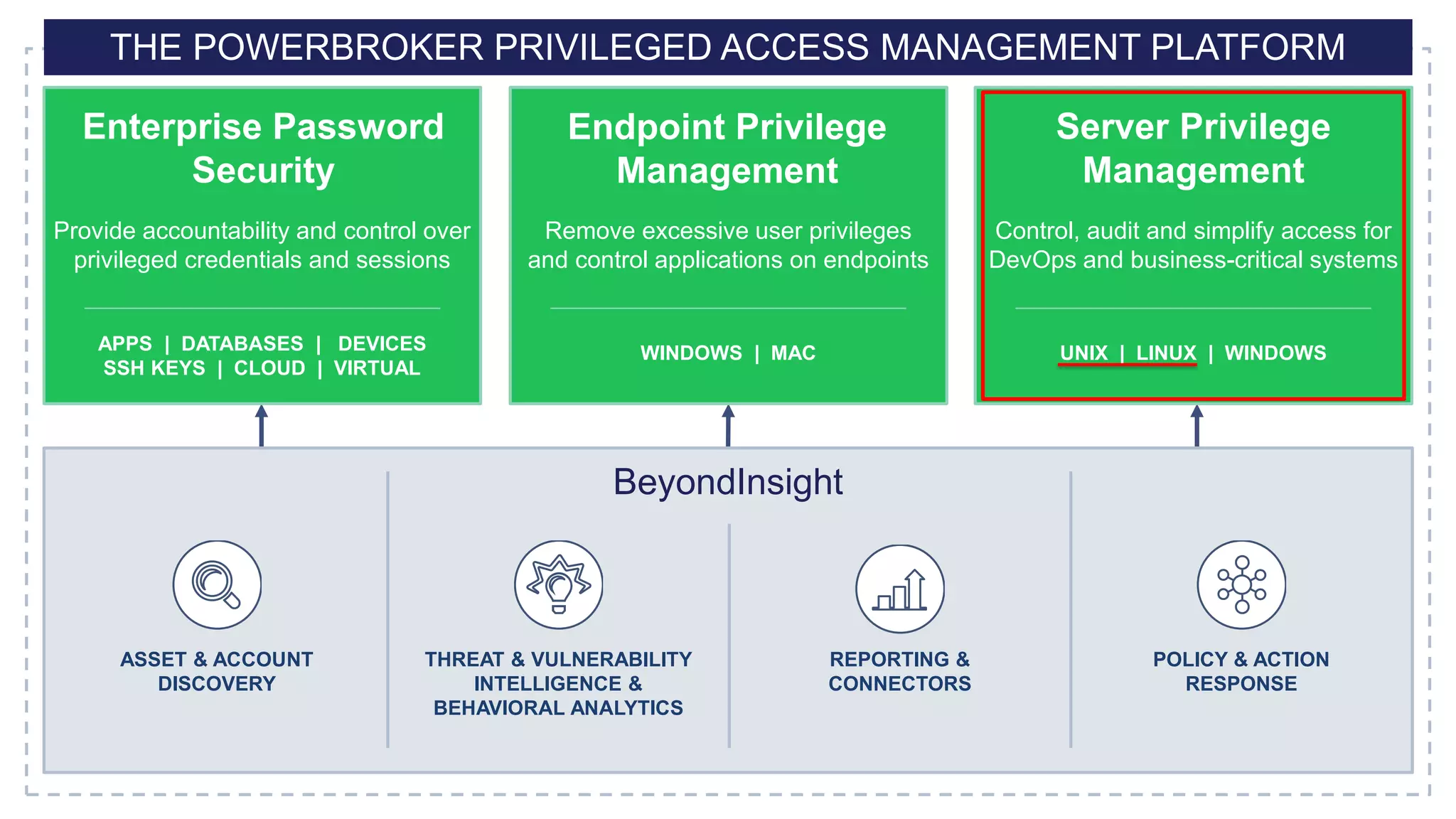
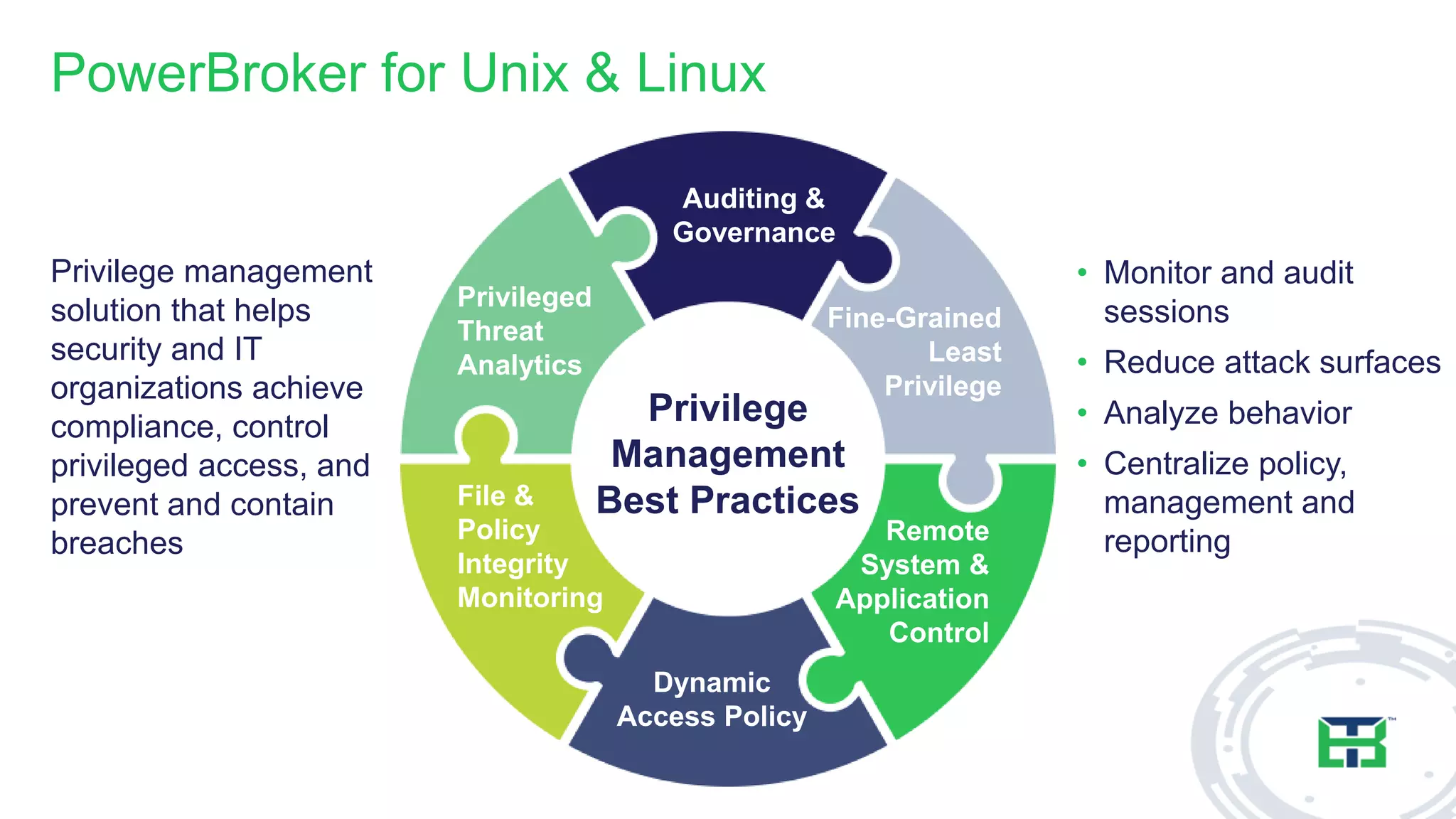
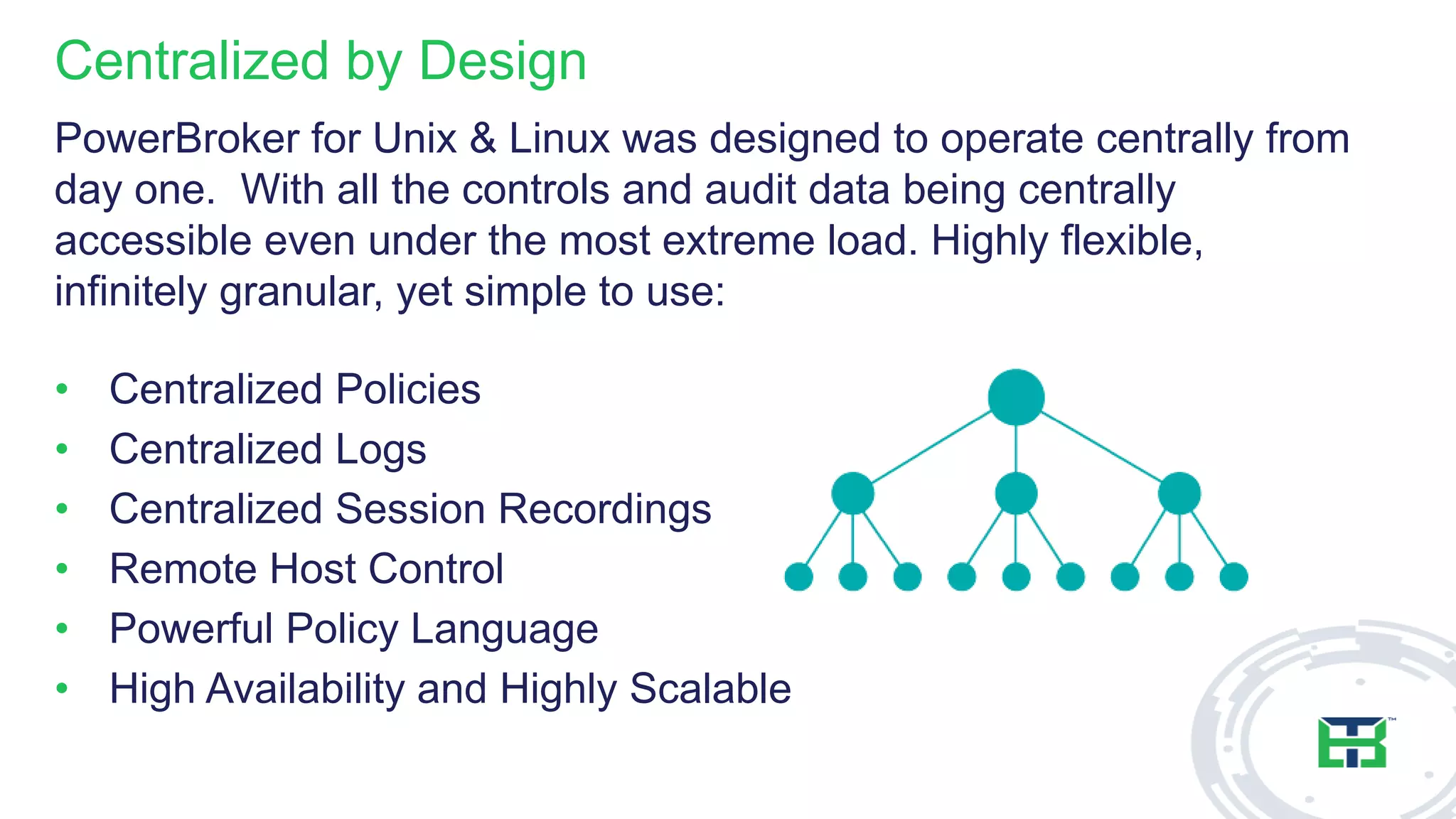
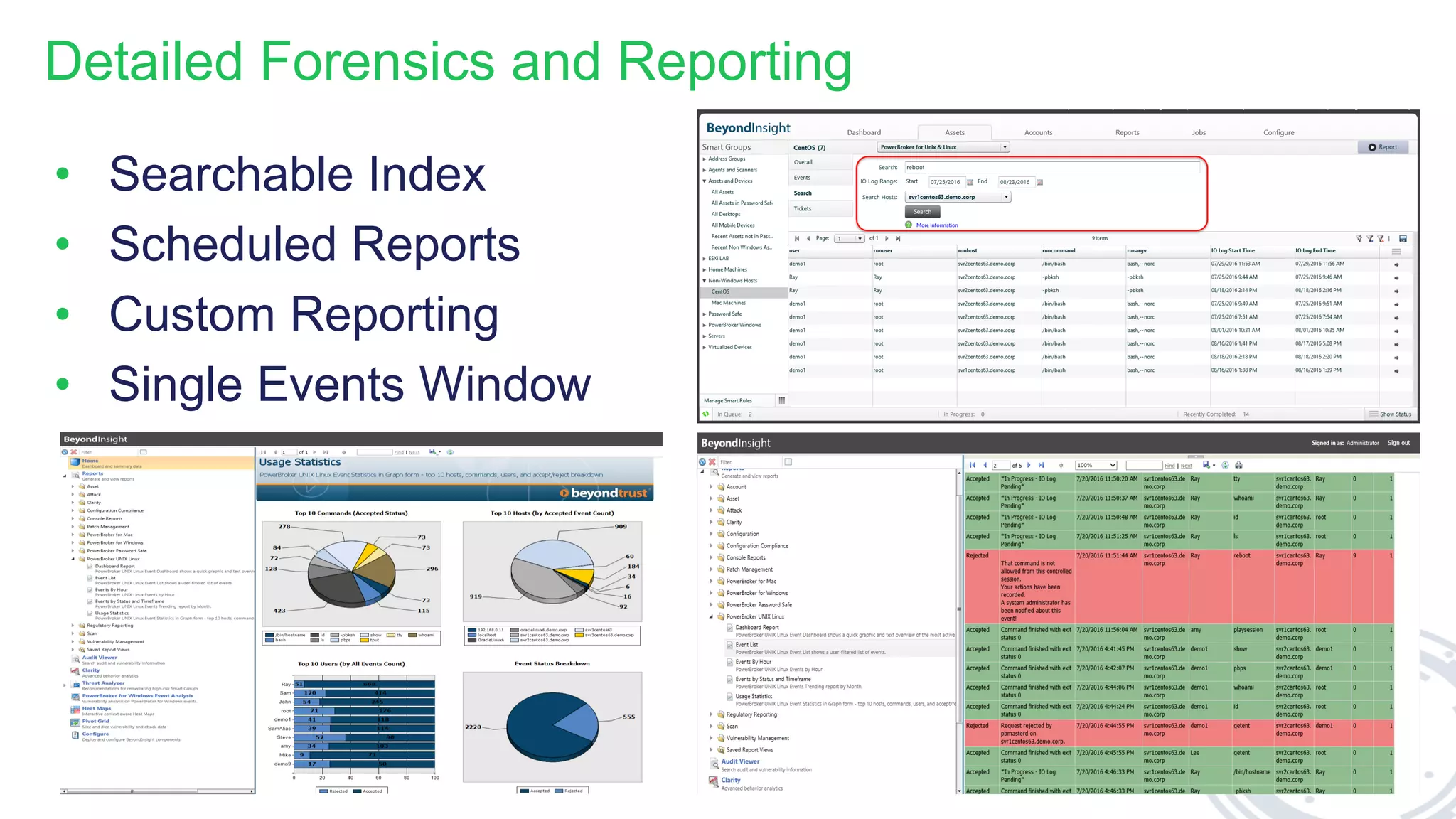
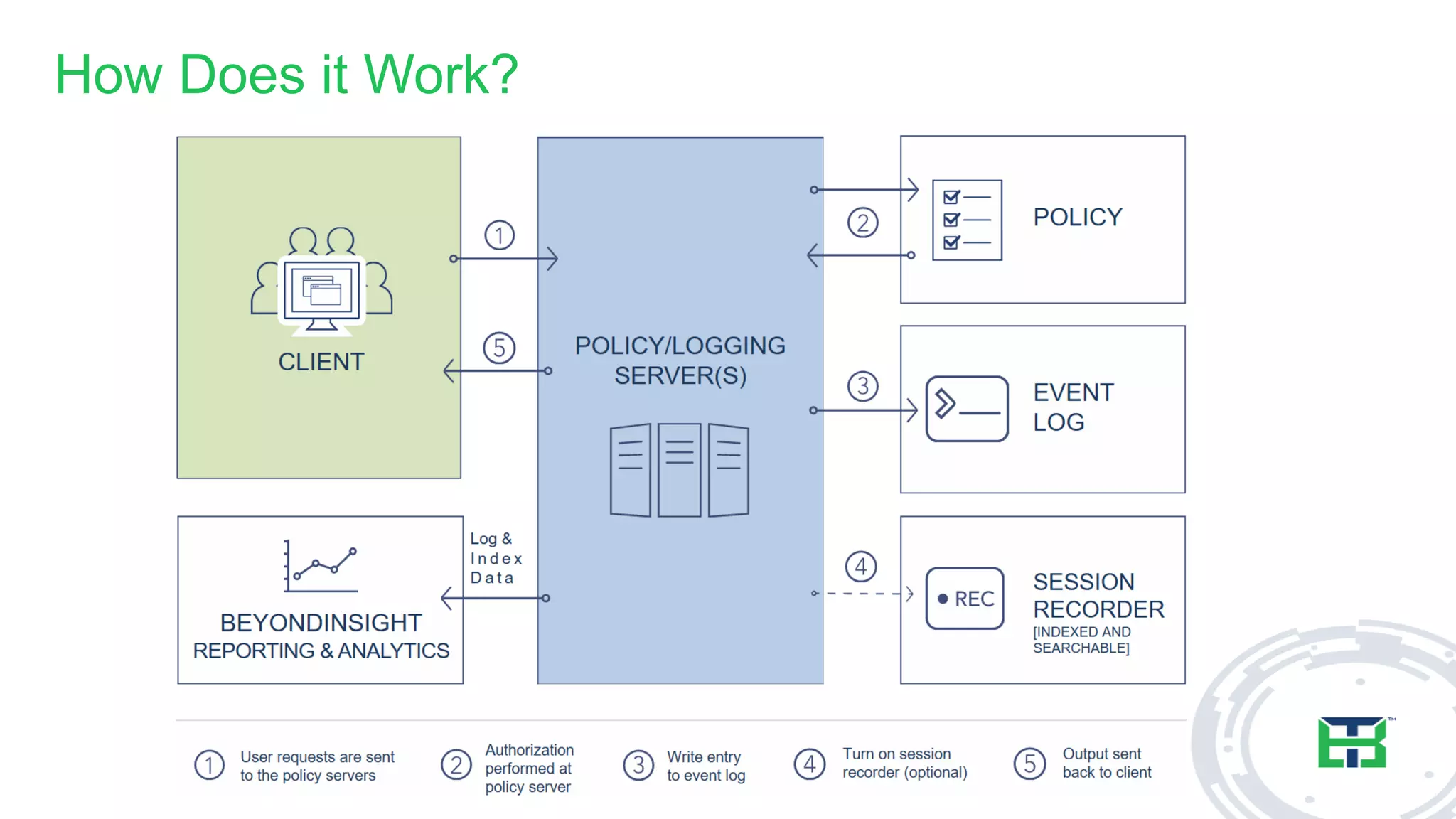
This document discusses the importance of the 'sudo' command in managing user privileges in Unix and Linux systems, highlighting its role in delegating authority, providing an audit trail, and the potential risks of misconfigured privileges. It also introduces the PowerBroker Privileged Access Management Platform, which offers comprehensive solutions for privilege management, auditing, and compliance. Additionally, it emphasizes the necessity of file integrity monitoring to ensure that elevated processes remain uncompromised.