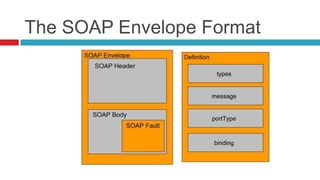
Web services present unique challenges for penetration testing due to their complexity and differences from traditional web applications. There is a lack of standardized testing methodology and tools for web services. Many penetration testers are unsure how to properly scope and test web services. Existing tools have limitations and testing environments must often be built from scratch. A thorough understanding of web service standards and frameworks is needed to effectively test for vulnerabilities from both the client and server side.