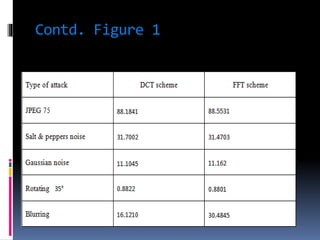
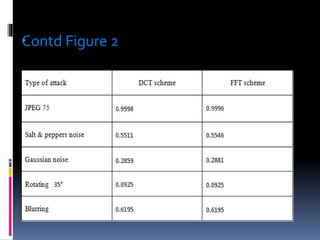
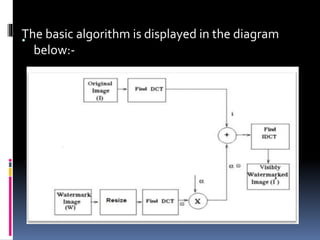
This document discusses various digital image watermarking techniques, focusing on embedding secret data into images using LSB, DWT, DCT, and FFT methods to enhance security during data transmission. It evaluates these techniques using metrics like signal-to-noise ratio and similarity ratio, concluding that while both DCT and FFT methods are robust, FFT shows superior resilience against blurring attacks. The project utilizes MATLAB for implementation and provides a comparison table of results.







![. The number of mismatched data between the
embedded watermark and the extracted watermark
is used to represent the Similarity of watermarks.
The similarity factor of extracted watermark and
original watermark is computed by the following:
Where and represent the original watermark image
and the extracted watermark image, respectively, M
and N represent the image size.The magnitude
range of SF is [0, 1]](https://image.slidesharecdn.com/watermarking-140530113106-phpapp01/85/Watermarking-Techniques-11-320.jpg)