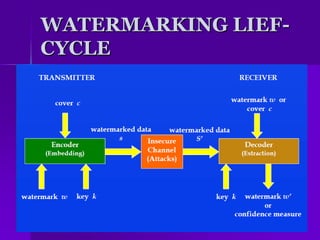
Digital watermarking embeds invisible identifying information into digital content like audio, video, and images. This allows copyright owners to establish ownership and prevents unauthorized distribution even if the content is copied. There are different types of watermarks that can be embedded, including robust watermarks that are difficult to remove and fragile watermarks that are destroyed if the content is tampered with. However, watermarks are not impossible to attack, as image processing techniques can potentially disable or overwrite them.