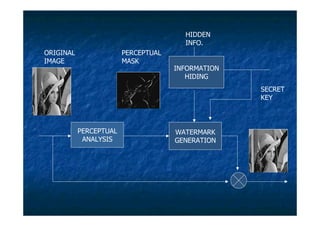
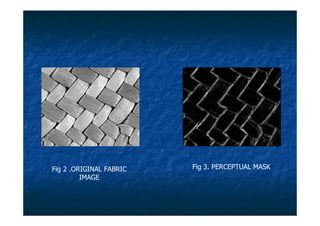
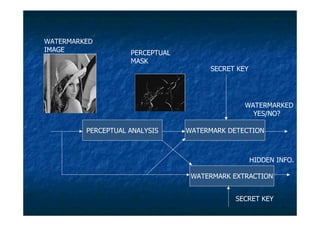
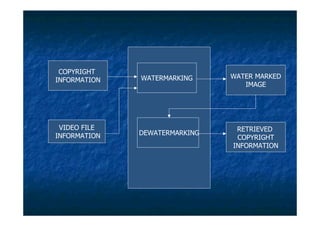
The document proposes a digital watermarking system to detect video piracy. Digital watermarks contain copyright information embedded in videos. The proposed system spreads watermarks throughout videos and makes them invisible, preventing easy removal. It embeds owner/distributor details, serial numbers and transaction dates. This allows tracing pirated videos back to their source by extracting the watermark information. The system overcomes issues like visible, concentrated watermarks in existing systems.