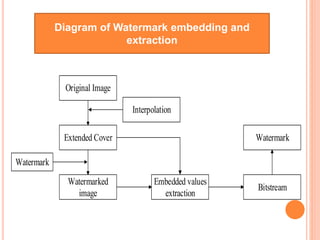
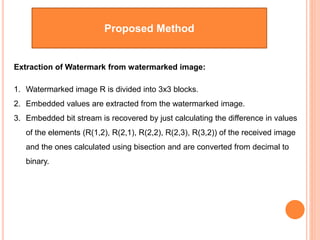
This document summarizes a student project on reversible data hiding techniques. The project compares different reversible watermarking methods and proposes a new technique that embeds a secret bitstream into a color image using bisection and square root interpolation. Experimental results showed the embedded and extracted bitstreams had a correlation of 1, indicating no data loss. Future work could improve the algorithm security by using multiple color planes and transformations for watermarking.
![A COMPARATIVE STUDY OF
REVERSIBLE DATA HIDING TECHNIQUES
SUBMITTED BY:
Abhishek Mukherjee (12500212001)
Ashish Kumar Singh (12500212016)
Nidhi Krishna (12500212050)
Nikhil Sinha (12500212052)
Probuddha Singha (12500212064)
Guided By :
Sayan Chakraborty
[Dept. Of Information Technology]](https://image.slidesharecdn.com/watermarkingppt-160910155650/75/Watermarkingppt-1-2048.jpg)







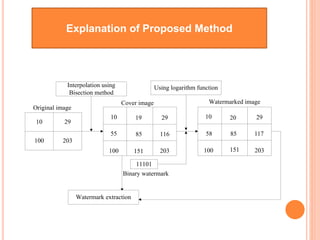
![Interpolation
Block_1[1,1] = Block_1[1,1]
Block_1[1,3] = Block_1[1,2]
Block_1[3,1] = Block_1[2,1]
Block_1[3,3] = Block_1[2,2]
Block_1[1,2] = (Block_1[1,1]+Block_1[1,3])/2
Block_1[2,1] = (Block_1[1,1]+Block_1[3,1])/2
Block_1[2,2] = (Block_1[1,2]+Block_1[3,2])/2
Block_1[2,3] = (Block_1[1,3]+Block_1[3,3])/2
Block_1[3,2] = (Block_1[3,1]+Block_1[3,3])/2
For using square root function we use
√(Block_x[y1,z1]2+Block_x[y2,z2]2 )/2 in
place of the bisection function.
19](https://image.slidesharecdn.com/watermarkingppt-160910155650/85/Watermarkingppt-11-320.jpg)
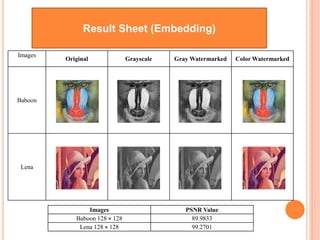
![Result Sheet (Extraction)
Original Carrier
Image
[128 X 128]
Embedded Secret
Binary Image
[128 X 128]
Watermarked
Image
[192 X 192]
Extracted Secret
Binary Image
[128 X 128]
Correlation
1
1
This is the result of using bisection method. We have also used a square
root function √(a2+b2 )/2 which also gave us the Correlation value of 1.](https://image.slidesharecdn.com/watermarkingppt-160910155650/85/Watermarkingppt-14-320.jpg)

![Conclusion
Disadvantages
1. In our proposed method, we have only used the blue plane only. If we had
used the other 2 planes too, (i.e., Red, Green & Blue planes) our algorithm
& watermarking technique could be made more secure from attacks.
2. The PSNR values were not that impressive & were varying for the images
3. The algorithm used is very simple. More complicated algorithms lower the
risk of information being extracted from attacks.
4. There is a limit to the number of bits that can be embedded into a cover
image. For example, if we have an image of size M x M then, Max. No. of
bits that can be embedded into its watermarked image =
[(M x M) / (2 x 2)] x 10](https://image.slidesharecdn.com/watermarkingppt-160910155650/85/Watermarkingppt-16-320.jpg)

![References
[1] S. R. Chowdhury, R. Ray; N. Dey; S. Chakraborty; W. Ben Abdessalem Karaa
& S. Nath, "Effect of demons registration on biomedical content watermarking",
2014 International Conference on Control, Instrumentation, Communication and
Computational Technologies (ICCICCT), July 2014, pp.509-514.
[2] Craver,S. Memon,N. Yeo, B.L and Yeung, M.M "Resolving Rightful Ownership
with Invisible Watermarking Techniques: Limitations, Attacks and
Implications," IEEE JSAC, March 1997.
[3] Yeung, M.M and Mintzer, F. "An Invisible Watermarking Technique for Image
Verification," Proceedings of IEEE ICIP'97, Santa Barbara, CA, Oct. 1997.
[4] Hoover A., Goldbaum M. (2003) ‘Locating the optic nerve in a retinal image
using the fuzzy convergence of the blood vessels’, in IEEE Transaction on
Medical Imaging, Vol. 22, No. 8, pp. 951 -958.
[5] Jiang X., Mojon D. (2003) ‘Adaptive local thresholding by verification based
multithreshold probing with application to vessel detection in retinal images’, in
IEEE Trans. Pattern Anal. Mach. Intell., Vol. 25, No. 1, pp. 131 -137.
[6] Niemeijer M., van Ginneken B., Staal J. J., Suttorp-Schulten M. S. A., Abramoff
M. D. (2005) ‘Automatic detection of red lesions in digital color fundus
photographs’, in IEEE Transaction on Med. Imaging, Vol. 24 , No. 5, pp. 584 -592.
[7] Foracchia M., Grisan E., Ruggeri A. (2005) ‘Luminosity and contrast
normalization in retinal images’ in Med. Image Anal., Vol. 9, No. 3, pp. 179 -190.
[8] Mendon a A. M., Campilho A. (2006) ’Segmentation of retinal blood vessels by
combining the detection of centerlines and morpholo gical reconstruction’, in
IEEE Trans. Med. Imag. Vol. 25, No. 9, pp. 1200 -1213.](https://image.slidesharecdn.com/watermarkingppt-160910155650/85/Watermarkingppt-18-320.jpg)
