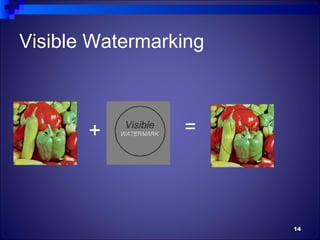
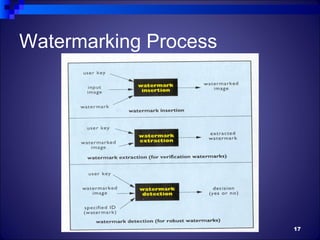
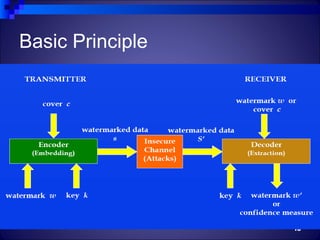
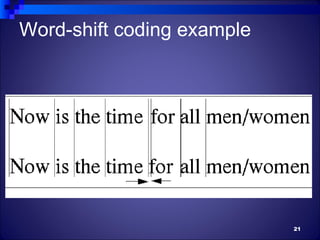
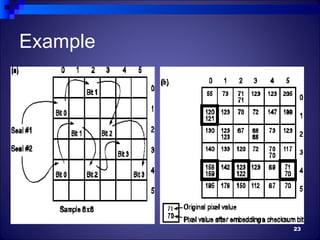
The document discusses watermarking, including its history and different types. It defines watermarking as a recognizable image or pattern embedded in paper or a digital signal inserted into digital content to carry ownership information. The summary describes visible watermarking, which embeds visible logos or text, and invisible watermarking, which makes imperceptible changes to encode data. It also classifies watermarking as either text-based, image-based, or audio/video-based and discusses example watermarking techniques and applications for copyright protection.