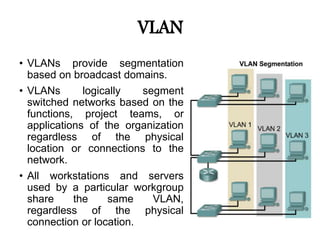
This document discusses VLANs (virtual local area networks). It defines LANs and VLANs, explaining that VLANs logically segment networks based on functions or teams rather than physical connections. It describes static and dynamic VLAN implementation methods and port-based, MAC address-based, and protocol-based VLAN types. Finally, it outlines benefits of VLANs such as easy network changes, traffic control, and improved security.