Embed presentation
Download to read offline
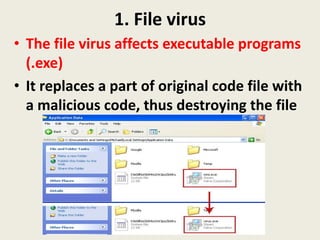






This document discusses different types of computer viruses including file viruses, boot sector viruses, and partition table viruses. It explains that file viruses replace executable program code with malicious code, boot sector viruses substitute themselves for the bootstrap loader program to automatically load when the computer starts, and partition table viruses modify the partition table. It also provides examples of other types of viruses such as Trojan horses, worms, and stealth viruses. Finally, it states that antivirus software is used to identify and remove malicious software from computers.







